1.下载dashboard镜像
在运维主机(mfyxw50.mfyxw.com)上执行命令
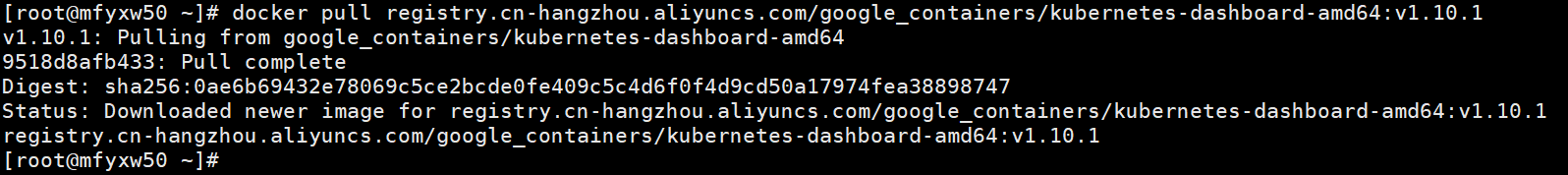
[root@mfyxw50 ~]# docker pull registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
2.对dashboard打标签并上传到私有仓库
在运维主机(mfyxw50.mfyxw.com)上执行命令
[root@mfyxw50 ~]# docker images | grep dashboard
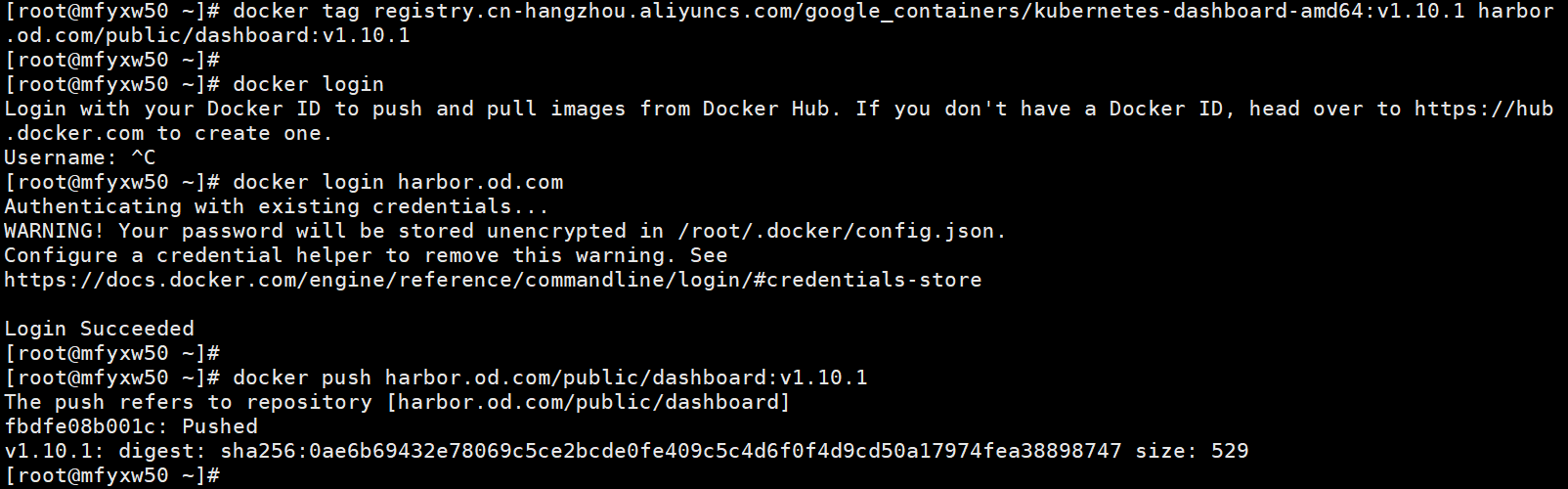
[root@mfyxw50 ~]# docker tage registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 harbor.od.com/public/dashboard:v1.10.1
[root@mfyxw50 ~]# docker login harbor.od.com
[root@mfyxw50 ~]# docker push harbor.od.com/public/dashboard:v1.10.1
3.创建目录用于保存dashboard资源配置清单文件
在运维主机(mfyxw50.mfyxw.com)上执行命令
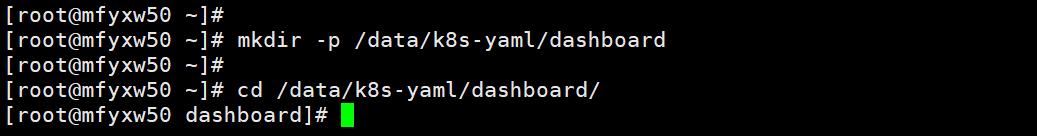
[root@mfyxw50 ~]# mkdir -p /data/k8s-yaml/dashboard
[root@mfyxw50 ~]# cd /data/k8s-yaml/dashboard/
4.创建dashboard资源配置清单
在运维主机(mfyxw50.mfyxw.com)上执行命令
rbac.yaml文件内容如下:
[root@mfyxw50 ~]# cat > /data/k8s-yaml/dashboard/rbac.yaml << EOF
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
EOF
deployment.yaml文件内容如下:
[root@mfyxw50 ~]# cat > /data/k8s-yaml/dashboard/deployment.yaml << EOF
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/public/dashboard:v1.10.1
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
EOF
svc.yaml文件内容如下:
[root@mfyxw50 ~]# cat > /data/k8s-yaml/dashboard/svc.yaml << EOF
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
EOF
ingress文件内容如下:
[root@mfyxw50 ~]# cat > /data/k8s-yaml/dashboard/ingress.yaml << EOF
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
EOF
5.应用dashboard资源配置文件
在master主机(mfyxw30.mfyxw.com或mfyxw40.mfyxw.com)任意一台执行
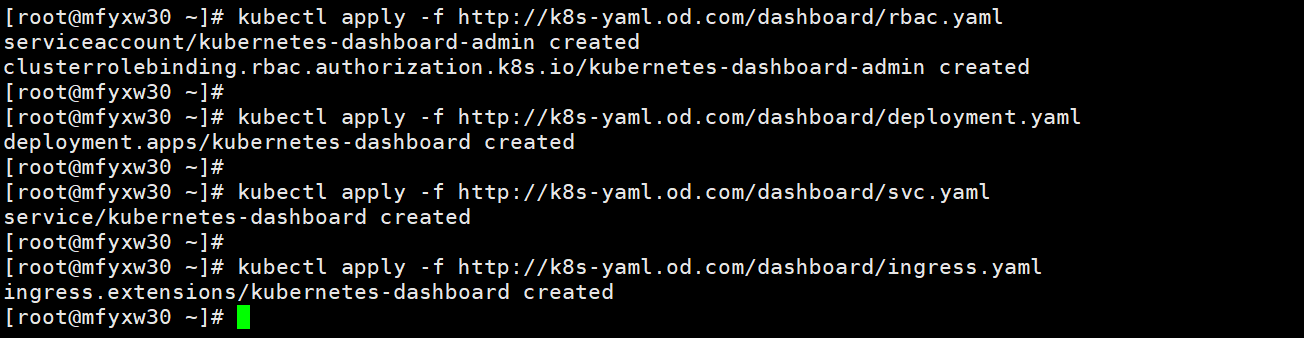
[root@mfyxw30 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/rbac.yaml
[root@mfyxw30 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/deployment.yaml
[root@mfyxw30 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/svc.yaml
[root@mfyxw30 ~]# kubectl apply -f http://k8s-yaml.od.com/dashboard/ingress.yaml
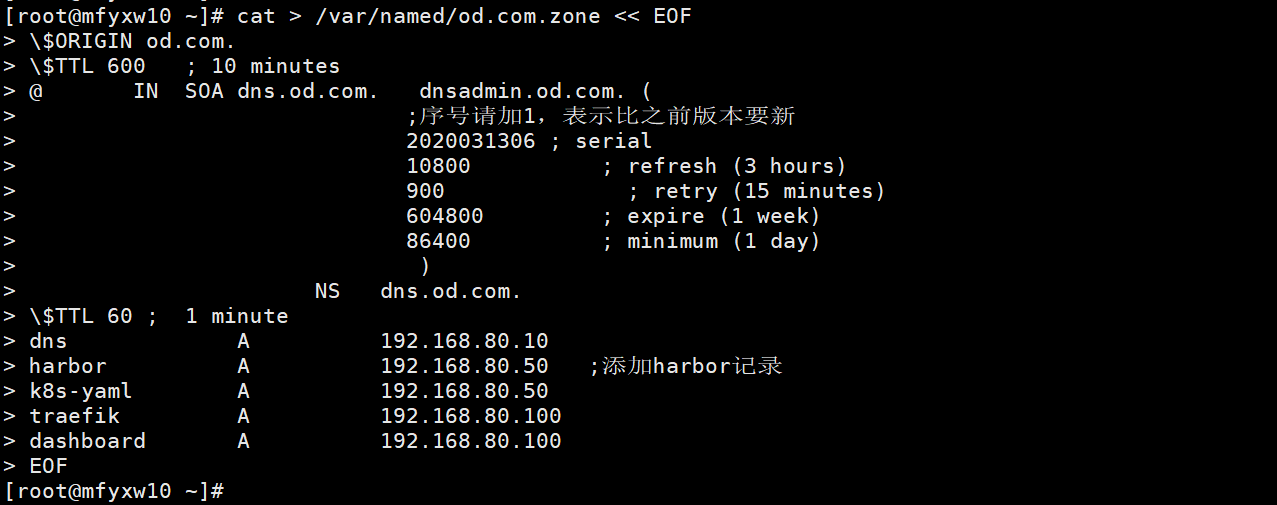
6.在DNS服务器上配置域名解析
在mfyxw10.mfyxw.com主机下执行
[root@mfyxw10 ~]# cat > /var/named/od.com.zone << EOF
$ORIGIN od.com.
$TTL 600 ; 10 minutes
@ IN SOA dns.od.com. dnsadmin.od.com. (
;序号请加1,表示比之前版本要新
2020031306 ; serial
10800 ; refresh (3 hours)
900 ; retry (15 minutes)
604800 ; expire (1 week)
86400 ; minimum (1 day)
)
NS dns.od.com.
$TTL 60 ; 1 minute
dns A 192.168.80.10
harbor A 192.168.80.50 ;添加harbor记录
k8s-yaml A 192.168.80.50
traefik A 192.168.80.100
dashboard A 192.168.80.100
EOF
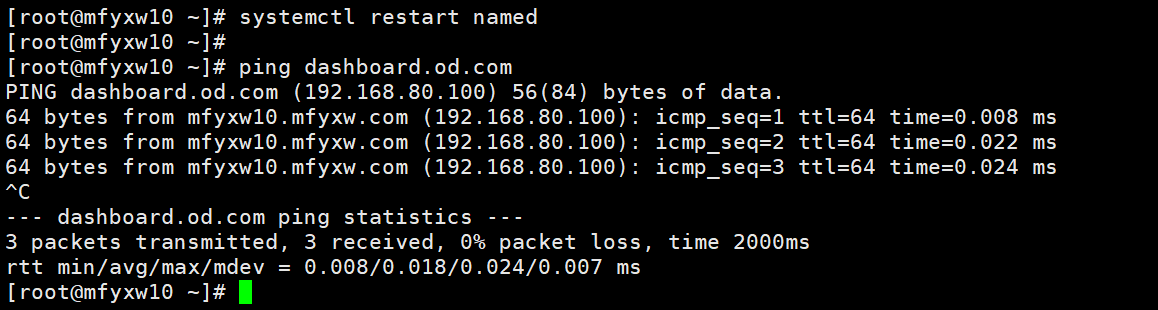
7.重载DNS服务
在mfyxw10.mfyxw.com主机下执行
[root@mfyxw10 ~]# systemctl restart named
[root@mfyxw10 ~]# ping dashboard.od.com
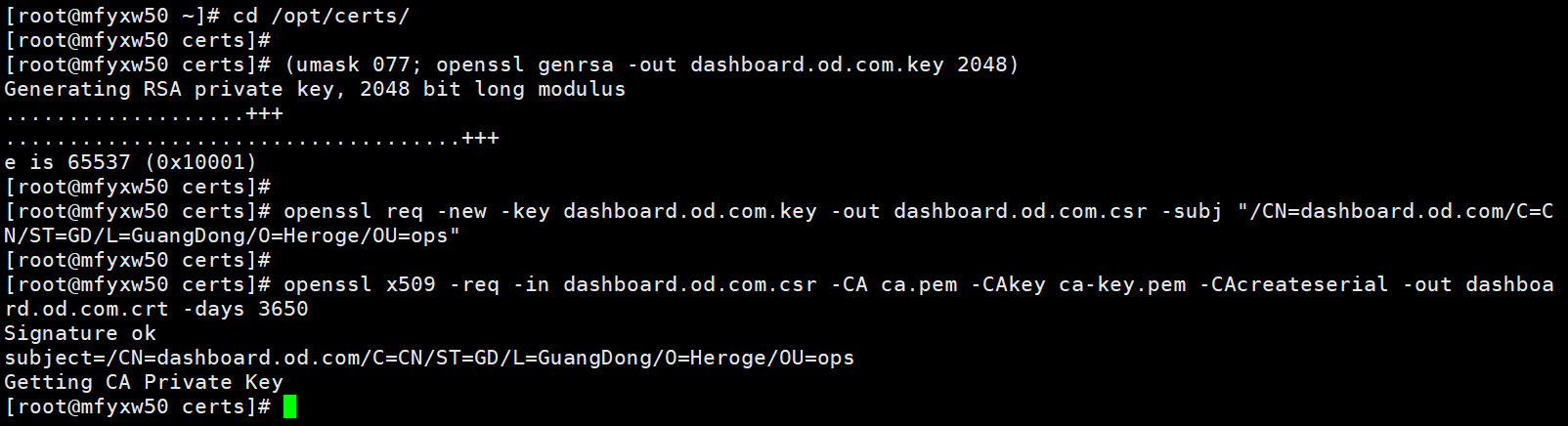
8.生成dashboard证书
在运维主机(mfyxw50.mfyxw.com)上执行
[root@mfyxw50 ~]# cd /opt/certs/
[root@mfyxw50 certs]# (umask 077 openssl genrsa -out dashboard.od.com 2018)
[root@mfyxw50 certs]# openssl req -new -key dashboard.od.com.key -out dashboard.od.com.csr -subj "/CN=dashboard.od.com/C=CN/ST=GD/L=GuangDong/O=Heroge/OU=ops"
[root@mfyxw50 certs]# openssl x509 -req -in dashboard.od.com.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out dashboard.od.com -days 3650
9.将生成的dashboard证书复制相对应的主机
分别在mfyxw10.mfyxw.com和mfyxw20.mfyxw.com主机执行
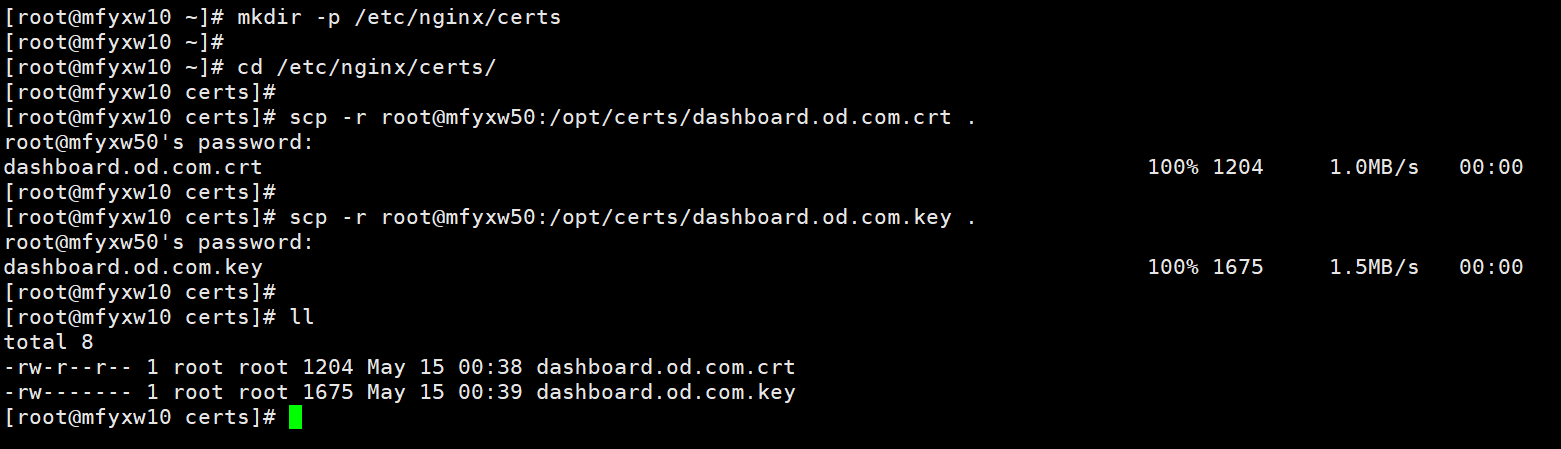
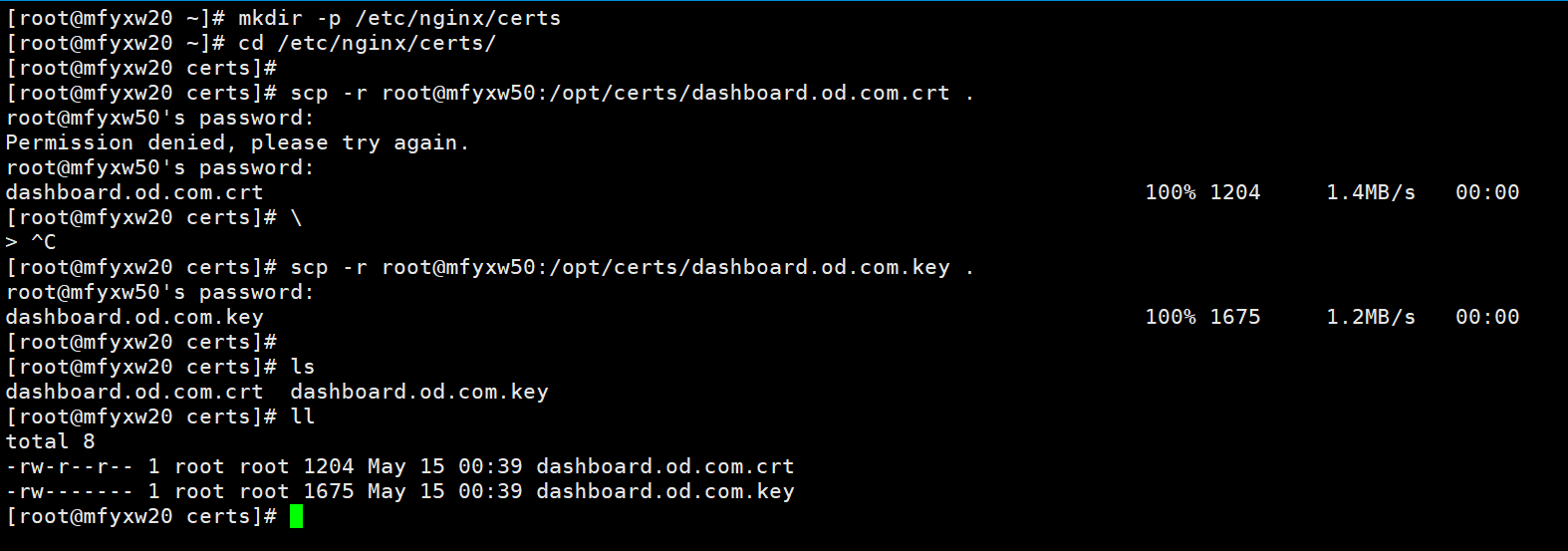
~]# mkdir -p /etc/nginx/certs
~]# cd /etc/nginx/certs/
certs]# scp -r root@mfyxw50:/opt/certs/dashboard.od.com.crt .
certs]# scp -r root@mfyxw50:/opt/certs/dashboard.od.com.key .
10.为域名提供nginx的证书配置文件
分别在mfyxw10.mfyxw.com和mfyxw20.mfyxw.com上机上执行如下命令
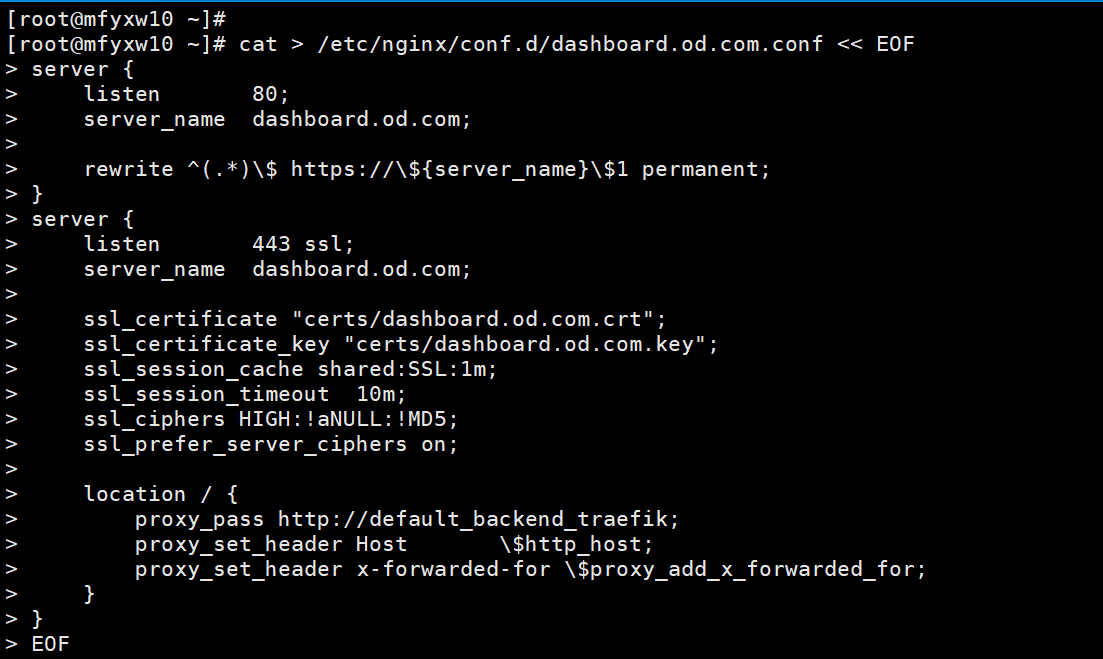
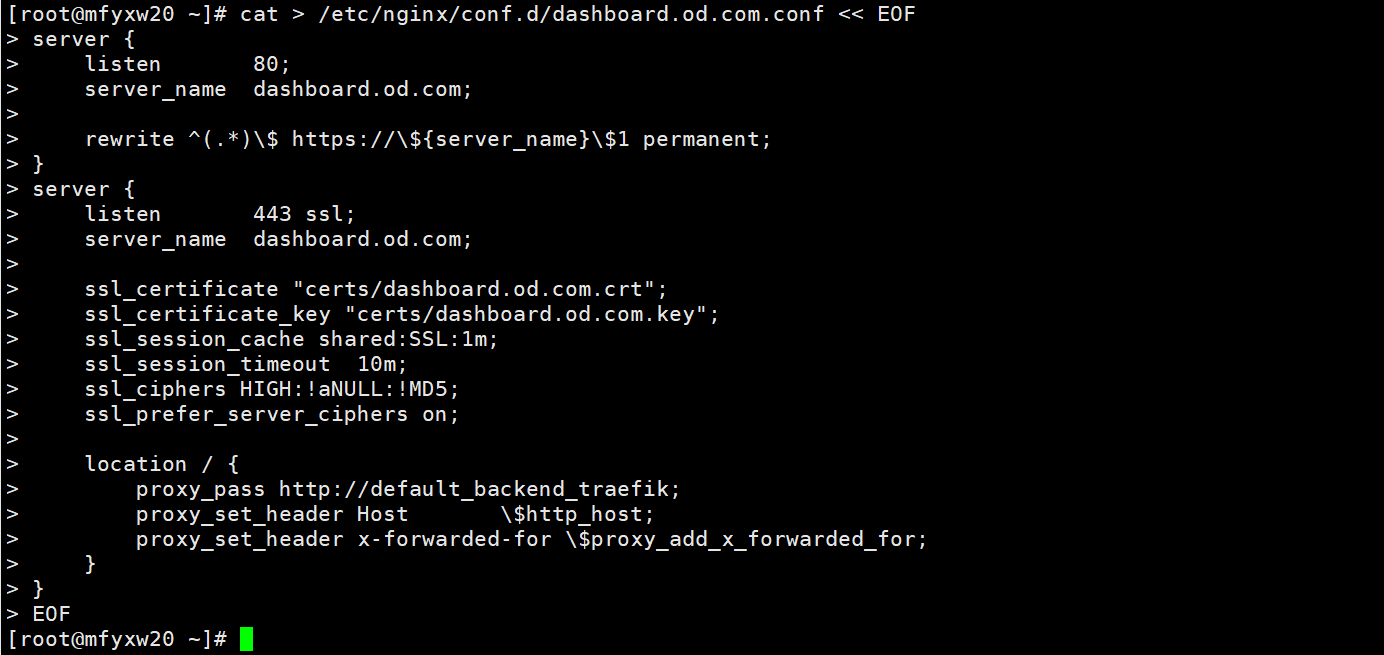
~]# cat > /etc/nginx/conf.d/dashboard.od.com.conf << EOF
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.od.com.crt";
ssl_certificate_key "certs/dashboard.od.com.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
EOF
分别重启mfyxw10.mfyxw.com和mfyxw20.mfyxw.com主机的nginx服务
~]# nginx -t
~]# nginx -s reload

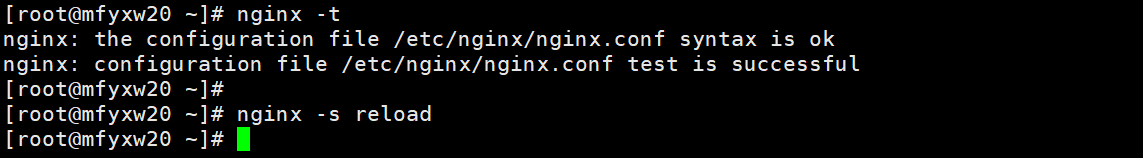
11.查看bashboard的pod是否运行起来
在master节点(mfyxw30.mfyxw.com或mfyxw40.mfyxw.com)任意一台执行
[root@mfyxw30 ~]# kubectl get pod -n kube-system
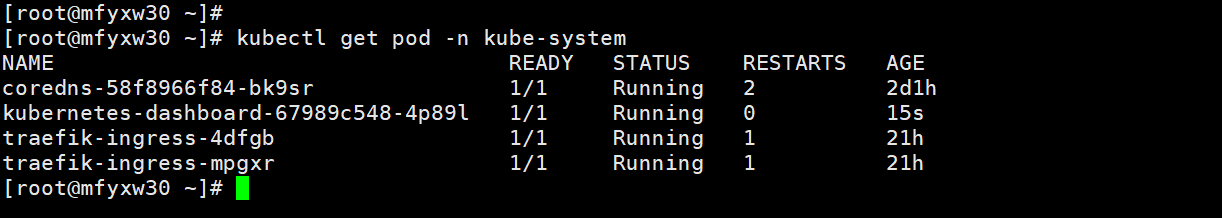
12.访问域名dashboard.od.com
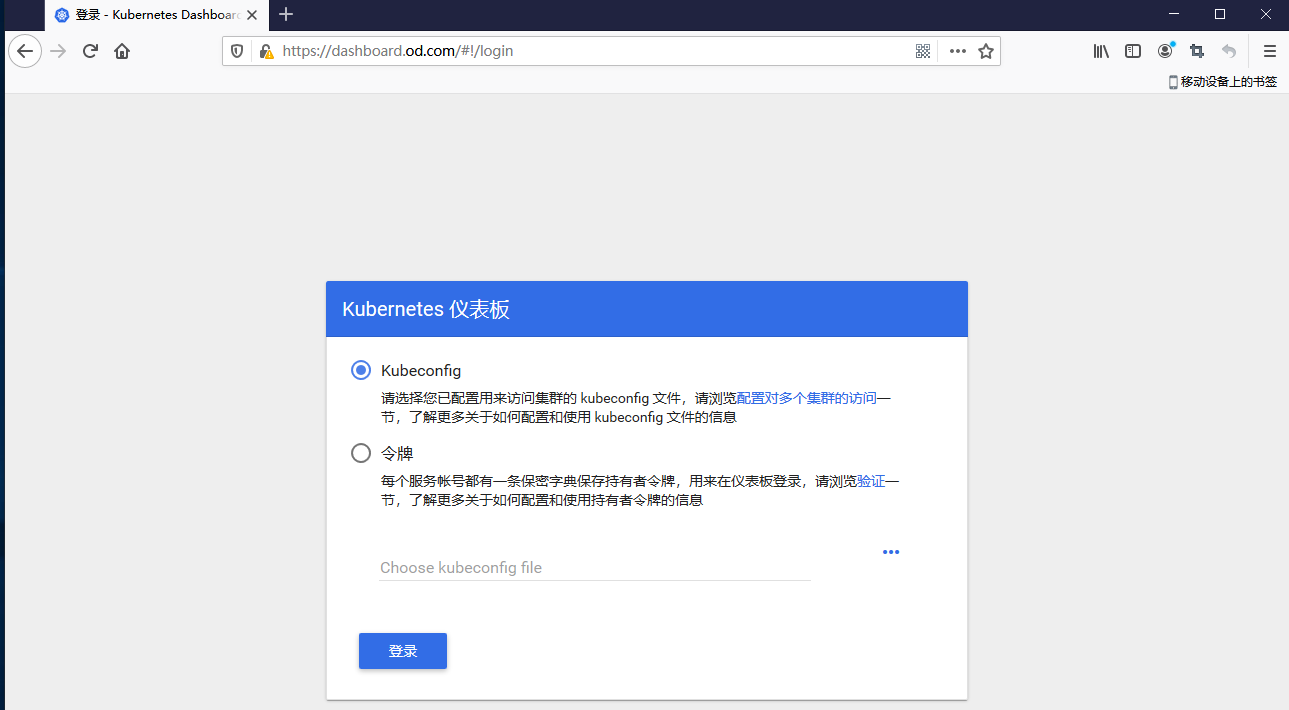
13.查看dashboard的token
kubernetes-dashboard的pod镜像成功运行后,会由kuberneter-dashboard-admin服务帐号自动生成secret,查看secret得到token就可以登录
一个服务帐号,它一定会对应着一个惟一的有服务帐号的secret
在master节点(mfyxw30.mfyxw.com或mfyxw40.mfyxw.com)任意一台执行
[root@mfyxw30 ~]# kubectl get secret -n kube-system
[root@mfyxw30 ~]# kubectl describe secret kubernetes-dashboard-admin-token-94gf4 -n kube-system
14.使用查询到的token登录dashboard
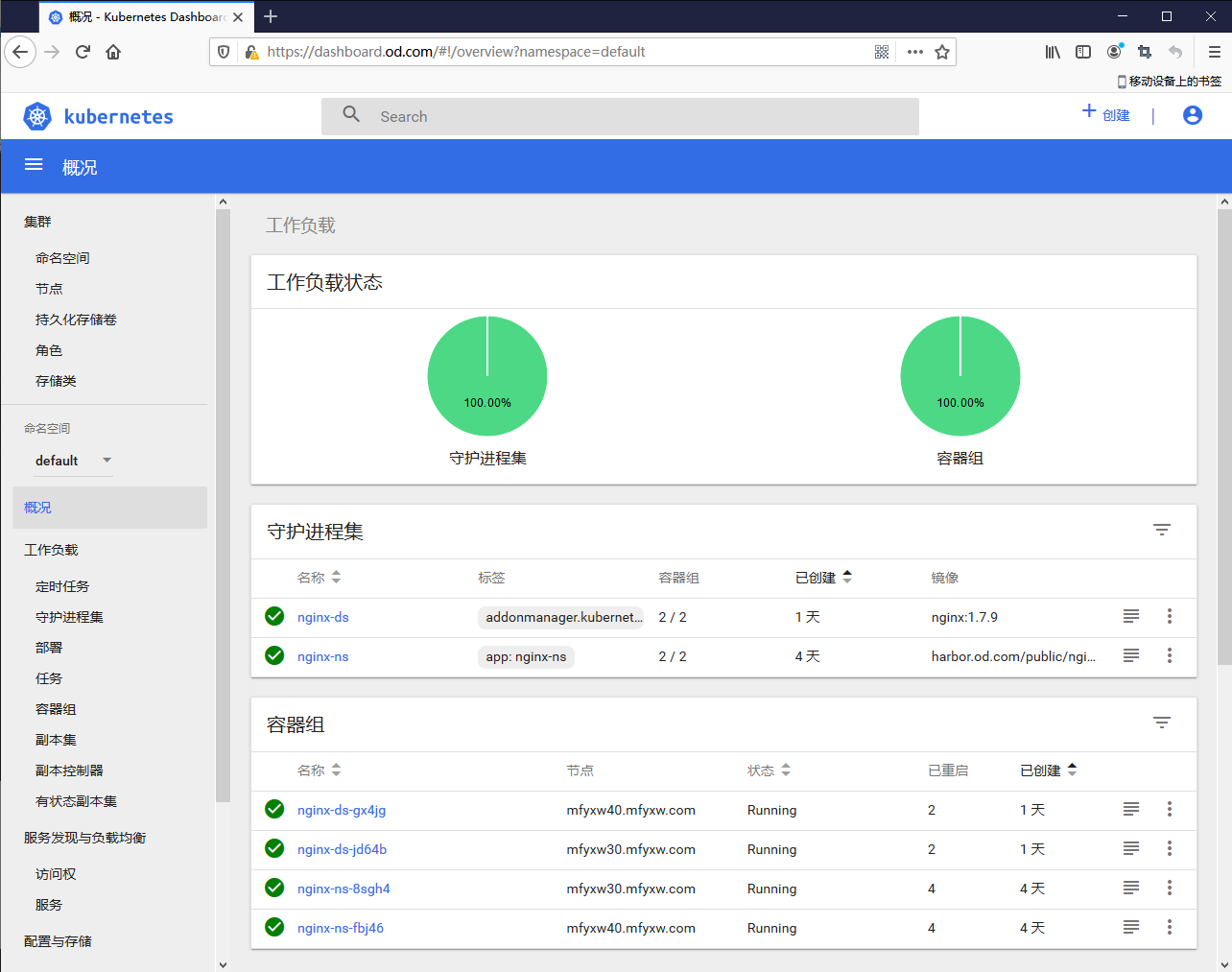
15.查看traefik