这个问题实际上就是iframe sandbox 沙盒绕过,iframe通过sandbox属性实现沙箱模式,允许js脚本执行,可直接引用第三方js文件来绕过。禁止iframe 里的javascript 执行 top.location = self.location。 也就是禁止了跳转,绕过了反点击劫持。
案例:
<iframe src='2.html' sandbox="allow-scripts allow-same-origin allow-popups">
父页面:
<!DOCTYPE html>
<html>
<head>
<title>test</title>
</head>
<body>
<iframe src='2.html' sandbox="allow-scripts allow-same-origin allow-popups">
</body>
2.html
<!DOCTYPE html><html><head>
<script language="JavaScript">
//window.location.href="https://www.baidu.com";
//location.replace("https://www.baidu.com");
//location.assign("https://www.baidu.com");
alert(1);
</script>
</head><body>test</body>
火狐可以触发xss
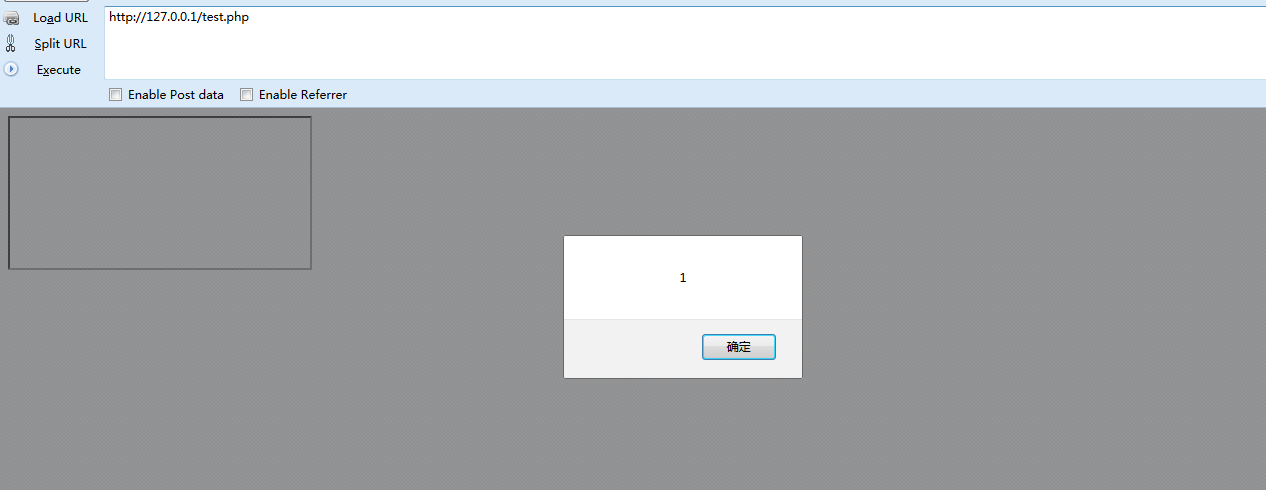
禁止iframe重定向让父级页面跳转
<script language="JavaScript">
if (window != top)
top.location.href = location.href;
</script>
//window.parent.location.href='https://xx.xx.xx.xx';
参考文章:https://www.cnblogs.com/afanti/p/9298415.htm