import socketserver class KnightServer(socketserver.BaseRequestHandler): def handle(self): # self.request 相当于conn链接通道 while 1: from_client_msg = self.request.recv(1024) print(from_client_msg.decode('utf-8')) server_msg = input('服务端说>>>') self.request.send(server_msg.encode('utf-8')) if __name__ == '__main__': ip_port = ('127.0.0.1',8001) server = socketserver.ThreadingTCPServer(ip_port,KnightServer) server.serve_forever()
import socket import time client = socket.socket() client.connect(('127.0.0.1',8001)) while 1: client_data = input('别开车>>>') client.send(client_data.encode('utf-8')) from_server_msg = client.recv(1024) print(from_server_msg.decode('utf-8')) client.close()
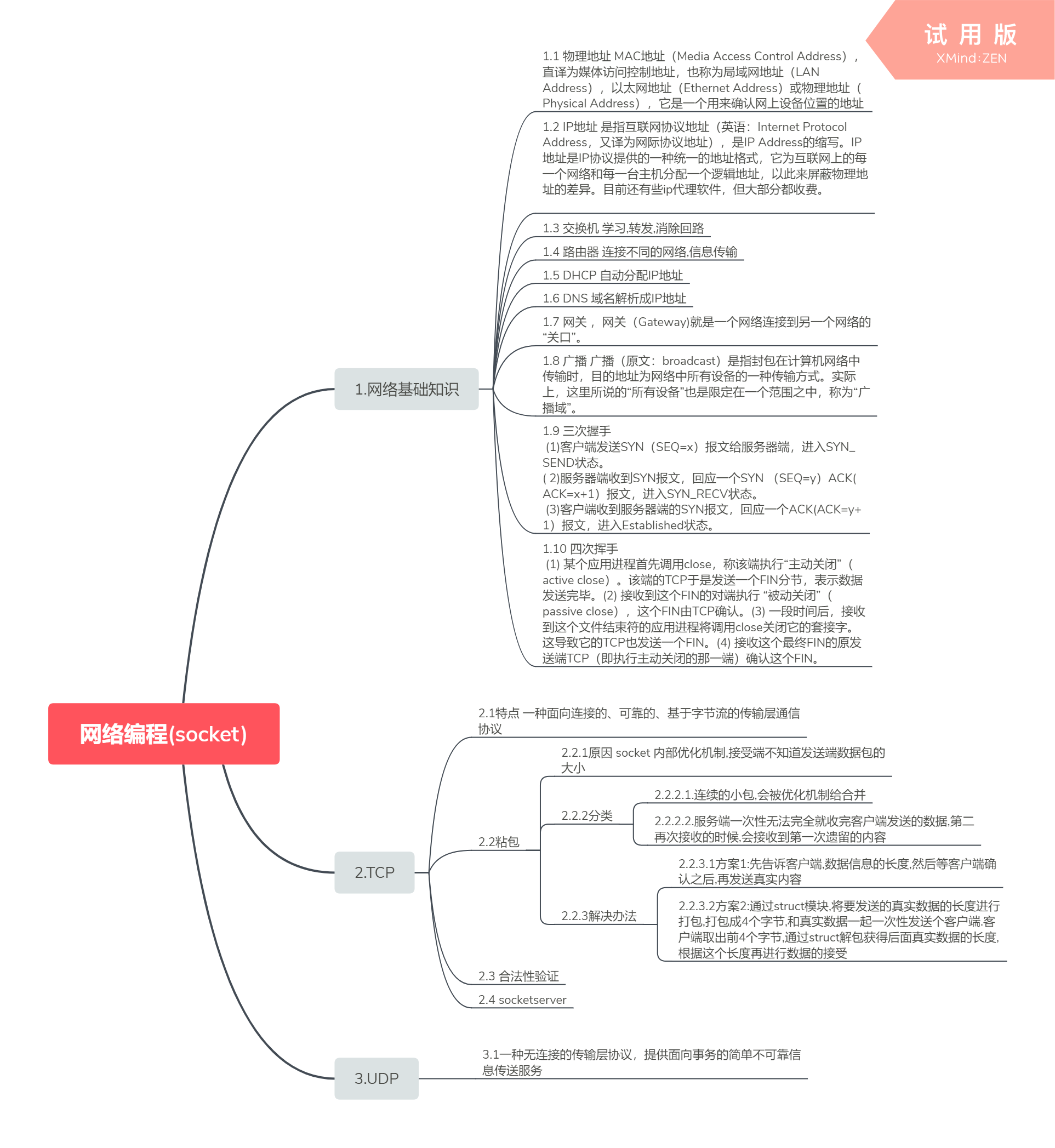
粘包解决方案一
import socket import subprocess server = socket.socket() ip_port = ('127.0.0.1',8001) server.bind(ip_port) server.listen() conn,addr = server.accept() while 1: from_client_cmd = conn.recv(1024).decode('utf-8') sub_obj = subprocess.Popen( from_client_cmd, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, ) #subprocess对象.read 得到的结果是bytes类型的 cmd_res = sub_obj.stdout.read() data_len = len(cmd_res) data_len_str = str(data_len) print('结果长度>>>',data_len) conn.send(data_len_str.encode('utf-8')) client_stutas = conn.recv(1024).decode('utf-8') if client_stutas == 'ok': conn.send(cmd_res) else: print('客户端长度信息没有收到')
import json import socket client = socket.socket() ip_port = ('127.0.0.1',8001) client.connect(ip_port) while 1: client_cmd = input('请输入系统指令>>>') client.send(client_cmd.encode('utf-8')) from_server_datalen = client.recv(1024).decode('utf-8') client.send(b'ok') from_server_result = client.recv(int(from_server_datalen)) print(from_server_result.decode('gbk'))
#粘包解决方案二
import socket import subprocess import struct server = socket.socket() ip_port = ('127.0.0.1',8001) data_full_len = 0 #统计发送数据的长度 server.bind(ip_port) server.listen() conn,addr = server.accept() while 1: from_client_cmd = conn.recv(1024).decode('utf-8') sub_obj = subprocess.Popen( from_client_cmd, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, ) #subprocess对象.read 得到的结果是bytes类型的 cmd_res = sub_obj.stdout.read() data_len = len(cmd_res) #总数据长度 data_len_str = str(data_len) print('结果长度>>>',data_len) #将真实数据长度打包成4个字节的数据 struct_data_len = struct.pack('i',data_len) conn.send(struct_data_len + cmd_res)
import json import socket import struct client = socket.socket() ip_port = ('127.0.0.1',8001) client.connect(ip_port) all_recv_len = 0 all_data_byte = b'' while 1: client_cmd = input('请输入系统指令>>>') client.send(client_cmd.encode('utf-8')) #先接收4个字节,这4个字节是真实数据长度加工成的 recv_data_len = client.recv(4) #将4个字节长度的数据,解包成后面真实数据的长度 real_data_len = struct.unpack('i',recv_data_len)[0] print(real_data_len) server_result = client.recv(real_data_len) print(server_result.decode('gbk'))
合法性验证
from socket import * import hmac,os secret_key=b'Jedan has a big key!' def conn_auth(conn): ''' 认证客户端链接 :param conn: :return: ''' print('开始验证新链接的合法性') msg=os.urandom(32)#生成一个32字节的随机字符串 conn.sendall(msg) h=hmac.new(secret_key,msg) digest=h.digest() respone=conn.recv(len(digest)) return hmac.compare_digest(respone,digest) def data_handler(conn,bufsize=1024): if not conn_auth(conn): print('该链接不合法,关闭') conn.close() return print('链接合法,开始通信') while True: data=conn.recv(bufsize) if not data:break conn.sendall(data.upper()) def server_handler(ip_port,bufsize,backlog=5): ''' 只处理链接 :param ip_port: :return: ''' tcp_socket_server=socket(AF_INET,SOCK_STREAM) tcp_socket_server.bind(ip_port) tcp_socket_server.listen(backlog) while True: conn,addr=tcp_socket_server.accept() print('新连接[%s:%s]' %(addr[0],addr[1])) data_handler(conn,bufsize) if __name__ == '__main__': ip_port=('127.0.0.1',9999) bufsize=1024 server_handler(ip_port,bufsize)
from socket import * import hmac,os secret_key=b'Jedan has a big key!' def conn_auth(conn): ''' 验证客户端到服务器的链接 :param conn: :return: ''' msg=conn.recv(32) h=hmac.new(secret_key,msg) digest=h.digest() conn.sendall(digest) def client_handler(ip_port,bufsize=1024): tcp_socket_client=socket(AF_INET,SOCK_STREAM) tcp_socket_client.connect(ip_port) conn_auth(tcp_socket_client) while True: data=input('>>: ').strip() if not data:continue if data == 'quit':break tcp_socket_client.sendall(data.encode('utf-8')) respone=tcp_socket_client.recv(bufsize) print(respone.decode('utf-8')) tcp_socket_client.close() if __name__ == '__main__': ip_port=('127.0.0.1',9999) bufsize=1024 client_handler(ip_port,bufsize)