Ubantu中的openssh连接
一、什么是openssh
OpenSSH 是 SSH (Secure SHell) 协议的免费开源实现。SSH协议族
可以用来进行远程控制, 或在计算机之间传送文件。而实现此功能的传统方式,如telnet(终端仿真协议)、 rcp ftp、 rlogin、rsh都是极为不安全的,并且会使用明文传送密码。OpenSSH提供了服务端后台程序和客户端工具,用来加密远程控件和文件传输过程的中的数据,并由此来代替原来的类似服务。
二、openssh版本协议和支持验证类型以及配置文件相关
1、openssh版本协议
openssh V1:存在安装漏洞,现已不再采用
openssh V2:现在推出的RHEL系列版本默认采用的版本协议
2、openssh支持验证类型:
2.1、基于口令的认证
2.2、基于密钥的认证
Note:RHEL默认是安装了openssh(客户端/服务器端并存)并置了开机自启动
[root@lovelace ssh]# rpm -qa | grep openssh;chkconfig --list | grep sshd openssh-server-4.3p2-82.el5 openssh-4.3p2-82.el5 openssh-askpass-4.3p2-82.el5 openssh-clients-4.3p2-82.el5 sshd 0:关闭 1:关闭 2:启用 3:启用 4:启用 5:启用 6:关闭 + + [root@lovelace ssh]# cat /etc/redhat-release Red Hat Enterprise Linux Server release 5.8 (Tikanga)
3、openssh客户端的使用
3.1、ssh –l username [hostname|ip]
由于机器的原因,中间有报错,但不影响结果
[root@lovelace ~]# ssh -l nick 192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: + #输入ifconfig命令,提示没有权限 [nick@nick ~]$ ifconfig eth0 | grep 'inet' -bash: ifconfig: command not found
3.2、ssh [hostname|ip]
如果不指定用户,默认会使用当前系统的当前用户
[root@lovelace ~]# ssh 192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! #我们没有指定用户,默认为root root@192.168.2.29's password: Last login: Fri Jun 7 20:20:09 2013 from 192.168.2.28 [root@nick ~]# ifconfig eth0 | grep 'inet addr' inet addr:192.168.2.29 Bcast:192.168.2.255 Mask:255.255.255.0
我们使用一个普通账户测试下
[lovelace@lovelace ~]$ ssh 192.168.2.29 The authenticity of host '192.168.2.29 (192.168.2.29)' can't be established. RSA key fingerprint is f9:ed:0e:99:f3:cb:85:8b:b6:c3:3b:85:a1:a3:3f:af. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.2.29' (RSA) to the list of known hosts. reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! #让输入密码进行验证 lovelace@192.168.2.29's password: Permission denied, please try again. lovelace@192.168.2.29's password: Permission denied, please try again. lovelace@192.168.2.29's password: Permission denied (publickey,gssapi-with-mic,password).
3.3、ssh username@[hostname|ip]
[lovelace@lovelace ~]$ ssh nick@192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: Permission denied, please try again. nick@192.168.2.29's password: Last login: Fri Jun 7 20:22:24 2013 from 192.168.2.54 [nick@nick ~]$
4、配置文件的讲解
openssh配置文件存放路径:
/etc/ssh
客户端配置文件:ssh_config
服务器端配置文件:sshd_config(对应的脚本文件:/etc/init.d/sshd)
这里我们主要看下sshd_config的配置:
[root@lovelace ssh]# cat sshd_config # $OpenBSD: sshd_config,v 1.73 2005/12/06 22:38:28 reyk Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/local/bin:/bin:/usr/bin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options change a # default value. #端口号设置,默认是22号端口可自定义设置,但是客户端连接的时候后面要跟上端口号 #Port 22 #支持ssh协议类型,默认只开启ssh v2 #Protocol 2,1 Protocol 2 #指定sshd应当使用暗中地址族{any(默认)、inet(仅ipv4)、inet6(仅ipv6)} #AddressFamily any #指定监听的IP网络地址,默认监听所有地址 #ListenAddress 0.0.0.0 #ListenAddress :: + + #设定包含计算机私人密钥的文件 # HostKey for protocol version 1 #HostKey /etc/ssh/ssh_host_key # HostKeys for protocol version 2 #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_dsa_key + + # Lifetime and size of ephemeral version 1 server key #设置多少秒之后自动生成服务器的密钥, #KeyRegenerationInterval 1h #定义服务器密钥的位数 #ServerKeyBits 768 + + # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH #指定日志消息通过那个日志子系统发送 SyslogFacility AUTHPRIV #设定sshd的日志等级 #LogLevel INFO + + # Authentication: #限定用户必须在指定的时间内认证登陆,0表示无限制,默认是120秒 #LoginGraceTime 2m #是否允许管理直接登陆 #PermitRootLogin yes #指定是否要求 sshd(8) 在接受连接请求前对用户主目录和相关的配置文件进行宿主和权限检查 #StrictModes yes #指定每个连接最大允许的认证次数。默认值是 6 #MaxAuthTries 6 + + #设置是否允许只有RSA安全验证 #RSAAuthentication yes #是否允许公钥认证。默认值为”yes” #PubkeyAuthentication yes #存放该用户可以用来登录的 RSA/DSA 公钥。 #AuthorizedKeysFile .ssh/authorized_keys + + #下面是基于主机的认证(不建议使用,不在详解) # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts #RhostsRSAAuthentication no # similar for protocol version 2 #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # RhostsRSAAuthentication and HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes + + # To disable tunneled clear text passwords, change to no here! #基于口令的认证 #PasswordAuthentication yes #是否允许空密码 #PermitEmptyPasswords no PasswordAuthentication yes + + #是否允许质疑-应答(challenge-response)认证(不建议使用) # Change to no to disable s/key passwords #ChallengeResponseAuthentication yes ChallengeResponseAuthentication no + + #Kerberos认证相关 # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no + + # # GSSAPI options #是否允许使用基于 GSSAPI 的用户认证。默认值为”no” #GSSAPIAuthentication no GSSAPIAuthentication yes #是否在用户退出登录后自动销毁用户凭证缓存。默认值是”yes” #GSSAPICleanupCredentials yes GSSAPICleanupCredentials yes + + #PAM认证模块 # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication mechanism. # Depending on your PAM configuration, this may bypass the setting of # PasswordAuthentication, PermitEmptyPasswords, and # "PermitRootLogin without-password". If you just want the PAM account and # session checks to run without PAM authentication, then enable this but set # ChallengeResponseAuthentication=no #UsePAM no UsePAM yes + + # Accept locale-related environment variables AcceptEnv LANG LANGUAGE LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT AcceptEnv LC_IDENTIFICATION LC_ALL #是否允许TCP转发,默认值为”yes” #AllowTcpForwarding yes #GatewayPorts no + #设置是否允许X11转发 #X11Forwarding no X11Forwarding yes #指定 sshd(8) X11 转发的第一个可用的显示区(display)数字。默认值是 10 #X11DisplayOffset 10 #sshd(8) 是否应当将X11转发服务器绑定到本地loopback地址。默认值是”yes” #X11UseLocalhost yes #设置sshd是否在用户登录的时候显示“/etc/motd”中的信息 #PrintMotd yes #指定 sshd(8) 是否在每一次交互式登录时打印最后一位用户的登录时间 默认值是”yes”(强烈不建议启用) #PrintLastLog yes #指定系统是否向客户端发送 TCP keepalive 消息。默认值是”yes” #TCPKeepAlive yes #是否在交互式会话的登录过程中使用 login默认值是”no” #UseLogin no #是否让 sshd(8) 通过创建非特权子进程处理接入请求的方法来进行权限分离 默认值是”yes #UsePrivilegeSeparation yes #PermitUserEnvironment no #是否对通信数据进行加密,还是延迟到认证成功之后再对通信数据加密 可用值:”yes” “delayed”(默认) “no” #Compression delayed #设置一个以秒记的时长,如果超过这么长时间没有收到客户端的任何数据,sshd(8) 将通过安全通道向客户端发送一个”alive”消息,并等候应答。默认值 0 表示不发送”alive”消息 #ClientAliveInterval 0 #Sshd在未收到任何客户端回应前最多允许发送多少个”alive”消息 默认值是 3 #ClientAliveCountMax 3 #ShowPatchLevel no #UseDNS yes #指定在哪个文件中存放SSH守护进程的进程号,默认为 /var/run/sshd.pid 文件 #PidFile /var/run/sshd.pid #最大允许保持多少个未认证的连接 默认值是 10 #MaxStartups 10 #是否允许 tun 设备转发 #PermitTunnel no #ChrootDirectory none + + #是否允许设置欢迎词之类的信息(不建议使用) # no default banner path #Banner /some/path + + #是否允许启动sftp-server # override default of no subsystems Subsystem sftp /usr/libexec/openssh/sftp-server
5、ssh客户端自带的其他功能
5.1、sftp
sftp:类似ftp的工具,既是客户端又是服务器端
#sftp属于哪个安装包 [lovelace@lovelace ~]$ rpm -qf `which sftp` openssh-clients-4.3p2-82.el5 + #和ftp功能一致,只是不需要单独安装 + [lovelace@lovelace ~]$ sftp nick@192.168.2.29 Connecting to 192.168.2.29... reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: sftp> ls sftp> dir sftp> cd /etc sftp> ls DIR_COLORS DIR_COLORS.xterm Muttrc Muttrc.local NetworkManager X11 a2ps-site.cfg a2ps.cfg
5.2、scp
scp:两台主机直接复制数据(加密传送)
scp src dest (和cp用法一样)
参数:
-r 递归目录
-a 针对目录
scp 用户名@主机:/path/to/somefile /path/to/local
scp /path/to/local 用户名@主机:/path/to/somefile
#检查scp在哪个安装包里 [lovelace@lovelace ~]$ rpm -qf `which scp` openssh-clients-4.3p2-82.el5 + #查看当前目录下有哪些文件 [lovelace@lovelace ~]$ ls love name.txt test1 test2 + #拷贝name.txt文件大远程主机的桌面 [lovelace@lovelace ~]$ scp name.txt nick@192.168.2.29:~/ reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: name.txt 100% 42 0.0KB/s 00:00 + #在本地显示远程主机的桌面信息 [lovelace@lovelace ~]$ ssh nick@192.168.2.29 'ls ~;pwd' reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: name.txt /home/nick
5.3、ssh-copy-id
ssh-copy-id:将公钥传送到远程服务器
参数:
-i:指定拷贝文件
#查看ssh-copy-id属于哪个安装包 [lovelace@lovelace ~]$ rpm -qf `which ssh-copy-id` openssh-clients-4.3p2-82.el5<span style="font-family: 宋体, 'Arial Narrow', arial, serif; "> </span>
6、openssh的黑白名单(当白名单好黑名单共存的时候,黑名单失效)
这个在openssh安全的时候再提
7、其他
在本地显示远程主机的相关信息
命令格式:
ssh username@hostname 'command' 或者 ssh -l username hostname 'command'
[lovelace@lovelace ~]$ ssh nick@192.168.2.29 'cat ~/name.txt' reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: nick kale tony jack nick kale who you are [lovelace@lovelace ~]$
三、建立基于密钥的认证
步骤:
1、生成一对密钥
ssh-keygen
参数:
-t:指定加密类型
-f:指定保存在什么文件
-N:跳过私钥密钥认证
2、将公钥传输至服务器端某用户的家目录.ssh/authorized-keys文件中
可以使用ssh-copy-id或者scp来实现
Note:.ssh文件目录权限为700,其他任何值都不行
3、测试登陆
一幅图来表达ssh认证方式的讲解
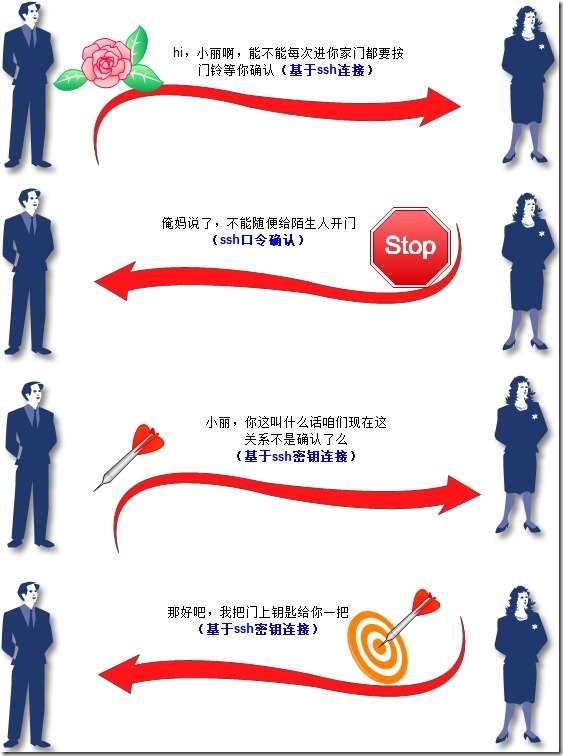
下面来看下具体的操作步骤:
1、生成一对密钥
方法一、
#生成密钥对 [lovelace@lovelace ~]$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/lovelace/.ssh/id_rsa): + #这里需要输入两次密钥验证密码 这里我们不在设置 Enter passphrase (empty for no passphrase): Enter same passphrase again: + #私钥保存路径及文件名 Your identification has been saved in /home/lovelace/.ssh/id_rsa. + #公钥保存路径进文件名 Your public key has been saved in /home/lovelace/.ssh/id_rsa.pub. The key fingerprint is: aa:0e:89:eb:83:55:44:d1:a1:ed:2d:81:aa:4e:47:29 lovelace@lovelace.localdomain
方法二、直接生成,不在询问用户输密码之类的信息
[lovelace@lovelace ~]$ ssh-keygen -t rsa -f .ssh/id_rsa -N '' Generating public/private rsa key pair. Your identification has been saved in .ssh/id_rsa. Your public key has been saved in .ssh/id_rsa.pub. The key fingerprint is: 62:23:24:34:dd:1a:85:2e:61:ca:cd:3d:e4:a1:32:5f lovelace@lovelace.localdomain [lovelace@lovelace ~]$ cd .ssh/;ls id_rsa id_rsa.pub
2、将公钥传输至服务器断某用户的家目录的.ssh/authorized-keys文件中
方法一、使用ssh-copy-id
#传输公钥文件到远程主机 [lovelace@lovelace .ssh]$ ssh-copy-id -i id_rsa.pub nick@192.168.2.29 10 The authenticity of host '192.168.2.29 (192.168.2.29)' can't be established. RSA key fingerprint is f9:ed:0e:99:f3:cb:85:8b:b6:c3:3b:85:a1:a3:3f:af. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.2.29' (RSA) to the list of known hosts. reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! + #这里需要输入一次远程主机对应账户的密码 nick@192.168.2.29's password: Now try logging into the machine, with "ssh 'nick@192.168.2.29'", and check in: .ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting. #查看远程主机桌面下.ssh目录下是否存在authorized_keys文件并查看内容 [lovelace@lovelace .ssh]$ ssh nick@192.168.2.29 'ls ~/.ssh/;cat ~/.ssh/authorized_keys' reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAy6bCpejLIIW+dinNwTrFymT0BNk10gSVqaas9CmdtDNfJdXZNX7IdXUU2xOnKYqcnt9gcTWS1RRP498hWdo/uWiEfBNXfMpzxqinBaW6UGSGG0/vWuviJbWdC9ccF6XYq9yVK831jkBrMAENM+FrKXAwWz8Y3LD6XJIe1TyegrOD1FzrJ6nTNSTUts0lcLwwQv4C8A4Rwks0rme8yirTjcFcAI3vBuoC1IJJhN0RQ7/Sn1Hx5m8t0J1FFFymn29HCEM46ZjMhRdiALkaathMgMLTwWfwi1lmkXBVtGlqM+RusFtlqjSzik2vjT1Rr7XCH4+tcLZxt8Rr4Ju2wpAqGw== lovelace@lovelace.localdomain
方法二、使用scp
#首先删除远程主机上的authorized_keys配置文件 + #登陆到远程主机,这里已经不需要密码验证了 [lovelace@lovelace .ssh]$ scp id_rsa.pub nick@192.168.2.29 [lovelace@lovelace .ssh]$ ssh nick@192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! Last login: Fri Jun 7 20:29:09 2013 from 192.168.2.54 [nick@nick ~]$ cd .ssh/ [nick@nick .ssh]$ ls authorized_keys + #清空authorized_keys [nick@nick .ssh]$ echo >authorized_keys [nick@nick .ssh]$ cat authorized_keys
#拷贝公钥到远程主机上,由于我们清空了远程主机上的authorized_keys 文件这里需要重新密码认证 [lovelace@lovelace .ssh]$ scp id_rsa.pub nick@192.168.2.29:~/ reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: id_rsa.pub 100% 411 0.4KB/s 00:00 + #登陆到远程主机 [lovelace@lovelace .ssh]$ ssh nick@192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! nick@192.168.2.29's password: Last login: Fri Jun 7 21:18:06 2013 from 192.168.2.54 [nick@nick ~]$ ls id_rsa.pub name.txt + #把公钥信息添加到authorized_keys 配置文件中去 [nick@nick ~]$ cat id_rsa.pub >>.ssh/authorized_keys + #查看文件内容 [nick@nick ~]$ cat .ssh/authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAy6bCpejLIIW+dinNwTrFymT0BNk10gSVqaas9CmdtDNfJdXZNX7IdXUU2xOnKYqcnt9gcTWS1RRP498hWdo/uWiEfBNXfMpzxqinBaW6UGSGG0/vWuviJbWdC9ccF6XYq9yVK831jkBrMAENM+FrKXAwWz8Y3LD6XJIe1TyegrOD1FzrJ6nTNSTUts0lcLwwQv4C8A4Rwks0rme8yirTjcFcAI3vBuoC1IJJhN0RQ7/Sn1Hx5m8t0J1FFFymn29HCEM46ZjMhRdiALkaathMgMLTwWfwi1lmkXBVtGlqM+RusFtlqjSzik2vjT1Rr7XCH4+tcLZxt8Rr4Ju2wpAqGw== lovelace@lovelace.localdomain
3、测试登陆
#进行登陆远程主机测试 [lovelace@lovelace .ssh]$ ssh nick@192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! Last login: Fri Jun 7 21:23:35 2013 from 192.168.2.54 [nick@nick ~]$ exit logout Connection to 192.168.2.29 closed. + #进行登录远程主机测试 [lovelace@lovelace .ssh]$ ssh -l nick 192.168.2.29 reverse mapping checking getaddrinfo for . failed - POSSIBLE BREAK-IN ATTEMPT! Last login: Fri Jun 7 21:27:47 2013 from 192.168.2.54 [nick@nick ~]$
四、安全总结:
话说没有绝对的安全可言,但是相对于常规性的安全漏洞,我们还是要尽可能避免的。
关于验证安装这块:
1、密码周期性更换且足够复杂
2、使用非默认端口
3、限制登陆客户地址
4、限制管理直接登陆
5、仅运行有限用户登陆
6、使用基于密钥的认证
7、不要使用协议版本1
五、配置文件的讲解
openssh配置文件存放路径:
/etc/ssh
客户端配置文件:ssh_config
服务器端配置文件:sshd_config(对应的脚本文件:/etc/init.d/sshd)
这里我们主要看下sshd_config的配置:
[root@lovelace ssh]# cat sshd_config # $OpenBSD: sshd_config,v 1.73 2005/12/06 22:38:28 reyk Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/local/bin:/bin:/usr/bin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options change a # default value. #端口号设置,默认是22号端口可自定义设置,但是客户端连接的时候后面要跟上端口号 #Port 22 #支持ssh协议类型,默认只开启ssh v2 #Protocol 2,1 Protocol 2 #指定sshd应当使用暗中地址族{any(默认)、inet(仅ipv4)、inet6(仅ipv6)} #AddressFamily any #指定监听的IP网络地址,默认监听所有地址 #ListenAddress 0.0.0.0 #ListenAddress :: + + #设定包含计算机私人密钥的文件 # HostKey for protocol version 1 #HostKey /etc/ssh/ssh_host_key # HostKeys for protocol version 2 #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_dsa_key + + # Lifetime and size of ephemeral version 1 server key #设置多少秒之后自动生成服务器的密钥, #KeyRegenerationInterval 1h #定义服务器密钥的位数 #ServerKeyBits 768 + + # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH #指定日志消息通过那个日志子系统发送 SyslogFacility AUTHPRIV #设定sshd的日志等级 #LogLevel INFO + + # Authentication: #限定用户必须在指定的时间内认证登陆,0表示无限制,默认是120秒 #LoginGraceTime 2m #是否允许管理直接登陆 #PermitRootLogin yes #指定是否要求 sshd(8) 在接受连接请求前对用户主目录和相关的配置文件进行宿主和权限检查 #StrictModes yes #指定每个连接最大允许的认证次数。默认值是 6 #MaxAuthTries 6 + + #设置是否允许只有RSA安全验证 #RSAAuthentication yes #是否允许公钥认证。默认值为”yes” #PubkeyAuthentication yes #存放该用户可以用来登录的 RSA/DSA 公钥。 #AuthorizedKeysFile .ssh/authorized_keys + + #下面是基于主机的认证(不建议使用,不在详解) # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts #RhostsRSAAuthentication no # similar for protocol version 2 #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # RhostsRSAAuthentication and HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes + + # To disable tunneled clear text passwords, change to no here! #基于口令的认证 #PasswordAuthentication yes #是否允许空密码 #PermitEmptyPasswords no PasswordAuthentication yes + + #是否允许质疑-应答(challenge-response)认证(不建议使用) # Change to no to disable s/key passwords #ChallengeResponseAuthentication yes ChallengeResponseAuthentication no + + #Kerberos认证相关 # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no + + # # GSSAPI options #是否允许使用基于 GSSAPI 的用户认证。默认值为”no” #GSSAPIAuthentication no GSSAPIAuthentication yes #是否在用户退出登录后自动销毁用户凭证缓存。默认值是”yes” #GSSAPICleanupCredentials yes GSSAPICleanupCredentials yes + + #PAM认证模块 # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication mechanism. # Depending on your PAM configuration, this may bypass the setting of # PasswordAuthentication, PermitEmptyPasswords, and # "PermitRootLogin without-password". If you just want the PAM account and # session checks to run without PAM authentication, then enable this but set # ChallengeResponseAuthentication=no #UsePAM no UsePAM yes + + # Accept locale-related environment variables AcceptEnv LANG LANGUAGE LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT AcceptEnv LC_IDENTIFICATION LC_ALL #是否允许TCP转发,默认值为”yes” #AllowTcpForwarding yes #GatewayPorts no + #设置是否允许X11转发 #X11Forwarding no X11Forwarding yes #指定 sshd(8) X11 转发的第一个可用的显示区(display)数字。默认值是 10 #X11DisplayOffset 10 #sshd(8) 是否应当将X11转发服务器绑定到本地loopback地址。默认值是”yes” #X11UseLocalhost yes #设置sshd是否在用户登录的时候显示“/etc/motd”中的信息 #PrintMotd yes #指定 sshd(8) 是否在每一次交互式登录时打印最后一位用户的登录时间 默认值是”yes”(强烈不建议启用) #PrintLastLog yes #指定系统是否向客户端发送 TCP keepalive 消息。默认值是”yes” #TCPKeepAlive yes #是否在交互式会话的登录过程中使用 login默认值是”no” #UseLogin no #是否让 sshd(8) 通过创建非特权子进程处理接入请求的方法来进行权限分离 默认值是”yes #UsePrivilegeSeparation yes #PermitUserEnvironment no #是否对通信数据进行加密,还是延迟到认证成功之后再对通信数据加密 可用值:”yes” “delayed”(默认) “no” #Compression delayed #设置一个以秒记的时长,如果超过这么长时间没有收到客户端的任何数据,sshd(8) 将通过安全通道向客户端发送一个”alive”消息,并等候应答。默认值 0 表示不发送”alive”消息 #ClientAliveInterval 0 #Sshd在未收到任何客户端回应前最多允许发送多少个”alive”消息 默认值是 3 #ClientAliveCountMax 3 #ShowPatchLevel no #UseDNS yes #指定在哪个文件中存放SSH守护进程的进程号,默认为 /var/run/sshd.pid 文件 #PidFile /var/run/sshd.pid #最大允许保持多少个未认证的连接 默认值是 10 #MaxStartups 10 #是否允许 tun 设备转发 #PermitTunnel no #ChrootDirectory none + + #是否允许设置欢迎词之类的信息(不建议使用) # no default banner path #Banner /some/path + + #是否允许启动sftp-server # override default of no subsystems Subsystem sftp /usr/libexec/openssh/sftp-server