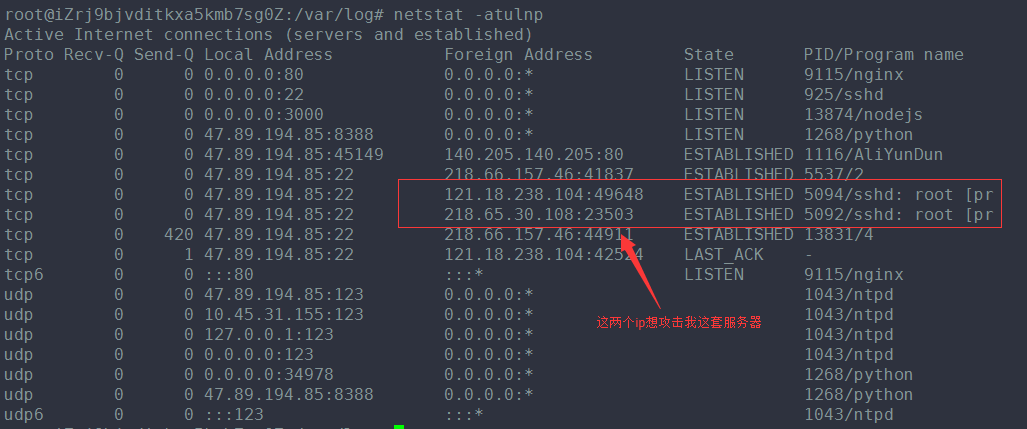
查看auth.log日志,差点吓一跳,好多攻击记录。
vim /var/log/auth.log
才两天的功夫,900多万条记录,

一些解决应对的办法:
|
43down voteaccepted
|
It is very common. Many botnets try to spread that way, so this is a wide scale mindless attack. Mitigation measures include:
|
标注黄色背景的是解决的办法!
stack-overflow上面,搜索了一下这方面的攻击,看到一个提问和我遇到的情况类似:
Is it normal to get hundreds of break-in attempts per day?
I just checked my server's /var/log/auth.log and found that I'm getting over 500 failed password/break-in attempt notifications per day! My site is small, and its URL is obscure. Is this normal? Should I be taking any measures?
下面是回答:
|
Until we locked down all unnecessary external ports, I remember not only did we get lots of hack attempts, but one day it was so bad that we were being hacked from two different countries -- at the same time! So yes, 100s of break-in attempts is perfectly normal. – Django Reinhardt Mar 8 '11 at 14:53
|
||
|
We have servers that experience a new attack "sequence" once every 16 seconds. A single sequence is usually a batch of around 100 attempts across various ports. Just for kicks one day I turned on an unpatched server outside our firewall; it tooks less than 10 minutes from the time it was powered on for it to get pwnd. Point is the internet truly is a jungle; try not to get eaten. – NotMe Mar 8 '11 at 18:55
|
||
|
I can see I posted my question to the wrong site: superuser.com/questions/200896/… – Justin C Mar 9 '11 at 22:01
|
||
|
while I agree with others this is normal on common ports required (80, 443) I practically eliminated these attempts against my SSH port by simply changing the default port from 22 to something obscure like 6022 for example. Just doing that, alone, nearly eliminated 99% of that type of attack. – Kilo Mar 11 '11 at 20:32
|
||
|
If you're going to change your SSH port, there are security reasons to keep it below port 1024 (only root can open ports < 1024, so it protects you from other users hijacking SSH). –
|
|
accepted
|
In today's internet this is quite normal sadly. There are hordes of botnets trying to login to each server they find in whole IP networks. Typically, they use simple dictionary attacks on well-known accounts (like root or certain applications accounts). The attack targets are not found via Google or DNS entries, but the attackers just try every IP address in a certain subnet (e.g. of known root-server hosting companies). So it doesn't matter that your URL (hence the DNS entry) is rather obscure. That's why it is so important to:
Additionally, you can install fail2ban which will scan the authlog and if it finds a certain amount of failed login attempts from an IP, it will proceed to add that IP to In addition to the SSH attacks, it is also becoming common to scan your webserver for vulnerable web-applications (some blogging apps, CMSs, phpmyadmin, etc.). So make sure to keep those up-to-date and securely configured too! |
||||||||||||||||||||
|