Last year hackers stole millions from Taiwan First Commercial bank's ATMs without using a card. This was absolutely a premeditated attack. Hackers "broke into" the voice recording server of First Bank's London branch. They started to gain administrator privilege of servers and workstations. Finally they manipulated those ATMs to spit out cash successfully. Suspects were caught at last oweing to three factors:
1.Taiwanese law-enforcement authorities(indluding skillful forensic examiner from MJIB,CIB, etc)
2.vast network of security cameras
3.sharp-eyed and enthusiastic citizens
How to improve endpoint security is a very important issue. Take ATM for example, ATM is like a self service kiosk. Customers can access their bank deposit or credit accounts conveniently. As long as these ATMs are up and running, IT administrators seldom pay attention to these ATMs.They'd like to spend time on banking systems and servers.
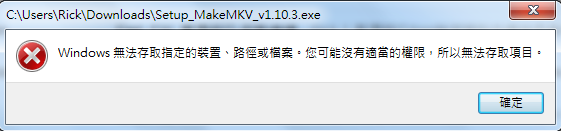
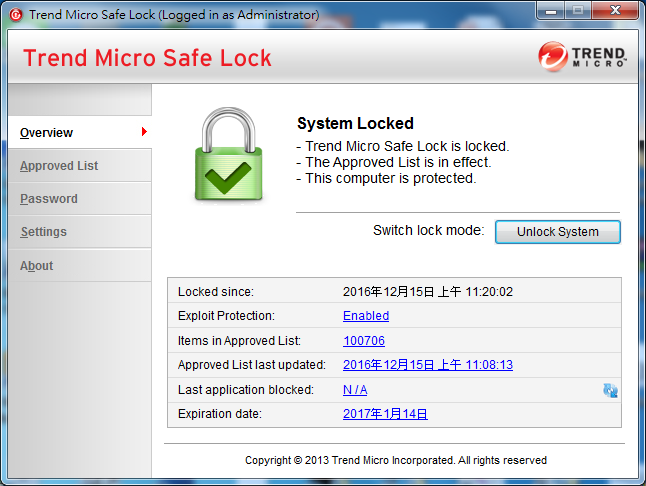
So how to keep ATMs safe and sound? My suggestion is to deploy some security machanism like "Trend Micro SafeLock". It could prevent intrusion and execution of any executable programs not on the whitelist. If you try to run a .exe not on the approved list, Safe Lock will block it and you will see a error message popup as below.
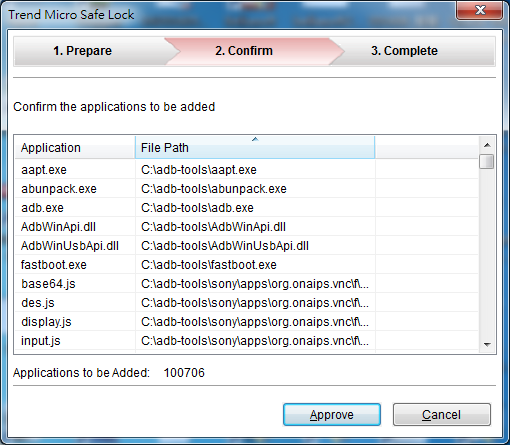
The keypoint is "hash value". Safe Lock will scan and calculate hash values of files in this computer. Administrators could do approved list managemnt easily.
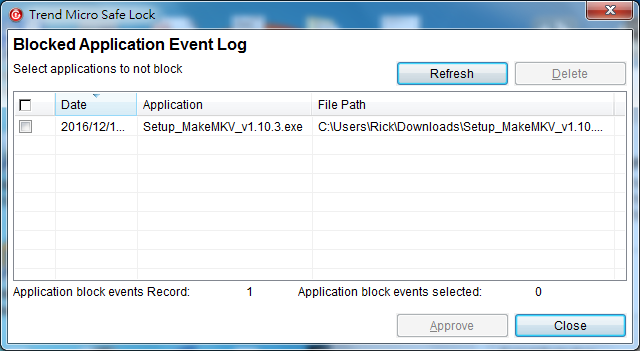
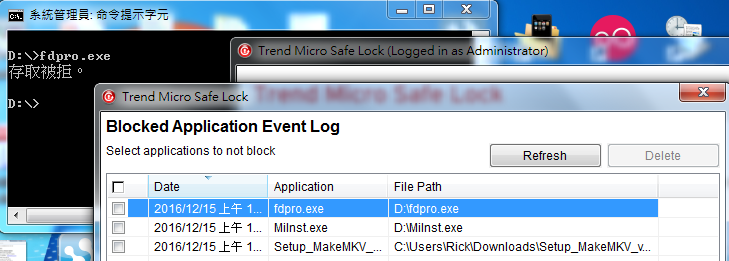
Look at the event log and you could know what suspecious application blocked by Safe Lock, including the applcation name, full path and date.Even the exe running in command prompt could be detected and blocked with fail.