集群相关证书类型
client certificate: 用于服务端认证客户端,例如etcdctl、etcd proxy、fleetctl、docker客户端
server certificate: 服务端使用,客户端以此验证服务端身份,例如docker服务端、kube-apiserver
peer certificate: 双向证书,用于etcd集群成员间通信
根据认证对象可以将证书分成三类:服务器证书server cert,客户端证书client cert,对等证书peer cert(表示既是server cert又是client cert),在kubernetes 集群中需要的证书种类如下:
etcd 节点需要标识自己服务的server cert,也需要client cert与etcd集群其他节点交互,当然可以分别指定2个证书,也可以使用一个对等证书
master 节点需要标识 apiserver服务的server cert,也需要client cert连接etcd集群,这里也使用一个对等证书
kubectl calico kube-proxy 只需要client cert,因此证书请求中 hosts 字段可以为空
kubelet证书比较特殊,不是手动生成,它由node节点TLS BootStrap向apiserver请求,由master节点的controller-manager 自动签发,包含一个client cert 和一个server cert
0.安装cfssl工具并设定权限
wget -O /usr/bin/cfssl https://software.yangyijing.cn/kubernetes/cfssl/cfssl
wget -O /usr/bin/cfssl-json https://software.yangyijing.cn/kubernetes/cfssl/cfssl-json
wget -O /usr/bin/cfssl-certinfo https://software.yangyijing.cn/kubernetes/cfssl/cfssl-json
chmod +x /usr/bin/cfssl*
[root@rstx-53 test]# cfssl version
Version: 1.2.0
Revision: dev
Runtime: go1.6
示例
[root@rstx-53 test]# cfssl print-defaults csr
{
"CN": "example.net",
"hosts": [
"example.net",
"www.example.net"
],
"key": {
"algo": "ecdsa",
"size": 256
},
"names": [
{
"C": "US",
"L": "CA",
"ST": "San Francisco"
}
]
}
[root@rstx-53 test]# cfssl print-defaults config
{
"signing": {
"default": {
"expiry": "168h"
},
"profiles": {
"www": {
"expiry": "8760h",
"usages": [
"signing",
"key encipherment",
"server auth"
]
},
"client": {
"expiry": "8760h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
}
}
}
}
1.生成根签名证书的请求文件(certificate signing request) ca-csr.json
cat > /opt/certs/ca-csr.json <<EOF
{
"CN": "RSTX",
"hosts": [
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
],
"ca": {
"expiry": "175200h"
}
}
EOF
CN 是请求用户的用户名
O:是请求用户的组名
expiry 设置CA证书的签名请求文件有效期为 10年
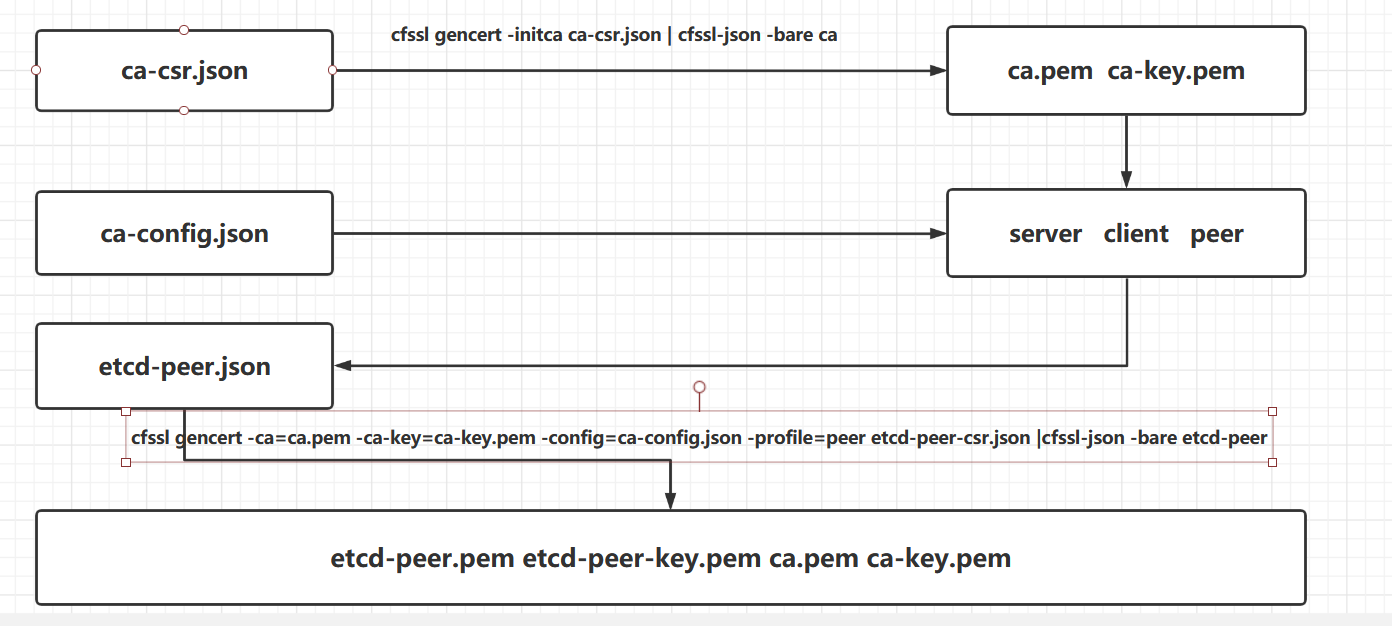
cfssl gencert -initca ca-csr.json | cfssl-json -bare ca
上述命令会生成一个证书 ca.pem ,一个私钥 ca-key.pem,以及ca.csr (证书签名请求).
可以通过openssl来校验一个证书
openssl x509 -in ca.pem -text -noout
2.创建基于根证书的config配置文件 CA的配置文件
vi /opt/certs/ca-config.json
{
"signing": {
"default": {
"expiry": "175200h"
},
"profiles": {
"server": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth"
]
},
"client": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
},
"peer": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
signing :表示可以签发证书
profiles:是证书的类型,本例中该证书用于签名,且是双向对等证书(server auth, client auth)
3.用CA证书为k8s-etcd用户签发一个证书及私钥
vi /opt/certs/etcd-peer-csr.json
{
"CN": "k8s-etcd",
"hosts": [
"192.168.1.201",
"192.168.1.202",
"192.168.1.203",
"192.168.1.204",
"192.168.1.205"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
]
}
hosts字段包含etcd服务运行主机的ip地址 填写ip段无效
生成etcd-peer.pem 及etcd-peer-key.pem证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer etcd-peer-csr.json |cfssl-json -bare etcd-peer
检验etcd-peer.pem信息
cfssl-certinfo -cert etcd-peer.pem