使用GIT克隆TFS服务器上的代码到本地时出现错误如下:
fatal: Authentication failed for 'https://***.visualstudio.com/***Project/_git/***/'
解决办法:
原文请查看(https://roadtoalm.com/2015/07/22/using-personal-access-tokens-to-access-visual-studio-online/)
People who use Visual Studio Online for a while are probably familiar with the alternate credentials. These are used when accessing the REST API or when using an external client for accessing your Git repositories.
You configure your alternate credentials on your [My Profile] page and fill a username and password of your choice.
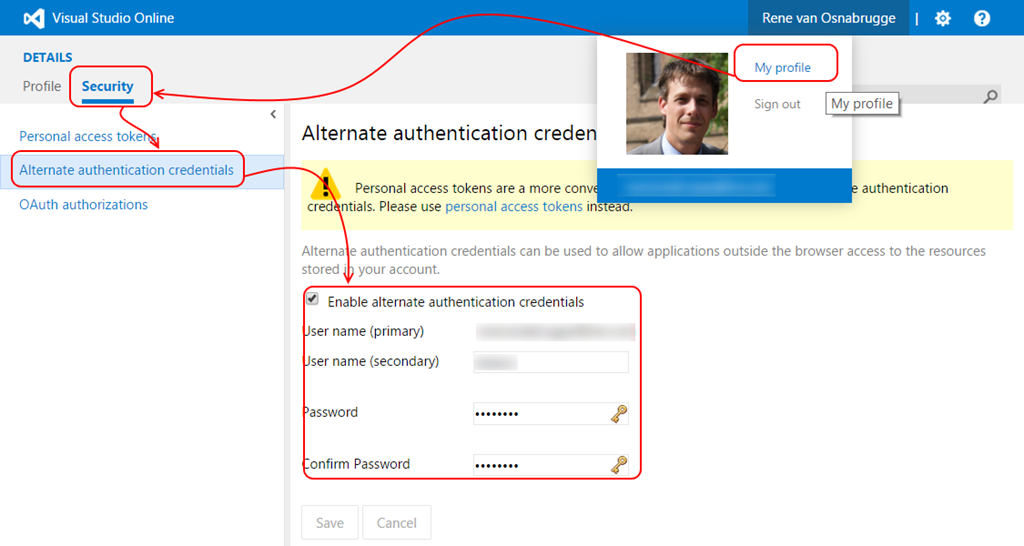
Once you enable your credentials, you can use these credentials when doing a REST call or (easier to test) clone a Git repository
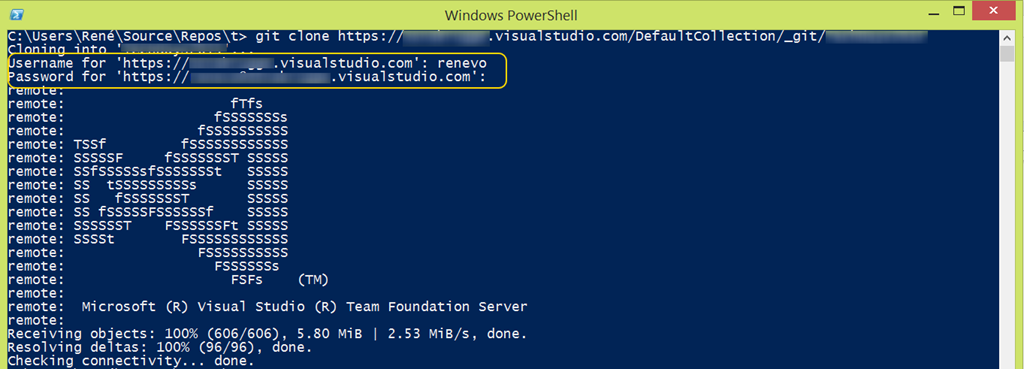
This is great but not the most secure way of doing things.
Personal Access Tokens
In the update of July 7th, we now have the ability to use Personal Access Tokens as an alternative to the Alternate Credentials. Instead of sending our username and password over the wire we an now use a secure token that we can scope to a timeframe and to functionality within VSO. On the [My Profile] page you can configure one or more Personal Access Tokens. For example a token to access Code Features.
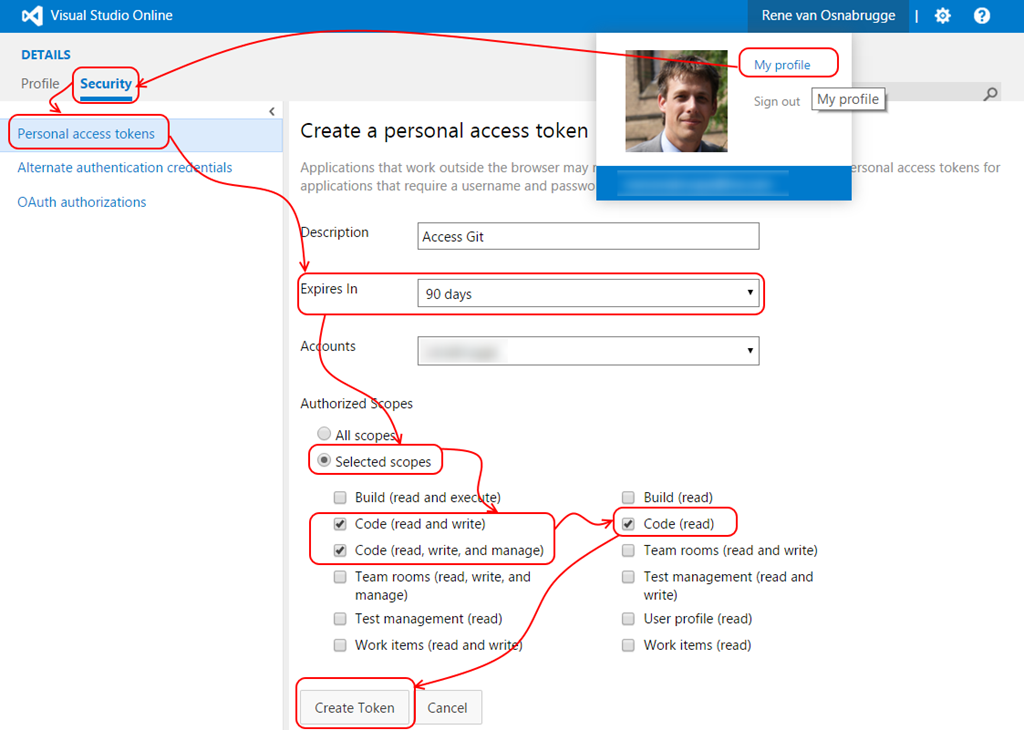
When you create the token, you see a token (only visible after creation !) that you should copy and keep safe.

This token alone is sufficient to authenticate against VSO. So when you now clone a Git repository you only have to fill in this token in the password box. Username can be empty or any value

The great thing is that you can revoke rights or the token afterwards and make sure that people cannot access stuff anymore.
Hope this helps!