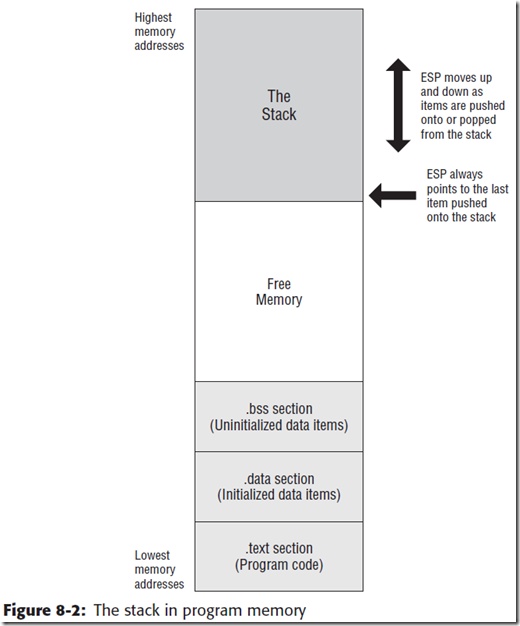
Linux中,Stack是一种数据的操作方式,对内存中的数据进行操作。
stack是倒置的,从上往下长。
在C语言中,动态内存分配(malloc)是在heap中进行的。汇编中的动态分配本书没有涉及。
当stack和下面的代码部分发生冲撞时,Linux会产生"segmentation fault”,并终止程序。
stack的大小并不一定与.text .data的大小成比例。
当程序开始运行时,stack中并非全是空的。有一些比较特殊的东西在里面放着。
Push-y命令:
PUSH pushes a 16-bit or 32-bit register or memory value that is specified by you in your source code.
PUSHF pushes the 16-bit Flags register onto the stack.
PUSHFD pushes the full 32-bit EFlags register onto the stack.
PUSHA pushes all eight of the 16-bit general-purpose registers onto the stack.
PUSHAD pushes all eight of the 32-bit general-purpose registers onto the stack.(PUSH All Double word registers)
pushf ; Push the Flags register pusha ; Push AX, CX, DX, BX, SP, BP, SI, and DI, in that order, all at once pushad ; Push EAX, ECX, EDX, EBX, ESP, EBP, ESI, and EDI, all at once push ax ; Push the AX register push eax ; Push the EAX register push [bx] ; Push the word stored in memory at BX push [edx] ; Push the doubleword in memory at EDX push edi ; Push the EDI register
Pop命令:
POP, POPF, POPFD, POPA, and POPAD
popf ; Pop the top 2 bytes from the stack into Flags popa ; Pop the top 16 bytes from the stack into AX, CX, DX, BX, BP, SI, and DI...but NOT SP! popad ; Pop the top 32 bytes from the stack into EAX, ECX, EDX, EBX, EBP, ESI and EDI...but NOT ESP!!! pop cx ; Pop the top 2 bytes from the stack into CX pop esi ; Pop the top 4 bytes from the stack into ESI pop [ebx] ; Pop the top 4 bytes from the stack into memory at EBX
对Flags寄存器操作:
PUSHF ; Push the Flags register onto the stack..
POP BX ; ..and pop it immediately into BXNot all bits of EFlags may be changed with POPFD. Bits VM and RF are not affected by popping a value off the stack into EFlags.
Stack可以用来短暂存储寄存器中的数据,使寄存器可以用在别的地方。
不过stack的更大的用途是调用Linux的系统服务。