21766239b79ece18b15a03f4517f3be6ed9c07ed
样本行为:
1、修改MBR
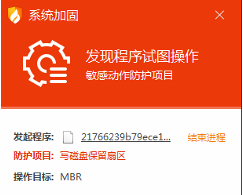
2、自关机
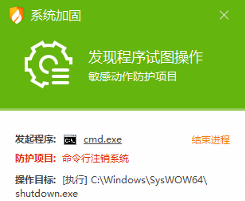
3、关机自启后锁机
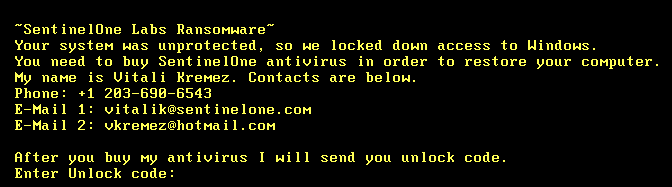
样本分析:
载入IDA
主函数 如下:
void start
{
sub_402058();
a2(&VirtualProtect, 172);
sub_402002(&VirtualProtect, 172, 255);
(loc_405010);
sub_402002(&VirtualProtect, 172, 255);
a1(&VirtualProtect, 172);
off_40100C = &unk_4051BA; //数据
dword_401010 = 512;
a2(&loc_4050BC, 254);
sub_402002(&loc_4050BC, 254, 255);
(loc_4050BC);
sub_402002(&loc_4050BC, 254, 255);
a1(&loc_4050BC, 254);
ExitProcess(a3);
}
sub_402058():
{
sub_402002(&nullsub_1, 16, 255);
v1 = VirtualProtect;
v2 =VirtualProtect;
VirtualProtect(&nullsub_1, 16);
(nullsub_1);
if ( v3 )
{
v2(&nullsub_1, 16);
sub_402002(&nullsub_1, 16, 255);
}
else
{start(v2, v1, a1);}
}
sub_402002(): //对数据进行操作
{
char *v3; // esi
char *v4; // edi
char v6; // al
v3 = a1;
v4 = a1;
do
{
v6 = *v3++;
*v4++ = a3 ^ v6;
--a2;
}
while ( a2 );
}
loc_4050BC:
{
Lahf //将标志位加载到 AH
xchg eax, ebp //交换eax和ebp的内容
call dword ptr [ebp-6A036A01h]
call dword ptr [ebp-6803h]
}
载入OD:
首先进入函数0x4020B5
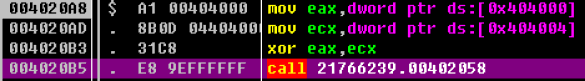
然后进0x402002函数
该函数 装载0x405000处的数据 做异或
![gguß2ß11 912 ßß0ß2ß114 ßß0ß2ß15 3 oc8 75 F9 byte ptr ds:[esi] lods xor byte ptr es:[edi] stos dec edx Short 21766239.00402011](https://s2.loli.net/2022/01/16/KTFbrx2oicz1Jvp.png)
0x40307D call esi 此处调用VirtualProtect、VirtualProtectEx
VirtualProtect将进程句柄、内存地址、内存大小等参数传递给VirtualProtectEx函数来设置内存的属性
调用ZwProtectVirtualMemory修改内存属性
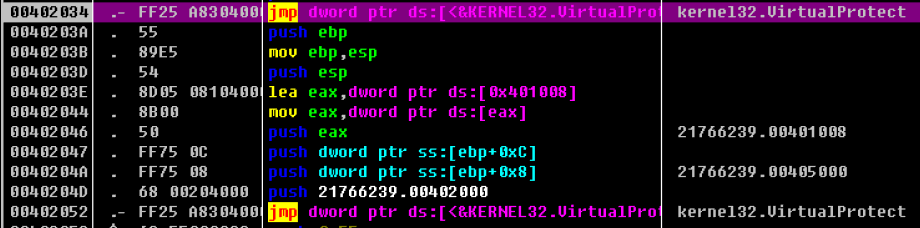
0x402083-进入到0x405000地址位置 此处存储的是0x402002函数处理的数据
后续调用IsDebuggerPresent函数 用来检测调试器
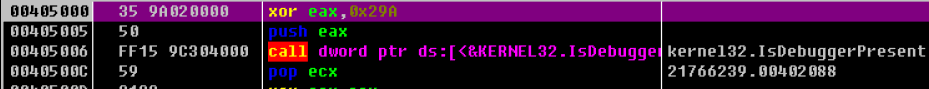
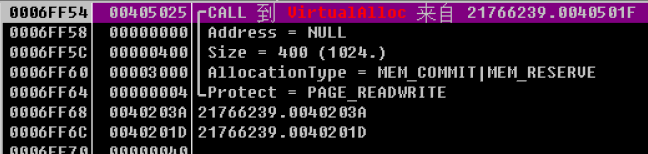
0x4020DD 此地址处的函数 后续调用VirtualAlloc分配了两次空间
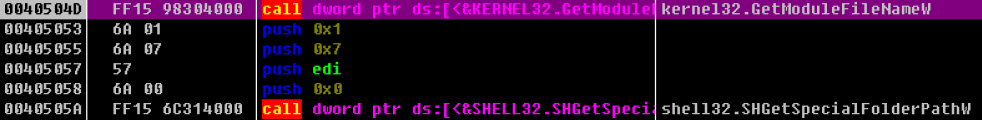
0x40504D GetModuleFileName获取当前进程文件的路径
0x40505A SHGetSpecialFolderPath获取系统路径(开始菜单)
0x405064-进入该地址可见调用了lstrcatW、CopyFileW函数 此处的主要目的是 设置开机自启
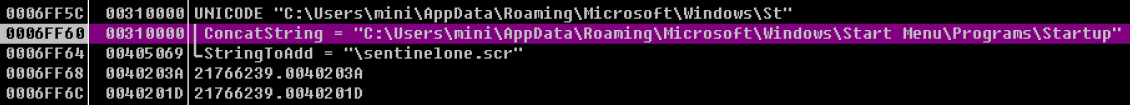
0x4050A6 此处释放一次VirtualFree
0x4050B4 此处释放再一次VirtualFree
0x40213C 进入该地址
0x4050CD-0x4050F8该地址处调用了CreateFile函数 打开\.\PhysicalDrive0
0x40512F 调用WriteFile函数 修改MBR数据
KiFastSystemCall
0x4050157-0x40518B-0x4051A1
0x4051B2 调用ShellExecute函数 启动CMD
执行命令shutdown -r -t 1 -f 以关机