安装nginx,这里我是yum直接下载的
yum -y install nginx
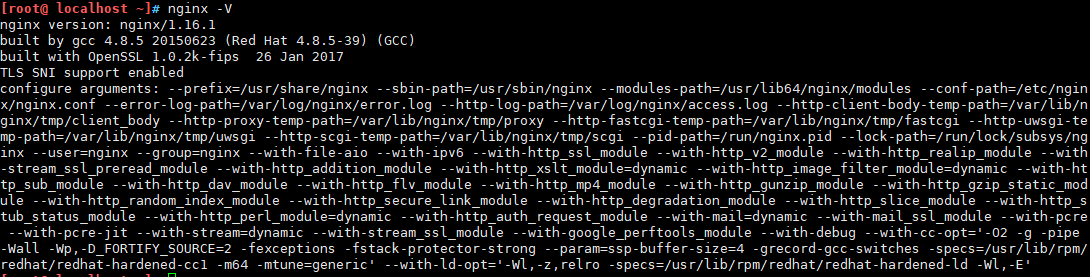
检查nginx的SSL模块
准备私钥和证书
创建私钥
[root@ localhost ~]# cd /etc/nginx/ [root@ localhost nginx]# mkdir -p ssl [root@ localhost nginx]# cd ssl/ [root@ localhost ssl]# openssl genrsa -des3 -out server.key 1024 Generating RSA private key, 1024 bit long modulus .............................................................................++++++ .........++++++ e is 65537 (0x10001) Enter pass phrase for server.key: 123456 Verifying - Enter pass phrase for server.key: 123456 [root@ localhost ssl]# ls server.key [root@ localhost ssl]# ll total 4 -rw-r--r-- 1 root root 963 2020-02-26 20:32 server.key
签发证书
[root@ localhost ssl]# openssl req -new -key server.key -out server.csr Enter pass phrase for server.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BJ Locality Name (eg, city) [Default City]:BJ Organization Name (eg, company) [Default Company Ltd]:SDU Organizational Unit Name (eg, section) []:BJ Common Name (eg, your name or your server's hostname) []:TYK Email Address []:931130942@qq.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: 回车 An optional company name []: 回车
删除私钥口令
[root@ localhost ssl]# [root@ localhost ssl]# cd /etc/nginx/ssl/ [root@ localhost ssl]# cp server.key server.key.ori [root@ localhost ssl]# openssl rsa -in server.key.ori -out server.key Enter pass phrase for server.key.ori: 123456 writing RSA key
生成使用签名请求证书和私钥生成自签证书
[root@ localhost ssl]# cd /etc/nginx/ssl/ [root@ localhost ssl]# cp server.key server.key.ori [root@ localhost ssl]# openssl rsa -in server.key.ori -out server.key Enter pass phrase for server.key.ori: writing RSA key [root@ localhost ssl]# openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt Signature ok subject=/C=CN/ST=BJ/L=BJ/O=SDU/OU=BJ/CN=TYK/emailAddress=931130942@qq.com Getting Private key
开启nginxSSL
创建虚拟主机
先去/etc/nginx/nginx.conf直接复制,复制完以后注释掉
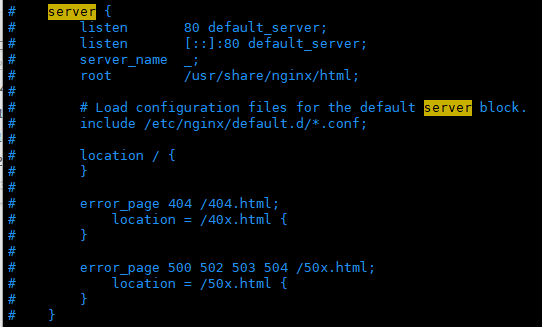
[root@ localhost ~]# cd /etc/nginx/conf.d/
[root@ localhost conf.d]# mkdir -p /etc/nginx/html
[root@ localhost conf.d]# vim hack.conf
[root@ localhost conf.d]# cat hack.conf
server {
listen 443 ssl;
server_name www.hack.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
include /etc/nginx/default.d/*.conf;
#定义站点目录
location / {
root /etc/nginx/html;
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
#检查语法有没有问题然后重启
[root@ localhost conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@ localhost conf.d]# nginx -s reload
绑定windows的hosts,在导入测试页面,然后谷歌浏览器访问https://www.hack.com/back.html

[root@ localhost conf.d]# cd /etc/nginx/html/ [root@ localhost html]# rz -E rz waiting to receive. [root@ localhost html]# ls hack.html
虽然会提示不安全但还是可以正常访问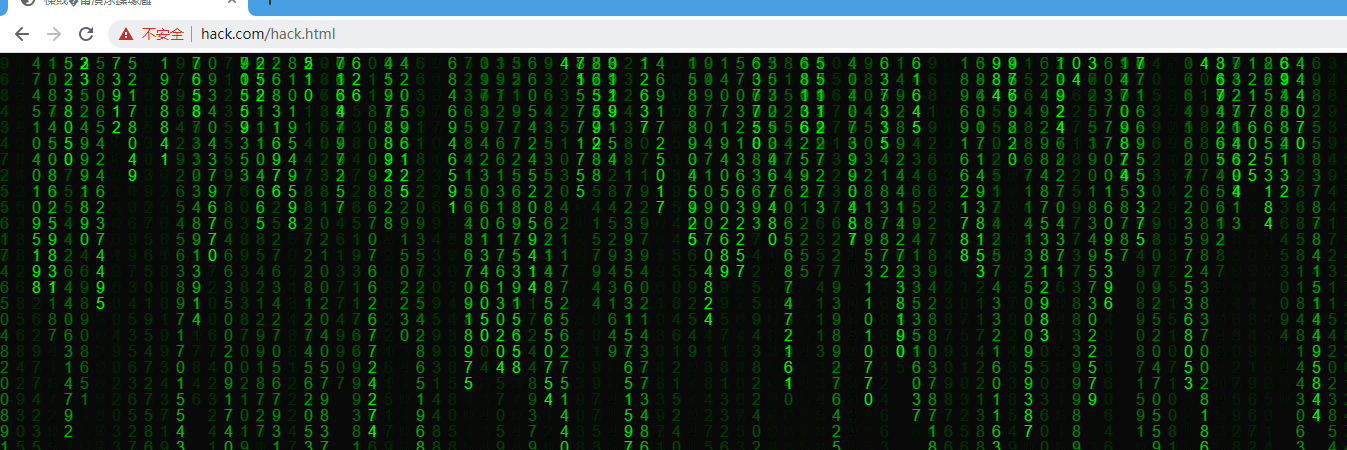
这时候就无法用http://www.hack.com/hack.html去访问了(注意浏览器的缓存)这时候就需要将80端口重定向到443端口。
rewrite重定向
以上配置有个不好的地方,如果用户忘了使用https或者443端口,那么网站将无法访问,因此需要将80端口的访问转到443端口并使用ssl加密访问。只需要增加一个server端,使用301永久重定向。
更改完以后检测语法,然后重新启动nginx。
[root@ localhost conf.d]# cat hack.conf
server {
listen 80;
server_name www.hack.com;
rewrite ^(.*) https://www.$server_name$1 permanent;
}
server {
listen 443 ssl;
server_name www.hack.com;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
include /etc/nginx/default.d/*.conf;
#定义站点目录
location / {
root /etc/nginx/html;
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
[root@ localhost conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@ localhost conf.d]# nginx -s reload
这时再用浏览器去访问http://www.hack.com/hack.html就可以正常访问了,nginx会将请求跳到https://www.hack.com/hack.html,可查看一下nginx的日志显示。
