1
1
1
XSS (跨站脚本攻击) 的原理分析,测试
1
demo:
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Document</title> </head> <body> <div> <h1>XSS test using PHP!</h1> <form action="XSS.php" method="GET"> <label for="">XSS input test!</label> <input type="text" name="xss_input" placeholder=""> <!-- --> <input type="submit" value="Submit"> </form> <!-- <script>alert("XSS alert test!");</script> <script>console.log("XSS console.log test!");</script> <script>console.log("XSS console.log test!");<⁄script> --> </div> </body> </html> <?php $xss = $_GET['xss_input']; // echo "你输入的字符为:<br><mark>".$xss."</mark>"; echo "你输入的字符为: <mark>{$xss}</mark>"; ?>1 XSS test using PHP!
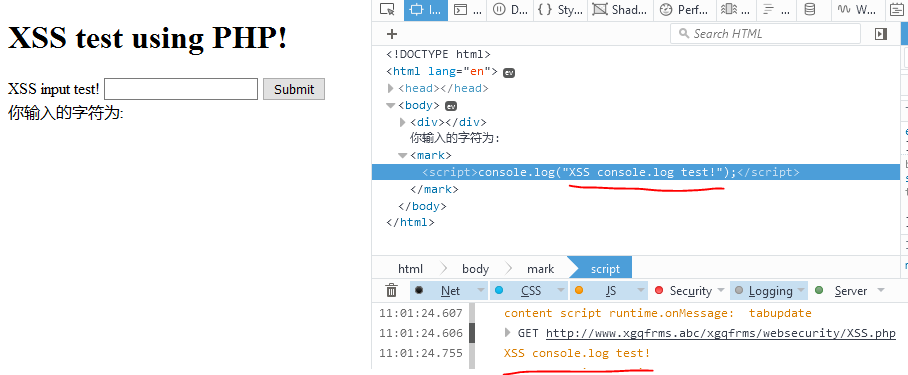
1 <script>console.log("XSS console.log test!");</script>
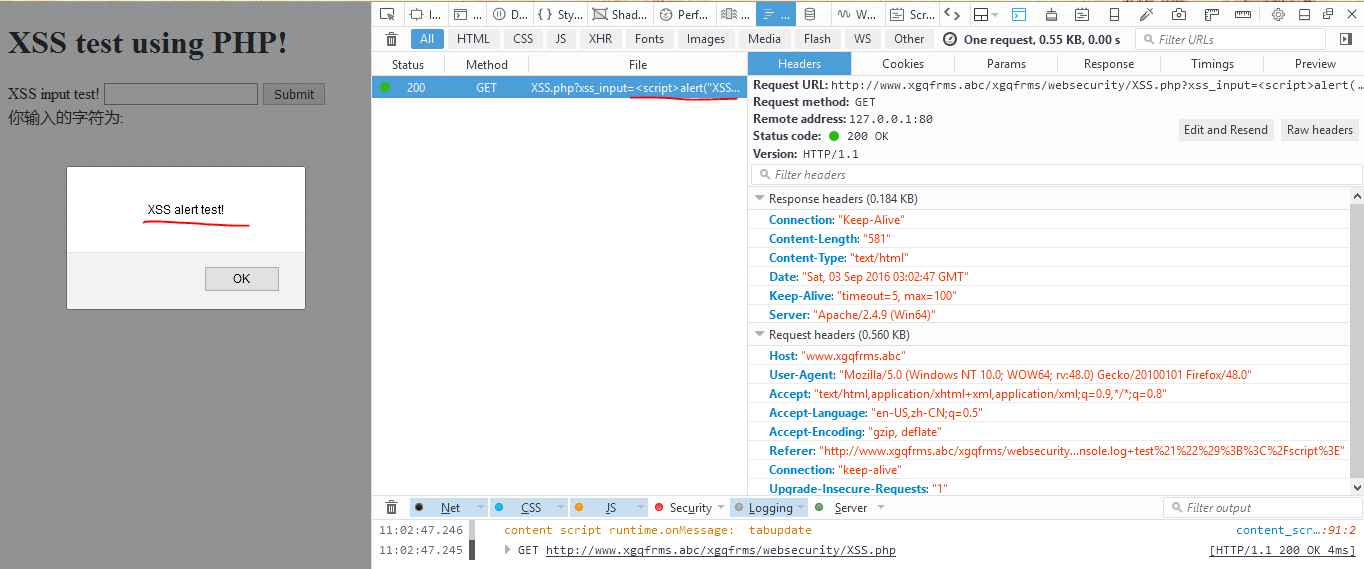
1 <script>alert("XSS alert test!");</script>
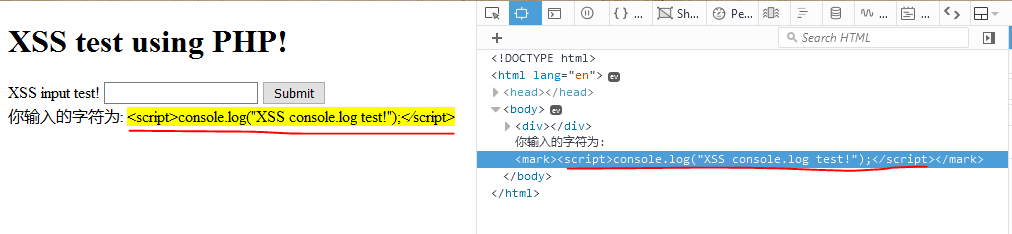
1 实体字符: <script>console.log("XSS console.log test!");<⁄script>
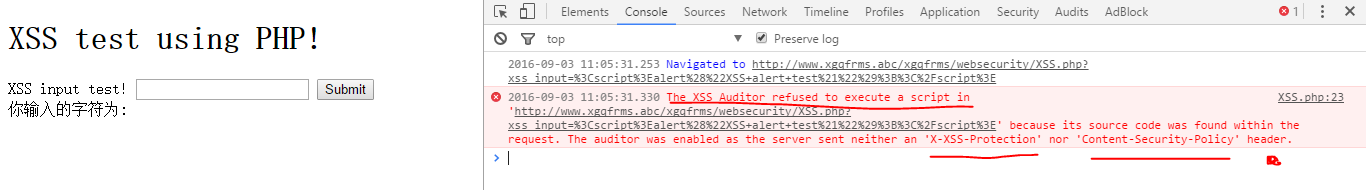
1 Chrome 测试: version 52
1
1
1
1
1
1
1
1
1
1
1
1
1
1
XSS 应对措施:
1. CORS
https://fetch.spec.whatwg.org/#http-cors-protocol
Cross-Origin Resource Sharing
W3C Recommendation 16 January 2014
2. CSP
Content Security Policy Level 2
W3C Candidate Recommendation, 21 July 2015
https://www.w3.org/TR/2012/CR-CSP-20121115/
Content Security Policy 1.0
W3C Candidate Recommendation 15 November 2012
1
1
1
1
reference links:
http://www.freebuf.com/articles/web/40520.html
1
1