准备
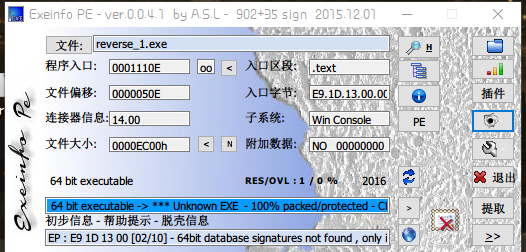
获得信息
64位文件
x64dbg打开
搜索全部字符串
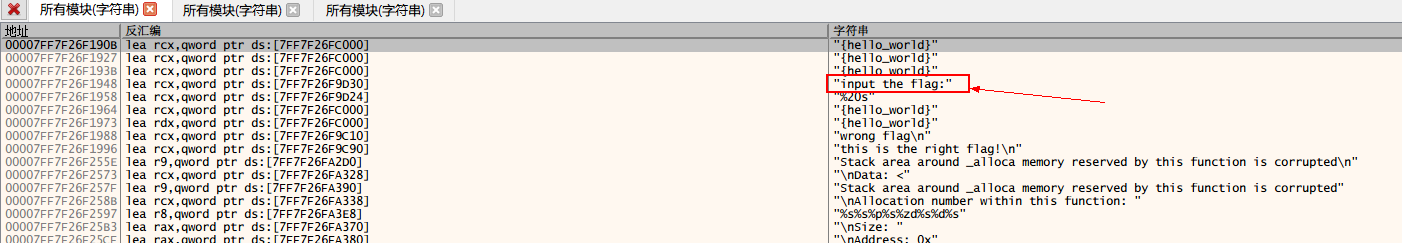
打开红框中字符串的位置
1 00007FF7F26F18FD | 8945 04 | mov dword ptr ss:[rbp+4],eax | 2 00007FF7F26F1900 | 48:6345 04 | movsxd rax,dword ptr ss:[rbp+4] | 3 00007FF7F26F1904 | 48:8985 08010000 | mov qword ptr ss:[rbp+108],rax | 4 00007FF7F26F190B | 48:8D0D EEA60000 | lea rcx,qword ptr ds:[7FF7F26FC000] | 00007FF7F26FC000:"{hello_world}" 5 00007FF7F26F1912 | E8 8DF8FFFF | call reverse_1.7FF7F26F11A4 | 6 00007FF7F26F1917 | 48:8B8D 08010000 | mov rcx,qword ptr ss:[rbp+108] | 7 00007FF7F26F191E | 48:3BC8 | cmp rcx,rax | 8 00007FF7F26F1921 | 77 25 | ja reverse_1.7FF7F26F1948 | 9 00007FF7F26F1923 | 48:6345 04 | movsxd rax,dword ptr ss:[rbp+4] | 10 00007FF7F26F1927 | 48:8D0D D2A60000 | lea rcx,qword ptr ds:[7FF7F26FC000] | 00007FF7F26FC000:"{hello_world}" 11 00007FF7F26F192E | 0FBE0401 | movsx eax,byte ptr ds:[rcx+rax] | 12 00007FF7F26F1932 | 83F8 6F | cmp eax,6F | 6F:'o' 13 00007FF7F26F1935 | 75 0F | jne reverse_1.7FF7F26F1946 | 14 00007FF7F26F1937 | 48:6345 04 | movsxd rax,dword ptr ss:[rbp+4] | 15 00007FF7F26F193B | 48:8D0D BEA60000 | lea rcx,qword ptr ds:[7FF7F26FC000] | 00007FF7F26FC000:"{hello_world}" 16 00007FF7F26F1942 | C60401 30 | mov byte ptr ds:[rcx+rax],30 | 30:'0' 17 00007FF7F26F1946 | EB B0 | jmp reverse_1.7FF7F26F18F8 | 18 00007FF7F26F1948 | 48:8D0D E1830000 | lea rcx,qword ptr ds:[7FF7F26F9D30] | 00007FF7F26F9D30:"input the flag:" 19 00007FF7F26F194F | E8 7DF8FFFF | call reverse_1.7FF7F26F11D1 | 20 00007FF7F26F1954 | 48:8D55 28 | lea rdx,qword ptr ss:[rbp+28] | 21 00007FF7F26F1958 | 48:8D0D C5830000 | lea rcx,qword ptr ds:[7FF7F26F9D24] | 00007FF7F26F9D24:"%20s" 22 00007FF7F26F195F | E8 2BF9FFFF | call reverse_1.7FF7F26F128F | 23 00007FF7F26F1964 | 48:8D0D 95A60000 | lea rcx,qword ptr ds:[7FF7F26FC000] | 00007FF7F26FC000:"{hello_world}" 24 00007FF7F26F196B | E8 34F8FFFF | call reverse_1.7FF7F26F11A4 | 25 00007FF7F26F1970 | 4C:8BC0 | mov r8,rax | 26 00007FF7F26F1973 | 48:8D15 86A60000 | lea rdx,qword ptr ds:[7FF7F26FC000] | 00007FF7F26FC000:"{hello_world}" 27 00007FF7F26F197A | 48:8D4D 28 | lea rcx,qword ptr ss:[rbp+28] | 28 00007FF7F26F197E | FF15 4CE90000 | call qword ptr ds:[<&strncmp>] | 29 00007FF7F26F1984 | 85C0 | test eax,eax | 30 00007FF7F26F1986 | 74 0E | je reverse_1.7FF7F26F1996 | 31 00007FF7F26F1988 | 48:8D0D 81820000 | lea rcx,qword ptr ds:[7FF7F26F9C10] | 00007FF7F26F9C10:"wrong flag " 32 00007FF7F26F198F | E8 3DF8FFFF | call reverse_1.7FF7F26F11D1 | 33 00007FF7F26F1994 | EB 0C | jmp reverse_1.7FF7F26F19A2 | 34 00007FF7F26F1996 | 48:8D0D F3820000 | lea rcx,qword ptr ds:[7FF7F26F9C90] | 00007FF7F26F9C90:"this is the right flag! " 35 00007FF7F26F199D | E8 2FF8FFFF | call reverse_1.7FF7F26F11D1 |
代码分析
第28行代码调用了strcmp比较输入字符串与“{hello_world}”,这个“{hello_world}”似乎就是我们的flag。
在"input the flag"上面,分析代码,了解到此部分对“{hello_world}”进行了'o'字符替换为‘0’字符的操作。因此得到正确答案为“{hell0_w0rld}”
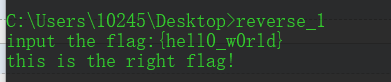
get flag!
flag{hell0_w0rld}