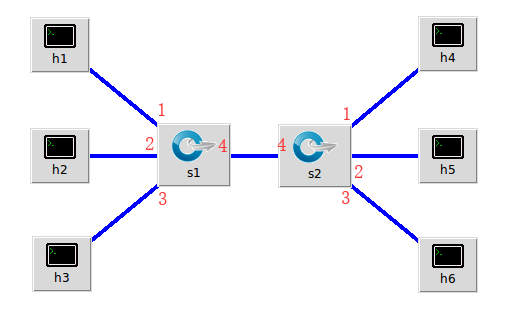
1.利用mininet创建如下拓扑,要求拓扑支持OpenFlow 1.3协议,主机名、交换机名以及端口对应正确,请给出拓扑Mininet执行结果,展示端口连接情况
(1)搭建如下拓扑
(2)python脚本代码
from mininet.topo import Topo
Hcount=3
Scount=2
class MyTopo(Topo):
def __init__(self):
Topo.__init__(self)
global Hcount,Scount
switchs = []
for i in range(Scount):
swit = self.addSwitch("s{}".format(i + 1))
switchs.append(swit)
c = 1
for sw in switchs:
for i in range(Hcount):
hx = self.addHost("h{}".format(c))
self.addLink(sw, hx)
c+=1
self.addLink(switchs[0], switchs[1])
topos = {"mytopo": (lambda : MyTopo()) }
(3)执行python脚本创建mininet网络拓扑
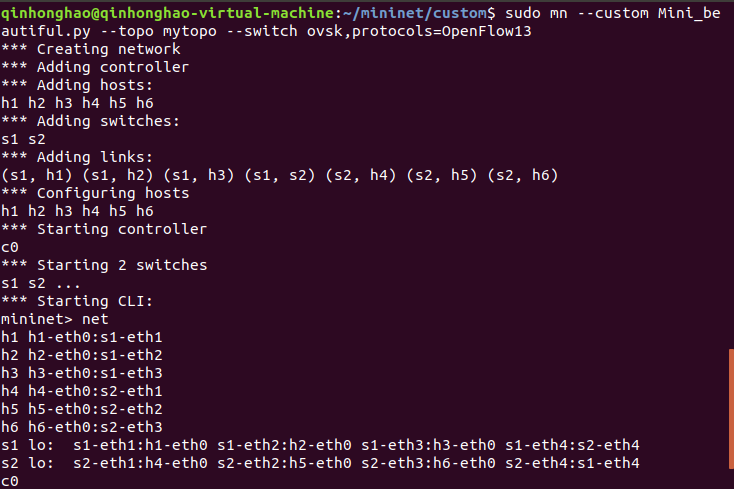
(4).测试端口连接情况
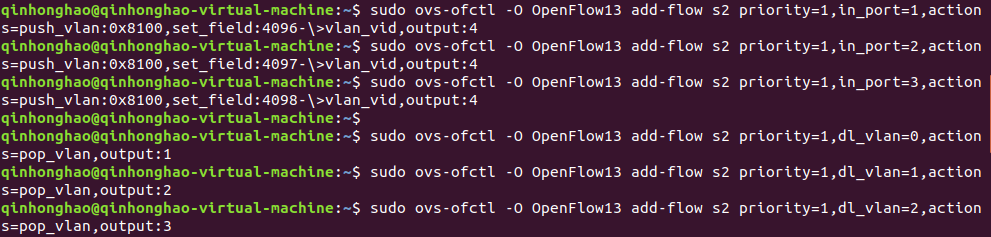
2.直接在Open vSwitch下发流表,用vlan得到下列虚拟网段,请逐条说明所下发的流表含义
(1)s1的流表
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,in_port=1,actions=push_vlan:0x8100,set_field:4096->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,in_port=2,actions=push_vlan:0x8100,set_field:4097->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,in_port=3,actions=push_vlan:0x8100,set_field:4098->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,dl_vlan=0,actions=pop_vlan,output:1
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,dl_vlan=1,actions=pop_vlan,output:2
sudo ovs-ofctl -O OpenFlow13 add-flow s1 priority=1,dl_vlan=2,actions=pop_vlan,output:3

(2)s2的流表
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,in_port=1,actions=push_vlan:0x8100,set_field:4096->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,in_port=2,actions=push_vlan:0x8100,set_field:4097->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,in_port=3,actions=push_vlan:0x8100,set_field:4098->vlan_vid,output:4
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,dl_vlan=0,actions=pop_vlan,output:1
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,dl_vlan=1,actions=pop_vlan,output:2
sudo ovs-ofctl -O OpenFlow13 add-flow s2 priority=1,dl_vlan=2,actions=pop_vlan,output:3
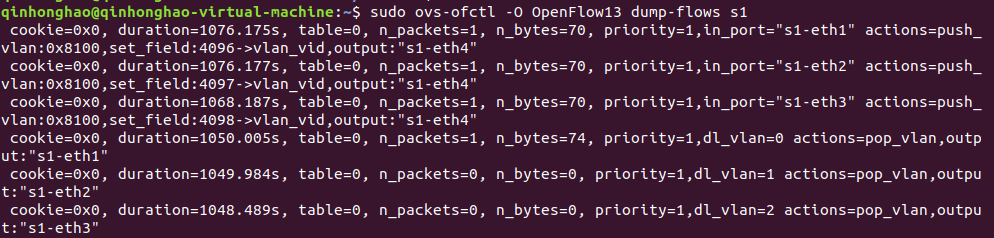
3. 直接在Open vSwitch查看流表,提交OVS命令执行结果
(1)查看s1的流表
**```sudo ovs-ofctl -O OpenFlow13 dump-flows s1
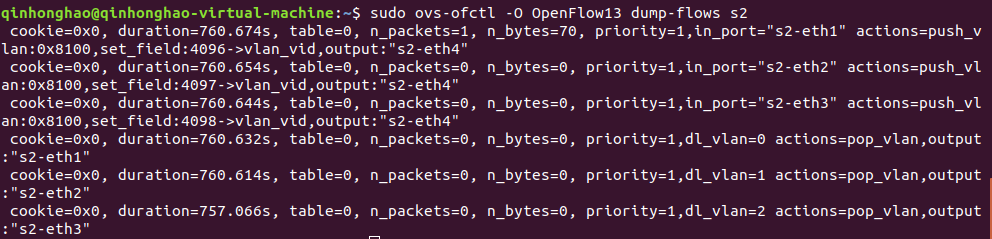
##(2)查看s2的流表
**```sudo ovs-ofctl -O OpenFlow13 dump-flows s2
```**
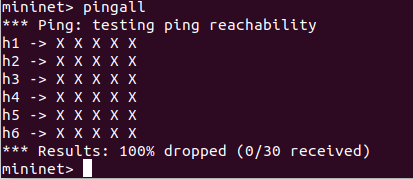
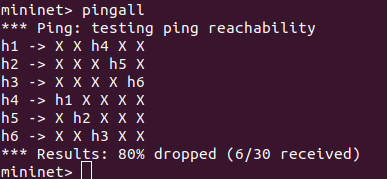
#4.提交主机连通性测试结果,验证流表的有效性
**```
pingall```**
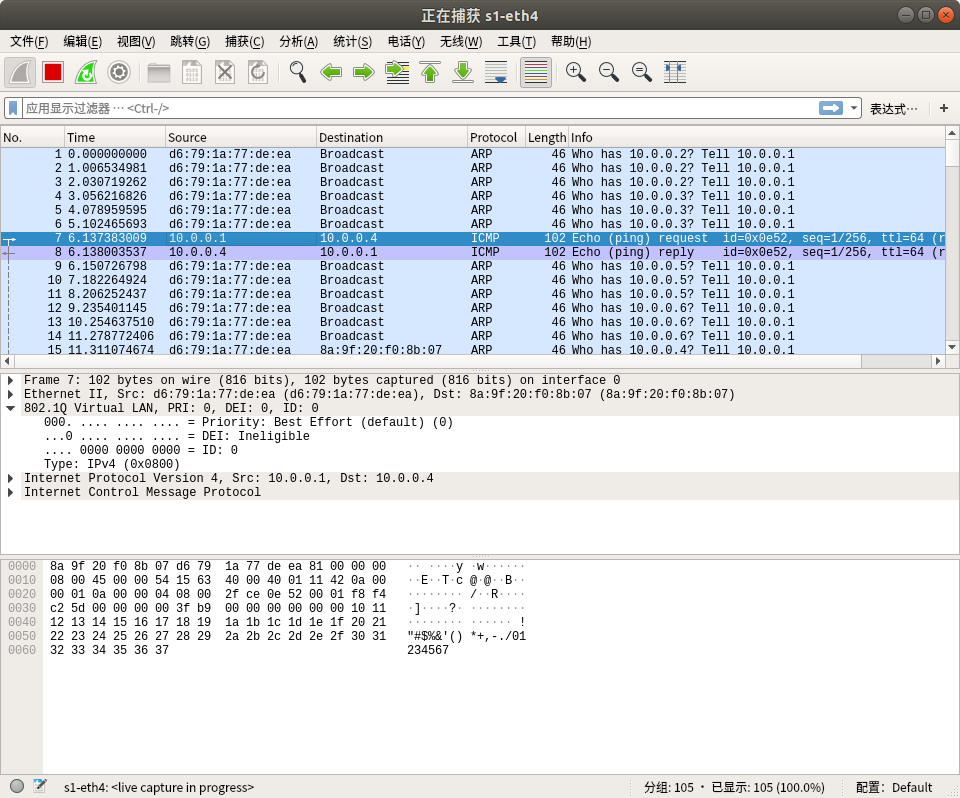
#5. 利用Wireshark抓包,分析验证特定报文
##(1)通过命令启动wireshark
**```sudo wireshark
```**
##(2)抓包
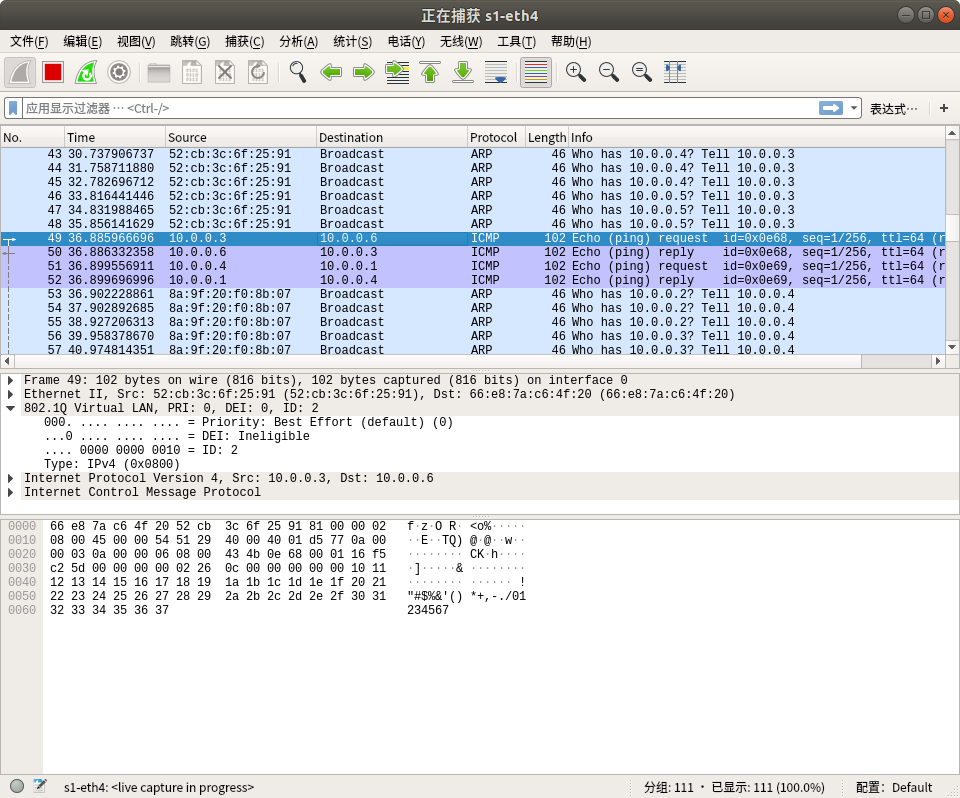
执行 pingall 命令,用wireshark抓包,在s1-eth4才能抓到vlan的包,而在s1-eth1、s1-eth2和s1-eth3均不能抓到vlan包(不知道为什么),
###vlan0:
###vlan1:
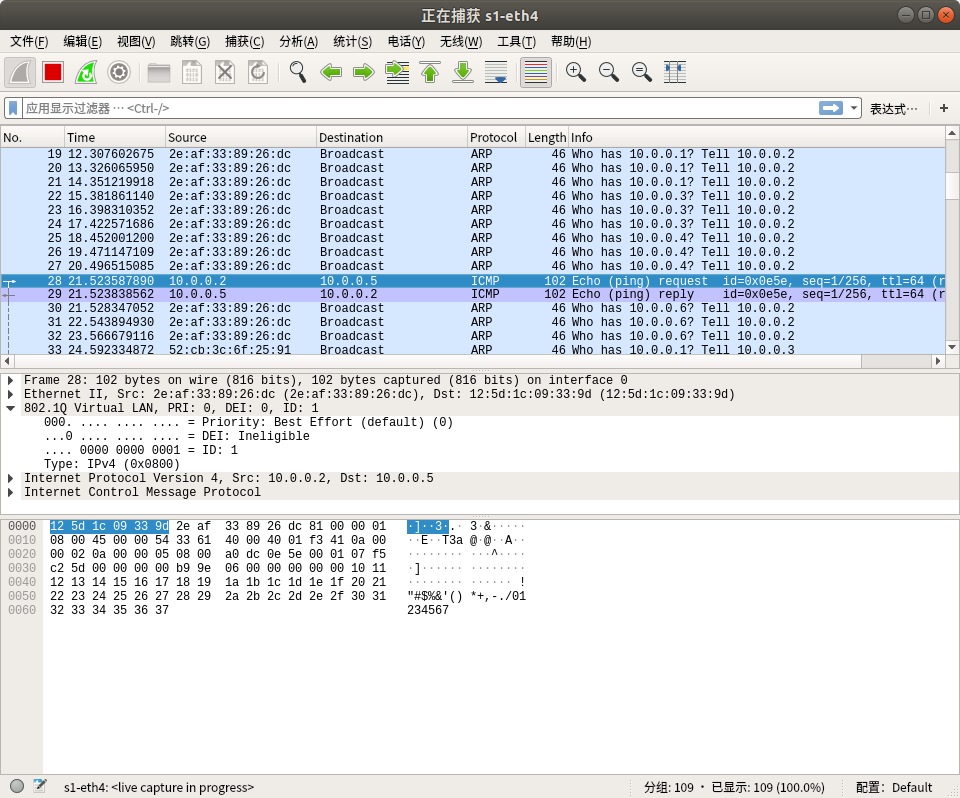
###vlan2: