上一节我们讲解到了如何限制用户访问dashboard的权限,这节我们讲解一个案例:如何创建一个只读权限的用户.
虽然可以根据实际情况灵活创建各种权限用户,但是实际生产环境中往往只需要两个就行了一个是前面创建的拥有集群所有权限的用户,另一个是一个拥有只读权限的普通用户.把只读权限分配给开发人员,使得开发人员也可以很清楚地看到自己的项目运行的状况.
在进行本章节之前,大家可以思考一下怎么用前面的知识来实现,大家可能都有思路,但是要真正的实现起来也不是一简非常容易的事,可能需要进行多轮修改和测试.实际上,kubernetes里有一个默认的叫作view的clusterrole,它其实就是一个有只读权限的的角色.我们来看一下这个角色
[centos@k8s-master ~]$ kubectl describe clusterrole view
Name: view
Labels: kubernetes.io/bootstrapping=rbac-defaults
rbac.authorization.k8s.io/aggregate-to-edit=true
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
bindings [] [] [get list watch]
configmaps [] [] [get list watch]
endpoints [] [] [get list watch]
events [] [] [get list watch]
limitranges [] [] [get list watch]
namespaces/status [] [] [get list watch]
namespaces [] [] [get list watch]
persistentvolumeclaims [] [] [get list watch]
pods/log [] [] [get list watch]
pods/status [] [] [get list watch]
pods [] [] [get list watch]
replicationcontrollers/scale [] [] [get list watch]
replicationcontrollers/status [] [] [get list watch]
replicationcontrollers [] [] [get list watch]
resourcequotas/status [] [] [get list watch]
resourcequotas [] [] [get list watch]
serviceaccounts [] [] [get list watch]
services [] [] [get list watch]
controllerrevisions.apps [] [] [get list watch]
daemonsets.apps [] [] [get list watch]
deployments.apps/scale [] [] [get list watch]
deployments.apps [] [] [get list watch]
replicasets.apps/scale [] [] [get list watch]
replicasets.apps [] [] [get list watch]
statefulsets.apps/scale [] [] [get list watch]
statefulsets.apps [] [] [get list watch]
horizontalpodautoscalers.autoscaling [] [] [get list watch]
cronjobs.batch [] [] [get list watch]
jobs.batch [] [] [get list watch]
daemonsets.extensions [] [] [get list watch]
deployments.extensions/scale [] [] [get list watch]
deployments.extensions [] [] [get list watch]
ingresses.extensions [] [] [get list watch]
networkpolicies.extensions [] [] [get list watch]
replicasets.extensions/scale [] [] [get list watch]
replicasets.extensions [] [] [get list watch]
replicationcontrollers.extensions/scale [] [] [get list watch]
networkpolicies.networking.k8s.io [] [] [get list watch]
poddisruptionbudgets.policy [] [] [get list watch]
[centos@k8s-master ~]$
可以看到,它对拥有的浆糊的访问权限都是get list和和watch,也就是都是不可以进行写操作的权限.这样我们就可以像最初把用户绑定到cluster-admin一样,新创建一个用户,绑定到默认的view role上.
kubectl create sa dashboard-readonly -n kube-system
kubectl create clusterrolebinding dashboard-readonly --clusterrole=view --serviceaccount=kube-system:dashboard-readonly
通过以上命令我们创建了一个叫作dashboard-readonly的用户,然后把它绑定到view这个role上.我们可以通过kubectl describe secret -n=kube-system dashboard-readonly-token-随机字符串(可以通过kubectl get secret -n=kube-system把所有的secret都列出来,然后找到具体的那一个)查看dashboard-readonly用户的secret,里面包含token,我们把token复制到dashboard登陆界面登陆.
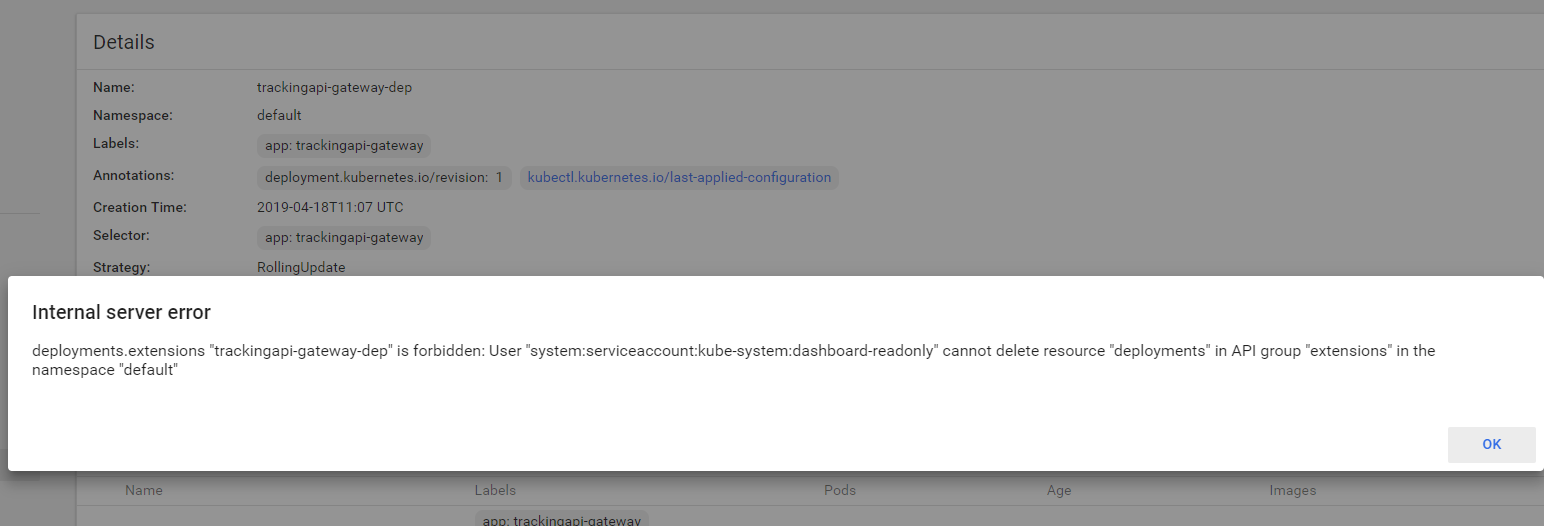
我们随便进到一个deployment里面,可以看到,左上角仍然有scale,edit和delete这些权限,其实不用担心,你如果尝试edit和scale的时候,虽然没有提示,但是操作是不成功的,如果你点击了delete,则会出现一个错误提示,如下图,提示dashboard-readonly用户没有删除的权限
手动创建一个具有真正意义上的只读权限用户
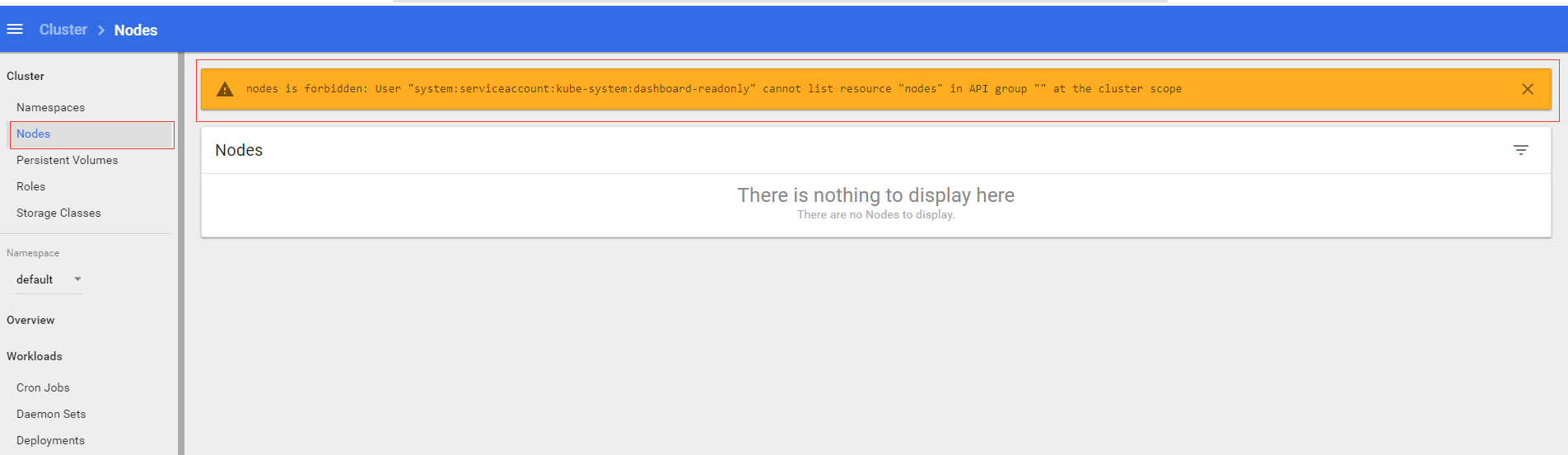
以前我们通过把用户绑定到view这个角色上创建了一个具有只读权限的用户,但是实际上你会发现,这个用户并不是一个完全意义上的只读权限用户,它是没有cluster级别的一些权限的,比如Nodes,persistent volumes等权限,比如我们点击左侧的Nodes标签,就会出现以下提示:
下面我们来手动创建一个对cluster级别的资源也有只读权限的用户
首先,我们先创建一个名叫作
kubectl create sa dashboard-real-readonly -n kube-system
下面我们来创建一个叫作dashboard-viewonly的clusterrole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: dashboard-viewonly
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- persistentvolumeclaims
- pods
- replicationcontrollers
- replicationcontrollers/scale
- serviceaccounts
- services
- nodes
- persistentvolumeclaims
- persistentvolumes
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- bindings
- events
- limitranges
- namespaces/status
- pods/log
- pods/status
- replicationcontrollers/status
- resourcequotas
- resourcequotas/status
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- list
- watch
- apiGroups:
- apps
resources:
- daemonsets
- deployments
- deployments/scale
- replicasets
- replicasets/scale
- statefulsets
verbs:
- get
- list
- watch
- apiGroups:
- autoscaling
resources:
- horizontalpodautoscalers
verbs:
- get
- list
- watch
- apiGroups:
- batch
resources:
- cronjobs
- jobs
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- daemonsets
- deployments
- deployments/scale
- ingresses
- networkpolicies
- replicasets
- replicasets/scale
- replicationcontrollers/scale
verbs:
- get
- list
- watch
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- networkpolicies
verbs:
- get
- list
- watch
- apiGroups:
- storage.k8s.io
resources:
- storageclasses
- volumeattachments
verbs:
- get
- list
- watch
- apiGroups:
- rbac.authorization.k8s.io
resources:
- clusterrolebindings
- clusterroles
- roles
- rolebindings
verbs:
- get
- list
- watch
然后把它绑定到dashboard-real-readonly ServiceAccount上
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
labels:
k8s-app: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: dashboard-viewonly
subjects:
- kind: ServiceAccount
name: dashboard-real-readonly
namespace: kube-system
后面就是获取这个用户的token进行登陆了,我们已经有多次讲到过,本章节前面部分也有,大家可以参照一下,这里就不再赘述了.