k8s-自带监控metrics-server
1. k8s-自带监控metrics-server
-
查看资源集群状态
-
查看master组件状态:
kubectl get cs -
查看node状态:
kubectl get node -
查看Apiserver代理的URL:
kubectl cluster-info -
查看集群详细信息:
kubectl cluster-info dump -
查看资源信息:
kubectl describe <资源> <名称> -
查看资源信息:
kubectl get <资源>
-
-
监控集群资源利用率
-
查看node资源消耗
kubectl top node <node name> -
查看pod资源消耗
kubectl top pod <pod name>
执行时会提示错误:error: Metrics API not available
这是因为这个命令需要由metric-server服务提供数据,而这个服务默认没有安装,还需要手动部署下。
-
-
Metrics-server 工作流程图
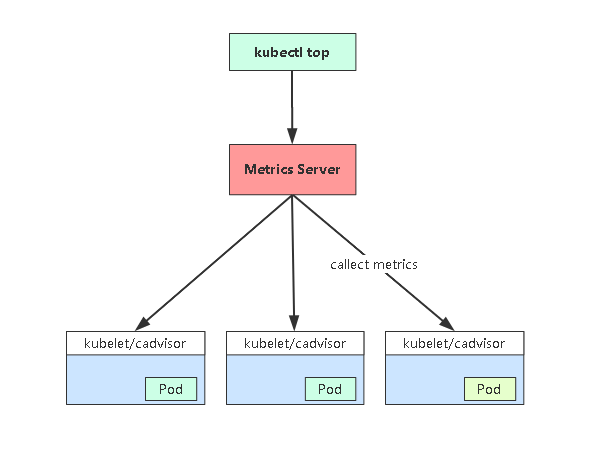
- Metrics Server是一个集群范围的资源使用情况的数据聚合器。作为一个应用部署在集群中。Metric server从每个节点上KubeletAPI收集指标,通过Kubernetes聚合器注册在Master APIServer中。
- 为集群提供Node、Pods资源利用率指标
- 项目地址:https://github.com/kubernetes-sigs/metrics-server
-
Metrics-server 部署
-
官网下载地址:https://github.com/kubernetes-sigs/metrics-server/releases/download/v0.3.7/components.yaml
-
示例代码
[root@k8s-master01 ~]# vim metrics-server.yaml [root@k8s-master01 ~]# cat metrics-server.yaml --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: system:aggregated-metrics-reader labels: rbac.authorization.k8s.io/aggregate-to-view: "true" rbac.authorization.k8s.io/aggregate-to-edit: "true" rbac.authorization.k8s.io/aggregate-to-admin: "true" rules: - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: metrics-server:system:auth-delegator roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: system:auth-delegator subjects: - kind: ServiceAccount name: metrics-server namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: metrics-server-auth-reader namespace: kube-system roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: extension-apiserver-authentication-reader subjects: - kind: ServiceAccount name: metrics-server namespace: kube-system --- apiVersion: apiregistration.k8s.io/v1 kind: APIService metadata: name: v1beta1.metrics.k8s.io spec: service: name: metrics-server namespace: kube-system group: metrics.k8s.io version: v1beta1 insecureSkipTLSVerify: true groupPriorityMinimum: 100 versionPriority: 100 --- apiVersion: v1 kind: ServiceAccount metadata: name: metrics-server namespace: kube-system --- apiVersion: apps/v1 kind: Deployment metadata: name: metrics-server namespace: kube-system labels: k8s-app: metrics-server spec: selector: matchLabels: k8s-app: metrics-server template: metadata: name: metrics-server labels: k8s-app: metrics-server spec: serviceAccountName: metrics-server volumes: # mount in tmp so we can safely use from-scratch images and/or read-only containers - name: tmp-dir emptyDir: {} containers: - name: metrics-server image: lizhenliang/metrics-server:v0.3.7 imagePullPolicy: IfNotPresent args: - --cert-dir=/tmp - --secure-port=4443 - --kubelet-insecure-tls - --kubelet-preferred-address-types=InternalIP ports: - name: main-port containerPort: 4443 protocol: TCP securityContext: readOnlyRootFilesystem: true runAsNonRoot: true runAsUser: 1000 volumeMounts: - name: tmp-dir mountPath: /tmp nodeSelector: kubernetes.io/os: linux kubernetes.io/arch: "amd64" --- apiVersion: v1 kind: Service metadata: name: metrics-server namespace: kube-system labels: kubernetes.io/name: "Metrics-server" kubernetes.io/cluster-service: "true" spec: selector: k8s-app: metrics-server ports: - port: 443 protocol: TCP targetPort: main-port --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: system:metrics-server rules: - apiGroups: - "" resources: - pods - nodes - nodes/stats - namespaces - configmaps verbs: - get - list - watch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: system:metrics-server roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: system:metrics-server subjects: - kind: ServiceAccount name: metrics-server namespace: kube-system -
运行配置文件
[root@k8s-master01 ~]# kubectl apply -f metrics-server.yaml clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created serviceaccount/metrics-server created deployment.apps/metrics-server created service/metrics-server created clusterrole.rbac.authorization.k8s.io/system:metrics-server created clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created -
检查是否部署成功
[root@k8s-master01 ~]# kubectl get apiservices |grep metrics kubectl get --raw /apis/metrics.k8s.io/v1beta1/nodesv1beta1.metrics.k8s.io kube-system/metrics-server True 5m58s [root@k8s-master01 ~]# kubectl get --raw /apis/metrics.k8s.io/v1beta1/nodes {"kind":"NodeMetricsList","apiVersion":"metrics.k8s.io/v1beta1","metadata":{"selfLink":"/apis/metrics.k8s.io/v1beta1/nodes"},"items":[{"metadata":{"name":"k8s-node01","selfLink":"/apis/metrics.k8s.io/v1beta1/nodes/k8s-node01","creationTimestamp":"2021-08-31T08:47:28Z"},"timestamp":"2021-08-31T08:46:28Z","window":"30s","usage":{"cpu":"74966621n","memory":"1476144Ki"}},{"metadata":{"name":"k8s-node02","selfLink":"/apis/metrics.k8s.io/v1beta1/nodes/k8s-node02","creationTimestamp":"2021-08-31T08:47:28Z"},"timestamp":"2021-08-31T08:46:33Z","window":"30s","usage":{"cpu":"64642735n","memory":"1883488Ki"}},{"metadata":{"name":"k8s-master01","selfLink":"/apis/metrics.k8s.io/v1beta1/nodes/k8s-master01","creationTimestamp":"2021-08-31T08:47:28Z"},"timestamp":"2021-08-31T08:46:30Z","window":"30s","usage":{"cpu":"107193694n","memory":"2307884Ki"}}]}如果状态True并能返回数据说明Metrics Server服务工作正常。
-