一、修改SElinux的状态
#sestatus --查看状态 #setenforce 0 --临时修改 #setenforce 1 #getenforce #vim /etc/selinux/config --通过配置文件修改 SELINUX=Enforcing #systemctl reboot --重启生效 #getenforce
二、文件的上下文
#setenforce 1
#yum install -y httpd
#mkdir /local
#echo lxjtest > /local/index.html
#ln -s /local/ /var/www/html/soft
[root@rhel1 html]# ll -Z /local/index.html -rw-r--r--. root root unconfined_u:object_r:default_t:s0 /local/index.html [root@rhel1 html]# ll -Z /var/www/ drwxr-xr-x. root root system_u:object_r:httpd_sys_script_exec_t:s0 cgi-bin drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 html
修改文件上下文的三种方法:
方法1:修改/local目录的的fcontext为httpd_sys_content_t
#semanage fcontext -l | grep http
#chcon -R -t httpd_sys_content_t /local/
方法2:
修改/local目录的的fcontext为跟/var/www目录一致
#chcon -R --reference /var/www/ /local/
方法3:
#semanage fcontext -a -t httpd_sys_content_t '/local(/.*)?'
#restorecon -FRv /local
# man semanage fcontext
#推荐使用第3钟方法,文件夹上下文类型将写入内核
在RHEL2上访问测试:
#setenforce 1
http://192.168.100.1/soft #未在RHEL1修改上下文,访问会被Forbidden,修改正确后可访问
实验一、端口的上下文
#查看端口的上下文
#semanage port -l | grep http
#添加端口的上下文
#semanage port -a -t http_port_t -p tcp 8899
#删除端口的上下文
#semanage port -d -t http_port_t -p tcp 8899
#修改端口的上下文
#semanage port -m -t http_port_t -p tcp 8899
#修改防火墙
#firewall-cmd --permanent --add-port=8899/tcp
#firewall-cmd --reload
#修改httpd配置文件,以监听8899端口
#vim /etc/httpd/conf/httpd.conf
Listen 8899 #增加
#mkdir /var/www/8899
#echo 8899 > /var/www/8899/index.html
#vim /etc/httpd/conf.d/0.conf
< VirtualHost 192.168.100.1:80> DocumentRoot "/var/www/html" ServerName 192.168.100.1 < /VirtualHost> < VirtualHost 192.168.100.1:8899> DocumentRoot "/var/www/8899" ServerName 192.168.100.1 < /VirtualHost>
#systemctl restart httpd
在rhel1和rhel2上访问测试:
http://192.168.100.1
http://192.168.100.1:8899
实验二、布尔值
使用SElinux图形画界面来配置selinux
#yum provides system-config-selinux
#yum install -y policycoreutils-gui-2.2.5-11.el7.x86_64
#system-config-selinux 打开SElinux图形界面
例:
#yum install -y samba
#getsebool -a
#getsebool -a | grep samba
#setsebool -P samba_enable_home_dir on
#setsebool -P samba_export_all_rw on
-a 列出
-P 永久生效permanent
实验三、SElinux在网络各服务中的配置
man selinux
常见有一些服务的SElinux配置
===ftp===
//If you want to share files anonymously <如果你想把这个共享给匿名的话,需要开启以下>
chcon -R -t public_content_t /var/ftp
//If you want to setup a directory where you can upload files
<如果你想让你设置的FTP目录可以上传文件的话,SELINUX需要设置>
chcon -t public_content_rw_t /var/ftp/incoming
//You must also turn on the boolean allow_ftpd_anon_write <允许匿名用户写入权限>
setsebool -P allow_ftpd_anon_write=1
//If you are setting up this machine as a ftpd server and wish to allow users to access their home directorories<如果你希望你的FTP用户可以访问自己的家目录的话,需要开启>
setsebool -P ftp_home_dir 1
//If you want to run ftpd as a daemon<如果你希望将vsftpd以daemon的方式运行的话,需要开启>
setsebool -P ftpd_is_daemon 1
//You can disable SELinux protection for the ftpd daemon<你可以让SElinux停止保护vsftpd的daemon方式动行>
setsebool -P ftpd_disable_trans 1
===httpd===
//If you want a particular domain to write to the public_content_rw_t domain
< 如果希望具体个doman具有可写权限的话,需要设置>
setsebool -P allow_httpd_anon_write=1
or
setsebool -P allow_httpd_sys__anon_write=1
//httpd can be setup to allow cgi s to be executed <HTTP被设置允许cgi的设置>
setsebool -P httpd_enable_cgi 1
//If you want to allow access to users home directories<允许用户HHTP访问其家目录,该设定限仅于用户的家目录主页>
setsebool -P httpd_enable_homedirs 1
chcon -R -t httpd_sys_content_t ~user/public_html
//httpd is allowed access to the controling terminal<允许httpd访问终端>
setsebool -P httpd_tty_comm 1
//such that one httpd service can not interfere with another
setsebool -P httpd_unified 0
//loadable modules run under the same context as httpd
setsebool -P httpd_builtin_ing 0
//httpd s are allowed to connect out to the network
setsebool -P httpd_can_network_connect 1
// You can disable suexec transition
setsebool -P httpd_suexec_disable_trans 1
//You can disable SELinux protection for the httpd daemon by executing <关闭Selinux的关于httpd进程守护的保护>
setsebool -P httpd_disable_trans 1
service httpd restart
===named===
//If you want to have named update the master zone files <关于named,master更新selinux设定>
setsebool -P named_write_master_zones 1
//You can disable SELinux protection for the named daemon by executing
< 关闭named的进程守护保护>
setsebool -P named_disable_trans 1
service named restart
===nfs===
//If you want to setup this machine to share nfs partitions read only
< Selinux将本机的NFS共享设置成只读>
setsebool -P nfs_export_all_ro 1
//If you want to share files read/write<Selinux将本机的NFS共享设置成可读可写>
setsebool -P nfs_export_all_rw 1
//If you want to use a remote NFS server for the home directories on this machine
<如果你想要将远程NFS的家目录共享到本机,需要开启>
setsebool -P use_nfs_home_dirs 1
===samba===
//If you want to share files other than home directorie
< 如果你希望将目录共享给其他用户,你需要设置>
chcon -t samba_share_t /directory
//If you want to share files with multiple domains
如果samba服务器共享目录给多个域,则需要:
setsebool -P allow_smbd_anon_write=1
//If you are setting up this machine as a Samba server and wish to share the home directories
samba服务器要共享家目录时:
setsebool -P samba_enable_home_dirs 1
//If you want to use a remote Samba server for the home directories on this machine
如果你需在本机上使用远程samba服务器的家目录
setsebool -P use_samba_home_dirs 1
//You can disable SELinux protection for the samba daemon by executing
关闭selinux关于samba的进程守护的保护
setsebool -P smbd_disable_trans 1
service smb restart
===rsync===
//If you want to share files using the rsync daemon
共享rsync目录时:
chcon -t public_content_t /directories
//If you want to share files with multiple domains
允许其他用户写入时
setsebool -P allow_rsync_anon_write=1
//You can disable SELinux protection for the rsync daemon by executing
停止rsync的进程保护
setsebool -P rsync_disable_trans 1
===kerberos===
//allow your system to work properly in a Kerberos environment
允许系统使用kerberos
setsebool -P allow_kerberos 1
//If you are running Kerberos daemons kadmind or krb5kdc
setsebool -P krb5kdc_disable_trans 1
service krb5kdc restart
setsebool -P kadmind_disable_trans 1
service kadmind restart
===nis===
Allow your system to work properly in a NIS environment
系统工作在nis环境时
setsebool -P allow_ypbind 1
实验四、selinux的troubleshoot
关闭SElinux问题直接解决说明很可能是SElinux的问题
方法一
如果SElinux阻止了某项服务,可以先设置SElinux为permissive模式,然后查看日志
方法二
#service auditd restart
#tail -f /var/log/message
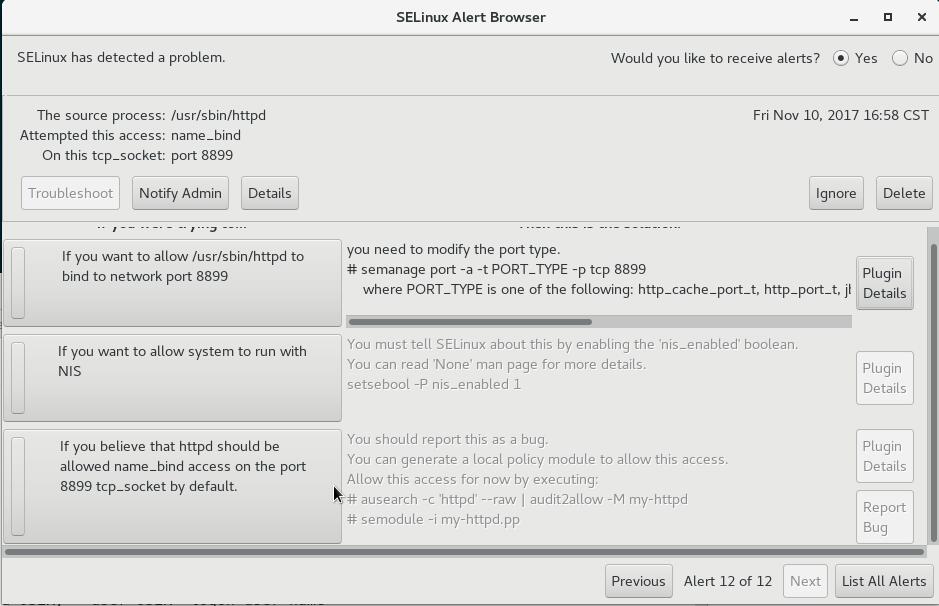
Nov 10 16:58:13 rhel2 setroubleshoot: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 8899.
For complete SELinux messages run: sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b Nov 10 16:58:13 rhel2 python: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 8899.#012#012*****
Plugin bind_ports (92.2 confidence) suggests ************************#012#012If you want to allow /usr/sbin/httpd to bind to network port 8899
#012Then you need to modify the port type.#012Do#012# semanage port -a -t PORT_TYPE -p tcp 8899#012
where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t.
#012#012***** Plugin catchall_boolean (7.83 confidence) suggests ******************#012#012If you want to allow nis to enabled
#012Then you must tell SELinux about this by enabling the 'nis_enabled' boolean.#012You can read 'None' man page for more details.
#012Do#012setsebool -P nis_enabled 1#012#012***** Plugin catchall (1.41 confidence) suggests **************************
#012#012If you believe that httpd should be allowed name_bind access on the port 8899 tcp_socket by default.
#012Then you should report this as a bug.#012You can generate a local policy module to allow this access.
#012Do#012allow this access for now by executing:#012# ausearch -c 'httpd' --raw | audit2allow -M my-httpd#012
# semodule -i my-httpd.pp#012
#sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b
[root@rhel2 ~]# sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port 8899. ***** Plugin bind_ports (92.2 confidence) suggests ************************ If you want to allow /usr/sbin/httpd to bind to network port 8899 Then you need to modify the port type. Do # semanage port -a -t PORT_TYPE -p tcp 8899 where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t. ***** Plugin catchall_boolean (7.83 confidence) suggests ****************** If you want to allow system to run with NIS Then you must tell SELinux about this by enabling the 'nis_enabled' boolean. You can read 'None' man page for more details. Do setsebool -P nis_enabled 1 ***** Plugin catchall (1.41 confidence) suggests ************************** If you believe that httpd should be allowed name_bind access on the port 8899 tcp_socket by default. Then you should report this as a bug. You can generate a local policy module to allow this access. Do allow this access for now by executing: # ausearch -c 'httpd' --raw | audit2allow -M my-httpd # semodule -i my-httpd.pp Additional Information: Source Context system_u:system_r:httpd_t:s0 Target Context system_u:object_r:unreserved_port_t:s0 Target Objects port 8899 [ tcp_socket ] Source httpd Source Path /usr/sbin/httpd Port 8899 Host rhel2.rusky.com Source RPM Packages httpd-2.4.6-67.el7.x86_64 Target RPM Packages Policy RPM selinux-policy-3.13.1-166.el7.noarch Selinux Enabled True Policy Type targeted Enforcing Mode Enforcing Host Name rhel2.rusky.com Platform Linux rhel2.rusky.com 3.10.0-693.el7.x86_64 #1 SMP Thu Jul 6 19:56:57 EDT 2017 x86_64 x86_64 Alert Count 4 First Seen 2017-11-10 16:49:42 CST Last Seen 2017-11-10 16:58:12 CST Local ID 477211dd-4f0a-4c46-a295-7eef08bf545b Raw Audit Messages type=AVC msg=audit(1510304292.2:1743): avc: denied { name_bind } for pid=12009 comm="httpd" src=8899 scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:unreserved_port_t:s0 tclass=tcp_socket type=SYSCALL msg=audit(1510304292.2:1743): arch=x86_64 syscall=bind success=no exit=EACCES a0=5 a1=55cf7ca992e8 a2=10 a3=7ffca3c9125c items=0 ppid=1 pid=12009 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm=httpd exe=/usr/sbin/httpd subj=system_u:system_r:httpd_t:s0 key=(null) Hash: httpd,httpd_t,unreserved_port_t,tcp_socket,name_bind
#sealert -b --通过图形化界面troubleshooting
方法三
audit2why < /var/log/audit/audit.log
audit2allow < /var/log/audit/audit.log