Nginx高级配置-https功能
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.HTTPS工作过程
1>.SSL/TLS
SSL(Secure Socket Layer)/TLS(Transport Layer Security):
1995:
SSL 2.0 Netscape(该浏览器是付费的,这也就是后来为什么IE,Googel浏览器相继横空出世的一个重要因素吧,这个360公司开发的免费的杀毒软件一样,直接让一些传统的杀毒软件公司黄掉了)
1996:
SSL 3.0
1999:
TLS 1.0
2006:
TLS 1.1 IETF(Internet工程任务组) RFC 4346
2008:
TLS 1.2 当前主流使用
2015:
TLS 1.3
功能:
机密性:
对数据进行加密。
认证:
验证身份。
完整性:
数据在传输过程中没有被破坏。
重放保护:
数据在发送中不允许重新发送,什么是重新发送?举个例子,A和B在通信过程中,若A往B发送数据请求登录验证,正常情况下会使用B的公钥对数据进行加密,并发送给B。若A的数据发送给B之前,被C来拦截下来了,由于数据已经被A使用B的公钥加密过了,因此C是破解不了数据的。但是C如果能将这个数据的IP头部信息修改成自己的IP地址并重新发送给B,那么C就间接实现了登录操作,测试A用户还一脸懵逼中。
两阶段协议,分为握手阶段和应用阶段
握手阶段(协商阶段):
客户端和服务器端认证对方身份(依赖于PKI体系,利用数字证书进行身份认证),并协商通信中使用的安全参数、密码套件以及主密钥。后续通信使用的所有密钥都是通过MasterSecret生成。
应用阶段:
在握手阶段完成后进入,在应用阶段通信双方使用握手阶段协商好的密钥进行安全通信
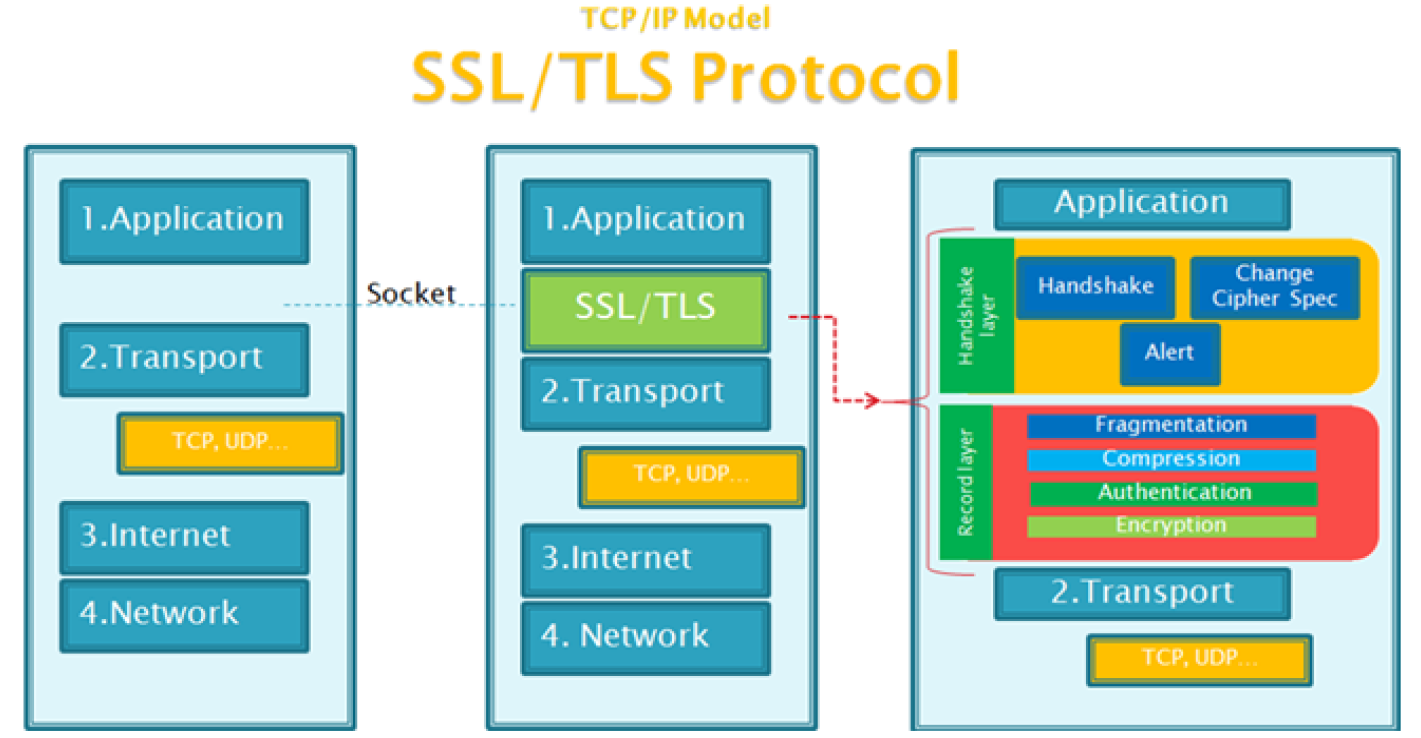
2>.HTTPS
Web网站的登录页面都是使用https加密传输的,加密数据以保障数据的安全,HTTPS能够加密信息,以免敏感信息被第三方获取,所以很多银行网站或电子邮箱等等安全级别较高的服务都会采用HTTPS协议,HTTPS其实是有两部分组成:HTTP + SSL / TLS,也就是在HTTP上又加了一层处理加密信息的模块。
服务端和客户端的信息传输都会通过TLS进行加密,所以传输的数据都是加密后的数据。
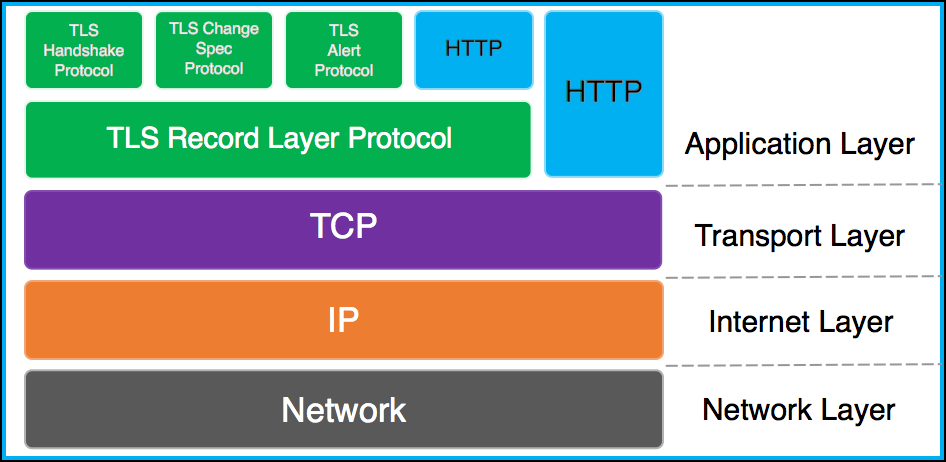
3>.HTTPS工作过程
https 实现过程如下:
1>.客户端发起HTTPS请求:
客户端访问某个web端的https地址,一般都是443端口
2>.服务端的配置:
采用https协议的服务器必须要有一套证书,可以通过一些组织申请,也可以自己制作,目前国内很多网站都自己做的,当你访问一个网站的时候提示证书不可信任就表示证书是自己做的,证书就是一个公钥和私钥匙,就像一把锁和钥匙,正常情况下只有你的钥匙可以打开你的锁,你可以把这个送给别人让他锁住一个箱子,里面放满了钱或秘密,别人不知道里面放了什么而且别人也打不开,只有你的钥匙是可以打开的。
3>.传送证书:
服务端给客户端传递证书,其实就是公钥,里面包含了很多信息,例如证书得到颁发机构、过期时间等等。
4>.客户端解析证书:
这部分工作是有客户端完成的,首先会验证公钥的有效性,比如颁发机构、过期时间等等,如果发现异常则会弹出一个警告框提示证书可能存在问题,如果证书没有问题就生成一个随机值,然后用证书对该随机值进行加密,就像2步骤所说把随机值锁起来,不让别人看到。
5>.传送4步骤的加密数据:
就是将用证书加密后的随机值传递给服务器,目的就是为了让服务器得到这个随机值,以后客户端和服务端的通信就可以通过这个随机值进行加密解密了。
6>.服务端解密信息:
服务端用私钥解密5步骤加密后的随机值之后,得到了客户端传过来的随机值(私钥),然后把内容通过该值进行对称加密,对称加密就是将信息和私钥通过算法混合在一起,这样除非你知道私钥,不然是无法获取其内部的内容,而正好客户端和服务端都知道这个私钥,所以只要机密算法够复杂就可以保证数据的安全性。
7>.传输加密后的信息:
服务端将用私钥加密后的数据传递给客户端,在客户端可以被还原出原数据内容。
8>.客户端解密信息:
客户端用之前生成的私钥获解密服务端传递过来的数据,由于数据一直是加密的,因此即使第三方获取到数据也无法知道其详细内容。

二.nginx的ssl配置
nginx的https功能基于模块ngx_http_ssl_module实现,因此如果是编译安装的nginx要使用参数ngx_http_ssl_module开启ssl功能。 但是作为nginx的核心功能,yum安装的nginx默认就是开启的,编译安装的nginx需要指定编译参数--with-http_ssl_module开启。 官方文档: https://nginx.org/en/docs/http/ngx_http_ssl_module.html 关键参数配置说明如下: ssl on | off; 为指定的虚拟主机配置是否启用ssl功能,此功能在1.15.0废弃,使用listen [ssl]替代。 ssl_certificate /path/to/file; 当前虚拟主机使用使用的公钥文件,一般是crt文件 ssl_certificate_key /path/to/file; 当前虚拟主机使用的私钥文件,一般是key文件 ssl_protocols [SSLv2] [SSLv3] [TLSv1] [TLSv1.1] [TLSv1.2]; 支持ssl协议版本,早期为ssl现在是TSL,默认为后三个 ssl_session_cache off | none | [builtin[:size]] [shared:name:size]; 配置ssl缓存 off:
关闭缓存 none:
通知客户端支持ssl session cache,但实际不支持 builtin[:size]:
使用OpenSSL内建缓存,为每worker进程私有 [shared:name:size]:
在各worker之间使用一个共享的缓存,需要定义一个缓存名称和缓存空间大小,一兆可以存储4000个会话信息,多个虚拟主机可以使用相同的缓存名称。 ssl_session_timeout time;
客户端连接可以复用ssl session cache中缓存的有效时长,默认5m

三.自签名证书
1>.生成CA证书
[root@node101.yinzhengjie.org.cn ~]# cd /yinzhengjie/softwares/nginx/ [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx]# mkdir certs && cd certs [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout ca.key -x509 -days 3650 -out ca.crt #生成CA自签名证书 Generating a 4096 bit RSA private key ............................................................................................................................................................................ ......................++.................++ writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN #指定国家代码,中国的国家代码一般为"CN" State or Province Name (full name) []:beijing #省份,如果是直辖市就直接写直辖市的名称即可,也可以写简称 Locality Name (eg, city) [Default City]:beijing #城市名称 Organization Name (eg, company) [Default Company Ltd]:yinzhengjie #公司名称,自定义即可,写你们公司名称 Organizational Unit Name (eg, section) []:devops #指定公司的部门 Common Name (eg, your name or your server's hostname) []:node101.yinzhengjie.org.cn #一般写当前主机名称即可 Email Address []:y1053419035@qq.com #此处需要写邮箱,当然你也可以不写它并不会影响证书的生成 [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# ll total 8 -rw-r--r-- 1 root root 2171 Dec 22 08:40 ca.crt #公钥 -rw-r--r-- 1 root root 3272 Dec 22 08:40 ca.key #私钥 [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]#
2>.生成证书请求文件
[root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# ll total 8 -rw-r--r-- 1 root root 2171 Dec 22 08:40 ca.crt -rw-r--r-- 1 root root 3272 Dec 22 08:40 ca.key [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout www.yinzhengjie.org.cn.key -out www.yinzhengjie.org.cn.csr Generating a 4096 bit RSA private key ............................................................................................................................................................................ ......................................++................................................................................................................................++ writing new private key to 'www.yinzhengjie.org.cn.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:yinzhengjie Organizational Unit Name (eg, section) []:devops Common Name (eg, your name or your server's hostname) []:www.yinzhengjie.org.cn #注意,这里可用写泛域名,在生产环境中最好写你公司的网站地址,除非你有多个网站需要使用证书可用申请泛域名,相对来说比较贵。 Email Address []:y1053419035@qq.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: #注意,这里不要输入密码,直接回车即可,否则nginx在使用证书时需要交互式输入密码! An optional company name []: [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# ll total 16 -rw-r--r-- 1 root root 2171 Dec 22 08:40 ca.crt -rw-r--r-- 1 root root 3272 Dec 22 08:40 ca.key -rw-r--r-- 1 root root 1769 Dec 22 08:52 www.yinzhengjie.org.cn.csr #专门用于网站的公钥,但是该公钥还没有被签发证书,需要找咱们自建的CA服务器做证书签发,我们有时候也可以说它是证书请求文件。 -rw-r--r-- 1 root root 3272 Dec 22 08:52 www.yinzhengjie.org.cn.key #专门用于网站的私钥 [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]#
3>.签发证书
[root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# ll total 16 -rw-r--r-- 1 root root 2171 Dec 22 08:40 ca.crt -rw-r--r-- 1 root root 3272 Dec 22 08:40 ca.key -rw-r--r-- 1 root root 1769 Dec 22 08:52 www.yinzhengjie.org.cn.csr -rw-r--r-- 1 root root 3272 Dec 22 08:52 www.yinzhengjie.org.cn.key [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# openssl x509 -req -days 36500 -in www.yinzhengjie.org.cn.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out www.yinzhengjie.org.cn.crt
Signature ok subject=/C=CN/ST=beijing/L=beijing/O=yinzhengjie/OU=devops/CN=www.yinzhengjie.org.cn/emailAddress=y1053419035@qq.com Getting CA Private Key [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# ll total 24 -rw-r--r-- 1 root root 2171 Dec 22 08:40 ca.crt -rw-r--r-- 1 root root 3272 Dec 22 08:40 ca.key -rw-r--r-- 1 root root 17 Dec 22 09:01 ca.srl -rw-r--r-- 1 root root 2049 Dec 22 09:01 www.yinzhengjie.org.cn.crt #这就是被咱们CA服务器签发证书的公钥啦,这个证书文件就可用使用了,生产环境别人就这样把你们公司钱赚走了 -rw-r--r-- 1 root root 1769 Dec 22 08:52 www.yinzhengjie.org.cn.csr -rw-r--r-- 1 root root 3272 Dec 22 08:52 www.yinzhengjie.org.cn.key [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]#
4>.验证证书内容
[root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# openssl x509 -in www.yinzhengjie.org.cn.crt -noout -text Certificate: Data: Version: 1 (0x0) Serial Number: df:db:ee:8e:fc:c7:70:b7 Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=beijing, L=beijing, O=yinzhengjie, OU=devops, CN=node101.yinzhengjie.org.cn/emailAddress=y1053419035@qq.com Validity Not Before: Dec 22 01:01:55 2019 GMT Not After : Nov 28 01:01:55 2119 GMT Subject: C=CN, ST=beijing, L=beijing, O=yinzhengjie, OU=devops, CN=www.yinzhengjie.org.cn/emailAddress=y1053419035@qq.com Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (4096 bit) Modulus: 00:cb:32:18:2f:d1:a6:0a:ec:be:47:10:74:a9:7e: 1f:8a:e4:da:d0:b0:d6:a6:ad:ec:c9:81:de:4e:2a: 86:9f:2d:6f:e8:50:b4:60:e2:57:6e:e9:2b:cf:8e: 60:5b:a1:3b:a2:87:89:bc:53:e2:7b:27:33:19:09: fb:87:72:d9:6f:98:27:2e:ac:34:73:21:d5:9a:1e: c2:76:d8:28:e0:b5:47:58:71:b8:8f:d8:ad:39:c2: 73:50:08:a5:f1:de:17:bc:67:36:15:51:35:c6:47: fd:3a:2e:52:a0:5d:96:38:d2:45:d3:8c:67:de:9c: 01:bc:d9:35:6e:ac:9e:64:80:e8:ab:c4:da:66:80: d0:82:da:87:3b:42:48:51:c2:37:0f:a8:85:03:3b: 52:91:b2:5e:91:07:9c:0f:3b:ae:eb:fa:6a:0c:44: bc:65:c3:3c:c3:ee:e0:54:da:3d:d3:33:68:21:a5: 24:ae:3c:c2:b4:ca:dc:69:e2:39:ea:c9:bd:a4:dc: fc:dd:48:19:35:08:74:9f:1a:0b:8b:d7:6c:e2:2d: fe:04:18:22:a1:28:42:8c:2a:b8:e9:f4:83:ac:a6: ff:59:d0:98:ef:df:3d:19:ff:e8:d8:24:41:d5:37: 66:1c:8f:48:12:82:80:15:f6:f9:a4:22:ca:c7:9d: cf:c4:3f:e7:7f:75:42:a4:02:8c:7d:90:37:a7:53: f0:a5:b7:20:2c:a4:97:97:4e:ff:f3:c7:4d:f8:d5: 9f:22:f3:27:31:13:b8:b5:4d:a3:55:bd:53:ab:a7: e4:45:c3:42:7e:f9:8a:5d:e0:c5:e3:55:57:7c:16: 57:25:fd:60:37:bc:c7:95:22:97:02:f3:92:e0:24: 18:3a:01:9d:8b:fa:ad:3c:3f:77:26:1f:ea:4d:0f: f7:c9:98:26:2b:1a:b8:2f:4a:9b:d6:f4:49:d4:2d: ff:6e:0f:fb:7d:51:02:4a:9e:84:9e:b1:7d:79:c3: dd:71:6f:54:96:f3:1a:7b:3a:ff:dd:ea:d5:3a:48: 00:99:c8:01:09:27:6f:92:b7:53:d1:4b:e0:10:bc: ba:5a:17:3d:d8:fe:ab:ee:9c:41:df:e2:74:12:50: 91:f5:9e:38:23:2b:55:0c:d3:5a:88:f8:02:16:39: 12:29:10:5d:e3:69:32:cc:b7:6b:f3:85:c3:07:c8: 57:6f:3b:97:53:23:3a:ab:9d:e4:4c:df:3a:29:0a: 48:62:cb:92:08:f1:a4:e1:a2:c6:56:55:ad:5d:d5: f9:62:5b:f8:00:27:bb:68:c9:5f:fb:9b:83:c2:2c: 75:97:4a:b0:9d:03:eb:22:c0:2e:21:a0:8a:56:74: 85:96:8b Exponent: 65537 (0x10001) Signature Algorithm: sha256WithRSAEncryption 99:cc:88:45:95:dc:b1:a3:9b:ed:0f:7f:38:14:31:6f:26:5a: c6:ea:5c:14:10:c2:4d:8b:a8:2c:4a:e9:31:89:12:d6:84:63: e9:1c:70:d7:22:0e:be:8a:f2:a8:20:18:38:c4:fa:a0:5b:eb: 63:1e:ac:bf:51:43:d3:55:58:48:03:5d:21:d0:19:ea:d4:8e: fe:38:5a:f1:a8:40:1c:40:31:b9:80:e9:5f:a8:1d:f2:c8:18: 42:93:2d:c1:11:f2:6f:ad:0d:67:99:54:0e:6d:d3:5e:b7:d4: ab:f5:a3:11:09:cd:5f:dc:f1:6f:63:be:ec:ca:6b:da:ba:d9: bf:b4:85:99:62:01:cb:f1:c4:fe:b8:ab:9a:0e:07:69:e2:5c: 5b:07:05:9d:85:30:27:d2:da:ed:24:2b:97:15:f6:18:e4:e1: 98:02:31:af:5f:75:85:59:36:ef:fd:1f:d2:cf:41:de:75:94: 30:a0:04:68:c4:ce:62:39:e2:57:08:3b:64:9b:a0:9e:cb:75: 4e:03:46:6e:8e:c1:f5:ea:02:d2:fa:70:9a:7b:fa:7a:50:83: f5:8a:e4:e4:1d:dd:2b:8d:b7:29:19:27:70:99:c8:fb:59:a4: 4a:20:f0:83:be:9c:26:cb:96:41:dc:12:55:40:4d:cb:42:31: de:16:78:42:73:b7:4e:07:dc:2d:41:ff:72:70:42:cf:64:91: 79:66:58:b5:a1:7c:85:c5:8e:83:8b:a9:b5:50:fd:61:06:69: e4:65:be:c6:32:a9:38:2c:78:11:5b:78:51:1c:d8:ab:8a:0a: e5:e4:c5:c6:9a:15:93:d5:af:b8:d1:99:44:15:1e:b3:95:23: b6:71:e4:93:99:19:56:d5:8d:92:64:96:3f:a4:7e:0a:ec:95: 06:94:e8:6c:cc:ec:87:27:ff:35:8c:d5:43:ad:bd:dc:6b:04: c6:77:e8:4c:44:07:2e:92:bb:a9:e8:d5:b1:54:0c:f9:ab:3c: e2:e1:2f:ff:13:61:c5:80:15:13:1d:7e:57:ca:b3:e2:60:c9: 3b:21:ad:e2:4e:22:b1:34:fa:8f:ff:c7:13:02:39:1d:8a:6d: f4:71:b0:17:db:58:4d:64:3e:4d:cc:5d:67:e7:ea:14:58:c7: 2b:4e:ed:7f:2f:e8:95:27:7b:e4:05:48:dc:d3:95:6c:fe:12: cb:e2:f3:06:8a:74:a3:ef:95:df:41:b2:87:20:04:5b:1e:8b: 9a:e0:40:f3:7d:96:0c:b8:90:6c:7a:71:ff:7d:14:fc:f2:28: 2e:fb:38:16:4f:64:3d:31:c4:32:fc:7e:0b:98:8c:78:51:70: ae:f7:88:d1:77:70:b9:c3 [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]# [root@node101.yinzhengjie.org.cn /yinzhengjie/softwares/nginx/certs]#
四.Nginx证书配置
1>.编辑nginx的主配置文件
[root@node101.yinzhengjie.org.cn ~]# cat /yinzhengjie/softwares/nginx/conf/nginx.conf worker_processes 4; worker_cpu_affinity 00000001 00000010 00000100 00001000; events { worker_connections 100000; use epoll; accept_mutex on; multi_accept on; } http { include mime.types; default_type text/html; charset utf-8; log_format my_access_json '{"@timestamp":"$time_iso8601",' '"host":"$server_addr",' '"clientip":"$remote_addr",' '"size":$body_bytes_sent,' '"responsetime":$request_ti me,' '"upstreamtime":"$upstream_response_time",' '"upstreamhost":"$upstream_addr",' '"http_host":"$host",' '"uri":"$uri",' '"domain":"$host",' '"xff":"$http_x_forwarded_for",' '"referer":"$http_referer",' '"tcp_xff":"$proxy_protocol_addr",' '"http_user_agent":"$http_user_agent",' '"status":"$status"}'; access_log logs/access_json.log my_access_json; ssl_certificate /yinzhengjie/softwares/nginx/certs/www.yinzhengjie.org.cn.crt; ssl_certificate_key /yinzhengjie/softwares/nginx/certs/www.yinzhengjie.org.cn.key; ssl_session_cache shared:sslcache:20m; ssl_session_timeout 10m; include /yinzhengjie/softwares/nginx/conf.d/*.conf; } [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# nginx -t nginx: the configuration file /yinzhengjie/softwares/nginx/conf/nginx.conf syntax is ok nginx: configuration file /yinzhengjie/softwares/nginx/conf/nginx.conf test is successful [root@node101.yinzhengjie.org.cn ~]#
2>.编辑nginx的子配置文件
[root@node101.yinzhengjie.org.cn ~]# cat /yinzhengjie/softwares/nginx/conf.d/https.conf server { listen 80; listen 443 ssl; server_name www.yinzhengjie.org.cn; location / { root /yinzhengjie/data/web/nginx/static; index index.html; } } [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# nginx -t nginx: the configuration file /yinzhengjie/softwares/nginx/conf/nginx.conf syntax is ok nginx: configuration file /yinzhengjie/softwares/nginx/conf/nginx.conf test is successful [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
3>.创建测试数据
[root@node101.yinzhengjie.org.cn ~]# mkdir -pv /yinzhengjie/data/web/nginx/static #创建存放数据的目录 mkdir: created directory ‘/yinzhengjie/data’ mkdir: created directory ‘/yinzhengjie/data/web’ mkdir: created directory ‘/yinzhengjie/data/web/nginx’ mkdir: created directory ‘/yinzhengjie/data/web/nginx/static’ [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/web/nginx/static/index.html #创建首页网站 <!DOCTYPE html> <html> <head> <meta charset="UTF-8"> <title>字体的样式</title> <style> .hello{ color: red; font-size: 30px; font-family: "curlz mt","华文彩云","arial", "微软雅黑"; } </style> </head> <body> <p class="hello">2019尹正杰到此一游,在这里提前祝大家2020年新年快乐~</p> </body> </html> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
4>.启动nginx服务
[root@node101.yinzhengjie.org.cn ~]# netstat -untalp | grep nginx [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# nginx [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# netstat -untalp | grep nginx tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 9901/nginx: master tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 9901/nginx: master [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# grep 172.30.1.101 /etc/hosts 172.30.1.101 node101.yinzhengjie.org.cn www.yinzhengjie.org.cn [root@node101.yinzhengjie.org.cn ~]#
5>.客户端浏览器访问
如下图所示,可用正常访问http协议的80端口

如下图所示,可用正常访问https协议的443端口,但是会有如下图所示的提示信息,点击"高级"
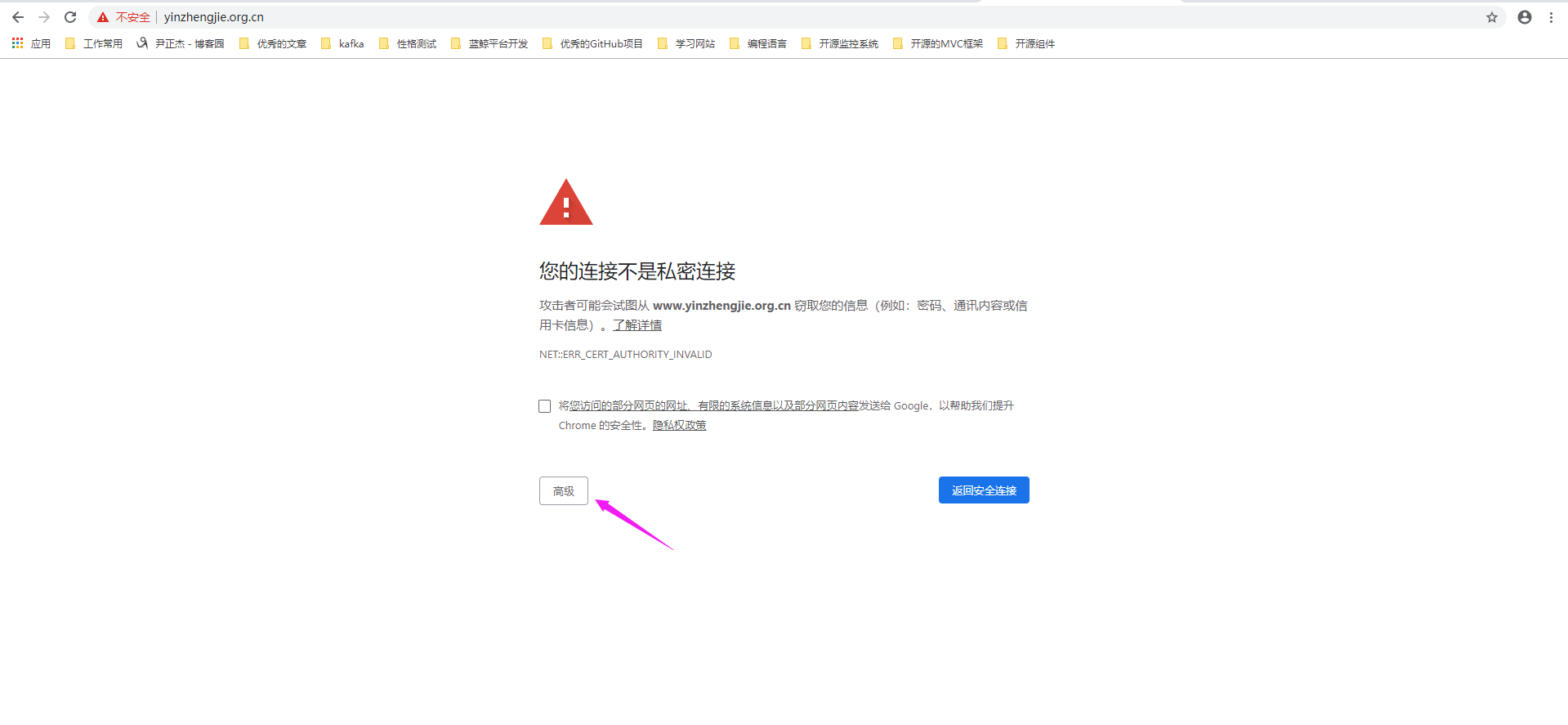
如下图所示,点击咱们的网址,就可用正常打开网页啦.

五.博主推荐阅读
实现多域名HTTPS:
https://www.cnblogs.com/yinzhengjie/p/12056590.html
局域网私有CA(Certificate Authority)证书服务器实战篇:
https://www.cnblogs.com/yinzhengjie/p/12075752.html