UDP/TCP checksum
1Content Table
Internet checksum
1’s complement sum
UDP/TCP checksum
2Internet checksum
(1) Adjacent octets to be checksummed are paired to form 16-bit
integers, and the 1's complement sum of these 16-bit integers is formed.
(2) To generate a checksum, the checksum field itself is cleared,
the 16-bit 1's complement sum is computed over the octets concerned, and the 1's complement of this sum is placed in the checksum field.
(3) To check a checksum, the 1's complement sum is computed over the same set of octets, including the checksum field. If the result is all 1 bits (-0 in 1's complement arithmetic), the check succeeds.
31’s complement sum
Checksum of a block of data is the complement of the one's complement of the 16-bit sum of the block. If checksum is included in the block of data, the new block of data will have its checksum zero. This is how checksum is used for error detection in datagram transmissions.
As an example, consider a block of data:
0x23fb
+ 0x34c0
+ 0xa090
+ 0xbcaf
+ 0xfc05
-----------
0x2b1ff
To calculate 16-bit 1's complement sum, the excess digit 2 needs to be added back to the least significant 16 bits:
0xb1ff
+ 0x2
-----------
0xb201
The complement of this is 0x4dfe. This is the checksum of the block of data.
Note that: checksum(checksum+data)=0
So, if we transmit the block of data including the checksum field, the receiver should see a checksum of 0 if there are no bit errors.
4UDP/TCP checksum
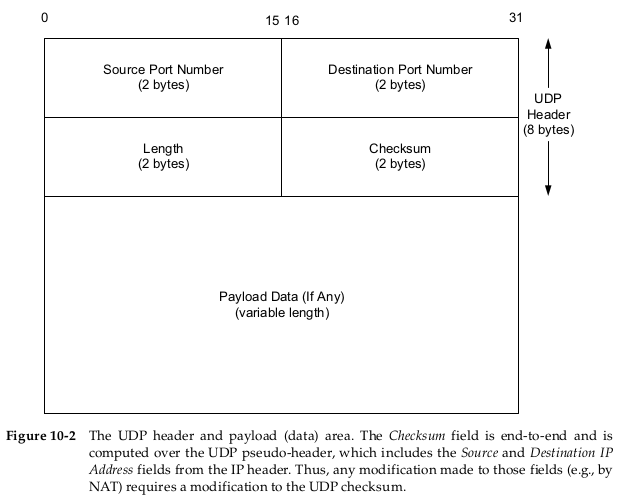
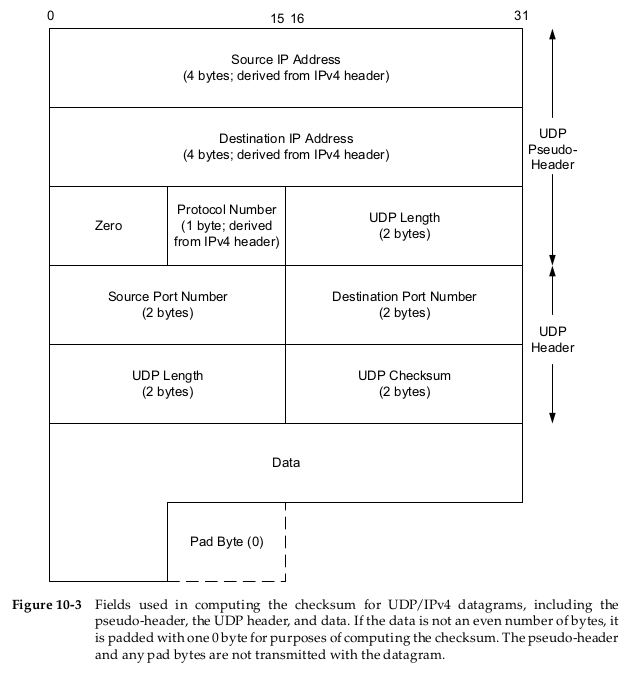

Although the basics for calculating the UDP checksum are similar to the general Internet checksum (the one’s complement of the one’s complement sum of 16-bit words), there are two small special details.
First, the length of the UDP datagram can be an odd number of bytes, whereas the checksum algorithm adds 16-bit words (always an even number of bytes). The procedure for UDP is to append a (virtual) pad byte of 0 to the end of odd-length datagrams, just for the checksum computation and verification.
The second detail is that UDP (as well as TCP) computes its checksum over a 12-byte pseudo-header derived from fields in the IPv4 header or a 40-byte pseudo-header derived from fields in the IPv6 header. This pseudo-header is also virtual and is used only for purposes of the checksum computation (at both the sender and the receiver). Its purpose is to let the UDP layer verify that the data has arrived at the correct destination (i.e., that IP has not accepted a misaddressed datagram, and that IP has not given UDP a datagram that is for another transport protocol).
The TCP Checksum field covers the TCP header and data and some fields in the IP header, using a pseudo-header computation similar to the one used with UDP. It is mandatory for this field to be calculated and stored by the sender, and then verified by the receiver.
5Reference
-
Vol 1. TCP/IP Illustrated