简介:主要讲解如何在linux和windows上面生成ssh密钥文件以及上传到被控主机上,实现免密连接。(请注意区分公钥和密钥的作用)
零、测试环境
windows10 x64
xshell6
mobaxterm
finalshell
[root@osker ~]# uname -a Linux oldboy 3.10.0-957.el7.x86_64 #1 SMP Thu Nov 8 23:39:32 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
一、linux主机向linux主机分发密钥
1.m01主机创建ssh密钥
[root@m01 ~]# ssh-keygen -C jumpserver Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: SHA256:17Leb+HcnQ6KG8DmaIJ1owCvMbGCgZyqA1/IuP8gXOs jumpserver The key's randomart image is: +---[RSA 2048]----+ | | |o . | |=o | |+B . . . | |X.+o.o +S o . | |=*=.+ = .. o . | |*oo+ o . .. + oo| | +..o .o.. =.o| | .E. oo..oo. | +----[SHA256]-----+
2.查看生成的公钥id_rsa.pub
[root@m01 ~]# cat .ssh/id_rsa.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCmsnAb+0VDb/8yfCDZhsMj8w1SoRthxTKEnFh+qCS6buM7V9MJckMOMWfBN47R6McQvvuSQAoPxm+67aCl75pvKpOXvypt/mzPmClHW7UYvKVKV46lOJKSqB43V8Qq1AhYqL6Ls3KZ7JkMWaT50DeSvRH7lIMk64zHRO896X9cfduQsUxh/f+tBfL+zYLynkrm+I45iVPq09eBrkrMJg9rrzzyzqOSze2CCB0gI+luz2fxaCJPNWbkx+VHOfx9N+j8oOPxNY1VLTTBZU/QDe+kdaiMAeCHQDqOfLEl0Sby83X7ou4K92URX0rr5Oy/XgYOT4LVyBMAeK7JgHlDb/4H jumpserver
3.使用ssh-copy-id命令自动上传公钥到41主机(backup主机)
[root@m01 ~]# ssh-copy-id -i ./.ssh/id_rsa.pub root@172.16.1.41 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "./.ssh/id_rsa.pub" The authenticity of host '172.16.1.41 (172.16.1.41)' can't be established. ECDSA key fingerprint is SHA256:cHKT5G6hYgv1k1zTfc36tZrLNQqJhc1JeBTeke545Fk. ECDSA key fingerprint is MD5:24:4e:94:6d:46:82:0a:61:3a:1e:83:3f:75:82:e1:aa. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@172.16.1.41's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'root@172.16.1.41'" and check to make sure that only the key(s) you wanted were added.[root@m01 ~]# ssh-copy-id -i ./.ssh/id_rsa.pub root@172.16.1.41 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "./.ssh/id_rsa.pub" The authenticity of host '172.16.1.41 (172.16.1.41)' can't be established. ECDSA key fingerprint is SHA256:cHKT5G6hYgv1k1zTfc36tZrLNQqJhc1JeBTeke545Fk. ECDSA key fingerprint is MD5:24:4e:94:6d:46:82:0a:61:3a:1e:83:3f:75:82:e1:aa. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@172.16.1.41's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'root@172.16.1.41'" and check to make sure that only the key(s) you wanted were added.
4.查看本机的私钥文件id_rsa (注意私钥文件的权限为600)
[root@m01 ~]# ll -a .ssh/ total 12 drwx------ 2 root root 57 Apr 20 11:24 . dr-xr-x---. 3 root root 163 Apr 13 12:37 .. -rw------- 1 root root 1679 Apr 20 11:23 id_rsa -rw-r--r-- 1 root root 392 Apr 20 11:23 id_rsa.pub -rw-r--r-- 1 root root 173 Apr 20 11:24 known_hosts [root@m01 ~]# cat .ssh/id_rsa -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAprJwG/tFQ2//Mnwg2YbDI/MNUqEbYcUyhJxYfqgkum7jO1fT ... n3h/Fk2FvAY5PCTBnMGeBl11hWMyIQTbW3Viyt36Dby3vvW0Z22lLw== -----END RSA PRIVATE KEY-----
5.此时直接使用ssh就可以免密登录了。
[root@m01 ~]# ssh root@172.16.1.41 Last login: Mon Apr 20 11:19:20 2020 from 10.0.0.1 [root@backup ~]#
6.m01分发公钥后到backup服务端查看公钥位置及信息(注意公钥的权限为600)
[root@backup ~]# ll .ssh/ -rw------- 1 root root 392 Apr 20 11:24 authorized_keys [root@backup ~]# cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCmsnAb+0VDb/8yfCDZhsMj8w1SoRthxTKEnFh+qCS6buM7V9MJckMOMWfBN47R6McQvvuSQAoPxm+67aCl75pvKpOXvypt/mzPmClHW7UYvKVKV46lOJKSqB43V8Qq1AhYqL6Ls3KZ7JkMWaT50DeSvRH7lIMk64zHRO896X9cfduQsUxh/f+tBfL+zYLynkrm+I45iVPq09eBrkrMJg9rrzzyzqOSze2CCB0gI+luz2fxaCJPNWbkx+VHOfx9N+j8oOPxNY1VLTTBZU/QDe+kdaiMAeCHQDqOfLEl0Sby83X7ou4K92URX0rr5Oy/XgYOT4LVyBMAeK7JgHlDb/4H jumpserver [root@backup ~]#
二、windows向linux分发密钥
1.打开xshell中的工具选项,选择“新建用户密钥生成向导”

2.密钥类型默认,密钥长度默认,点击下一步。
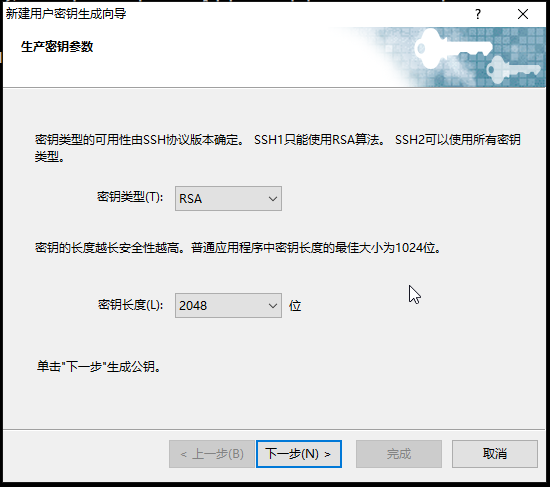
3.下一步

4.密钥名称填入自定义名称,密码为给密钥添加密码,此处可以不填。点击下一步。
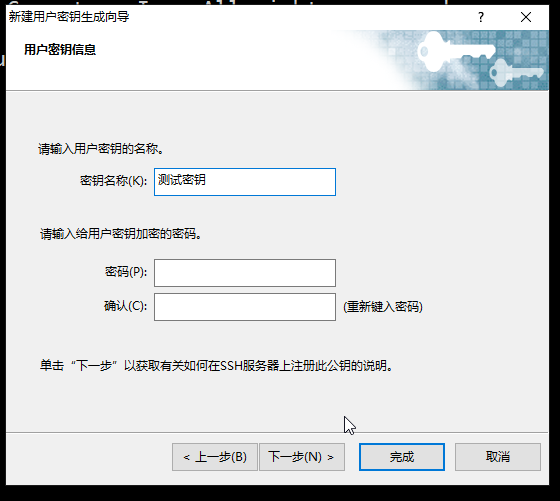
5.选择 是
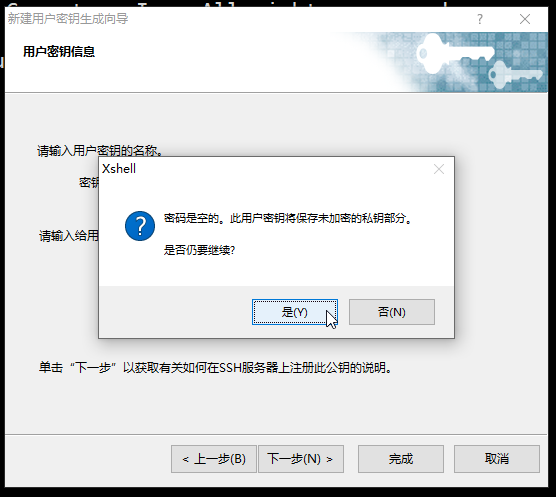
6.选择 完成

7.选择用户密钥管理者

8.选中刚刚生成的密钥名称,然后点击属性。
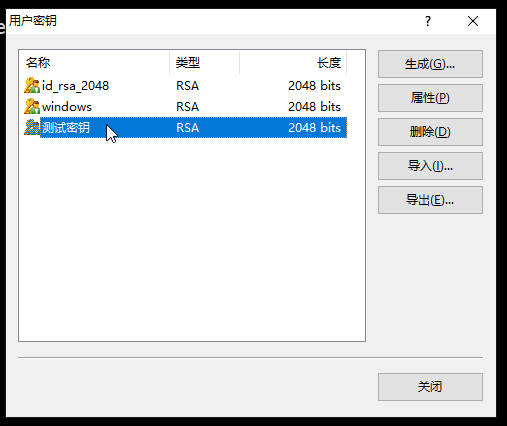
9.点击公钥
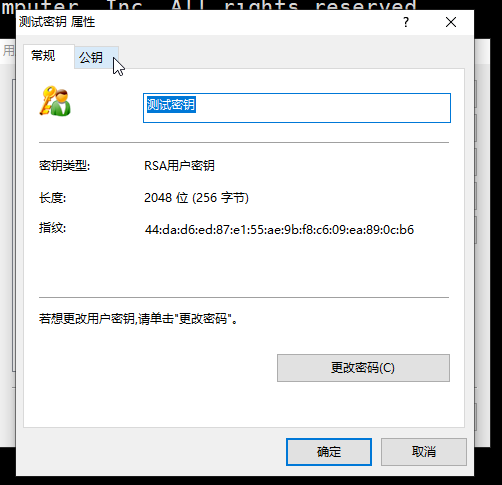
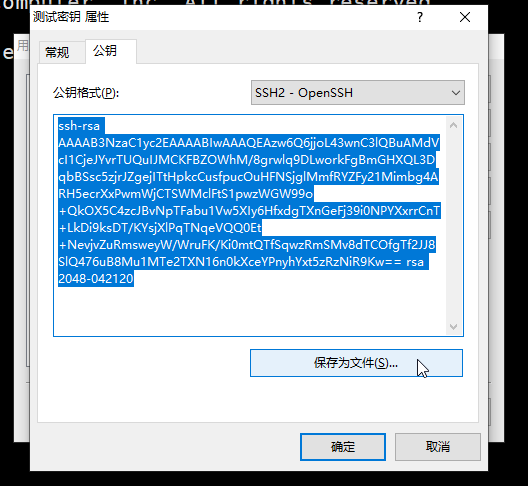
10.这里可以复制出公钥内容或者保存为文件
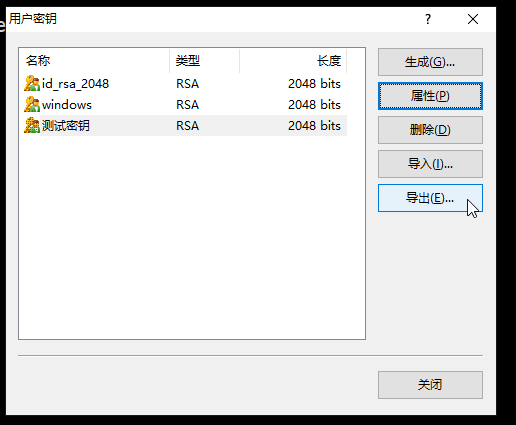
11.私钥导出:首先选中密钥名称,然后点击导出。(此私钥下文会使用到)
12.选择位置,添加文件名,保存即可。(私钥请妥善保管)

13.首先使用xshell 密码登录, ssh root@10.0.0.100
[root@osker ~]# ll -a -rw-r--r--. 1 root root 100 Dec 29 2013 .cshrc ... drwx------ 2 root root 25 Apr 9 20:14 .ssh -rw-r--r--. 1 root root 129 Dec 29 2013 .tcshrc ###切到.ssh下,创建authorized_keys文件并将公钥内容copy到文件中
###为什么要在此处创建认证文件?因为在sshd的配置文件中有默认定义认证文件的位置。
###vim /etc/ssh/sshd_config
###47 AuthorizedKeysFile .ssh/authorized_keys
###大约在第47行左右 [root@osker ~]# cd .ssh/ [root@osker .ssh]# vim authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAzw6Q6jjoL43wnC3lQBuAMdVcI1CjeJYvrTUQuIJMCKFBZOWhM/8grwlq9DLwor kFgBmGHXQL3DqbBSsc5zjrJZgejITtHpkcCusfpucOuHFNSjglMmfRYZFy21Mimbg4ARH5ecrXxPwmWjCTSWMclFtS1pwzWGW9 9o+QkOX5C4zcJBvNpTFabu1Vw5XIy6HfxdgTXnGeFj39i0NPYXxrrCnT+LkDi9ksDT/KYsjXlPqTNqeVQQ0Et+NevjvZuRmswe yW/WruFK/Ki0mtQTfSqwzRmSMv8dTCOfgTf2JJ8SlQ476uB8Mu1MTe2TXN16n0kXceYPnyhYxt5zRzNiR9Kw== rsa 2048-04 2120 [root@osker .ssh]# ll -a total 8 drwx------ 2 root root 48 Apr 21 07:46 . dr-xr-x---. 3 root root 163 Apr 21 07:46 .. -rw-r--r-- 1 root root 397 Apr 21 07:46 authorized_keys -rw-r--r-- 1 root root 177 Apr 9 20:14 known_hosts [root@osker .ssh]# ll authorized_keys -rw-r--r-- 1 root root 397 Apr 21 07:46 authorized_keys ###修改权限 [root@osker .ssh]# chmod 600 authorized_keys [root@osker .ssh]# ll authorized_keys -rw------- 1 root root 397 Apr 21 07:46 authorized_keys
至此,公钥就上传到被控主机上了。
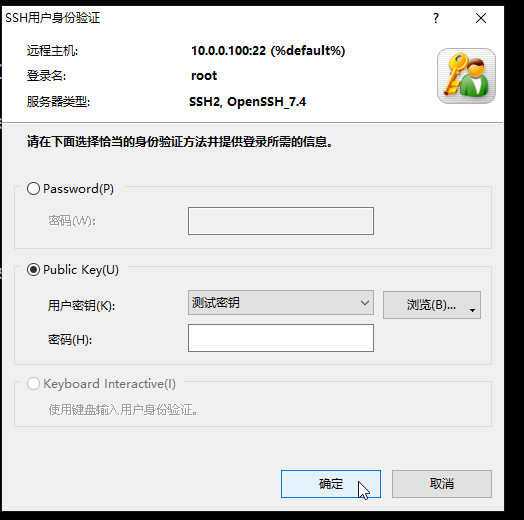
在xshell终端使用ssh 10.0.100登录,输入root
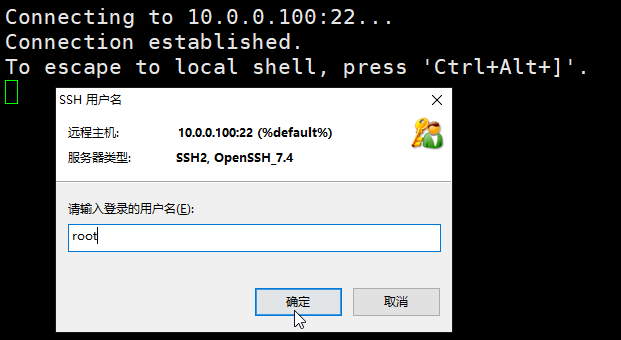
选择public key,再选中刚才创建的 测试密钥,就可以免密登录了。
三、其它远程连接软件添加私钥
1.mobaxterm设置:填入主机地址和用户名,再advanced ssh setting中 勾选use private key,然后找到之前导出到电脑的测试私钥文件,选中后点击ok。(我们已经在上文中上传了公钥到测试主机中,所以这里就不操作上传公钥了。)

2.finalshell设置:认证方法上选择公钥,私钥选择上文中导出到电脑的私钥文件。

至此,linux或windows向linux分发密钥的流程就介绍完毕了。
本博文为原创博文,转发请标明出处。
from:chiugui@qq.com