WindowsIdentity类可以获取当前执行者的身份信息
- /// <summary>
- /// 递归搜索文件方法
- /// </summary>
- /// <param name="path">搜索的目录</param>
- /// <param name="name">搜索的文件名</param>
- public void GetDir(string path,string name)
- {
- DirectoryInfo di = new DirectoryInfo(path);
- DirectorySecurity s = new DirectorySecurity(path, AccessControlSections.Access);
- //判断目录是否 可以访问
- if (!s.AreAccessRulesProtected)
- {
- foreach (DirectoryInfo d in di.GetDirectories())
- {
- foreach (FileInfo fi in di.GetFiles())
- {
- if (fi.Name.Contains(name))
- {
- txtInfo.AppendText("文件名:"+fi.Name + " 路径:" + fi.FullName + " ");
- }
- }
- GetDir(d.FullName, name);
- }
- }
- }
对执行的程序设定执行身份权限
如果程序不是以管理员身份运行,操作本地文件会提示:System.UnauthorizedAccessException异常
Vista 和 Windows 7 操作系统为了加强安全,增加了 UAC(用户账户控制) 的机制,如果 UAC 被打开,用户即使是以管理员权限登录,其应用程序默认情况下也无法对系统目录,系统注册表等可能影响系统运行的设置进行写操作。这个机制大大增强了系统的安全性,但对应用程序开发者来说,我们不能强迫用户去关闭UAC,但有时我们开发的应用程序又需要以 Administrator 的方式运行,即 Win7 中 以 as administrator 方式运行,那么我们怎么来实现这样的功能呢?
我们在 win7 下运行一些安装程序时,会发现首先弹出一个对话框,让用户确认是否同意允许这个程序改变你的计算机配置,但我们编写的应用程序默认是不会弹出这个提示的,也无法以管理员权限运行。本文介绍了 C# 程序如何设置来提示用户以管理员权限运行。
首先在项目中增加一个 Application Manifest File

默认的配置如下:
<asmv1:assembly manifestVersion="1.0" xmlns="urn:schemas-microsoft-com:asm.v1"
xmlns:asmv1="urn:schemas-microsoft-com:asm.v1" xmlns:asmv2="urn:schemas-microsoft-com:asm.v2"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<assemblyIdentity version="1.0.0.0" name="MyApplication.app"/>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges xmlns="urn:schemas-microsoft-com:asm.v3">
<!-- UAC Manifest Options
If you want to change the Windows User Account Control level replace the
requestedExecutionLevel node with one of the following.
<requestedExecutionLevel level="asInvoker" uiAccess="false" />
<requestedExecutionLevel level="requireAdministrator" uiAccess="false" />
<requestedExecutionLevel level="highestAvailable" uiAccess="false" />
If you want to utilize File and Registry Virtualization for backward
compatibility then delete the requestedExecutionLevel node.
-->
<requestedExecutionLevel level="asInvoker" uiAccess="false" />
</requestedPrivileges>
</security>
</trustInfo>
</asmv1:assembly>
我们可以看到这个配置中有一个 requestedExecutionLevel 项,这个项用于配置当前应用请求的执行权限级别。这个项有3个值可供选择,如下表所示:
| Value | Description | Comment |
| asInvoker | The application runs with the same access token as the parent process. | Recommended for standard user applications. Do refractoring with internal elevation points, as per the guidance provided earlier in this document. |
| highestAvailable | The application runs with the highest privileges the current user can obtain. | Recommended for mixed-mode applications. Plan to refractor the application in a future release. |
| requireAdministrator | The application runs only for administrators and requires that the application be launched with the full access token of an administrator. | Recommended for administrator only applications. Internal elevation points are not needed. The application is already running elevated. |
asInvoker : 如果选这个,应用程序就是以当前的权限运行。
highestAvailable: 这个是以当前用户可以获得的最高权限运行。
requireAdministrator: 这个是仅以系统管理员权限运行。
默认情况下是 asInvoker。
highestAvailable 和 requireAdministrator 这两个选项都可以提示用户获取系统管理员权限。那么这两个选项的区别在哪里呢?
他们的区别在于,如果我们不是以管理员帐号登录,那么如果应用程序设置为 requireAdministrator ,那么应用程序就直接运行失败,无法启动。而如果设置为 highestAvailable,则应用程序可以运行成功,但是是以当前帐号的权限运行而不是系统管理员权限运行。如果我们希望程序在非管理员帐号登录时也可以运行(这种情况下应该某些功能受限制) ,那么建议采用 highestAvailable 来配置。
关于requestedExecutionLevel 设置的权威文档请参考下面链接:
Create and Embed an Application Manifest (UAC)
下面是修改后的配置文件:
<asmv1:assembly manifestVersion="1.0" xmlns="urn:schemas-microsoft-com:asm.v1"
xmlns:asmv1="urn:schemas-microsoft-com:asm.v1" xmlns:asmv2="urn:schemas-microsoft-com:asm.v2"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<assemblyIdentity version="1.0.0.0" name="MyApplication.app"/>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges xmlns="urn:schemas-microsoft-com:asm.v3">
<!-- UAC Manifest Options
If you want to change the Windows User Account Control level replace the
requestedExecutionLevel node with one of the following.
<requestedExecutionLevel level="asInvoker" uiAccess="false" />
<requestedExecutionLevel level="requireAdministrator" uiAccess="false" />
<requestedExecutionLevel level="highestAvailable" uiAccess="false" />
If you want to utilize File and Registry Virtualization for backward
compatibility then delete the requestedExecutionLevel node.
-->
<requestedExecutionLevel level="requireAdministrator" uiAccess="false" />
</requestedPrivileges>
</security>
</trustInfo>
</asmv1:assembly>
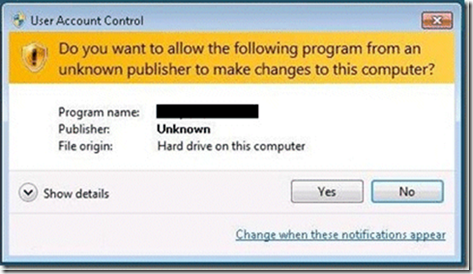
下面再来看看程序如何知道当前运行在系统管理员权限还是非系统管理员权限:
using System.Security.Principal
{
WindowsIdentity identity = WindowsIdentity.GetCurrent();
WindowsPrincipal principal = new WindowsPrincipal(identity);
return principal.IsInRole(WindowsBuiltInRole.Administrator);
}
using System;
using System.Collections;
using System.IO;
using System.Security.AccessControl;
static class Tester
{
public static void Main()
{
try
{
string filename = @"f:k"; //目标目录
string account = @"Administrator";//用户名
string userrights = @"RW";//权限字符串,自己定义的
AddDirectorySecurity(filename, account, userrights);
Console.ReadLine();
}
catch (Exception e)
{
Console.WriteLine(e);
Console.ReadLine();
}
}
static public void AddDirectorySecurity(string FileName, string Account, string UserRights)
{
FileSystemRights Rights = new FileSystemRights();
if (UserRights.IndexOf("R") >= 0)
{
Rights = Rights | FileSystemRights.Read;
}
if (UserRights.IndexOf("C") >= 0)
{
Rights = Rights | FileSystemRights.ChangePermissions;
}
if (UserRights.IndexOf("F") >= 0)
{
Rights = Rights | FileSystemRights.FullControl;
}
if (UserRights.IndexOf("W") >= 0)
{
Rights = Rights | FileSystemRights.Write;
}
bool ok;
DirectoryInfo dInfo = new DirectoryInfo(FileName);
DirectorySecurity dSecurity = dInfo.GetAccessControl();
InheritanceFlags iFlags = new InheritanceFlags();
iFlags = InheritanceFlags.ContainerInherit | InheritanceFlags.ObjectInherit;
FileSystemAccessRule AccessRule2 = new FileSystemAccessRule(Account, Rights, iFlags, PropagationFlags.None, AccessControlType.Allow);
dSecurity.ModifyAccessRule(AccessControlModification.Add, AccessRule2, out ok);
dInfo.SetAccessControl(dSecurity);
//列出目标目录所具有的权限
DirectorySecurity sec = Directory.GetAccessControl(FileName, AccessControlSections.All);
foreach (FileSystemAccessRule rule in sec.GetAccessRules(true, true, typeof(System.Security.Principal.NTAccount)))
{
Console.WriteLine("----------------------------------");
Console.WriteLine(rule.IdentityReference.Value);
if ((rule.FileSystemRights & FileSystemRights.Read) != 0)
Console.WriteLine(rule.FileSystemRights.ToString());
}
Console.Read();
}
}