1、查看当前vsftpd是否具有ssl模块
[root@localhost ~]# ldd $(which vsftpd) |grep ssl libssl.so.10 => /usr/lib64/libssl.so.10 (0x00007f55009bf000)
2、创建自签名证书
[root@localhost ~]# cd /etc/pki/tls/certs/ [root@localhost certs]# make vsftpd.pem umask 77 ; PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; /usr/bin/openssl req -utf8 -newkey rsa:2048 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 -set_serial 0 ; cat $PEM1 > vsftpd.pem ; echo "" >> vsftpd.pem ; cat $PEM2 >> vsftpd.pem ; rm -f $PEM1 $PEM2 Generating a 2048 bit RSA private key ..................................................+++ ............................+++ writing new private key to '/tmp/openssl.x3aynR' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:beijing Locality Name (eg, city) [Default City]:beijing Organization Name (eg, company) [Default Company Ltd]:it Organizational Unit Name (eg, section) []:ftp Common Name (eg, your name or your server's hostname) []: Email Address []:
3、查看证书
[root@localhost certs]# openssl x509 -in vsftpd.pem -noout -text
4、配置vsftp支持ssl
注:在编辑vstpd.conf时,注意格式,选项行后不得有空格
anonymous_enable=NO #禁止匿名用户登录 chroot_local_user=YES #禁锢所用系统用户在家目录中 ssl_enable=YES #启用ssl allow_anon_ssl=NO #匿名不支持SSL force_local_logins_ssl=YES #本地用户登录加密 force_local_data_ssl=YES #本地数据传输加密 rsa_cert_file=/etc/pki/tls/certs/vsftpd.pem #证书 [root@localhost ~]# useradd test 创建测试用户 [root@localhost ~]# passwd test
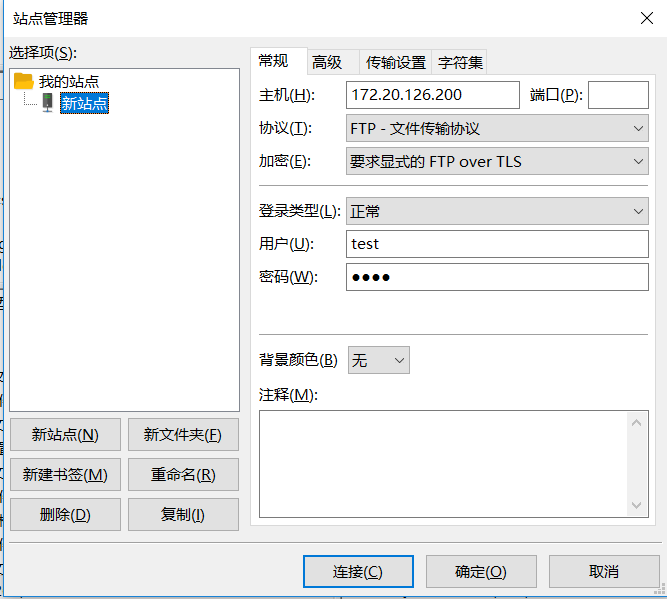
5、测试、利用filezilla 登录测试