ACL主要功能
-
流量控制
-
匹配感兴趣流量
-
是路由器和交换机接口的指令列表,用来控制接口进出的数据包
-
这张表包含里匹配关系,条件和查询条件,表只是一个框架结构,其目的是为了对某种访问进行控制。
ACL分类
-
1-99和1300-1999:标准IP ACL。基于源ip地址过滤
-
100-199和2000-2699:扩展IP ACL.
基于源,目的IP地址;源,目的TCP/UDP端口号
-
AppleTalk:600-699
-
IPX:800-899
配置ACL的3个原则
1,基于每种协议配置一个ACL(per protocol)
2,基于每个方向配置一个ACL(per direction)
3,基于每个接口配置一个ACL(per interface)
ACL工作种类:
入站ACL:在路由器的入接口就挂上ACL。由于没经过路由器,效率高。
出战ACL:无条件进入到路由器,路由器处理完后,到了出接口,在出接口挂上ACL.
ACL工作原理:
ACL表项的匹配顺序是从上到下,只要匹配到任意一个表项,后面的表项就不去匹配了,直接执行并退出。
ACL实验1
在R1的入站接口f0/0上挂ACL,只让R2可以ping通1.1.1.1,R3和R4ping不通1.1.1.1
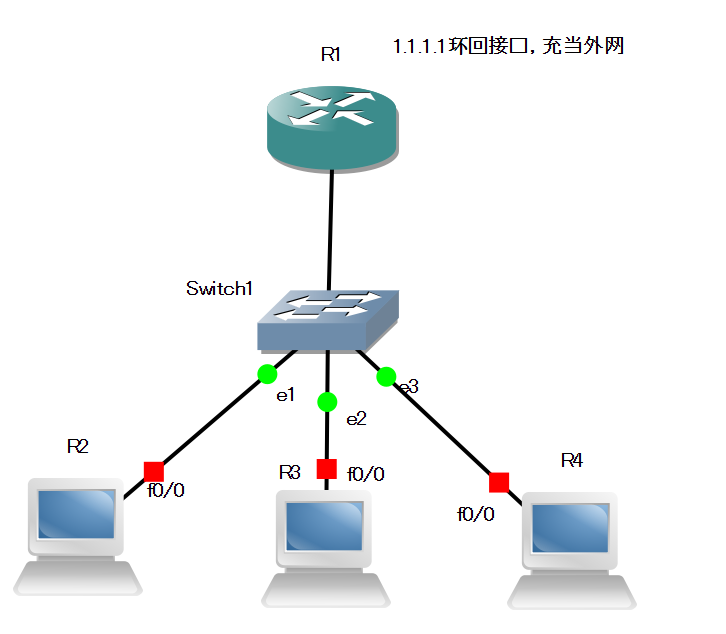
R2,R3,R3虽然是PC图标,但实际是路由器。但是会把它们的路由功能关闭,并指定网关(在全局模式指定网关),路由器默认是不需要指定网关的,因为路由条目里的下一跳就相当于网关了。
关闭路由功能的命令:在全局模式下no ip routing
指定网关的命令:在全局模式下ip default-gateway 192.168.1.1
R1配置:
使用扩展ACL
R1(config)#int f0/0
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#int lo0
R1(config-if)#ip add 1.1.1.1 255.255.255.255
#使用扩展ACL
R1(config)#access-list 100 permit ?
<0-255> An IP protocol number
ahp Authentication Header Protocol
eigrp Cisco's EIGRP routing protocol
esp Encapsulation Security Payload
gre Cisco's GRE tunneling
icmp Internet Control Message Protocol
igmp Internet Gateway Message Protocol
ip Any Internet Protocol
ipinip IP in IP tunneling
nos KA9Q NOS compatible IP over IP tunneling
ospf OSPF routing protocol
pcp Payload Compression Protocol
pim Protocol Independent Multicast
tcp Transmission Control Protocol
udp User Datagram Protocol
#由于ping使用的协议是icmp,所以选择icmp,后面接源地址
R1(config)#access-list 100 permit icmp ?
A.B.C.D Source address
any Any source host
host A single source host
access-list 100 permit icmp ?后面可以是单个主机,也可以是个网段,也可以是所有(any)
- 单个主机的写法:access-list 100 permit icmp host xxx.xxx.xxx.xxx。不需要写反掩码。
- 网段的写法:access-list 100 permit icmp xxx.xxx.xxx.xxx 反掩码。
icmp协议里,不止ping一个报文,所以要精确到ping的话,必须指定出哪个代表ping,echo代表ping的request
R1(config)#access-list 100 permit icmp host 192.168.1.10 host 1.1.1.1 ?
<0-255> ICMP message type
administratively-prohibited Administratively prohibited
alternate-address Alternate address
conversion-error Datagram conversion
dod-host-prohibited Host prohibited
dod-net-prohibited Net prohibited
dscp Match packets with given dscp value
echo Echo (ping)
echo-reply Echo reply
fragments Check non-initial fragments
general-parameter-problem Parameter problem
host-isolated Host isolated
host-precedence-unreachable Host unreachable for precedence
host-redirect Host redirect
host-tos-redirect Host redirect for TOS
host-tos-unreachable Host unreachable for TOS
host-unknown Host unknown
host-unreachable Host unreachable
information-reply Information replies
information-request Information requests
log Log matches against this entry
R1(config)#access-list 100 permit icmp host 192.168.1.10 host 1.1.1.1 echo
R1(config)#access-list 100 deny icmp any host 1.1.1.1 echo
192.168.1.10是源ip;1.1.1.1是目的ip
access-list 100 permit icmp host 192.168.1.10 host 1.1.1.1 echo:允许192.168.1.1的pc能ping通1.1.1.1
access-list 100 deny icmp any host 1.1.1.1 echo:不允许任何pc能ping通1.1.1.1
到此为止,指定了协议,但还没有指定接口和方向
把刚才的定义的ACL表项挂到R1的f0/0上,并指明是入方向:
R1(config-if)#ip access-group 100 ?
in inbound packets
out outbound packets
R1(config-if)#ip access-group 100 in
到此,ACL才生效,我们实验一下,分别从R2,R3,R4ping1.1.1.1。结果是符合预期的。
R2#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/64/72 ms
R3#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
R4#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
但是,从R2,3,4ping192.168.1.1确ping不通了,这是为什么?
-
查询ACL表项:
R1#show access-lists Extended IP access list 100 10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (15 matches) 20 deny icmp any host 1.1.1.1 echo (30 matches)发现当ping192.168.1.1时,ACL表项里的2个表项都不能匹配此次ping,所以就走到了最后面的隐藏语句。隐藏语句让所用源不能访问任何地方,所以导致不能ping通192.168.1.1
解决思路:就是在到达最后的隐藏表项之前,让一个表项能够匹配上,所以就在每个ACL表里的最后添加一条表项:
access-list 100 per ip any any。R1(config)#access-list 100 permit ip any any R1#show access-lists Extended IP access list 100 10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (30 matches) 20 deny icmp any host 1.1.1.1 echo (60 matches) 30 permit ip any any (45 matches)加上这条表项后,就永远不会走到隐藏表项了,所以R2,3,4就能ping通192.168.1.1了。
使用标准ACL
一条就搞定了。因为标准不支持协议,也不支持目的ip,只支持源ip
access-list 1 permit host 192.168.1.10
R2配置:关闭路由功能,并指定网关
R2(config)#int f0/0
R2(config-if)#ip add 192.168.1.10 255.255.255.0
R2(config-if)#no sh
R2(config-if)#exit
R2(config)#no ip routing
R2(config)#ip default-gateway 192.168.1.1
R3配置:关闭路由功能,并指定网关
R3(config)#int f0/0
R3(config-if)#ip add 192.168.1.20 255.255.255.0
R3(config-if)#no sh
R3(config-if)#exit
R3(config)#no ip routi
R3(config)#no ip routing
R3(config)#ip def
R3(config)#ip default-g
R3(config)#ip default-gateway 192.168.1.1
R4配置:关闭路由功能,并指定网关
R4(config)#int f0/0
R4(config-if)#ip add 192.168.1.30 255.255.255.0
R4(config-if)#no sh
R4(config-if)#exit
R4(config)#no ip routing
R4(config)#ip default-gateway 192.168.1.1
删除/添加ACl表里的某个表项
默认编号是10,20...。这样做的目的是,当你想在10和20间添加条目时,可以不改变后面的编号,直接添加一个11或19等,很方便。
R1(config)#ip access-list ?
扩展ACL:extended Extended Access List
log-update Control access list log updates
logging Control access list logging
resequence Resequence Access List
标准ACL:standard Standard Access List
R1(config)#ip access-list extended 100
R1(config-ext-nacl)#do show ip access-list
Extended IP access list 100
10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (30 matches)
20 deny icmp any host 1.1.1.1 echo (60 matches)
30 permit ip any any (45 matches)
R1(config-ext-nacl)#no 20
R1(config-ext-nacl)#do show ip access-list
Extended IP access list 100
10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (30 matches)
30 permit ip any any (45 matches
R1(config-ext-nacl)#20 deny icmp any host 1.1.1.1 echo
R1(config-ext-nacl)#do show ip access-list
Extended IP access list 100
10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (30 matches)
20 deny icmp any host 1.1.1.1 echo
30 permit ip any any (45 matches)
R1(config-ext-nacl)#5 permit icmp host 192.168.1.10 host 1.1.1.1
R1(config-ext-nacl)#do show ip access-list
Extended IP access list 100
5 permit icmp host 192.168.1.10 host 1.1.1.1
10 permit icmp host 192.168.1.10 host 1.1.1.1 echo (30 matches)
20 deny icmp any host 1.1.1.1 echo
30 permit ip any any (45 matches)
删除ACL整张表
R1(config)#no access-list 100
R1(config)#do show ip access-list
R1(config)#
实验2
R1:设置让别的路由器能够实验telnet协议登录到我自己。
R1(config)#line vty 0 4
R1(config-line)#password 123
R1(config-line)#login
R1(config-line)#exit
R1(config)#enable password 123
R2:登录到R1
R2#telnet 1.1.1.1
Trying 1.1.1.1 ... Open
User Access Verification
Password:
R1>
R1>enable
Password:
R1#
R1#exit
[Connection to 1.1.1.1 closed by foreign host]
R2#
R1:添加ACL表项
eq是跟在ip后面的端口号,源ip后面可以有,目的后面也可以有。23是telenet协议的端口号。
R1(config-ext-nacl)#5 permit tcp host 192.168.1.10 host 1.1.1.1 eq
R1(config-ext-nacl)#5 permit tcp host 192.168.1.10 host 1.1.1.1 eq 23
R1(config-ext-nacl)#8 deny tcp any host 1.1.1.1 eq 23
R1(config-ext-nacl)#10 permit ip any any
R1(config-ext-nacl)#do show access-list
Extended IP access list 100
5 permit tcp host 192.168.1.10 host 1.1.1.1 eq telnet
8 deny tcp any host 1.1.1.1 eq telnet
10 permit ip any any
实验R2,R3,R4能否telnet上R1,发现只有R2可以telnet上1.1.1.1,当R2,3能telnet上192.1.1.1。但都能ping通1.1.1.1
R2#telnet 1.1.1.1
Trying 1.1.1.1 ... Open
User Access Verification
Password:
R1>enable
R1>enable
Password:
R1#exit
[Connection to 1.1.1.1 closed by foreign host]
R2#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
R3#telnet 1.1.1.1
Trying 1.1.1.1 ...
% Destination unreachable; gateway or host down
R3#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
R4#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/52/68 ms
R4#telnet 1.1.1.1
Trying 1.1.1.1 ...
% Destination unreachable; gateway or host down