由于测试原因,要涉及到将windows机器加入到ldap域,所以查看各种文档进行ldap-pdc域的搭建,并成功将windows 2008r2加入到ldap-pdc域中。下面简单记录一下搭建过程
Linux : CentOS7.4.1708 ip:10.2.48.125
Windows : Windows 2008 R2 ip:10.2.48.86
配置了163yum源,并且把seLinux关闭
先安装openldap 和 samba
1 yum install openldap openldap-clients openldap-servers migrationtools samba
更改配置文件
1 cp /usr/share/doc/samba-4.7.1/LDAP/samba.ldif /etc/openldap/schema/ 2 cp /usr/share/openldap-servers/slapd.ldif /home/
生成ldap的管理密码slappasswd
1 [root@ldap-pdc ~]# slappasswd 2 New password: 3 Re-enter new password: 4 {SSHA}sGQJ/b8qamHOmbbBxdxUldfxm3R6ODIj
将slapd.ldif中的dc=my-doamin,dc=com修改为自己的域名,例如我的dc=ldap-pdc,dc=com,并添加部分配置文件,贴出配置文件,标红的位置需要修改
1 # 2 # See slapd-config(5) for details on configuration options. 3 # This file should NOT be world readable. 4 # 5 6 dn: cn=config 7 objectClass: olcGlobal 8 cn: config 9 olcArgsFile: /var/run/openldap/slapd.args 10 olcPidFile: /var/run/openldap/slapd.pid 11 # 12 # TLS settings 13 # 14 olcTLSCACertificatePath: /etc/openldap/certs 15 olcTLSCertificateFile: "OpenLDAP Server" 16 olcTLSCertificateKeyFile: /etc/openldap/certs/password 17 # 18 # Do not enable referrals until AFTER you have a working directory 19 # service AND an understanding of referrals. 20 # 21 #olcReferral: ldap://root.openldap.org 22 # 23 # Sample security restrictions 24 # Require integrity protection (prevent hijacking) 25 # Require 112-bit (3DES or better) encryption for updates 26 # Require 64-bit encryption for simple bind 27 # 28 #olcSecurity: ssf=1 update_ssf=112 simple_bind=64 29 30 31 # 32 # Load dynamic backend modules: 33 # - modulepath is architecture dependent value (32/64-bit system) 34 # - back_sql.la backend requires openldap-servers-sql package 35 # - dyngroup.la and dynlist.la cannot be used at the same time 36 # 37 38 #dn: cn=module,cn=config 39 #objectClass: olcModuleList 40 #cn: module 41 #olcModulepath: /usr/lib/openldap 42 #olcModulepath: /usr/lib64/openldap 43 #olcModuleload: accesslog.la 44 #olcModuleload: auditlog.la 45 #olcModuleload: back_dnssrv.la 46 #olcModuleload: back_ldap.la 47 #olcModuleload: back_mdb.la 48 #olcModuleload: back_meta.la 49 #olcModuleload: back_null.la 50 #olcModuleload: back_passwd.la 51 #olcModuleload: back_relay.la 52 #olcModuleload: back_shell.la 53 #olcModuleload: back_sock.la 54 #olcModuleload: collect.la 55 #olcModuleload: constraint.la 56 #olcModuleload: dds.la 57 #olcModuleload: deref.la 58 #olcModuleload: dyngroup.la 59 #olcModuleload: dynlist.la 60 #olcModuleload: memberof.la 61 #olcModuleload: pcache.la 62 #olcModuleload: ppolicy.la 63 #olcModuleload: refint.la 64 #olcModuleload: retcode.la 65 #olcModuleload: rwm.la 66 #olcModuleload: seqmod.la 67 #olcModuleload: smbk5pwd.la 68 #olcModuleload: sssvlv.la 69 #olcModuleload: syncprov.la 70 #olcModuleload: translucent.la 71 #olcModuleload: unique.la 72 #olcModuleload: valsort.la 73 # 74 # Schema settings 75 # 76 77 dn: cn=schema,cn=config 78 objectClass: olcSchemaConfig 79 cn: schema 80 81 include: file:///etc/openldap/schema/core.ldif 82 include: file:///etc/openldap/schema/corba.ldif 83 include: file:///etc/openldap/schema/cosine.ldif 84 include: file:///etc/openldap/schema/duaconf.ldif 85 include: file:///etc/openldap/schema/dyngroup.ldif 86 include: file:///etc/openldap/schema/inetorgperson.ldif 87 include: file:///etc/openldap/schema/java.ldif 88 include: file:///etc/openldap/schema/misc.ldif 89 include: file:///etc/openldap/schema/nis.ldif 90 include: file:///etc/openldap/schema/openldap.ldif 91 include: file:///etc/openldap/schema/ppolicy.ldif 92 include: file:///etc/openldap/schema/collective.ldif 93 include: file:///etc/openldap/schema/samba.ldif 94 95 96 97 # 98 # Frontend settings 99 # 100 101 dn: olcDatabase=frontend,cn=config 102 objectClass: olcDatabaseConfig 103 objectClass: olcFrontendConfig 104 olcDatabase: frontend 105 # 106 # Sample global access control policy: 107 # Root DSE: allow anyone to read it 108 # Subschema (sub)entry DSE: allow anyone to read it 109 # Other DSEs: 110 # Allow self write access 111 # Allow authenticated users read access 112 # Allow anonymous users to authenticate 113 # 114 #olcAccess: to dn.base="" by * read 115 #olcAccess: to dn.base="cn=Subschema" by * read 116 #olcAccess: to * 117 # by self write 118 # by users read 119 # by anonymous auth 120 # 121 # if no access controls are present, the default policy 122 # allows anyone and everyone to read anything but restricts 123 # updates to rootdn. (e.g., "access to * by * read") 124 # 125 # rootdn can always read and write EVERYTHING! 126 # 127 128 # 129 # Configuration database 130 # 131 132 dn: olcDatabase=config,cn=config 133 objectClass: olcDatabaseConfig 134 olcDatabase: config 135 olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c 136 n=auth" manage by * none 137 138 # 139 # Server status monitoring 140 # 141 dn: olcDatabase=monitor,cn=config 142 objectClass: olcDatabaseConfig 143 olcDatabase: monitor 144 olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c 145 n=auth" read by dn.base="cn=Manager,dc=ldap-pdc,dc=com" read by * none 146 147 # 148 # Backend database definitions 149 # 150 151 dn: olcDatabase=hdb,cn=config 152 objectClass: olcDatabaseConfig 153 objectClass: olcHdbConfig 154 olcDatabase: hdb 155 olcSuffix: dc=ldap-pdc,dc=com 156 olcRootDN: cn=Manager,dc=ldap-pdc,dc=com 157 olcDbDirectory: /var/lib/ldap 158 olcDbIndex: objectClass eq,pres 159 olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub 160 olcRootPW: {SSHA}CC+i80oqumZigXsWtKf4PJFHEfmyUtTd #密码前边是TAB贱,注意不要留空格
执行命令
1 rm -rf /etc/openldap/slapd.d/* 2 slapadd -F /etc/openldap/slapd.d/ -n 0 -l /home/slapd.ldif 3 slaptest -u -F /etc/openldap/slapd.d/
当出现
1 [root@ldap-pdc home]# slaptest -u -F /etc/openldap/slapd.d/ 2 config file testing succeeded 3 [root@ldap-pdc home]#
代表配置文件没有问题。可以往下进行
执行命令
1 chown -Rv ldap.ldap /etc/openldap/slapd.d 2 cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG 3 chown -Rv ldap.ldap /var/lib/ldap/DB_CONFIG 4 systemctl start slapd.service
当显示
1 [root@ldap-pdc home]# systemctl status slapd.service 2 ● slapd.service - OpenLDAP Server Daemon 3 Loaded: loaded (/usr/lib/systemd/system/slapd.service; disabled; vendor preset: disabled) 4 Active: active (running) since Wed 2018-06-06 11:18:27 CST; 1 day 8h ago 5 Docs: man:slapd 6 man:slapd-config 7 man:slapd-hdb 8 man:slapd-mdb 9 file:///usr/share/doc/openldap-servers/guide.html 10 Process: 1218 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS) 11 Process: 1180 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS) 12 Main PID: 1220 (slapd) 13 CGroup: /system.slice/slapd.service 14 └─1220 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:///
生成基本的ldap数据
1 vim /usr/share/migrationtools/migrate_common.ph 2 3 # Default DNS domain 4 $DEFAULT_MAIL_DOMAIN = "ldap-pdc.com"; 5 6 # Default base 7 $DEFAULT_BASE = "dc=ldap-pdc,dc=com"; 8 9 10 chmod +x /usr/share/migrationtools/migrate_common.ph 11 /usr/share/migrationtools/migrate_base.pl > /root/base.ldif 12 /usr/share/migrationtools/migrate_passwd.pl /etc/passwd /root/user.ldif 13 /usr/share/migrationtools/migrate_group.pl /etc/group /root/group.ldif
在bash.ldif和user.ldif以及group.ldif文件中删除与ldap无关的信息,之后进行数据的导入
1 ldapadd -D "cn=Manager,dc=ldap-pdc,dc=com" -W -x -f base.ldif 2 ldapadd -D "cn=Manager,dc=ldap-pdc,dc=com" -W -x -f group.ldif 3 ldapadd -D "cn=Manager,dc=ldap-pdc,dc=com" -W -x -f user.ldif
如果无报错信息,就代表数据正常导入。
配置ldap日志
1 vi /etc/rsyslog.conf 2 3 local4.* /var/log/ldap.log #尾部添加 4 5 6 touch /var/log/ldap.log #创建日志文件 7 systemctl restart rsyslog.service 重启服务
下面配置samba
1 yum install nss-pam-ldapd samba-winbind sssd-ldap perl perl-LDAP.noarch epel-release smbldap-tools.noarch sssd* pam_ldap openldap-clients 2 cp /etc/samba/smb.conf /etc/samba/smb.conf.bak 3 cp /usr/share/doc/smbldap-tools-0.9.11/smb.conf.example /etc/samba/smb.conf
1 vim /etc/samba/smb.conf 2 3 4 5 6 [global] 7 workgroup = ldap-pdc 8 netbios name = PDC-SRV 9 10 deadtime = 10 11 12 log level = 1 13 log file = /var/log/samba/log.%m 14 max log size = 5000 15 debug pid = yes 16 debug uid = yes 17 utmp = yes 18 19 security = user 20 domain logons = yes 21 os level = 64 22 logon path = 23 logon home = 24 logon drive = 25 logon script = 26 27 passdb backend = ldapsam:"ldap://10.2.48.125" 28 ldap ssl = no 29 ldap admin dn = cn=Manager,dc=ldap-pdc,dc=com 30 ldap delete dn = no 31 32 ## Sync UNIX password with Samba password 33 ## Method 1: 34 unix password sync = no 35 ldap password sync = yes 36 ## Method 2: 37 ;ldap password sync = no 38 ;unix password sync = yes 39 ;passwd program = /usr/sbin/smbldap-passwd -u '%u' 40 ;passwd chat = "Changing *\nNew password*" %n\n "*Retype new password*" %n\n" 41 42 ldap suffix = dc=ldap-pdc,dc=com 43 ldap user suffix = ou=Users 44 ldap group suffix = ou=Groups 45 ldap machine suffix = ou=Computers 46 ldap idmap suffix = ou=Idmap 47 add user script = /usr/sbin/smbldap-useradd -m '%u' -t 1 48 rename user script = /usr/sbin/smbldap-usermod -r '%unew' '%uold' 49 delete user script = /usr/sbin/smbldap-userdel '%u' 50 set primary group script = /usr/sbin/smbldap-usermod -g '%g' '%u' 51 add group script = /usr/sbin/smbldap-groupadd -p '%g' 52 delete group script = /usr/sbin/smbldap-groupdel '%g' 53 add user to group script = /usr/sbin/smbldap-groupmod -m '%u' '%g' 54 delete user from group script = /usr/sbin/smbldap-groupmod -x '%u' '%g' 55 add machine script = /usr/sbin/smbldap-useradd -w '%u' -t 1 56 57 [NETLOGON] 58 path = /var/lib/samba/netlogon 59 browseable = no 60 61 [PROFILES] 62 path = /var/lib/samba/profiles 63 browseable = no 64 writeable = yes 65 create mask = 0611 66 directory mask = 0700 67 csc policy = disable 68 map system = yes 69 map hidden = yes
上述内容根据需要进行定制。
1 systemctl startt smb 2 smbldap-config 3 smbldap-populate
修改nsswitch.conf
1 # To use db, put the "db" in front of "files" for entries you want to be 2 # looked up first in the databases 3 # 4 # Example: 5 #passwd: db files nisplus nis 6 #shadow: db files nisplus nis 7 #group: db files nisplus nis 8 9 passwd: files ldap 10 shadow: files ldap 11 group: files ldap 12 #initgroups: files sss 13 14 #hosts: db files nisplus nis dns 15 hosts: files ldap myhostname 16 17 # Example - obey only what nisplus tells us... 18 #services: nisplus [NOTFOUND=return] files 19 #networks: nisplus [NOTFOUND=return] files 20 #protocols: nisplus [NOTFOUND=return] files 21 #rpc: nisplus [NOTFOUND=return] files 22 #ethers: nisplus [NOTFOUND=return] files 23 #netmasks: nisplus [NOTFOUND=return] files 24 25 bootparams: nisplus [NOTFOUND=return] files 26 27 ethers: files 28 netmasks: files 29 networks: files 30 protocols: files 31 rpc: files 32 services: files sss 33 34 netgroup: files ldap 35 36 publickey: nisplus 37 38 automount: files ldap 39 aliases: files nisplus
修改/etc/nslcd.conf文件
1 # This is the configuration file for the LDAP nameservice 2 # switch library's nslcd daemon. It configures the mapping 3 # between NSS names (see /etc/nsswitch.conf) and LDAP 4 # information in the directory. 5 # See the manual page nslcd.conf(5) for more information. 6 7 # The user and group nslcd should run as. 8 uid nslcd 9 gid ldap 10 11 # The uri pointing to the LDAP server to use for name lookups. 12 # Multiple entries may be specified. The address that is used 13 # here should be resolvable without using LDAP (obviously). 14 #uri ldap://127.0.0.1/ 15 #uri ldaps://127.0.0.1/ 16 #uri ldapi://%2fvar%2frun%2fldapi_sock/ 17 # Note: %2f encodes the '/' used as directory separator 18 uri ldap://10.2.48.125/ 19 20 # The LDAP version to use (defaults to 3 21 # if supported by client library) 22 #ldap_version 3 23 24 # The distinguished name of the search base. 25 base dc=ldap-pdc,dc=com 26 27 # The distinguished name to bind to the server with. 28 # Optional: default is to bind anonymously. 29 #binddn cn=proxyuser,dc=example,dc=com 30 31 # The credentials to bind with. 32 # Optional: default is no credentials. 33 # Note that if you set a bindpw you should check the permissions of this file. 34 #bindpw secret 35 36 # The distinguished name to perform password modifications by root by. 37 #rootpwmoddn cn=admin,dc=example,dc=com 38 39 # The default search scope. 40 #scope sub 41 #scope one 42 #scope base 43 44 # Customize certain database lookups. 45 #base group ou=Groups,dc=example,dc=com 46 #base passwd ou=People,dc=example,dc=com 47 #base shadow ou=People,dc=example,dc=com 48 #scope group onelevel 49 #scope hosts sub 50 51 # Bind/connect timelimit. 52 #bind_timelimit 30 53 54 # Search timelimit. 55 #timelimit 30 56 57 # Idle timelimit. nslcd will close connections if the 58 # server has not been contacted for the number of seconds. 59 #idle_timelimit 3600 60 61 # Use StartTLS without verifying the server certificate. 62 #ssl start_tls 63 #tls_reqcert never 64 65 # CA certificates for server certificate verification 66 #tls_cacertdir /etc/ssl/certs 67 #tls_cacertfile /etc/ssl/ca.cert 68 69 # Seed the PRNG if /dev/urandom is not provided 70 #tls_randfile /var/run/egd-pool 71 72 # SSL cipher suite 73 # See man ciphers for syntax 74 #tls_ciphers TLSv1 75 76 # Client certificate and key 77 # Use these, if your server requires client authentication. 78 #tls_cert 79 #tls_key 80 81 # Mappings for Services for UNIX 3.5 82 #filter passwd (objectClass=User) 83 #map passwd uid msSFU30Name 84 #map passwd userPassword msSFU30Password 85 #map passwd homeDirectory msSFU30HomeDirectory 86 #map passwd homeDirectory msSFUHomeDirectory 87 #filter shadow (objectClass=User) 88 #map shadow uid msSFU30Name 89 #map shadow userPassword msSFU30Password 90 #filter group (objectClass=Group) 91 #map group member msSFU30PosixMember 92 93 # Mappings for Services for UNIX 2.0 94 #filter passwd (objectClass=User) 95 #map passwd uid msSFUName 96 #map passwd userPassword msSFUPassword 97 #map passwd homeDirectory msSFUHomeDirectory 98 #map passwd gecos msSFUName 99 #filter shadow (objectClass=User) 100 #map shadow uid msSFUName 101 #map shadow userPassword msSFUPassword 102 #map shadow shadowLastChange pwdLastSet 103 #filter group (objectClass=Group) 104 #map group member posixMember 105 106 # Mappings for Active Directory 107 #pagesize 1000 108 #referrals off 109 #idle_timelimit 800 110 #filter passwd (&(objectClass=user)(!(objectClass=computer))(uidNumber=*)(unixHomeDirectory=*)) 111 #map passwd uid sAMAccountName 112 #map passwd homeDirectory unixHomeDirectory 113 #map passwd gecos displayName 114 #filter shadow (&(objectClass=user)(!(objectClass=computer))(uidNumber=*)(unixHomeDirectory=*)) 115 #map shadow uid sAMAccountName 116 #map shadow shadowLastChange pwdLastSet 117 #filter group (objectClass=group) 118 119 # Alternative mappings for Active Directory 120 # (replace the SIDs in the objectSid mappings with the value for your domain) 121 #pagesize 1000 122 #referrals off 123 #idle_timelimit 800 124 #filter passwd (&(objectClass=user)(objectClass=person)(!(objectClass=computer))) 125 #map passwd uid cn 126 #map passwd uidNumber objectSid:S-1-5-21-3623811015-3361044348-30300820 127 #map passwd gidNumber objectSid:S-1-5-21-3623811015-3361044348-30300820 128 #map passwd homeDirectory "/home/$cn" 129 #map passwd gecos displayName 130 #map passwd loginShell "/bin/bash" 131 #filter group (|(objectClass=group)(objectClass=person)) 132 #map group gidNumber objectSid:S-1-5-21-3623811015-3361044348-30300820 133 134 # Mappings for AIX SecureWay 135 #filter passwd (objectClass=aixAccount) 136 #map passwd uid userName 137 #map passwd userPassword passwordChar 138 #map passwd uidNumber uid 139 #map passwd gidNumber gid 140 #filter group (objectClass=aixAccessGroup) 141 #map group cn groupName 142 #map group gidNumber gid 143 # This comment prevents repeated auto-migration of settings. 144 ssl no 145 tls_cacertdir /etc/openldap/cacerts
修改 /etc/openldap/ldap.conf
# # LDAP Defaults # # See ldap.conf(5) for details # This file should be world readable but not world writable. #SIZELIMIT 12 #TIMELIMIT 15 #DEREF never TLS_CACERTDIR /etc/openldap/cacerts # Turning this off breaks GSSAPI used with krb5 when rdns = false SASL_NOCANON on URI ldap://10.2.48.125/ BASE dc=ldap-pdc,dc=com
执行authconfig-tui
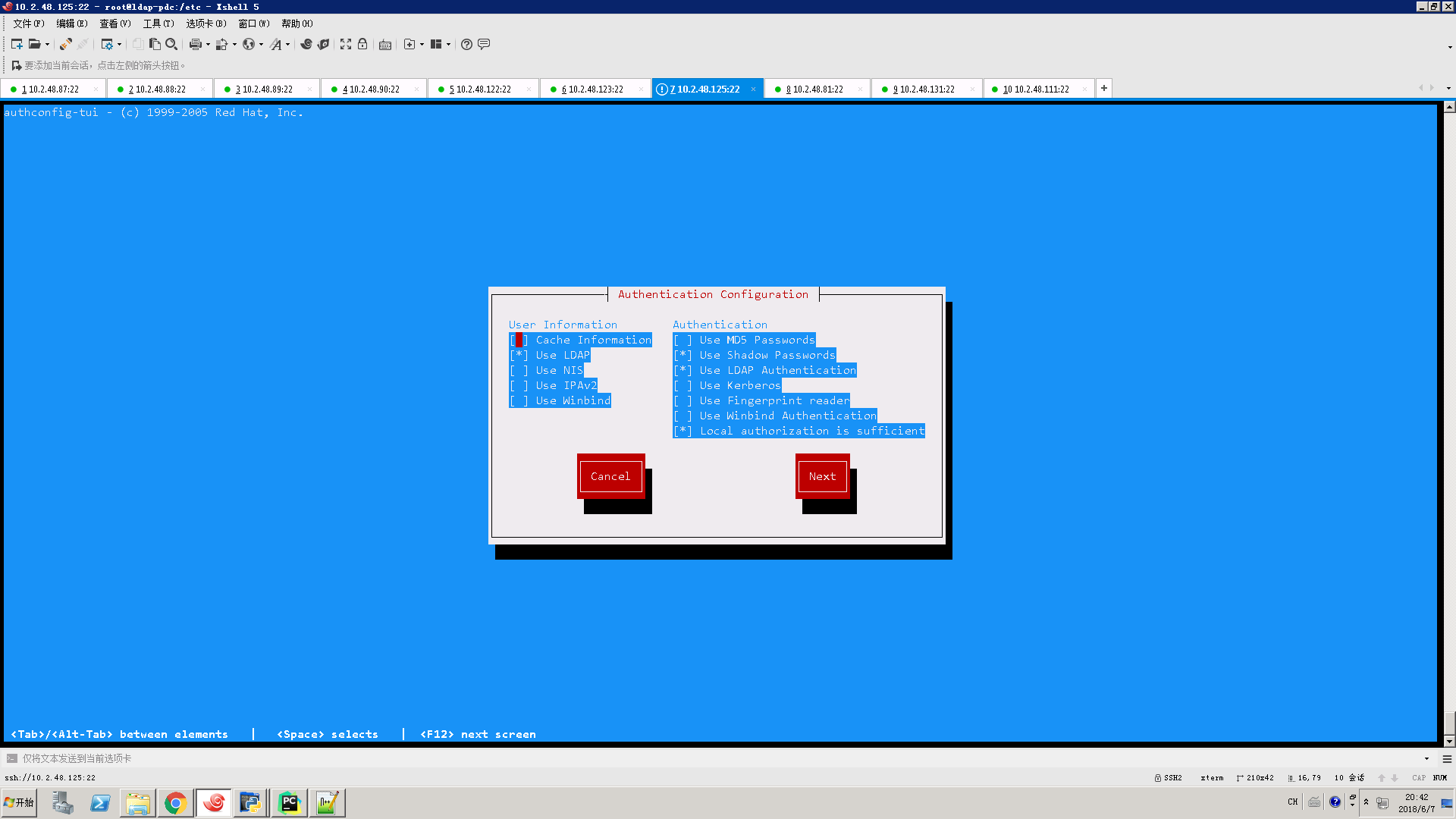
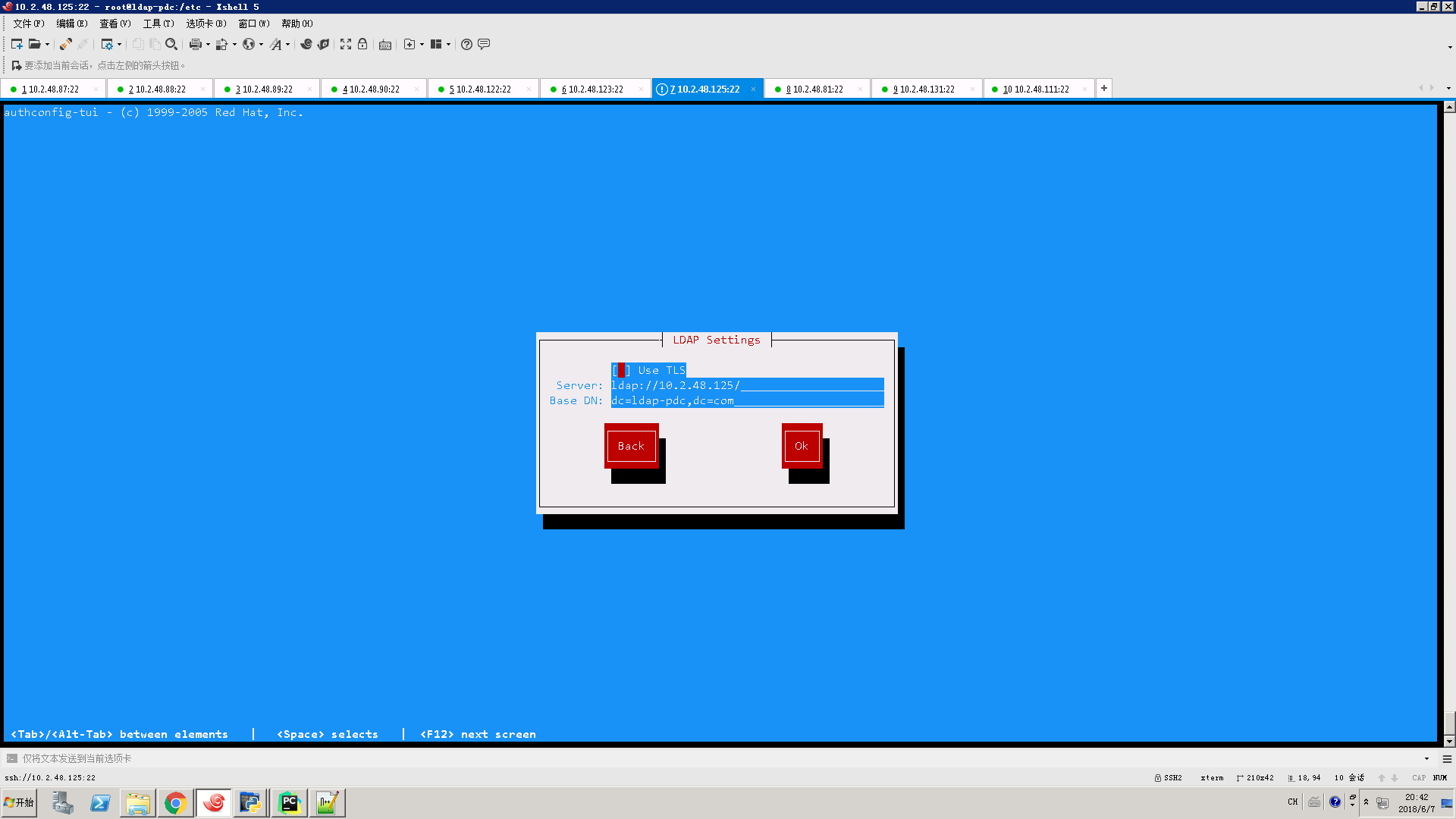
重启几个服务
systemctl restart slapd
systemctl restart smb
systemctl restart nmb
systemctl restart nslcd
systemctl restart nscd
systemctl restart winbind.service
测试本机加入ldap-pdc域
1 net rpc join -U root%111111 2 net rpc testjoin
1 [root@ldap-pdc etc]# net rpc testjoin 2 Join to 'LDAP-PDC' is OK 3 [root@ldap-pdc etc]#
ok.ldap-pdc服务器配置完毕,
windows机器首先需要将其dns服务器改成ldap-pdc服务器的地址,其次需要更改注册表
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlset\services\LanmanWorkstation\ Parameters] “DomainCompatibilityMode”=dword:0000 0001 “DNSNameResolutionRequired”=dword:00000000
之后就可以正常加入LDAP-PDC域啦