⭐Crib dragging attack
在开始了解 Crib dragging attack 之前,先来理一理 异或。
异或加密
【详情请戳这里】 XOR 加密简介
异或加密特性:
① 两个值相同时,返回
false,否则返回true。
② 如果对一个值连续做两次 XOR,会返回这个值本身。
③ 加密应用:
假设原始信息是
message,密钥是key,第一次 XOR 会得到加密文本cipherText。对方拿到以后,再用key做一次 XOR 运算,就会还原得到message。
④ 一次性密码本 one-time pad(OTP):
key的长度大于等于messagekey必须是一次性的,且每次都要随机产生满足上述两个条件,即称为 OTP
关于破解
这就要引入主题 :Crib dragging 法。
详情可见 这里
简单来说呢,就是利用一些用同个密钥生成的密文,猜对其中部分密文对应的明文,即可求出公共密钥,再用该可能的密钥去解其他的密文,若符合,则为密钥正确。
⭐ 例题解析-cr2-many-time-secrets
上一道例题看看。 【攻防世界】 题目链接 【cr2-many-time-secrets】
下载附件,得到如下字符串:
0529242a631234122d2b36697f13272c207f2021283a6b0c7908
2f28202a302029142c653f3c7f2a2636273e3f2d653e25217908
322921780c3a235b3c2c3f207f372e21733a3a2b37263b313012
2f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d
283f652c2b31661426292b653a292c372a2f20212a316b283c09
29232178373c270f682c216532263b2d3632353c2c3c2a293504
613c37373531285b3c2a72273a67212a277f373a243c20203d5d
243a202a633d205b3c2d3765342236653a2c7423202f3f652a18
2239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c
263e203d63232f0f20653f207f332065262c3168313722367918
2f2f372133202f142665212637222220733e383f2426386b
乍一看,可不就是十六进制嘛,结果一个ASCII码转换,一堆乱七八糟。
脚本1
依靠大佬 题解 才知 ,对于 OTP 密钥重用,可执行 此攻击脚本 进行破解
将其按一行展开):
0529242a631234122d2b36697f13272c207f2021283a6b0c79082f28202a302029142c653f3c7f2a2636273e3f2d653e25217908322921780c3a235b3c2c3f207f372e21733a3a2b37263b3130122f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d283f652c2b31661426292b653a292c372a2f20212a316b283c0929232178373c270f682c216532263b2d3632353c2c3c2a293504613c37373531285b3c2a72273a67212a277f373a243c20203d5d243a202a633d205b3c2d3765342236653a2c7423202f3f652a182239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c263e203d63232f0f20653f207f332065262c31683137223679182f2f372133202f142665212637222220733e383f2426386b
对其执行一下脚本(cribdrag.py):
python cribdrag.py 0529242a631234122d2b36697f13272c207f2021283a6b0c79082f28202a302029142c653f3c7f2a2636273e3f2d653e25217908322921780c3a235b3c2c3f207f372e21733a3a2b37263b3130122f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d283f652c2b31661426292b653a292c372a2f20212a316b283c0929232178373c270f682c216532263b2d3632353c2c3c2a293504613c37373531285b3c2a72273a67212a277f373a243c20203d5d243a202a633d205b3c2d3765342236653a2c7423202f3f652a182239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c263e203d63232f0f20653f207f332065262c31683137223679182f2f372133202f142665212637222220733e383f2426386b

输入 ALEXCTF{ “0”的位置出现 “Dear Fri” 有戏。

于是将其放入其中,按照步骤一步步来: (如下)

补全前面 Dear Friend ,继续 。得到 ALEXCTF{HER

就这样一步一步摸下来:
最后得到:

脚本2
选自此大佬 脚本
import binascii
def dec(msg, key):
'''
Simple char-by-char XOR with a key (Vigenere, Vernam, OTP)
'''
m = ""
for i in range(0, len(key)):
m += chr(msg[i] ^ ord(key[i]))
return m
######################################
lines = []
with open("msg", "r") as f:
# Read lines from file and decode Hex
ls = f.readlines()
for l in ls:
lines.append(binascii.unhexlify(l[:-1]))
# Step 1: Decode each line with the known key
k = "ALEXCTF{"
mes = []
for l in lines:
m = dec(l, k)
mes.append(m)
print(mes)
# Step 2: Guess some part of the first message 'Dear Fri'
k = "Dear Friend, "
m = dec(lines[0], k)
print(m)
# Step 3: Decode each line with the new known key
k = "ALEXCTF{HERE_"
mes = []
for l in lines:
m = dec(l, k)
mes.append(m)
print(mes)
# Step 4: Guess some part of the last message 'ncryption sc'
k = 'ncryption scheme '
m = dec(lines[-1], k)
print(m)
# Step 5: Decode each line with the new known key
k = "ALEXCTF{HERE_GOES_"
mes = []
for l in lines:
m = dec(l, k)
mes.append(m)
print(mes)
# Step 6: Guess all the second message 'sed One time pad e'
# the third message is 'n scheme, I heard '
# so we can retrive the complete key
k = 'sed One time pad encryptio'
m = dec(lines[2], k)
print(m)
'''
['Dear Fri', 'nderstoo', 'sed One ', 'n scheme', 'is the o', 'hod that', ' proven ', 'ever if ', 'cure, Le', 'gree wit', 'ncryptio']
ALEXCTF{HERE_
['Dear Friend, ', 'nderstood my ', 'sed One time ', 'n scheme, I h', 'is the only e', 'hod that is m', ' proven to be', 'ever if the k', 'cure, Let Me ', 'gree with me ', 'ncryption sch']
ALEXCTF{HERE_GOES
['Dear Friend, This ', 'nderstood my mista', 'sed One time pad e', 'n scheme, I heard ', 'is the only encryp', 'hod that is mathem', ' proven to be not ', 'ever if the key is', 'cure, Let Me know ', 'gree with me to us', 'ncryption scheme a']
ALEXCTF{HERE_GOES_THE_KEY}
'''
Flag 如下:
ALEXCTF{HERE_GOES_THE_KEY}
⭐ 异或例题 - buuctf 异性相吸
【buuctf】 题目链接 异性相吸
下载附件得到一段密文以及一段密钥。key.txt(密钥)如下:
asadsasdasdasdasdasdasdasdasdasdqwesqf
这题解法与 南邮CTF:密码学 异性相吸 相似
解法: 将密钥与密文的每一位异或 得到明文
于是写出相应脚本:
#coding:utf-8
miwen = open("E:\密文.txt",'rb').read()
key = open("E:\key.txt",'rb').read()
flag = ''
for i in range(0,len(miwen)):
str = list(miwen)[i] ^ list(key)[i]
flag += chr(str)
print(flag)
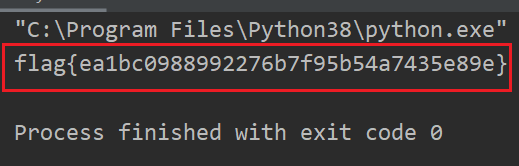
得到flag:
flag{ea1bc0988992276b7f95b54a7435e89e}
【侵权删】 【参考链接】